Does your organization find it challenging to use the content scanning capabilities in your existing data loss prevention (DLP) solution? Proofpoint has introduced a modern approach to content scanning that focuses on detecting sensitive data in motion when that data is most at risk.
Scanning content in motion
All organizations need to know when their sensitive data is being moved, especially in risky ways—such as synced with a personal cloud or copied to unapproved USB device. The sensitivity is identified through data classification by a classification label, source URL or destination URL, or by scanning the content during movement.
Content scanning on the endpoint is the ability to match patterns of content within files to preset content detector rules. This is one path to identifying sensitive data, often mandated by industry regulations. Not all files can be classified accurately without inspecting the content and before the file is moved.
Unfortunately, legacy endpoint DLP solutions force unfair tradeoffs on security teams, who must choose between performance and accuracy of their DLP product. Often, a casualty for a “performing” DLP product is to turn off the heavier features, such as endpoint content scanning.
Content detectors across Proofpoint Enterprise DLP
The endpoint-based content scanning capability from Proofpoint brings the same best-in-class and proven content detectors as found in Proofpoint Cloud App Security Broker (CASB), Proofpoint Email DLP and Proofpoint Endpoint DLP (which make up the Proofpoint Enterprise DLP suite). That means you can take advantage of your existing investments with Proofpoint.
The content detection rules identify credit card numbers, international bank account numbers (IBAN), U.S. Social Security numbers, U.K. national identifiers, email addresses, dates of birth, driver’s license numbers, email addresses, and other proprietary terms.
Content scanning is triggered when a user attempts to move data or files in four ways:
- Copying to USB devices
- Syncing files to cloud sync folders on the endpoint
- Uploading files to and from web applications
- Downloading files to and from web applications
Security administrators can also assign appropriate content detectors and data classification methods for groups or regions of users using realm or endpoint-level controls.
Workflow in the product
Security admins can configure content scanning within the administration application on the Information and Cloud Security platform. Once content scanning is enabled for the respective realm (see screenshot below), they can select the scan triggers and DLP detectors.
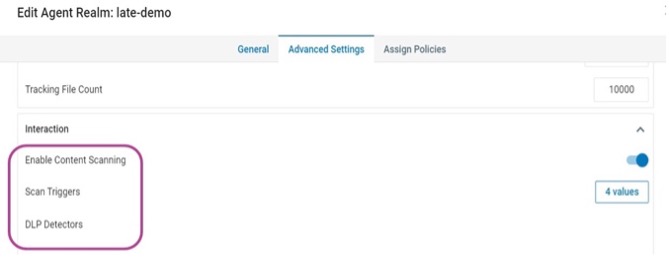
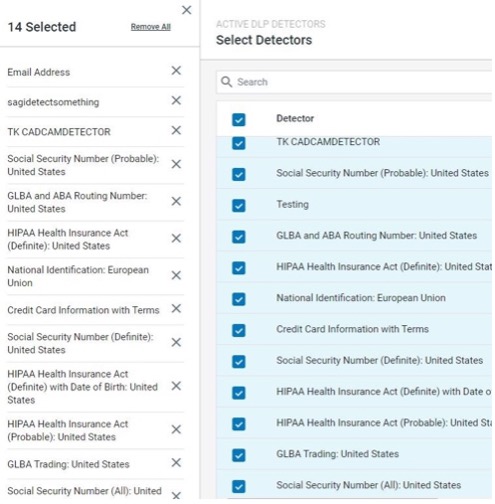
Figure 1: Proofpoint content scanning
Depending on an organization’s primary data movement channels, security administrators will select one or more of the scan triggers. Some organizations block or see very little USB usage, so they prioritize other channels when identifying important information.
Some organizations will choose from a bevvy of content detectors that help meet multiple regulations including the Health Insurance Portability and Accountability Act (HIPAA), Gramm-Leach-Bliley Act (GLBA), Payment Card Industry (PCI) security standards, the European Union’s General Data Protection Regulation (GDPR) and others.
Endpoint DLP will alert security analysts in cases of risky movement of sensitive data, where sensitivity is captured through the content scanning policies set up through the process above. That helps security teams identify risk even when apriori data classification is not possible. They also save their analysts time by focusing only on sensitive content.
In the analytics application, analysts will see the content detector rules that were matched. In the example shown below, the user was attempting to move a file containing credit card numbers from their desktop onto WeTransfer (a cloud-based file sharing application).
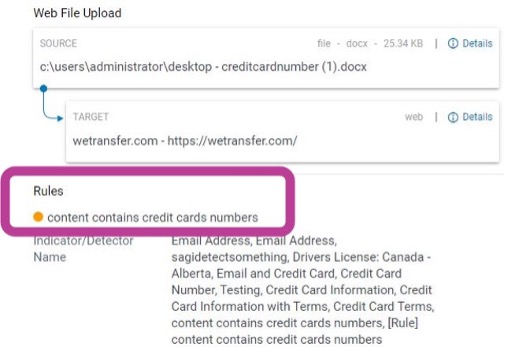
Figure 2: Risky data content scanning
If the organization has the Proofpoint Insider Threat Management solution on top of Endpoint DLP set up for the respective endpoint, screenshots of data movement will also appear. This provides irrefutable evidence of wrongdoing that’s easier for all teams, and not just the security team, to understand.
For example, in the screenshot below, it’s clear that the user opened the WeTransfer application and transferred the files through the WeTransfer website.
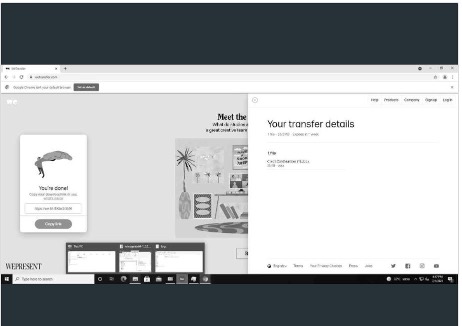
Figure 3: Risky data movement screenshot
Obey the rule: don’t break the endpoint
We built our content scanning features to remain lightweight by:
- Scanning content only when the file is in motion
- Providing security administrators with greater control over scanning workflows
- Using our unique, lightweight file driver that focuses on user activity with files
This is how we can meet most regulatory-driven content detection needs, while allowing your users to remain performative on their endpoints.
The combination of the user’s data activity, the sensitivity of that data via sensitivity labels and the user’s risk profile (e.g., watch lists), gives you meaningful insight into potentially risk behavior—whether compromised, malicious or negligent—to apply the necessary enforcement or action.
We’re excited for you to experience the content scanning capabilities in the Proofpoint Endpoint DLP solution. You can learn more about these capabilities here.











