Table of Contents
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard for implementing cybersecurity across the defence industrial base. It’s a framework designed to protect sensitive defence information housed within contractor systems and networks, reinforcing the security of the supply chain that underpins U.S. national security.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
What Is CMMC?
CMMC, or Cybersecurity Maturity Model Certification, is a tiered cybersecurity programme mandated by the Department of Defense (DoD) to safeguard against cyber threats within its supply chain. CMMC is a certification process designed to ensure protection over sensitive data that resides on contractors’ networks.
Increased cyber threats that compromised defence data on contractor-operated systems prompted the creation of CMMC. To counteract this vulnerability, the DoD developed CMMC as an amalgamation of various cybersecurity standards and best practices—including NIST SP 800-171 and FAR clause 52.204-21—while also incorporating input from industry experts and academic institutions.
With this initiative, the DoD ensures that all contractors meet a benchmarked level of cybersecurity maturity before being awarded government contracts involving Controlled Unclassified Information (CUI). By standardising these requirements across all levels of its supply chain, CMMC serves not just as a compliance measure but also as an assurance framework for securing critical assets essential to U.S. national security interests at home and abroad.
Who Needs CMMC Compliance and Why Is It Important?
CMMC compliance is essential for a specific group in the defence sector. Organisations contracting with the DoD, including subcontractors, must meet CMMC requirements.
This spans a wide array of companies—from those providing direct product support to defence services to suppliers further down the supply chain. Essentially, if an entity is part of the Defense Industrial Base (DIB) and handles CUI, investing in CMMC compliance becomes mandatory.
The importance of CMMC cannot be overstated for several reasons:
- Protection against cyber threats: The rise in cyber-attacks targeting sensitive government data necessitates robust security protocols. By adhering to CMMC standards, organisations can better protect against espionage, theft, and sabotage by malicious actors.
- Assurance across supply chain: It ensures all members within the DoD’s supply chain maintain consistent cybersecurity practices—establishing trust throughout every level by ensuring each link in the chain takes information protection seriously.
- Competitive advantage: For businesses seeking DoD contracts, achieving certification can serve as a differentiator from competitors who may not meet required levels—a key consideration when submitting a proposal for a coveted defence project.
- Regulatory compliance: Beyond securing data lies a legal obligation. Failure to comply with CMMC compliance regulations could result in fines, penalties, or loss of eligibility for future contracting opportunities, effectively barring non-compliant entities from participation in critical defence projects.
CMMC compliance is more than just meeting regulatory requirements. It’s a demonstration of an organisation’s commitment to safeguarding national security. By adhering to these stringent cybersecurity measures, companies enhance their resilience against vulnerabilities and contribute to the continuity and integrity of operations crucial for the wider defence space. Compliance strengthens the military’s collective efforts to protect the vital systems upon which modern society relies.
What Is CMMC 2.0?
CMMC 2.0 is the updated version of the original Cybersecurity Maturity Model Certification (CMMC) programme rolled out by the DoD. This iteration has been introduced to refine and streamline cybersecurity requirements, making it more accessible for contractors in the defence supply chain while still upholding a high standard of security.
Several key objectives drove the development of CMMC 2.0:
- Simplification: The DoD aimed to reduce complexity in achieving compliance by consolidating five maturity levels into three, focusing on essential cybersecurity practices.
- Increased clarity: It provides clearer guidance around certification requirements that improves understanding and consistency across all companies involved with DoD contracts.
- Alignment with existing standards: CMMC 2.0 aligns more closely with well-established standards outlined in FAR regulations, helping organisations integrate their existing compliance efforts into this new model without redundant or conflicting measures.
- Efficient resource utilisation: By streamlining assessment procedures and documentation, CMMC 2.0 enables quicker certification processes—a change especially beneficial for small and medium-sized businesses in the defence industry.
CMMC 2.0 is designed to strengthen cybersecurity defences while also promoting fairness and accessibility within the defence supply chain. The updates facilitate a more equitable environment where companies of all sizes can protect sensitive information effectively without excessive strain on their resources.
