This week, we released the 2018 edition of our Beyond the Phish® Report, an annual publication that analyzes data gathered from knowledge assessments and training challenges presented to our customers’ end users via our Security Education Platform. This year’s report analyzes nearly 85 million questions and answers related to 12 cybersecurity topics, and compares results across 16 industries.
Whether you are actively running a security awareness training program or are still in discovery and planning stages, the statistics in our report will provide valuable insights as you consider how your employees’ cybersecurity knowledge matches up against their industry peers and other end users in general.
Assessing Knowledge Beyond the Click
You’ll get no argument from us that email-based phishing attacks are a serious threat to organizations worldwide. Anti-phishing training should be the foundation of any cybersecurity education program — but it’s critical to think beyond email (in more ways than one) in order to effectively strengthen end-user defenses.
Simulated phishing attacks — that is, email tests designed to mimic real-world social engineering attacks — are a staple of anti-phishing education programs. And given that Wombat Security’s co-founders pioneered this form of risk assessment during their research at Carnegie Mellon University, we are big believers in these tools. But we know that they don’t tell the full story of susceptibility, nor can they alone be relied on to effectively educate end users about the myriad of cybersecurity threats they are likely to face day to day.
The differences between phishing tests and question-based evaluations is illustrated in the figure below. It compares average simulated attack click rates — courtesy of our 2018 State of the Phish™ Report — with the Beyond the Phish data from our Identifying Phishing Threats category.

The reality is that there can be many reasons why someone doesn’t respond to a simulated attack: overfull mailbox; mail that wasn’t relevant to them; too busy with other things; etc. Non-engagement is not a clear indication of knowledge, understanding, or strong defenses, which is why click rates alone don’t tell the full story of susceptibility. As the illustration reflects — and as additional comparisons within our report show — simulated attacks and question-based assessments, when used together, give a fuller representation of end-user knowledge levels than phishing tests alone.
Comparing End-User Performance Across 12 Categories and 16 Industries
Though our analysis does cover knowledge levels related to email-based phishing, as the name of our report so clearly indicates, it’s critical that organizations acknowledge and evaluate the many other risky end-user behaviors that can negatively impact the security of data, systems, and assets — including employees.
This year’s report includes two new categories: Avoiding Ransomware Attacks (which covers employees’ recognition of what ransomware is and best practices for identifying and avoiding attacks) and Identifying Common Security Issues (which examines users’ high-level understanding of essential cybersecurity best practices). In addition, we again explore end-user understanding of important topics like compliance with data security standards, recognition of phishing tactics, application of data management techniques, and more.
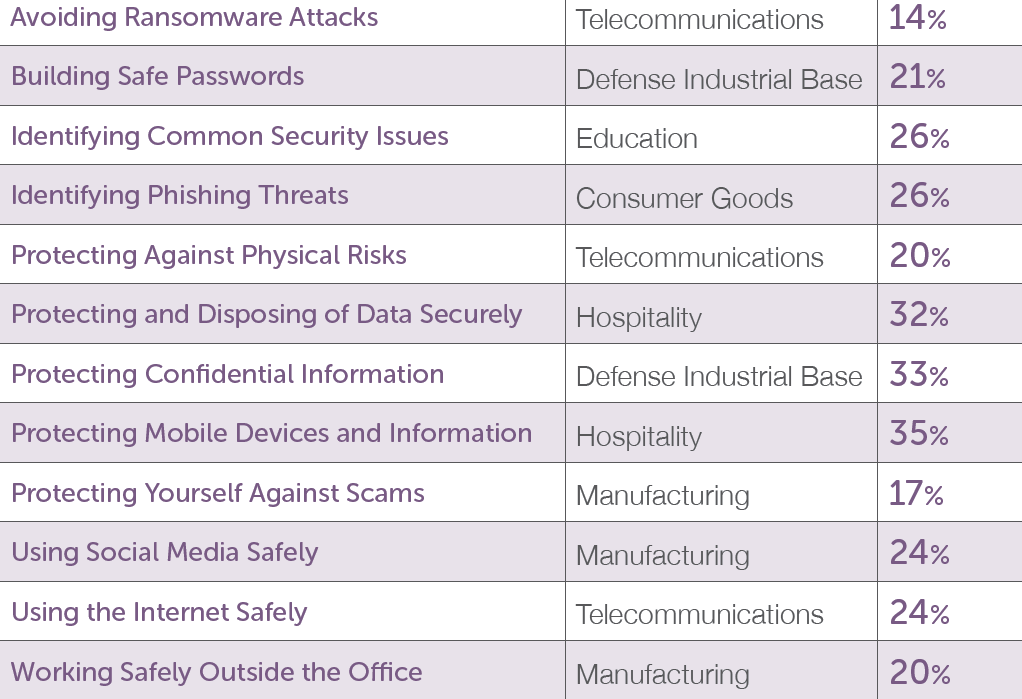
Also new for 2018, we’ve dug deeper into performances by industry, showing how end users in each of 16 industries fared in all 12 categories. We also provide comparisons like those shown in the chart below, which identifies the industries whose end users answered the highest percentage of questions incorrectly about each cybersecurity topic.
Worst Category Performance by Industry
For additional information and analysis, including descriptions of all 12 categories, the best performing industries by category, and industry breakdowns, download your free copy of the Beyond the Phish Report.













