Cloud account compromise is one of the top three concerns for today’s CISOs. That’s for good reason, too. In 2022, Proofpoint threat intelligence shows that 62% of all organizations were compromised via account takeover. And nearly one-third (32%) of the hijacked accounts used multifactor authentication (MFA) for protection.
These findings make it clear that MFA no longer provides “silver bullet” protection for cloud accounts. Want proof? Just consider the rise of EvilProxy, which is now the most prominent MFA phishing-as-a-service provider.
Threat actors use these attacks to gain control of employee accounts. But they don’t stop there. Account takeovers are often one of the first steps in a much larger series of events. Dubbed the “cyber attack chain,” these events start with user compromise and progress to privilege escalation and lateral movement across the network. Later, they advance to privilege abuse, data theft and more.
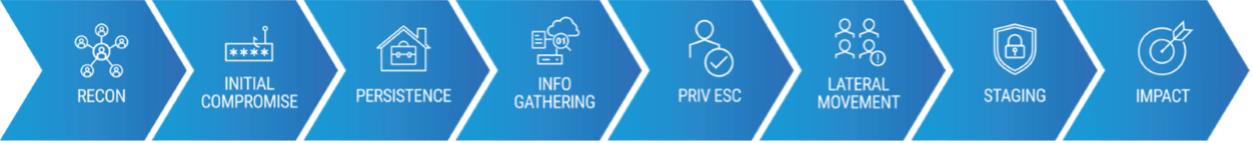
Steps in the attack chain.
The key to breaking the attack chain is to identify compromised accounts and automate remediation. Unfortunately, the process is often fraught with problems that can expose businesses to even more risk.
Take, for example, behavioral analytics. While it can be used to detect account takeovers, it often generates an overwhelming number of false alerts and undermines the user experience. Or let’s say a cloud account has been compromised. You can’t simply generate a new password and be done. Once an attacker has gotten inside your cloud environment, they can manipulate third-party apps and gain undetected persistent access to the account—and wage attacks at will.
A more effective way to detect account takeovers
Proofpoint TAP Account Takeover helps businesses defend their email and cloud environments from threats, including:
- Phishing
- Brute-force attacks
- Business email compromise (BEC)
- Malware
- Data exfiltration
- Attackers’ persistent access
This solution provides insight into what types of threats are targeting email accounts. And, if an attacker manages to gain access to an account, it gives you the tools to take corrective action to protect that account.
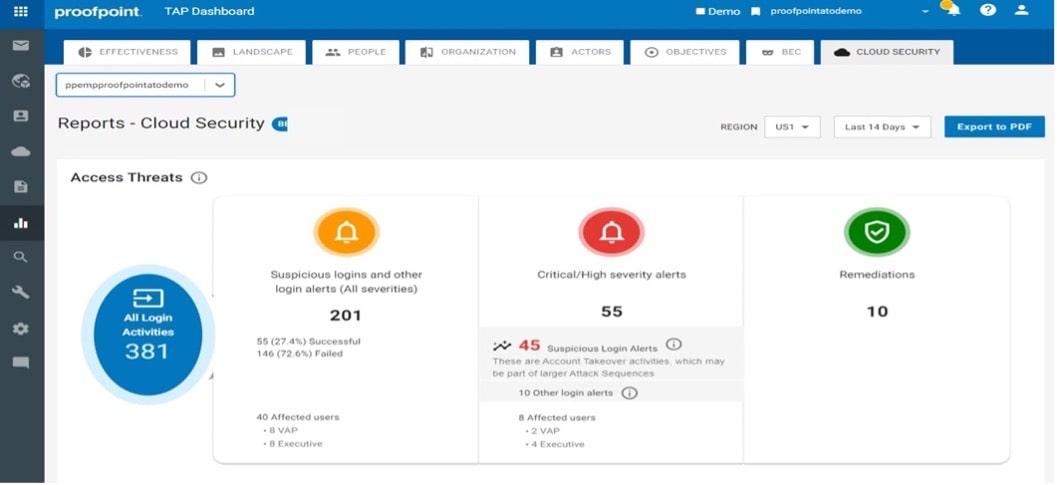
With the Access Threats report, you can see suspicious logins and automated remediations at a glance.
Proofpoint TAP Account Takeover helps security teams to:
- Detect compromised email accounts with automated alerts
- Protect against MFA bypass
- Accelerate and unify email threat investigations of account takeover attacks and post-compromise cloud activities
- Remediate accounts, malicious mailbox rule changes and manipulations of third-party apps
- Prevent data exfiltration across email and cloud environments
Increase visibility
TAP Account Takeover is very effective at finding malicious events across the email attack chain. That’s because it correlates threat intelligence with artificial intelligence, machine learning (AI/ML) and behavioral analytics to get deep insights into what’s going on behind the scenes. This unique approach means you can see who is being attacked and how. It also reduces false positives and gives you greater confidence in account takeover verdicts.