This table provides a clear overview of the changes and differences between CMMC 1.0 and CMMC 2.0.
Feature
CMMC 1.0
CMMC 2.0
Purpose
Enhance cybersecurity standards within the Defence Industrial Base
Simplify the framework and strengthen cybersecurity requirements
Levels
5 levels (Basic to Advanced)
Streamlined to 3 levels (Foundational, Advanced, Expert)
Assessment Requirements
All levels required third-party assessments or self-assessments depending on the level
Levels 1 and 2 primarily require self-assessments; Level 3 requires government-led assessments
Certification Process
Conducted by Certified Third-Party Assessor Organisations (C3PAOs) or self-assessment for lower levels
Self-assessment with annual affirmations by company executives for Levels 1 and 2; C3PAO or government assessment for Level 3
Focus Areas
Broad set of cybersecurity practices across all levels
Streamlined focus with prioritised practices and processes, more aligned with NIST SP 800-171
Cost
Potentially high due to extensive third-party assessments
Reduced cost for lower levels due to self-assessment option
Regulatory Alignment
Original CMMC practices plus additional requirements
Closer alignment with NIST SP 800-171, reducing complexity for contractors
Flexibility and Scalability
Less flexible, one-size-fits-all approach
Greater flexibility and scalability, tailored to the size and complexity of organisations
Implementation Timeline
Immediate for contracts following the introduction of CMMC 1.0
Phased implementation, allowing organisations time to adjust to the new requirements
Maturity Process
Process maturity integral at higher levels
Focus shifted more towards the implementation of practices rather than process maturity
Feature
Purpose
CMMC 1.0
Enhance cybersecurity standards within the Defence Industrial Base
CMMC 2.0
Simplify the framework and strengthen cybersecurity requirements
Feature
Levels
CMMC 1.0
5 levels (Basic to Advanced)
CMMC 2.0
Streamlined to 3 levels (Foundational, Advanced, Expert)
Feature
Assessment Requirements
CMMC 1.0
All levels required third-party assessments or self-assessments depending on the level
CMMC 2.0
Levels 1 and 2 primarily require self-assessments; Level 3 requires government-led assessments
Feature
Certification Process
CMMC 1.0
Conducted by Certified Third-Party Assessor Organisations (C3PAOs) or self-assessment for lower levels
CMMC 2.0
Self-assessment with annual affirmations by company executives for Levels 1 and 2; C3PAO or government assessment for Level 3
Feature
Focus Areas
CMMC 1.0
Broad set of cybersecurity practices across all levels
CMMC 2.0
Streamlined focus with prioritised practices and processes, more aligned with NIST SP 800-171
Feature
Cost
CMMC 1.0
Potentially high due to extensive third-party assessments
CMMC 2.0
Reduced cost for lower levels due to self-assessment option
Feature
Regulatory Alignment
CMMC 1.0
Original CMMC practices plus additional requirements
CMMC 2.0
Closer alignment with NIST SP 800-171, reducing complexity for contractors
Feature
Flexibility and Scalability
CMMC 1.0
Less flexible, one-size-fits-all approach
CMMC 2.0
Greater flexibility and scalability, tailored to the size and complexity of organisations
Feature
Implementation Timeline
CMMC 1.0
Immediate for contracts following the introduction of CMMC 1.0
CMMC 2.0
Phased implementation, allowing organisations time to adjust to the new requirements
Feature
Maturity Process
CMMC 1.0
Process maturity integral at higher levels
CMMC 2.0
Focus shifted more towards the implementation of practices rather than process maturity
CMMC 2.0 reflects a dynamic approach that caters to the modern challenges of digital security, ensuring that our nation’s defence infrastructure remains robust against today’s threats.
