The data presented in this report were collected during the second quarter of 2019 and reflect the disappearance of the Emotet botnet from the threat landscape beginning in June. The effects of this disappearance are discussed at length and continued throughout much of the third quarter. The report, because of its scope, does not reflect the re-emergence of Emotet on September 16, 2019, in a mid-sized campaign. Proofpoint researchers will continue to monitor Emotet in Q3 and beyond and will provide additional context around its return in the Q3 Threat Report.
Key Takeaways: Emotet goes on hiatus while impostor techniques go mainstream
Below are key takeaways from the second quarter of 2019.
- Malicious URLs made up 85% of global combined malicious URL and attachment message volume, a slight increase from May, but overall in-line with the trend for 2019.
- Global combined malicious URL and attachment message volume decreased almost 10% compared to May, yet this decrease was less than would have been expected given that the two consistently highest-volume threat actors tracked by Proofpoint researchers – TA542 and TA511 – were inactive for the entire month of June.
- Ransomware message volume and campaign activity for June decreased significantly compared to May, but expanded use of Sodinokibi ransomware in email- and web-based campaigns indicate that it has emerged as the main successor to the ‘retired’ GandCrab.
- Messages leveraging impostor techniques and identity deception began appearing at scale in bulk scams in Q2; previously, many of these messages were associated with BEC but actors now appear to be adopting the techniques for other purposes and in far greater volumes.
- The use of domain spoofing in impostor attacks jumped 47 percentage points, up from less than 10% in Q1.
Overview
Key stat: 85% of payloads were delivered via URLs in emails, matching the ratio of URLs vs. malicious attachments observed in Q1 2019.
The most notable change in the malware landscape in the second quarter of 2019 was the disappearance of the Emotet botnet at the end of May. Emotet had dominated the email landscape for much of the previous year with high-volume campaigns that slowly declined throughout the quarter. However, despite the disappearance of Emotet and attendant quarter-over-quarter decline in malicious email, message volume remained relatively high, up 32% from the same quarter in 2018.
Similarly, the relative volumes of messages with malicious attachments vs. URLs remained unchanged from Q1 to Q2, with threat actors continuing to favor URL-based distribution of malware payloads. While the reason for the continued dominance of URLs (Figure 1 and 2) may be due to a range of factors, it is likely that most end users have been conditioned to be suspicious of attachments in unsolicited email. URLs, on the other hand, are increasingly common in business email as we regularly receive notifications of shared files and collaboration updates via email as organizations move to the cloud.
Malware by the numbers
Even as final payloads shifted throughout the first half of 2019, URL-based malicious messages continued to account for about 85% of overall volume.
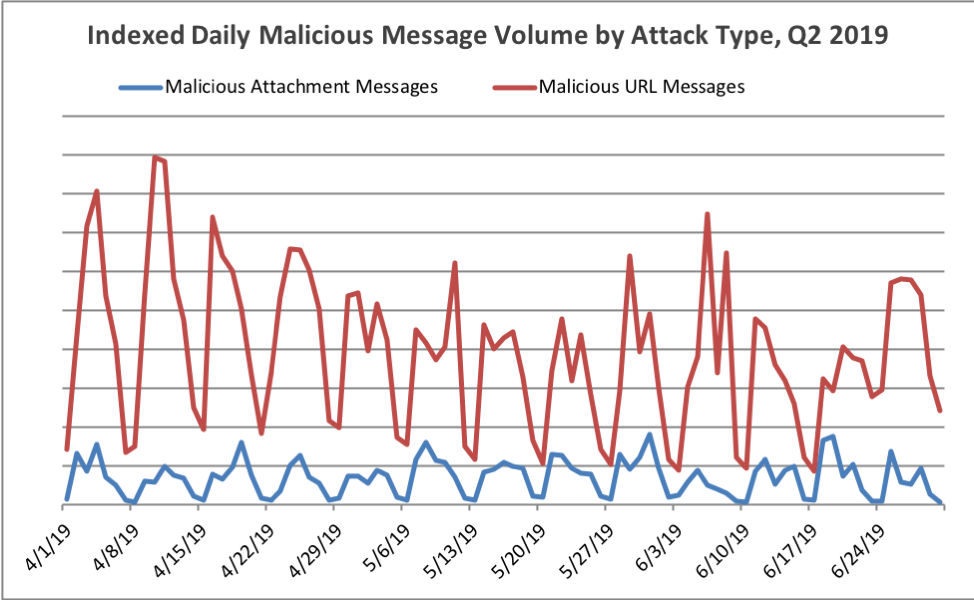
Figure 1: Indexed relative volume of malicious messages by attachment-based vs. URL-delivered payloads, Q2 2019
With the exception of a large spike in URL-based distribution in February, Figure 2 shows that this trend has remained consistent throughout the year.