An attack sequence report provides you with an overview of the accounts that are at risk for takeover. It also shows the number of both the accounts that are impacted and malicious activities—from pre-access to post-account access. You can see how an attacker accessed the account and what they did after logging in. Post-access suspicious activities include:
- Uploading malicious files
- Changing mailbox rules to obfuscate their presence in your system
- Sending suspicious mail
- Manipulating third-party apps
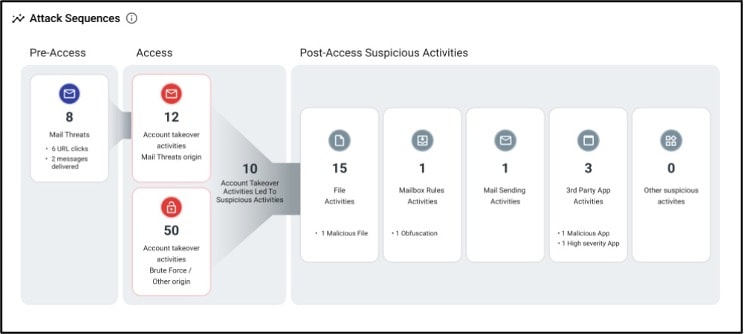
The Attack Sequences report shows you how an attacker accessed the account and what they did after logging in.
Accelerate investigations
TAP Account Takeover helps security analysts quickly understand what happened and how they can limit risk. Account takeover information is integrated with the Proofpoint Targeted Attack Protection investigation system and process. You get the same correlated people-centric insights and threat intelligence that is provided in the TAP dashboard.
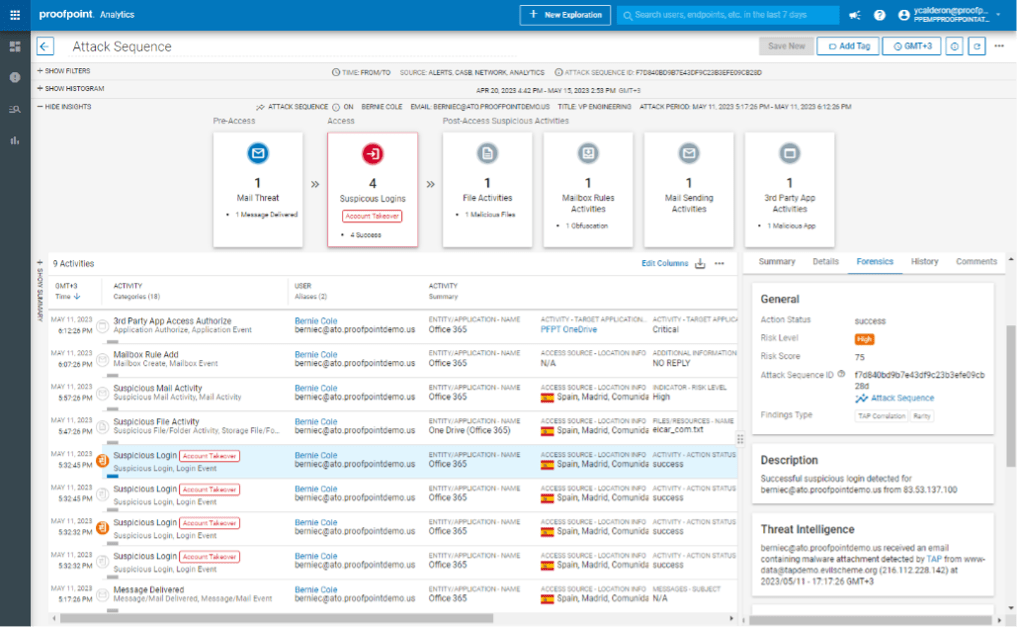
An activity timeline provides insights about compromised accounts.
All data in the Proofpoint TAP Account Takeover solution is clickable, so analysts can drill down and investigate each incident to determine:
- Whether the user is a Very Attacked Person (VAP™)
- How the account was compromised
- Where the attacker was located
- Which other users were impacted by similar threats
Automate responses
TAP Account Takeover can detect when an attacker changes mailbox rules to conceal their identity before to staging a BEC attack. It can also detect when third-party apps are being controlled by attackers.
In both these events, TAP Account Takeover automatically responds, reducing attackers’ dwell time in compromised accounts and revoking their access to apps. This limits the damage to your organization.
Later, if you investigate and find other malicious activity, you can move fast to remediate any other compromised accounts. You can also limit data loss and delete the malicious files inserted into your environment.
Learn more
Proofpoint TAP Account Takeover helps you to defend cloud email accounts against threats. It is licensed as an add-on to Proofpoint Targeted Attack Protection and is now available for purchase.
For more information, see the Targeted Attack Protection data sheet or contact your Proofpoint sales representative.