Achieving CMMC Compliance
To achieve CMMC compliance, organisations must understand and meet the criteria outlined in one of three maturity levels—each corresponding to a set of cybersecurity practices with increasing complexity and rigour. These tiers are grounded in widely accepted NIST (National Institute of Standards and Technology) standards.
Level 1 – Foundational:
- At this initial level, an organisation must implement basic cyber hygiene practices.
- It involves 17 controls primarily derived from FAR clause 52.204-21 focusing on essential safeguarding measures for federal contract information (FCI).
- This tier is a starting point for small companies or subcontractors new to the DoD supply chain.
Level 2 – Advanced:
- This intermediate stage requires establishing and documenting standardised processes based on NIST SP 800-171 rev2 guidelines.
- This level emphasises protecting CUI, with requirements extending beyond foundational cybersecurity protocols into more robust protection mechanisms against threats.
- Companies at this level should have established policies governing their cybersecurity efforts while actively managing their data protection strategies.
Level 3 – Expert:
- At the pinnacle of CMMC, Level 3 requires organisations to implement advanced cybersecurity practices to protect against sophisticated threats.
- This level builds upon NIST SP 800-171 rev2 by incorporating additional controls from sources like NIST SP 800-172, ensuring protection against Advanced Persistent Threats (APTs).
- Companies at this tier must show that they can not only establish but also actively manage and adapt their cybersecurity posture in response to evolving tactics and techniques used by cyber adversaries.
- Certification at this expert level indicates a company’s capability to provide the highest security standard for DoD projects requiring uncompromised defence mechanisms.
These CMMC levels are widely accepted because they are based on established NIST cybersecurity standards recognised as comprehensive and robust frameworks for protecting sensitive government information.
Who Needs to Obtain a CMMC Certificate?
The requirement for obtaining a CMMC certificate impacts a specific group in the defence sector:
- Defence contractors: Any organisation, large or small, that intends to do business with the DoD by directly bidding on contracts.
- Subcontractors: Companies further down the supply chain that may not contract directly with the DoD but contribute to fulfilling defence contracts must also be certified. Subcontractors include suppliers and service providers who handle or produce components and systems for primary contractors.
- Vendors handling CUI: If an entity deals with information that federal standards deem sensitive—information requiring safeguarding but not classified—certification is required because the data is critical to national security.
In essence, any company playing any role in providing goods or services within the Defence Industrial Base, especially those dealing with sensitive unclassified information, needs to pursue and maintain an appropriate level of CMMC certification relevant to their work’s nature and scope.
How Proofpoint Can Help
Embracing the complexities of CMMC compliance can be daunting for organisations at any level in the defence industry. However, Proofpoint is an invaluable ally in this journey by providing solutions to help organisations with CMMC compliance. Proofpoint has tailored Government Threat Protection Bundles for customers who need to comply with CMMC. Proofpoint can help customers with CMMC compliance with several product sets of Fedramp hosted cloud solutions, US commercial and on-premise products. The products and blog below go into more detail around our solutions and how they support compliance and security for Organisations Seeking Compliance (OSCs)
- Proofpoint’s Identity Threat Detection & Response platform helps reveal and safeguard attack pathways that can be exploited by threat actors, aiding in achieving cyber resilience for CMMC Level 3 compliance.
- Additionally, Proofpoint’s email filtering and secure email gateway solutions can assist in meeting CMMC requirements, such as detecting or blocking malicious emails and employing FIPS 140-2 validated encryption for data at rest and during transmission. Our SEG is Fedramp Moderate certified, TAP is Fedramp Moderate and our Email DLP module is also Fedramp moderate certified.
- Proofpoint Zenguide offers numerous options for training, awareness and curriculum for government customers. It supports the Awareness and Training (AT) domain for Level 2 and Level 3 certifications for CMMC. Read more about how it can help.
- Proofpoint can provide agencies with a critical edge in their efforts to defend data from risky users and detect real-time identity threats. Products to help with these challenges include Proofpoint Insider Threat Management and Data Loss Prevention Solutions.