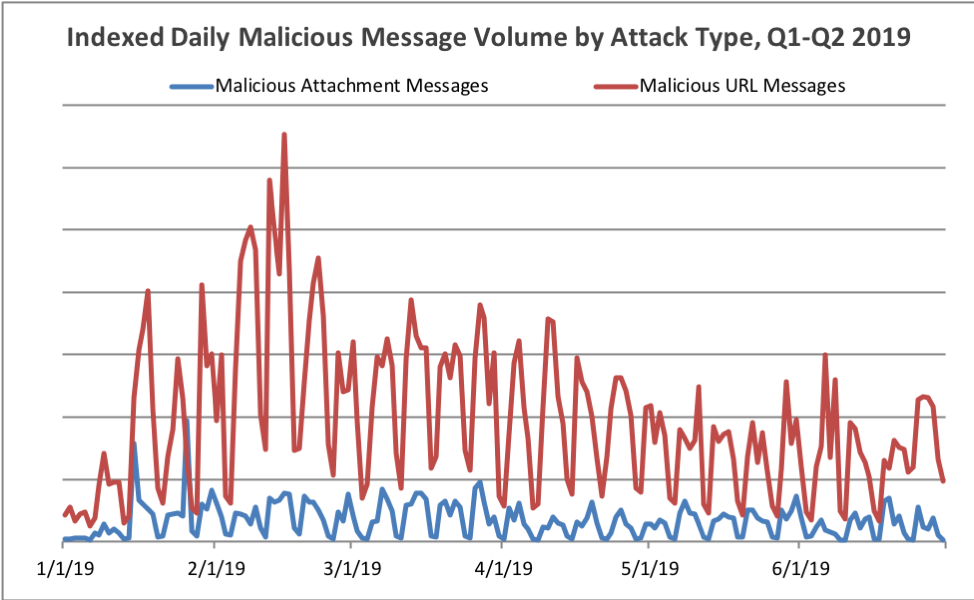
Figure 2: Indexed relative volume of malicious messages by attachment-based vs. URL-delivered payloads, Q1 and Q2 2019
Figure 3 shows the overall distribution of message volumes by malware family in Q2. While botnets (driven almost exclusively by Emotet) remains the top payload, banking Trojans and information stealers still made up 39% of all malicious payloads collectively.
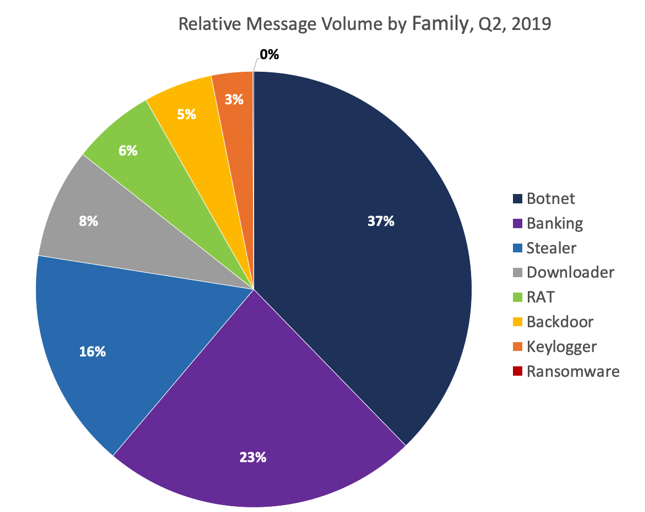
Figure 3: Relative message volumes associated with the top malware families in Q2 2019
Figure 4 illustrates the dramatic shift in relative malware volumes observed between Q1 2019 and Q2 2019. Although Emotet still accounts for over one-third of all payloads, it was displaced by credential stealer volume which nearly doubled relative to Q1. Several typically low-volume families of malware including RATs, Backdoors, and Keyloggers also saw an increase in total volume, but still accounted for less than 15% of all message volume collectively.
