Key Takeaways
- Proofpoint identified a series of campaigns using fraudulent job offers to target university students.
- The lures mostly purported to be related to bioscience and health entities.
- The campaigns began as early as March 2023 and continued through June 2023.
- The threat actor tried to entice recipients to have a video call about the role, with the ultimate objective of the campaigns to likely to conduct advance fee fraud (AFF).
Overview
As layoffs impact thousands of people across many different industries, threat actors continue to exploit the labor market with employment scams to attempt to steal money from job-hunters, based on Proofpoint research and analysis.
Proofpoint observed a campaign in late May 2023 using a series of job-themed email lures to target university students in North America. The email messages purported to be from a variety of organizations, the majority of which were related to biosciences, healthcare, and biotechnology, with some additional unrelated organizations included as well. The activity continued through June 2023.
The messages contained interview requests for remote data entry jobs. Emails typically contained an attached PDF that included alleged information about the organization, the position offered, salary, and equipment specifications.
The sender would invite the recipient to conduct a video or chat interview on a third-party platform for additional information and to prepare them for the role. While Proofpoint was not able to confirm the requests made in a video interview, researchers assess with high confidence based on previous related activity that the actor likely told the recipient they would need to pay an advance fee for equipment before receiving it, which the threat actor would collect.
Retrospective analysis identified multiple related and similar campaigns using the same biotech themes leading to advance fee fraud (AFF) activity in Proofpoint threat data and external sources going back to at least March 2023. Similar related activity following the job fraud model goes back a number of years.
Universities tend to be frequent targets of employment scams. Threat actors may target universities for a variety of reasons. Students are likely more open to flexible, remote work opportunities; international students may not recognize telltale signs of fraudulent emails as well as native English speakers; and rising inflation and cost of education is putting the pinch on students’ finances, making the promise of quick cash more attractive.
Proofpoint has previously published details on employment fraud targeting universities. However, recent activity involving the spoofing of science and technology employers is unique.
Campaign Details
Messages purported to be from a variety of senders, including:
russ@valentbiosciencescareers[.]com
linda@ensyscecareers[.]com
robin@agcbiocareers[.]com
The subjects all pertained to requests for interviews, for example:
- re: interview
- interview invite
- invitation to interview (FRND)
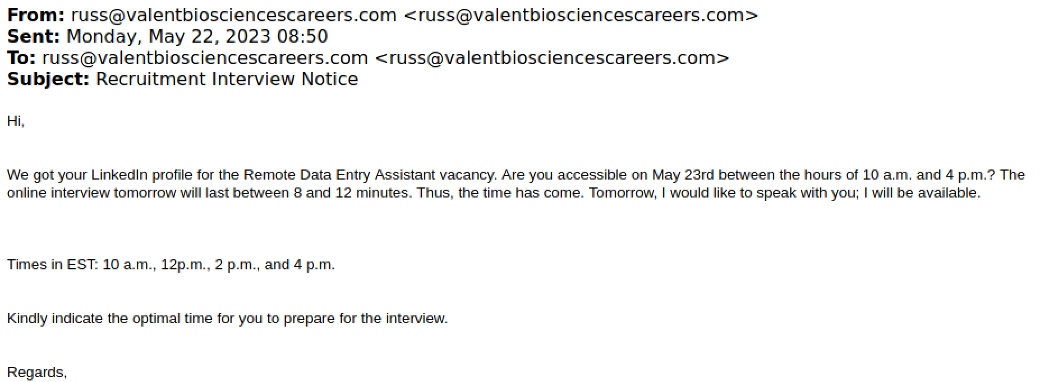
Figure 1: Recruitment interview lure spoofing a biosciences company targeting university students.
The actor created fake domains that purported to belong to legitimate companies, typically adding “careers” to the domain name. The spoofed organizations were typically in biosciences, healthcare, biotechnology, and related industries. Email addresses typically impersonated real people at the companies the actor was attempting to spoof. (In one instance, a LinkedIn user who had been impersonated updated her profile on LinkedIn to warn potential recipients of the scam.)
The messages contained a PDF attachment that purported to contain details of the company and the proposed role. Proofpoint identified multiple PDF samples spoofing various companies. The spoofed PDFs contained the same text content overall, with some details changed including the brand logo, company name, website, and location. These variables were always in bolded text, suggesting the actor used automation to mass create PDFs with different company names to “personalize” the documents.