- Proofpoint helps you mitigate the risk of impersonation abuse with a holistic, multilayered approach. With Proofpoint Impersonation Protection, you can protect your organisation’s communications from impersonation threats. Stop attackers from impersonating your brand, detect and defend against risky suppliers, including compromised supplier accounts, and secure user and application emails so that they can be trusted with our Fedramp application traffic solution.
- Normalyze our Data Security and Posture Management (DSPM) solution also has specific mapping to CMMC compliance. DSPM continuously identifies and highlights data privacy gaps against over 500 compliance frameworks including CMMC, NIST, HIPAA, SOC2 and others.
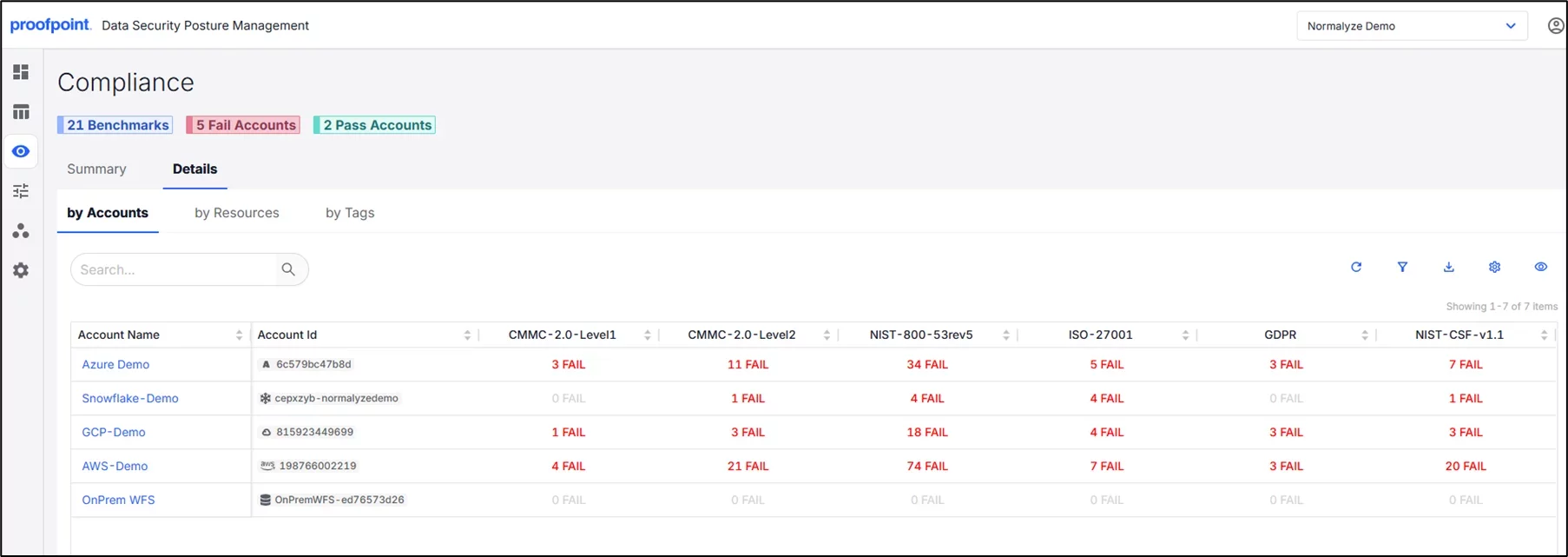
DSPM dashboard screenshot showing compliance mapping to CMMC, NIST and ISO frameworks
These capabilities make Proofpoint a valuable partner for organisations seeking to comply with CMMC requirements.
Learn more
For more information about our leading products for the federal market, see:
- Proofpoint Solutions for Federal Agencies
- Threat Intelligence Solutions for the Federal Government
- https://www.proofpoint.com/uk/solutions/federal
To learn more about the scope of available cybersecurity solutions, contact Proofpoint.











