Key Findings
- Threat actors use the promise of easy money working from home to collect personal data, steal money, or convince victims to unwillingly participate in illegal activities, such as money laundering.
- The threat, called employment fraud, almost exclusively impacts higher education organisations.
- This threat type has been exacerbated by COVID-19 as more people are open to working from home.
Overview
Proofpoint researchers regularly identify and block employment fraud threats that attempt to entice victims with an easy, work-from-home job. These threats disproportionately impact people at colleges and universities, especially students.
An employment fraud threat occurs when a threat actor attempts to recruit someone under the premise of a legitimate job offer. Job threat actors will craft fraudulent job offers hoping to steal money, personal information, or to recruit an individual to unknowingly comply with illegal activities such as money laundering. Threat actors will typically pose as recruiters or employers and try to entice victims with a variety of opportunities.
There are many variations of job threats including offers for positions as caregivers, mystery shoppers, administrative assistants, models, or rebate processors. Employment fraud is differentiated from other threats such as Advanced Fee Fraud (AFF) due to the job theme and ultimate end result or goal of the attacker. A recipient may end up getting “hired” for a job, role, or function aiding the attacker. With AFF the attacker is hoping to get a small amount money upfront by promising big money later. Employment fraud collects information and recruits unknowing participants into a criminal network. Some may initially start by collecting money allegedly for administrative fees or passport services, but that's typically done to weed out applicants and is not usually the end goal. Additionally, participation in these schemes could result in a victim facing criminal charges for working as a money mule.
COVID-19 has exacerbated job scams as many employers have shifted to remote work, and the concept of working from home is increasingly expected and desirable. In fact, some identified threats will reference COVID-19 as part of the job description or reason for being remote.
Victimology
Of the job themed threats recently identified by Proofpoint, nearly 95% are targeted to educational institutions, mainly colleges and universities. Although most targets are in the United States, threat actors occasionally target European and Australian entities as well. Proofpoint identifies nearly 4,000 of these email threats each day.
Threat actors may target universities for a variety of reasons. Students are likely more open to flexible, remote work opportunities; international students may not recognise tell-tale signs of fraudulent emails as well as native English speakers; and rising inflation and cost of education is putting the pinch on students’ finances, making the promise of quick cash more attractive.
Employment fraud typically impacts individuals, and the results can be costly. According to the FBI’s Internet Crime Complaint center, the average reported loss from job fraud is $3,000. In 2021, U.S. employment fraud losses totalled over $45 million.
Case Study 1
The apparent legitimacy of emails and job opportunities varies – some threat actors use legitimate branding, proper spelling and grammar, and real roles at spoofed organisations. Additionally, the threat actor may use spoofed or compromised email addresses to send the fake recruitment email, especially posing as university career centres or job placement facilitators.
In January 2022, Proofpoint identified emails purporting to recruit university students and staff to an executive personal assistant role at the United Nations Children's Fund (UNICEF).
From: exampleuser@university[.]edu
Subject: Staffs and Students Employment
The messages purported to come from university email addresses and contained a link to a Google Form. The form referenced a COVID-19 relief program.