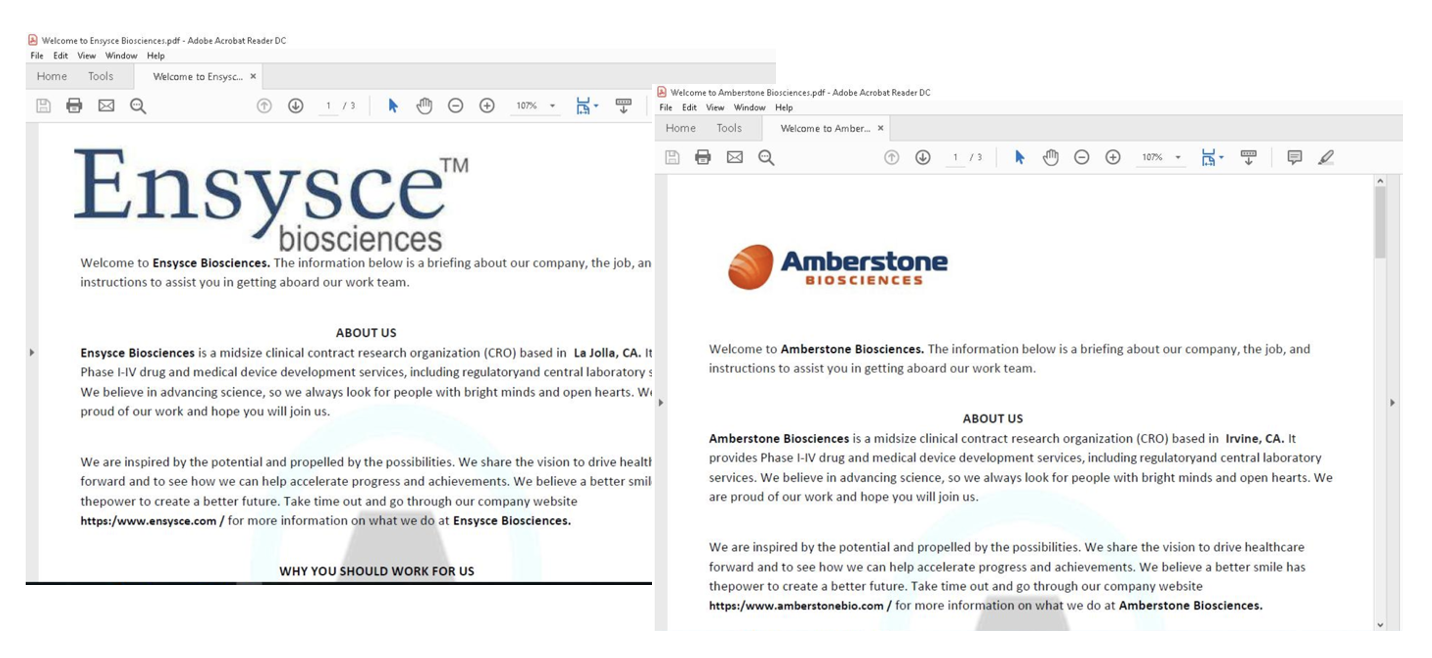
Figure 2: PDF lure examples spoofing science companies that include the same descriptions with different branding, locations, and websites.
Each PDF contained a page listing hardware and software requirements. The total sum of the requirements listed was up to $7,000.
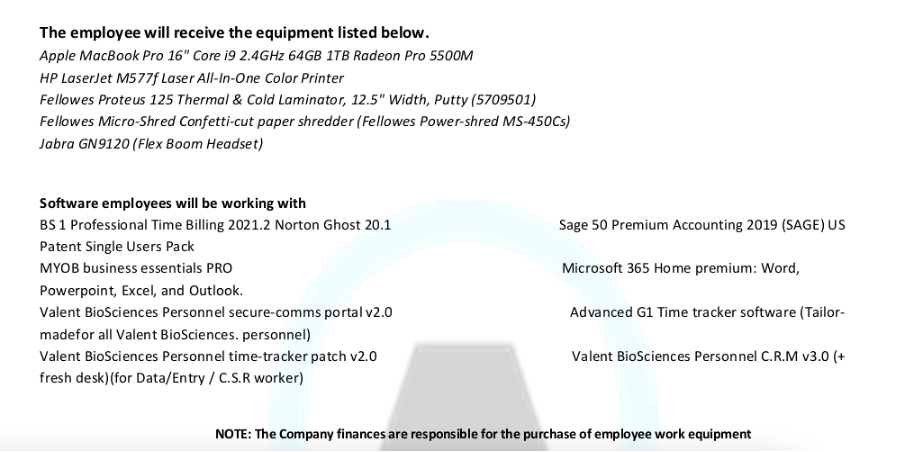
Figure 3: Example hardware and software list provided by the threat actor on a fake job offer.
