Business Email Compromise and Email Account Compromise Are Costing Businesses Billions
Business Email Compromise (BEC) and Email Account Compromise (EAC) afflict businesses of all sizes across every industry. More money is lost to this type of attack than any other cybercriminal activity. The FBI reported that from June 2016 to June 2019, companies reported $26.2B in losses. And in 2019 alone, BEC scams accounted for more than half of all cybercrime losses—an estimated $1.77B. The average loss per BEC incident in 2019 was $74,723.
BEC/EAC are People-Centric Threats
BEC/EAC attacks rely on tricking a person into believing the criminal is someone they are not. What makes BEC/EAC attacks so effective at evading traditional email defenses is the fact that they don’t utilize traditional malware-based methods. Instead BEC/EAC attacks are crafted by people to deceive people.
Criminals use a variety of credential phishing, account compromise, identity deception and social engineering techniques to trick people into giving up confidential information or activate an unauthorized transfer of funds.
Types of BEC and EAC Attacks
While the end goal of BEC/EAC attacks are the same—to steal your organization’s money—there are several different attack types or scams.
Here are the four current BEC/EAC attack types:
1. Payroll diversion:
In a payroll diversion scam, a criminal sends a fraudulent email to HR or payroll employees requesting to change or update direct deposit information from a legitimate employee bank account to the fraudster’s account or a pre-paid card account. The latest FBI data shows that the dollars lost as a result of payroll diversion scams have increased more than 815% between Jan 1, 2018 and Jun 30, 2019.
2. Gift card scam:
In this attack, the criminal poses as a supervisor or employee with authority and sends an urgent email requesting assistance to purchase gift cards for staff or clients. The email asks for serial numbers so s/he can email them out right away.
3. Supplier invoicing:
When implementing this attack type, a criminal will impersonate a vendor your company regularly does business with and send a request to update bank information for payment of outstanding invoices. When you consider the large dollar amounts often associated with supplier invoices, this type of scam leads to the biggest losses.
4. M&A fraud:
M&A fraud involves the fraudster pretending to be an executive of the victim company (either using impersonation or a compromised account). He or she requests that funds be transferred to a given 3rd party. For example, the email might say something like “We’re buying Company X and we need to make a payment or we risk losing the deal.”
Four Key BEC/EAC Tactics
Proofpoint detects, analyzes and blocks millions of these BEC/EAC attacks every day. In doing so, we’ve observed that across each BEC/EAC attack type, fraudsters leverage four key tactics:
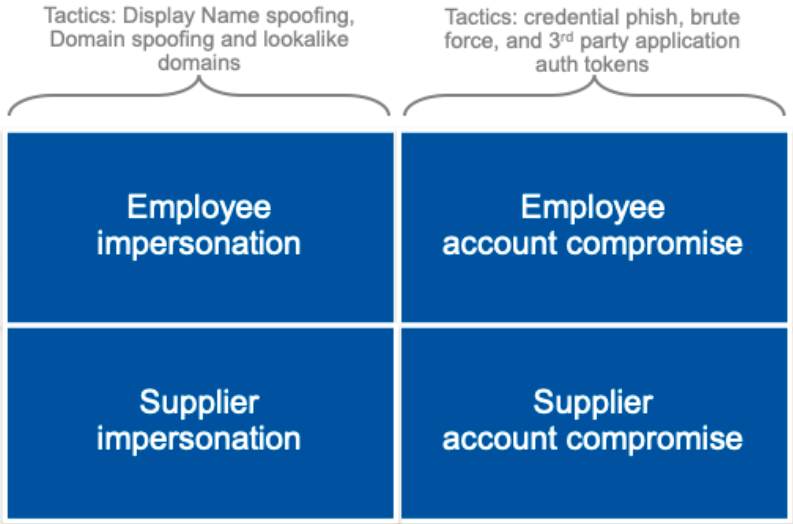
Impersonation in email happens by exploiting technical and human vulnerabilities. Not only are people wired to ignore subtle textual differences, thereby making lookalike domains a useful tool in BEC/EAC attacks, but also Simple Mail Transfer Protocol (SMTP) is, by its own admission, “inherently insecure” and therefore prone to both Display Name and domain spoofing.
Compromised accounts are priceless to threat actors. They afford them the ability to conduct extensive reconnaissance, and fraudulent emails sent from that account will be almost indistinguishable from legitimate emails. They will bear the same Display Name and email address; they will be sent from the same mail server; and they will pass all the email authentication protocols (SPF , DKIM and DMARC). Accounts are compromised using stolen credentials (often obtained via phishing), 3rd party application auth tokens or brute force attacks.
While every BEC/EAC attack can be mapped to at least one of the four tactics, we are seeing more and more attacks that span multiple tactics in a single attempt to steal money. For example:
· The target company’s domain is spoofed (employee impersonation) to steal credentials that gives the threat actor access to an employee’s account (employee account compromise) from which they can then conduct payroll diversion or gift carding scams.
· Cybercriminals use stolen credentials to access the account of a supplier (supplier account compromise) from which they initiate or intercept discussions with the target company’s Accounts Payable team before switching the conversation (very often by introducing the new email addresses into the Cc field) to a lookalike domain of that supplier (supplier impersonation) from which a demand for payment is made.
Siloed Defense Won’t Solve the Multifaceted BEC/EAC Problem
Because cybercriminals employ multiple tactics and combinations of impersonation and account compromise, defending against one or two of these tactics is insufficient to address the threat as a whole.
And legacy email security providers that rely only on reputation and malware sandboxing won’t help when good/legitimate email accounts are being used to socially engineer the theft of money by sending payload-less (e.g. text only) messages.
You need an email security solution that invests in detecting and stopping impersonation, account compromise, credential phishing and social engineering. And let’s not forget about training your users to spot and report on these attacks/tactics too.
To build such a solution, email security providers need access to the right data sources: email traffic, cloud account activity, user data and domain data. With that information, threat analysts and machine learning models can detect the use of multiple tactics in these types of attacks and implement integrated, adaptive controls across the attack surface of email, cloud accounts and people.
Learn how to protect your organization
Stay tuned for more posts in this series which will dive into specific BEC and EAC attack types, what tactics were used, and how you can stop them.
To learn how to implement a holistic security solution to combat multi-faceted attacks right now, download our Unmasking BEC and EAC eBook.











