Phishing attacks have increased in the past few years. More than half of the information security professionals surveyed for the 2021 State of the Phish report from Proofpoint said their organization had experienced a successful phishing attack in 2020. As attackers adapt their social engineering techniques to focus on relevant themes that prey on strong emotions, it’s critical for organizations to take a proactive, multilayered approach to keep their users safe from phishing attacks in and out of the workplace.
In this blog, we’ll focus on some common phishing campaigns observed by Proofpoint threat intelligence in the wild—and what your users can learn from the materials included in our latest Phishing Awareness Kit.
Criminals use internal department reputation to trick users into falling for attacks
People are bombarded with email in todays’ remote work environment. Employees might have their guard up when receiving external emails and check the reputation of a site before clicking on a link. However, they are likely to trust internal emails from cross-functional departments—especially messages from human resources (HR).
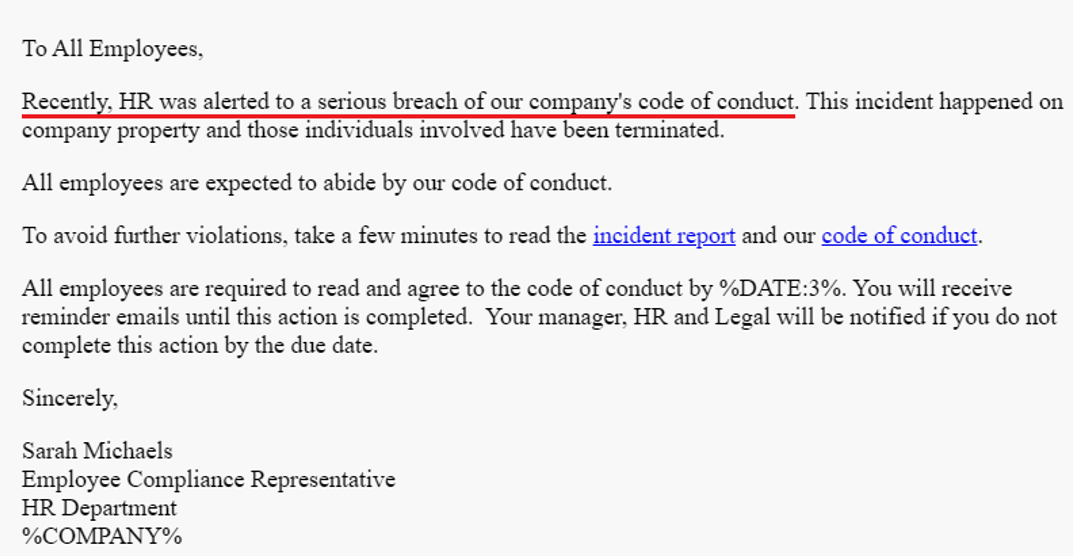
Figure 1. Attackers use the status of HR to convince users to follow through on a requested action
The email above includes a sample simulated phishing email “from HR” that over a quarter of Proofpoint customers have fallen for. But what makes this email so tricky?
First, the tone and content of the email strike a serious, professional tone, discussing a “breach of company conduct.” Next, emotionally charged words like “terminated” and “avoid further violations” help to draw in the user and create a sense of urgency. The message even mentions the involvement of the legal department and a manager if the employee doesn’t meet certain conditions.
Busy employees checking email messages on their phone between meetings will likely be motivated to act quickly to comply with company regulations and avoid getting reprimanded. Since the body of the email sounds legitimate and includes a time-sensitive ask, it’s easy for users to click on the links without hovering over them first.
If the user hovered over the link, they would notice that the URL address in the email doesn’t match any websites related to their organization. They may instead be potentially malicious sites.
Criminals work after hours to attack people with fake package information
Attackers also know that when people work from home, they’re more likely to order products online and anticipate receiving package notifications on their work and personal devices (which are also often linked to corporate accounts).
In the image below, the malicious actor is presenting enticing information about an expected delivery time and even includes a realistic parcel number. Because users won’t remember the exact order number, they might easily trust the number provided and click on it based on their curiosity and eagerness to receive their item.