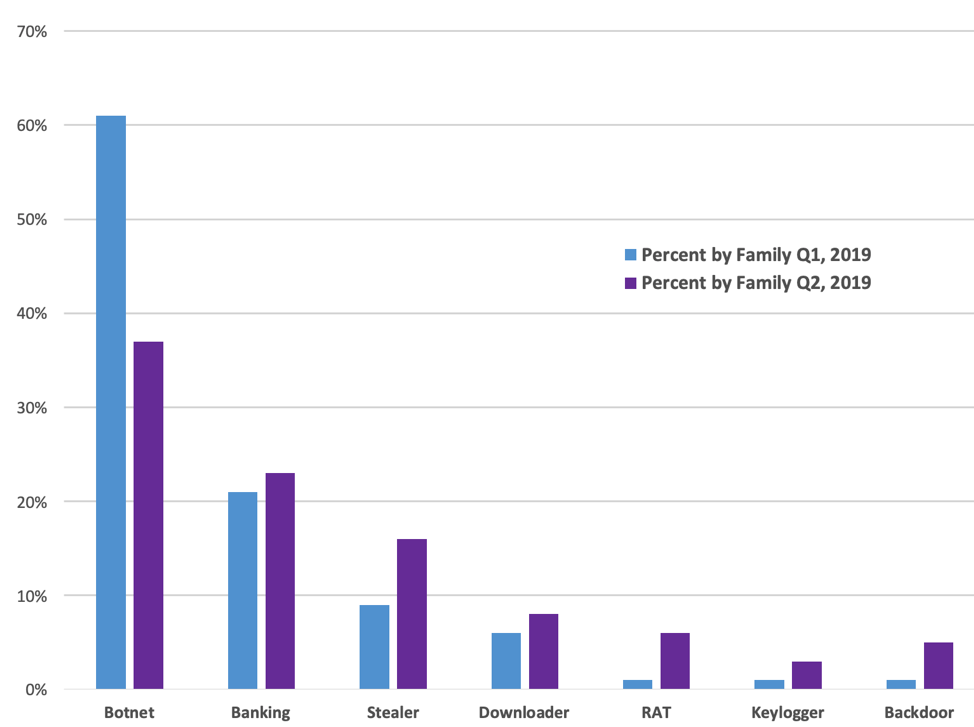
Figure 4: Quarter-over-quarter comparisons of malicious message volume by family
As in recent quarters, ransomware was virtually absent in Q2, with the exception of some smaller-scale, targeted GandCrab and Sodinokibi campaigns. Remote access Trojans (RATs), which peaked at a mere 1% of the overall volume in Q1 2019, increased several fold to 6% of initial malicious payloads, largely due to increased activity by TA505, a frequent distributor of RATs in moderate-volume campaigns. Keylogger and backdoor activity increased several fold, but still account for less than 8% of payloads. Banking Trojan activity remained relatively steady, increasing from 21% from Q1 to 23% in Q2. Stealer activity increased by 80% compared to Q1, while Q2 Botnet activity was nearly half that of Q1, with Emotet being displaced by high-volume Ursnif (Banking Trojan) and Pony (Credential Stealer) campaigns.
Ursnif, Pony, and URLZone displace Emotet as Banking Trojans and Stealers dominate summer malware activity
Key stat: Relative Emotet message volumes dropped 24 percentage points between Q1 and Q2 2019, as the high-volume botnet appeared to go on hiatus beginning at the end of May.
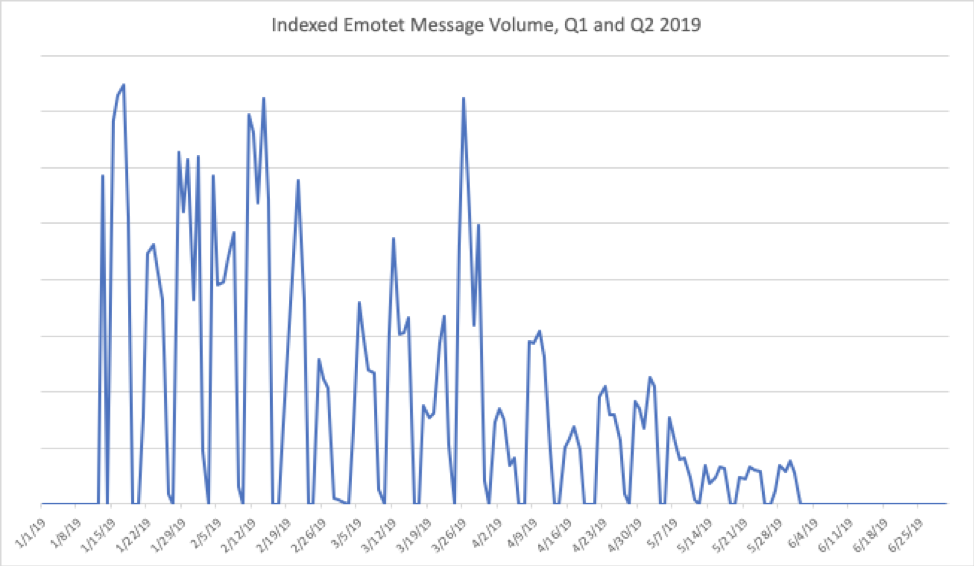
Figure 5: Indexed relative Emotet message volumes for Q1 and Q2 2019
After consistent, high-volume campaigns during Q4 2018 and much of Q1 2019, Emotet volumes began to drop off over the course of Q2. We observed what appeared to be the last Emotet campaign prior to a summer hiatus on May 31, 2019. However, as we have observed with other large-scale malware operations, breaks are not uncommon as actors retool, build new infrastructure, or regain control of sending botnets. Given the significant influence of Emotet on the overall threat landscape based on sheer volume, as well as well-crafted, localized campaigns, we will continue to monitor the malware and C&C infrastructure in coming quarters.
