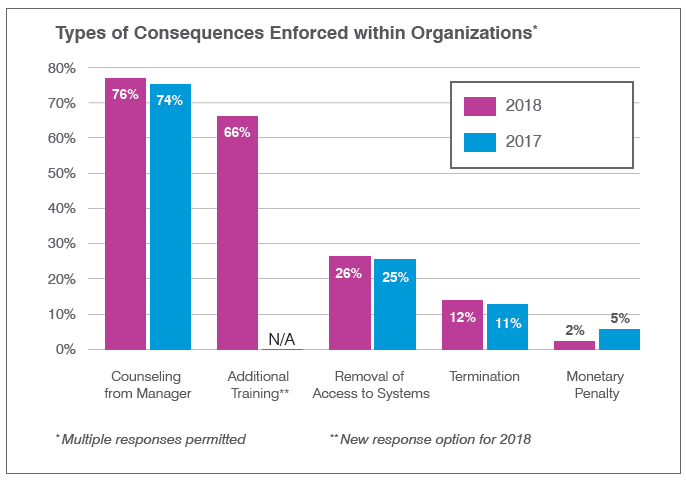
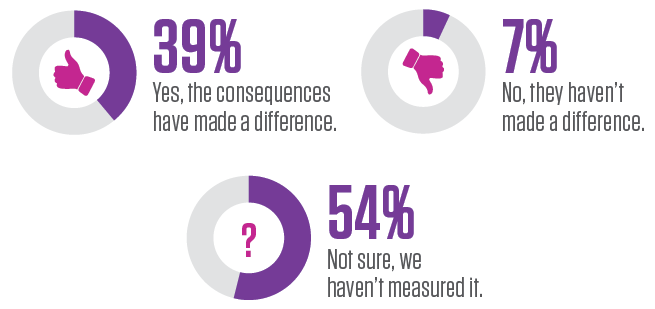
Carrot vs. Stick: Simply a Case of Perception?
Levine — a former Fortune 500 CISO and former non-believer in security awareness training — has strong opinions about the use of negative reinforcement techniques, which he shared in our recent State of the Phish SecureWorld web conference. “Failing tests is not the same thing as refusing to learn,” he said. “Any one of us in the right conditions — or as the case may be, the wrong conditions — could fall for a phishing scam.”
Levine is passionate about this topic, and his advocacy for “more carrot than stick” within organizations extends even to “kinder, gentler” ramifications like counseling and additional training (the latter of which he said is “always good” for users who are having difficulty grasping new skills). He advised that end users’ perceptions will be heavily influenced by policies and communications — and by the way organizations position user “failures.”
“Bad news travels much faster than good news; bad news will be discussed at the water cooler. And bad news for an individual can become bad news for an entire organization,” Levine cautioned. When users worry about being slapped on the wrist for making mistakes during the learning process, they could become nervous about all of their interactions with email, he warned, which could have a negative impact on the flow of business.
Levine says that infosec teams should focus on creating a program that “builds a bridge” to users, rather than expecting users to cross the bridge on their own. “We should reward users who do well, and we should help users who don’t do well along the way,” he said. “Reach out and communicate, with help, not hassle, to mobilize the workforce for the good fight.”
For more insights and advice, listen to the on-demand replay of the webinar, which highlights several key findings from our State of the Phish Report. CPE credits are available.