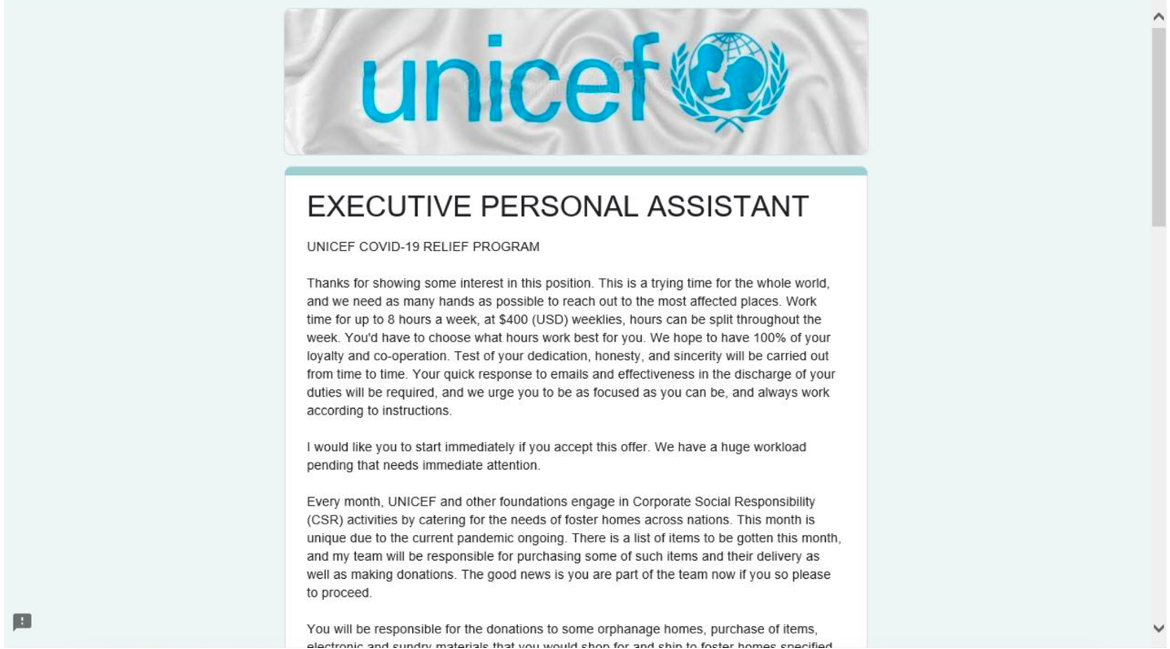
Figure 1: Fake UNICEF job description.
The form requests recipients to fill out their name, alternative email address, phone number, and additional personal details.
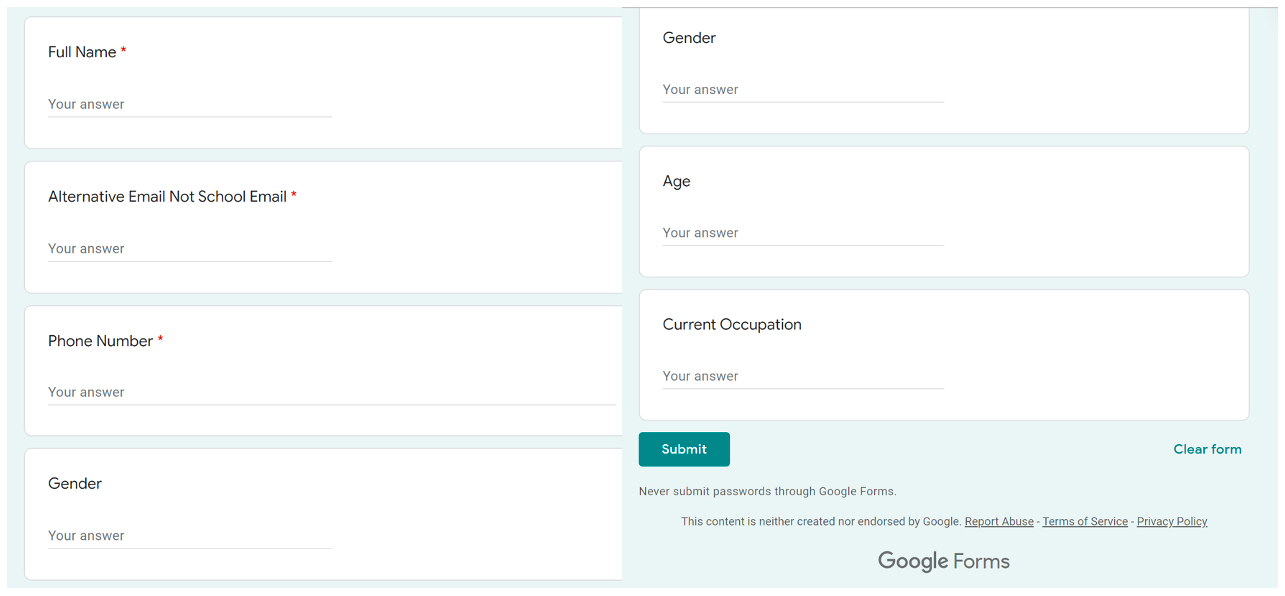
Figure 2: Google Form details.
A Proofpoint researcher completed the form and the threat actor contacted them via Gmail with additional requests for information and detailed the alleged job description.
