Cyber criminals have evolved their tactics to run targeted campaigns that trick people into clicking on malicious messages. While 99% of organizations have a security awareness solution, only 57% provide organization-wide training, according to the “2022 State of the Phish Report.” That means many users aren’t prepared to identify or report malicious messages, leaving them vulnerable to attacks.
The next question is: Who are these vulnerable users? Understanding user vulnerability is key to building a strong security awareness program. It allows you to establish a baseline and identify current gaps, so you can assign users with more targeted education and better evaluate the effectiveness of the program.
Some organizations use knowledge assessments and/or phishing simulations to determine vulnerable users based on scores and click rates; others leverage threat intelligence to help identify users who interact with real-world threats. In this blog, we’ll dig deeper into the common methods used to determine user vulnerability, address the limitations of these tools, and explore how you can enhance visibility into your highly vulnerable users.
Phishing simulations provide insight into user click rates and responses
Phishing simulation is one of the most common ways to identify vulnerable users. It allows security teams to assess how users would interact with potential threat actors in a safe environment.
Research for our “2022 State of the Phish Report” found that while 85% of organizations educate their employees who fall for real or simulated phishes, there are organizations that just continue to phish their end users with different templates, hoping that they build resilience over time. This could leave knowledge gaps unaddressed.
Additional challenges arise when organizations depend solely on phishing simulation to determine user vulnerability:
- Inconsistency of results due to the level of difficulty of phishing templates
- Inability to draw conclusions about what users don’t know
Different phishing templates have widely varied click rates. Some are more obvious “simulations” than others. As a result, security teams may see a lower click rate in one quarter and a higher click rate in the next quarter. There’s no easy way for those that only measure click rates of simulated phish to know whether their users are making progress. Security teams can’t tell if the users have acquired the knowledge and skills to identify elusive threats in the wild.
While click rate/failure rate of phishing simulation is a critical metric, it is only one metric; it doesn’t tell you what your users struggle with. Also, you can’t tell whether users are avoiding the bad or just “missing” the bad. No matter how many phishing simulations you run, you won’t be able to uncover the concepts your users fail to understand.
Knowledge assessments provide metrics around training module understanding
Another common metric organizations use to determine user vulnerability is scores from knowledge assessments or quizzes. These scores provide a quantitative measure for security teams to identify what users know about threats. By tracking performance and completion rate, knowledge assessments also provide insights into user engagement and areas of improvement.
However, knowledge assessments don’t always predict how vulnerable users will react when they encounter real-world threats. It’s one thing to know what a threat looks like and how to report it to a security team, but another entirely to practice safe cyber habits—especially when faced with a mountain of emails, work chats, and projects. Just like good habits in our daily lives fall to the side when life gets busy, users might understand what constitutes malicious, but it doesn’t guarantee they’ll make the right decisions when faced with a real one.
Threat intelligence allows you to focus your program on real risk
More than 90% of infosec and IT survey respondents said that threat intelligence influences security awareness training decisions, according to Proofpoint’s latest “State of the Phish Report.” One way to leverage threat intelligence is to obtain visibility into how your PEOPLE are being attacked and targeted at any given time. That way, you can deliver specific training to people who are being targeted by certain types of attacks, making training more relevant to your more vulnerable users.