Also, because the delivery time window is for the same day, the email adds a sense of urgency that ma also prompt users to click on the tracking details link. Note that the attacker doesn’t simply use engaging messaging here—they’ve also copied official logos and used email footers that appear legitimate and trustworthy.
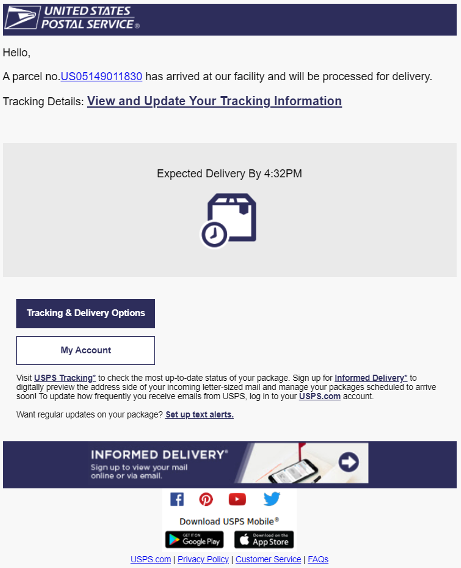
Figure 2. Attackers use nearly identical logos and messaging to build trust with users
People regularly shop online, so sensitive work information can be compromised if users fall for an attack. It’s critical that users always stay vigilant and learn to recognize phishing emails that look like legitimate emails to ensure the safety of your organization and sensitive data.
Attackers use current events to increase urgency and prompt clicks on malicious content
As we enter the second year of the COVID-19 pandemic and new strains emerge, messages that provide “lists of infected users” are sure to capture many people’s attention.
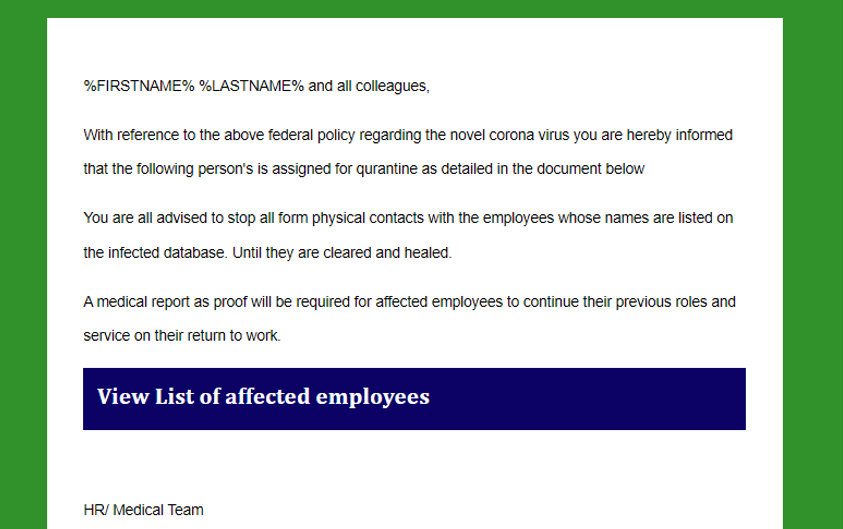
Figure 3. COVID-19 emails that promise information related to employees’ health status appeal to users’ fear
In the email above, the attacker uses professional language and seeks to trick users into clicking a link that will show them a list of all infected employees in their organization, capitalizing on the fear of exposure. The attack tries to build credibility by using a signature from the HR and medical team. Use of a personalized “first name” and “last name” email header is another attempt to build trust by making users believe this email is specifically meant for them.
A strong security awareness education program can set the right foundational knowledge to educate users on how to spot clues that indicate a phishing email, despite the clever social engineering tactics attackers employ.
Use the Proofpoint Phishing Awareness Kit to help educate your users
Cybersecurity education and best practice tips are vital to helping users stay safe. We’ve curated a selection of resources to help your users:
- Identify phishing emails effectively, inside and outside the workplace
- Report phishing to the organization
- Understand the consequences phishing emails can have on data loss and account compromise
The Proofpoint Phishing Awareness Kit provides written, video and other visual content that can be emailed, displayed, posted or presented throughout the next few weeks. You’ll also find instructions on how to use the materials and a suggested communication plan and schedule.