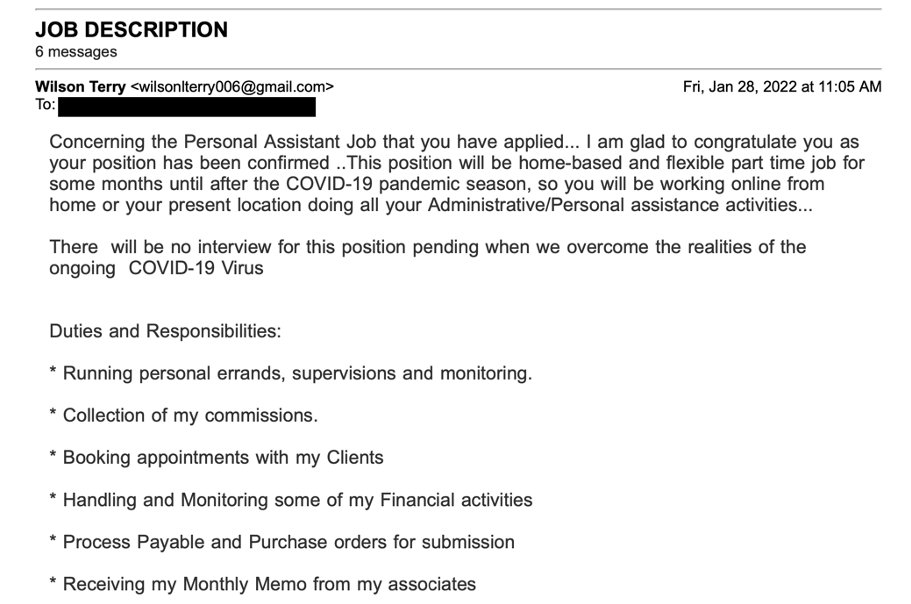
Figure 3: Alleged job duties.
In this case, the threat actor also claimed the assistant position would also include buying and distributing toys for “orphanage homes.” Within the first few messages, the threat actor sent our researcher a fake cashier’s check for $950. The conversation stalled for a few weeks, until the threat actor reached out again, this time with a bigger fraudulent check for $1,950.
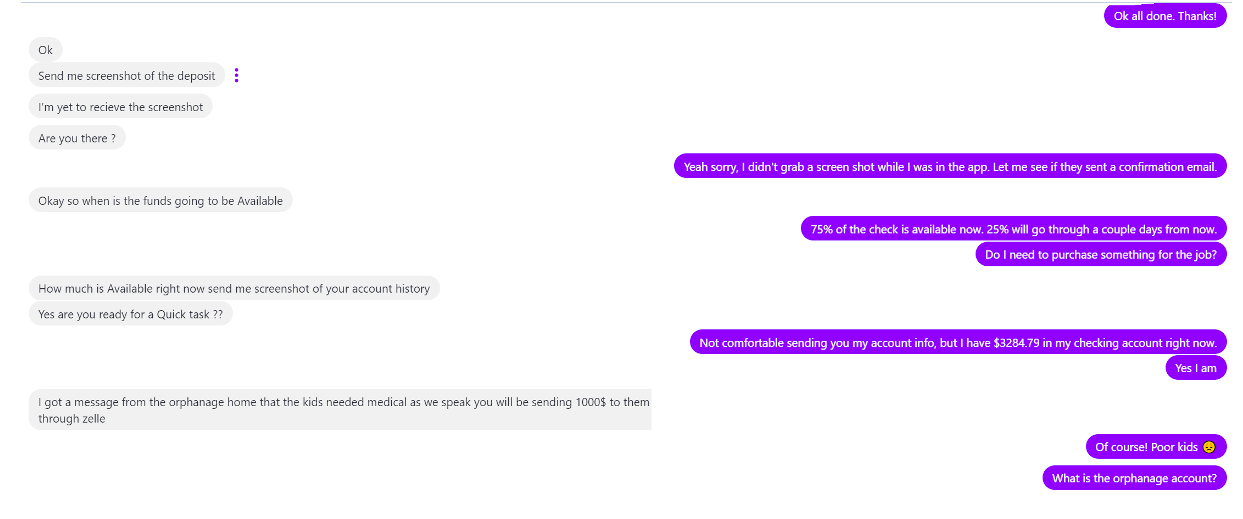
Figure 4: Conversation between the threat actor (grey) and our researcher (purple).
