At the core of information security is the need to defend data—including from threat actors seeking to monetise stolen data for geopolitical or financial gain. Recently, we’ve seen a rise in cyber criminals “triple dipping” from data exfiltration. They’re getting paid to return stolen data, destroy that stolen data and reveal what modifications were made to the returned data.
Now, picture the cyber kill chain. But let’s start at the end of it, where the malicious actor is realising their data exfiltration goal. Data doesn’t just sit around in an organisation, accessible to everyone. There are access rules around the data, and these rules are governed by who the person is. For example:
- A Microsoft 365 SharePoint site has access rules that govern who can download sensitive files.
- Login credentials to a user’s machine govern who can access the files on that device.
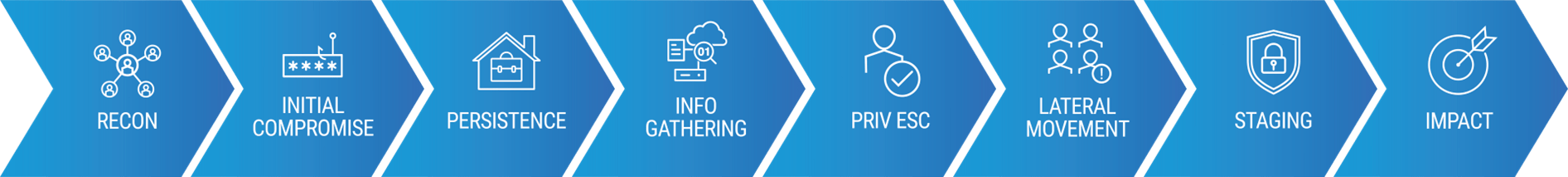
Regardless of where data sits, the key to accessing it is an identity. Cyber criminals understand this—that by owning the identity, they can get to the crown jewels of an organisation. So they map out their attack, moving laterally from one identity to another, elevating their privileges with the goal to access those files.
This series of chess moves could include the attacker using a vulnerable local administrator account credential, elevating privileges to shadow administrator and then gaining access to corporate files. In the post-compromise phase, lateral movement with identity compromise is a threat actor’s go-to activity.
Email’s critical role in helping attackers achieve their endgame
Keep rolling the chess moves back along the attack chain and it raises questions, such as: “What was the attacker’s opening move?” and “How did they end up within the organisation in the first place?”
Well, if we follow the theme of identity, the external-facing form of identity is the ubiquitous email address. Your full name in the directory, your login credential to your PC, your Microsoft 365 identity—everything is tied together and exposed externally as your email address.
Unfortunately, attackers know that. And it’s why:
- Email remains the number one threat vector used by malicious actors.
- Attackers continue to use email to deliver malware.
- Business email compromise (BEC) is a multibillion-dollar problem across the globe.
- Credential phishing attacks are delivered via email.
- Email continues to be the opening move for many threat actors.
It’s also why Proofpoint starts the story with protecting people. When threat actors target people, they target their email addresses, identities and the data those identities have access to.
And it’s why we are unique. No other vendor in the marketplace can align the necessary defence-in-depth elements to protect against a threat actor’s chess moves—from the opening move to the endgame.
New innovations to break the attack chain
Today we are announcing a host of innovations across our platforms to help you combat increasingly common threats. Available today, these innovations help you stop malicious email attacks, detect and prevent identity-based threats and defend sensitive data. Learn more.
One of these innovations is Supplier Threat Protection. Trusted supplier relationships are a growing attack vector: 69% of organisations experienced a supply chain attack within the past year, and CISOs rate it as one of their top concerns. Discover how Proofpoint Supplier Threat Protection helps organisations manage risk by proactively defending against email-based supply chain attacks.
Join us at RSA
Learn more at the upcoming RSA conference about how Proofpoint can help your organisation break the attack chain. During our session “Identity, Data, Email, Endpoint – The 4 Horsemen of the Security Apocalypse,” you’ll learn why it’s essential to protect these four critical vectors to keep your organisation safe. Space is limited. Don’t miss out.
Also, come visit us at booth #6253 at the Moscone Center, North Hall for live demos of Proofpoint solutions and an opportunity to meet with our experts.











