At Proofpoint, we offer a people-centric security approach in response to how external attackers are targeting employees within a company. Innovations such as the Very Attacked People Dashboard, Company-Level Attack Index and, most recently announced at our user conference, Protect 2020, the Nexus People Risk Explorer are the result of this perspective. These products not only provide our customers with insight into who is being attacked but also empower them to apply adaptive controls on top targets.
We wanted to apply the same people-centric approach to solving for data loss and provide original ways for our customers to prevent this problem, which continues to be a major pain point for many organizations around the world.
Today at Protect 2020, we are excited to announce our new people-centric Enterprise DLP Platform. This platform brings together the Proofpoint cloud, email and endpoint DLP solutions. All content, user behavior and threat telemetry are combined across channels in a unified investigations interface to help organizations identify and respond quickly to data risks posed by negligent, compromised and malicious users.
Understanding the “People” in People-Centric DLP
The “people” involved in data loss at a company fall into three main categories:
- The Negligent User: This is the employee who inadvertently makes a mistake and violates a compliance requirement. For example, by mistake, they may send personal identifiable information (PII) such as health records or financial data to an external, untrusted source.
- The Compromised User: This employee is unaware they have been targeted by an attacker due to their privileged access to information. Attackers leverage this access to exfiltrate data for financial or political gain.
- The Malicious User: this is the “pre-meditated” employee who decides to pro-actively undermine the sanctity of corporate data by leaking it out for personal gain.
Too long have DLP products been relegated to a checkbox compliance product addressing just the “negligent” user. A comprehensive DLP solution must successfully address the risks posed by all three of these at-risk users. Here’s how Proofpoint’s Enterprise DLP solution does just that.
How Proofpoint Employees a Telemetric Approach to Mitigate User Risk
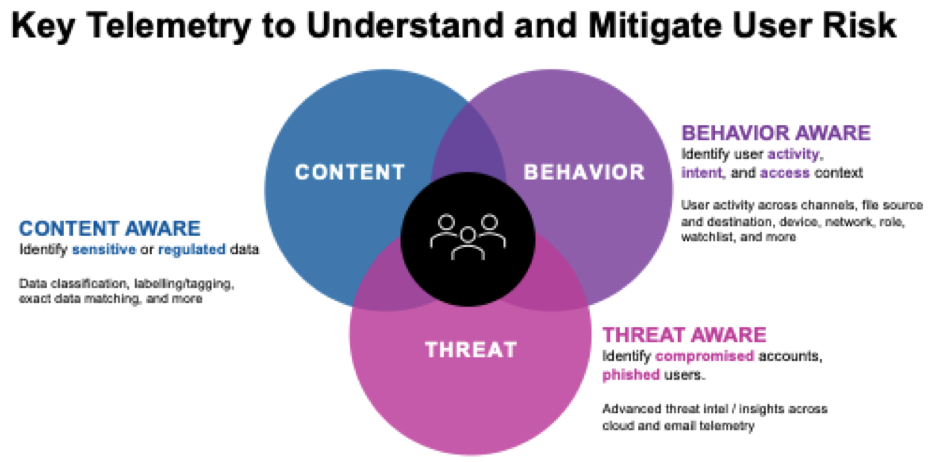
In the last golden age of DLP solutions, the major technological breakthrough was understanding content. Knowing what was within an outgoing email or file was a big step forward from the time before when most organizations were in the dark about what was leaving their organization.
However, as with any golden age, many promises were unfulfilled, and many people were left out. Specifically, the “compromised” and “malicious” users.
To address the risks posed by these two user groups, content alone is not sufficient; additional telemetry is needed to ascertain, for example, that there is data exfiltration because of a compromised user account. To protect against compromised users, organizations must be “threat aware” across the various channels such as email and cloud. With that knowledge, organizations can discover that an O365 account compromise through a state-sponsored actor is resulting in the observed data exfiltration.
To address the “malicious user”, organizations must employ yet another telemetry: behavioral awareness. By weaving together user actions across the different channels of data loss, a pattern of behavior can emerge that correlates to our malicious user. Experience has taught us that bad people act in a certain way. Behavioral awareness allows us to understand if an employee is downloading copious amounts of files from OneDrive and then proceeding to install a Dropbox client on the same machine.
Learn More about People-Centric DLP at Proofpoint
New technological breakthroughs allow us to tackle problems in new ways. At Proofpoint, we’re using technologies such as cloud first, user behavior awareness, global threat intelligence, lightweight endpoint agents and security awareness training, which are all very important building blocks to tackle the ongoing concern and unfulfilled promise of DLP. But what is more important is how these different technologies are strung together to ensure the same innovation is delivered. At Proofpoint, “people-centric enterprise DLP” is that focal point.
If you are interested to learn more about our people-centric approach to Enterprise DLP, please reach out to us here.











