Ransomware is nothing new. It has been a significant threat to organisations around the world for some time now. However, what was once a relatively straightforward threat is fast becoming increasingly complex.
Traditionally, cybercriminals would force their way through perimeter defences, drop their malicious payload and demand a ransom to “fix” the situation. This brute force method of attack was usually remedied by detection, containment and recovery. Essentially, systems would be shut down and backups restored.
Today, however, ransomware is much more sophisticated, targeted and further reaching. Rather than forcing their way in, cybercriminals will target users looking to compromise their credentials, trick them into making a mistake or convince them to launch a malicious attack against their employer.
To defend against this, cyber teams must shift left – earlier in the attack chain. Moving away from detection and recovery and focusing on preparation, prevention – and people.
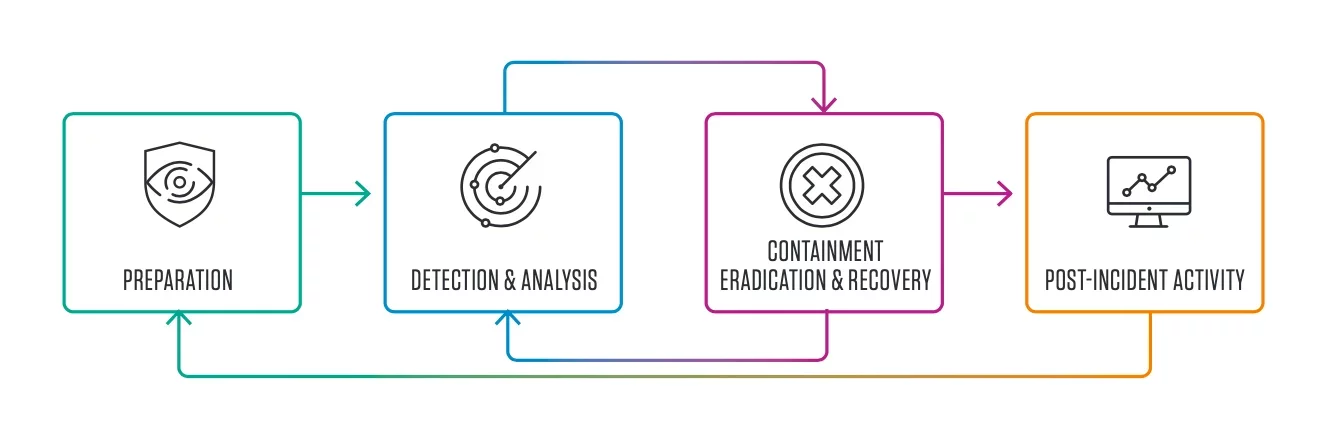
Figure 1. Incident response life cycle (detection and analysis).
Defending your data
The detection and response approach to ransomware was understandable when the issue was solely about information protection. However, with fewer organisations caving in to ransom demands, cybercriminals have changed tact to protect their revenue streams.
Modern ransomware now often carries an extra sting in the tail, be that corporate espionage or data theft, making it very much a data loss prevention (DLP) issue.
That’s why any effective defence against ransomware should place data at its heart. This starts with classification. You need to understand what data is at risk, who needs access to it, who has access to it and how prized it is likely to be by cybercriminals.
When making these classifications, go beyond geography and data location. The traditional data in use and data at rest model is no longer fit for purpose. A modern DLP strategy must follow the user wherever they go – for it is your people that put your data at risk.
The people problem
With over 90% of cyber-attacks requiring some form of human interaction, your users are the biggest risk factor facing your organisation.
These days, cybercriminals rarely break down the door. Instead, they are invited in by your people through either malice, carelessness or compromise. The more you know about your users, their activity and behaviour, the better you can spot the early warning signs of an attack, whatever the driving factor.
Malicious: A malicious user is one who knowingly looks to cause harm to your organisation. They may be disgruntled and looking for revenge or being paid by criminal gangs for access to your networks and data.
Vigilance is critical when detecting malicious users. Implement a solution that can spot suspicious behaviour such as out of hours logins or unusual access requests, and limit access to sensitive information to only your most privileged employees.
Careless: Careless users let cybercriminals inside your perimeter defences by mistake. This may be because they do not log out of corporate systems correctly, use default passwords or fail to apply security patches.
When it comes to spotting carelessness among your teams, keep an eye out for poor security hygiene, such as writing down passwords and installing unauthorised applications.
Compromise: A compromised user is one whose devices or credentials have been commandeered by cybercriminals. Accounts and devices can be compromised by malware, phishing or another form of targeted attack.
Unfortunately, account compromise is notoriously hard to spot. The best defence is to minimise compromise in the first place, through protections such as multi-factor authentication and cybersecurity training.
Rooting out ransomware
The ultimate target of ransomware may be your data, networks and systems. But it can only reach that target via your people. Therefore, the most effective way to keep it at bay is to remove the human element entirely.
With a robust email protection and data loss prevention solution in place, you can analyse, filter and block malicious messaging before it reaches the inbox. However, even the best perimeter defences can be breached.
Email protections should be coupled with deep insight into the telemetry of your access logs and network activity. You need to know who’s accessing your data – how, when and why. The more you know, the faster you can spot anything out of the ordinary.
And then there’s the last line of your defence, your people. Every user must know exactly what to do when faced with a ransomware attack and the consequences of failing to stop one. Most importantly, they must understand how their behaviour can put your organisation at risk.
This is only possible through ongoing and adaptive security awareness training that goes beyond multiple-choice tests and standard best practices. The ultimate goal of any training program should be to create a security culture in which cybersecurity is everyone’s responsibility.
The simple fact is, ransomware is growing ever more sophisticated, rendering traditional defences ineffective – and when the cure no longer works, prevention is the only remedy.
Find out more in this overview to the modern approach to information protection.
Learn more about DLP and insider risk
Our fourth issue of New Perimeters – Data Doesn’t Lose Itself is out now.
In a world of increasingly targeted attacks, one thing remains the same - attackers target people. Their techniques have evolved, making protecting your people, your data and how it's accessed more critical than ever.
Explore why we must change the way we prevent data loss and protect against insider threats in our ‘work from anywhere’ reality.