The actor encourages the recipient to schedule a virtual interview to discuss the position further. While Proofpoint cannot confirm subsequent activity, it is likely they either:
- Ask the individual to pay for the computer and other supplies upfront and tells them they will be reimbursed on their first paycheck
- Provide a fake check that the recipient is supposed to use to buy a computer and products from their "supplier" which then bounces
These are typical behaviors for threat actors perpetrating employment fraud. In some cases, the actor may also ask for cryptocurrency payments to cover the “shipping expenses” of items they are supposed to purchase.
While most of the observed threats associated with this cluster were bioscience, biotechnology, and health themed, Proofpoint has also observed other themes that follow similar tactics, techniques, and procedures.
Conclusion
Based on the observed payloads, victimology, and campaign and message volume, Proofpoint assesses with high confidence that this is a financially motivated cybercriminal activity cluster. This activity is typically preying on university students, especially those who are currently job hunting.
All users should be aware of this type of threat, especially those currently in the job market and engaging with recruiters and human resources representatives. Legitimate employers will never send paychecks before an employee’s first day of work, nor will they ask employees to send money to purchase items prior to work beginning. Key components of fraudulent job offers may include:
- An unexpected job offer received from a freemail account such as Gmail or Hotmail spoofing a legitimate organization
- A job offer from an email address that uses a domain different from the official company website
- Nonexistent or overly simplistic interview questions with little to no information about the job duties
- PDFs or other documentation that includes grammar and spelling mistakes, and includes generic content about the organization and role
- Receiving a “paycheck” almost immediately after beginning a discussion with a sender
- A sender encouraging a recipient to switch to a personal email or chat account to discuss the job opportunity
- Language such as requesting a “quick task” be completed, especially if it involves sending money via mobile applications or Bitcoin addresses
Recent Indicators of Compromise
| Indicator | Description |
|---|---|
| agcbiocareers[.]com |
Spoofed domain used for employment fraud |
|
amicusrxcareers[.]com |
Spoofed domain used for employment fraud |
|
xeneticbiocareers[.]com |
Spoofed domain used for employment fraud |
|
aleralabscareers[.]com |
Spoofed domain used for employment fraud |
|
ensyscecareers[.]com |
Spoofed domain used for employment fraud |
|
amberstonebiocareers[.]com |
Spoofed domain used for employment fraud |
|
cernerenvizacareers[.]com |
Spoofed domain used for employment fraud |
|
patientpointcareers[.]com |
Spoofed domain used for employment fraud |
|
geisingercareer[.]org |
Spoofed domain used for employment fraud |
|
lindybiocareers[.]com |
Spoofed domain used for employment fraud |
|
tbcrtampacareers[.]com |
Spoofed domain used for employment fraud |
|
twinstrandbiocareers[.]com |
Spoofed domain used for employment fraud |
|
catalystcrcareers[.]com |
Spoofed domain used for employment fraud |
|
alamarbiocareers[.]com |
Spoofed domain used for employment fraud |
|
ensyscecareers[.]com |
Spoofed domain used for employment fraud |
|
ventyxbiocareers[.]com |
Spoofed domain used for employment fraud |
|
valentbiosciencescareers[.]com |
Spoofed domain used for employment fraud |
|
cnshealthcaree[.]org |
Spoofed domain used for employment fraud |
|
miradrycareers[.]com |
Spoofed domain used for employment fraud |
|
cocrystalpharmacareers[.]com |
Spoofed domain used for employment fraud |
|
taelifesciencescareers[.]com |
Spoofed domain used for employment fraud |
|
akadeumcareers[.]com |
Spoofed domain used for employment fraud |
|
arborbioscicareers[.]com |
Spoofed domain used for employment fraud |
|
endrainccareers[.]com |
Spoofed domain used for employment fraud |
|
ethos-labscareers[.]com |
Spoofed domain used for employment fraud |
|
irvineclinicalcareers[.]com |
Spoofed domain used for employment fraud |
|
juneaubiosciencescareers[.]com |
Spoofed domain used for employment fraud |
|
nuviewlifesciencescareers[.]com |
Spoofed domain used for employment fraud |
|
quansysbiocareers[.]com |
Spoofed domain used for employment fraud |
|
vialcareers[.]com |
Spoofed domain used for employment fraud |