While no actor or malware strain fully compensated for the absence of Emotet in June 2019, Ursnif and Pony volumes were high throughout the quarter. We also observed consistent, high-volume URLZone campaigns, most of which were used to distribute Ursnif as a secondary payload in Japan.
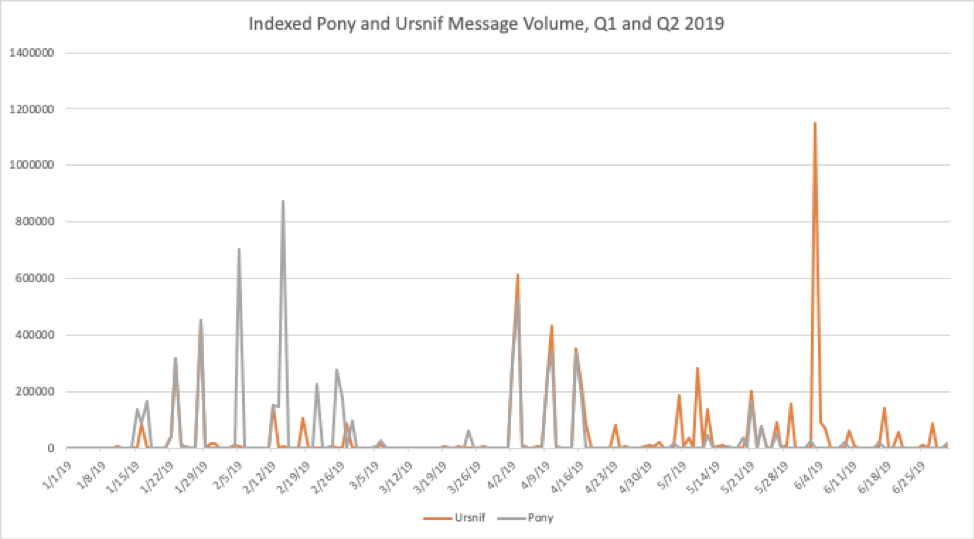
Figure 6: Indexed relative Ursnif banking Trojan and Pony Stealer message volumes for Q1 and Q2 2019
While Q1 2019 saw high volumes of IcedID, The Trick, and Qbot, accounting for 85% of banking Trojan payloads in email, Q2 banking Trojan payloads were dominated by Ursnif, accounting for almost 80% of all bankers. URLZone, primarily used to distribute Ursnif as a secondary payload, accounted for another 11%. The Trick and Dridex made up 3% and 2% of banking Trojan payloads, respectively. Figure 7 illustrates the disproportionate volume of Ursnif in Q2.