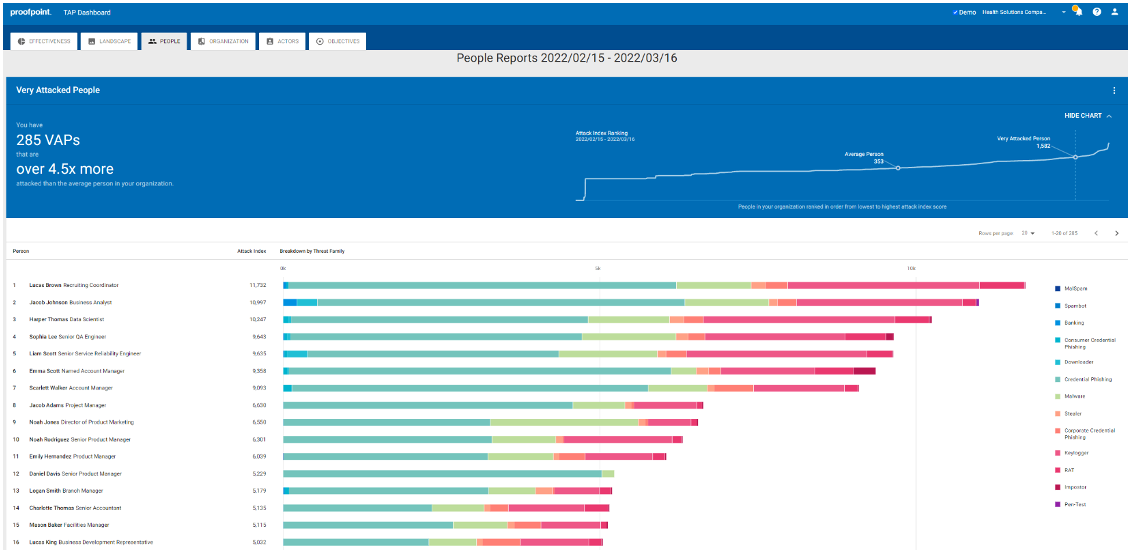
Figure 1. The Targeted Attack Protection Dashboard from Proofpoint ranks users in a VAPs list, making it easy to identify which users are vulnerable to what type of threats.
Proofpoint provides unique insights into an organization’s Very Attacked People™ (VAPs). Our Attack Index ranks threats based on severity in our Targeted Attack Protection Dashboard. By incorporating VAP insights and threat data, along with user participation and performance in simulated phishing tests and knowledge assessments, Proofpoint surfaces your highly vulnerable users, including top clickers, through our CISO Dashboard.
This insight from our dashboard allows you to focus your program on real risky users and draw conclusions about who needs prioritized attention. You can then assign targeted training based on the type of threats targeting your VAPs.
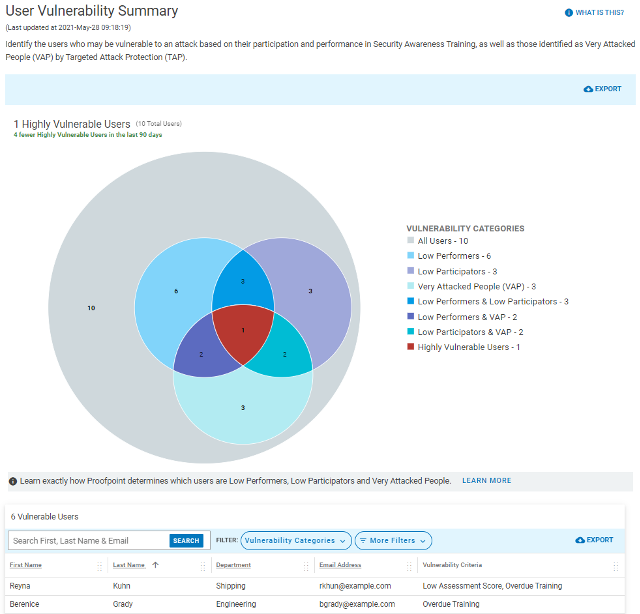
Figure 2. Reporting from Proofpoint shows the relationship between performance, participation, and VAPs to show security teams which users should get prioritized attention.
The last piece that’s critical to uncovering vulnerable users is the use of threat intelligence to develop realistic phishing simulations that mirror what users see in the wild. Proofpoint has a wealth of intelligence pooled from all our customers in different industries. We have a dedicated threat research team that stays abreast of the current events and topics that attackers are using to trick their victims.
But don’t take our word for it, the data says it all: Proofpoint is currently responsible for reviewing almost 24% of global email, which enhances the visibility we have into the latest threats. We incorporate this knowledge into our phishing simulations that mimic trending threats.
Start decreasing your user vulnerability today with Security Awareness Training
If criminals send both wide-net attacks and targeted attacks to steal credentials and information, your organization should also approach training from a tailored and targeted approach to combat cyber criminals. Proofpoint Security Awareness Training provides a holistic framework that gives context into user vulnerabilities and helps security teams decide how to reduce them.
To learn more about how Proofpoint can help boost your last line of defence, download this e-book.