After asking how much was in our researcher’s bank account, the threat actor requested $1,000 be immediately sent to one of the supported “orphanages” to be paid via the Zelle app. Additionally, the threat actor sent our researcher a Bitcoin address for follow up payments.
In this case, the idea is the recipient would receive their $950 “salary” and the extra money would be sent on – but the check is illegitimate, so the victim would be sending their own money to the threat actor.
UNICEF is aware of threat actors spoofing its organisation in job fraud email lures. In January 2022, the organisation published an advisory warning people to be aware of fraudulent activity spoofing UNICEF and shared via email, social media, and online job boards.
Case Study 2
In another recent campaign, Proofpoint observed a threat actor pretending to recruit college students for an alleged modelling job. The messages read:
“We require the service of a model for a 3-day shoot. Our scouts found your profile on Instagram in which you have been properly reviewed, If youre interested kindly get back to us via email for more details and interview. We hope to hear from you soon”
Our researcher contacted the threat actor and a conversation started over the Hangouts chat app and Gmail. The threat actor impersonated fast fashion brands Zaful and Fashion Nova. Using these organisations in lures might be compelling for students, especially those interested in women’s fashion – the two popular fashion brands with large Instagram followings regularly feature user generated content to market their products to millions of followers.
Before engaging via chat, the threat actor sent over a “contract” to further convince the recipient the job offer was genuine.
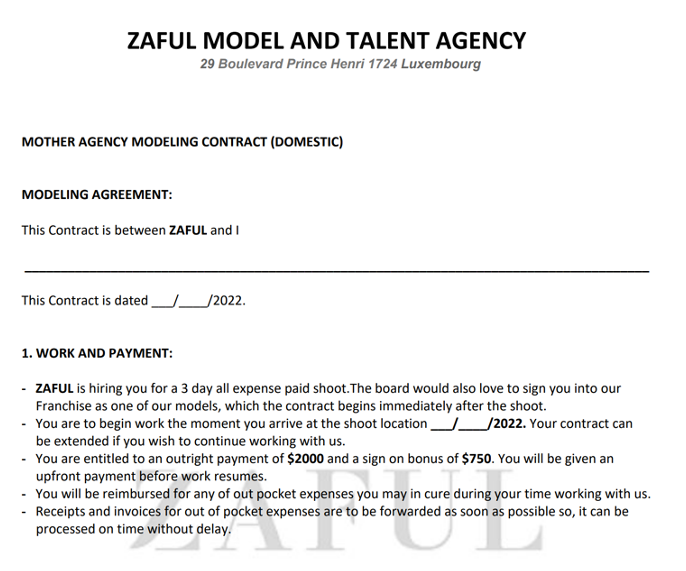
Figure 5: Fake Zaful modelling contract.
The threat actors then began a conversation with our researcher purporting to plan a photoshoot in Los Angeles, and requested they select outfits and coordinate scheduling. The threat actor emailed a fake check for $4,950 and requested $100 in cryptocurrency to cover “shipping” of the items that would be used in the photoshoot. (Sometimes checks are sent directly to the victim’s house to further legitimise the crime).

Figure 6: Fake paycheck sent by the threat actor.
In this case, the threat actor spent a lot of time and effort communicating with our researcher and answering questions about the supposed job opportunity. Proofpoint assesses the amount of effort in this specific campaign – including documentation and communication – is greater than typically observed employment fraud threats.
Conclusion
Users should be aware of these types of job scams, especially job hunters and students and faculty at post-secondary educational institutions. Legitimate employers will never send paychecks before an employee’s first day of work, nor will they ask employees to send money to purchase items prior to work beginning. Key components of fraudulent job offers may include:
- An unexpected job offer received from a freemail account such as Gmail or Hotmail spoofing a legitimate organisation
- Non-existent or overly simplistic interview questions with little to no information about the job duties
- Receiving a “paycheck” almost immediately after beginning a discussion with a sender
- A sender encouraging a recipient to switch to a personal email or chat account to discuss the job opportunity
- Language such as requesting a “quick task” be completed, especially if it involves sending money via mobile applications or Bitcoin addresses