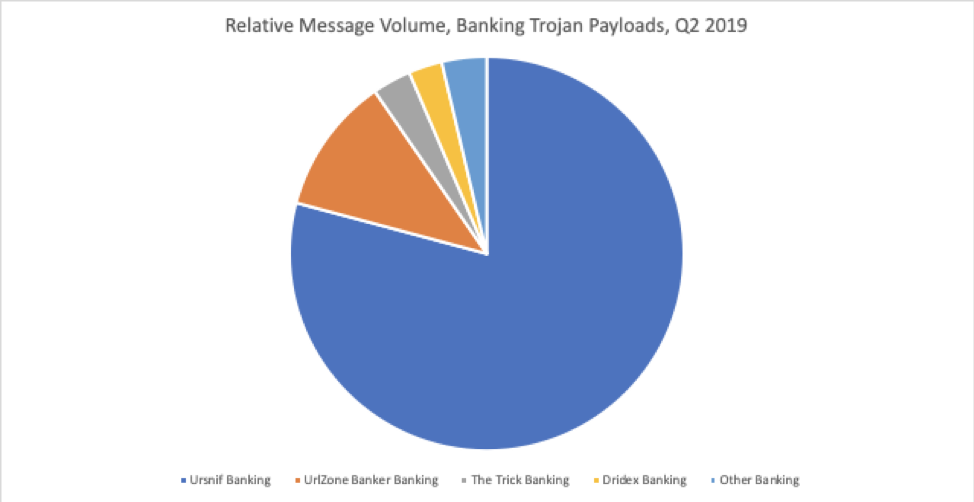
Figure 7: Relative message volumes of top banking Trojan strains, Q2 2019
It is worth noting that credential stealers, led by Pony, featured prominently in Q2. Pony accounted for over half of all stealer traffic in email, driven by high-volume campaigns from a threat actor we track as TA511. AZORult stealer accounted for 16% while Loki Bot and Formbook rounded out the top four stealers. Although Emotet’s malware multitool approach was absent in the last part of the quarter, all of these are robust malware strains designed, like many strains we see in abundance, to reside quietly on infected devices without the victim’s knowledge.
RATs return while GandCrab calls it quits
Key Stat: Remote access Trojans made up 6% of all malicious payloads in email in Q2.
Although ransomware had largely disappeared from the email space prior to the first quarter of 2019, GandCrab remained the exception with carefully constructed localized and geographically targeted campaigns. Late in Q2, however, the operators of the GandCrab “ransomware-as-a-service” announced that they were retiring after reportedly collecting over $2 billion dollars in ransoms. While we observed several small campaigns distributing Sodinokibi ransomware (believed by some to be a successor to GandCrab), ransomware attacks via email became even rarer in Q2.
Campaigns distributing remote access Trojans (RATs), on the other hand, increased five-fold relative to other malware families vs. Q1. These attacks were driven primarily by TA505, which distributed several mid-sized FlawedAmmyy campaigns throughout the quarter. As we noted last quarter, the trend towards robust, multipurpose malware began with the widespread distribution of RATs by TA505 and a shift away from ransomware more broadly.
Impostor threats: Q2 sees widening use of identity deception techniques
Key stat: The use of domain spoofing in impostor emails increased 47 percentage points over Q1 to 57%.
While the use of impersonation tactics has been common in consumer email spam for years, Q2 saw the widespread adoption of these techniques in bulk scams being distributed to organizations. Where we normally observe tens or hundreds of so-called impostor emails being distributed to organizations each quarter, often associated with business email compromise (BEC), thousands of messages utilizing such tactics began hitting organizations in the second quarter. Most of these messages, however, were not BEC but rather bulk scams and affiliate spam. The reasons for this shift are unclear, but this is the first time we have observed such techniques being used for bulk scams targeted at organizations and their employees rather than in widespread consumer scams.
At the same time, Q2 saw a massive increase in the relative use of domain spoofing as an identity deception tactic. In Q1, less than 10% of messages used domain spoofing instead of other, simpler tactics such as display-name spoofing. In Q2, however, that number had increased to 57%.
Similarly, the number and types of domains used in these attacks increased dramatically quarter over quarter. The number of unique header-from domains used to launch impostor attacks increased by 54 times while the number of top-level domains (TLDs) used more than doubled.
We will continue to monitor this trend to determine possible reasons behind the seismic shift in the use and implementation of identity deception techniques in enterprise-targeted email.
Proofpoint Recommendations
This report provides insight into the shifting threat landscape that can help inform an organization’s cybersecurity strategy. Here are our top recommendations for how companies can protect their data, customers, and brands in the coming months.
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks and criminals continue to find new ways to exploit the human factor. Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Build a robust defense against impostor attacks. Highly-targeted, low volume business email compromise scams often have no payload at all and are thus difficult to detect. Invest in a solution that has dynamic classification capabilities that you can use to build quarantine and blocking policies. This solution must also be scalable as threat actors with a variety of aims and practices adopt identity deception techniques and should, where possible, include full implementation of DMARC.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand. Look for a comprehensive domain fraud solution that scans the web and reports fraudulent and suspicious activity.
Partner with a threat intelligence vendor. Smaller, more targeted attacks call for sophisticated threat intelligence. Leverage a solution that combines static and dynamic techniques to detect new attack tools, tactics, and targets—and then learns from them.











