Imagine if your security team could easily see which people in your organization are targeted most often, and also know which security controls to implement to further improve your security posture?
Proofpoint makes that possible with “Actionable Insights,” which go beyond volume-based metrics to uncover insights about how individuals in your organization are being attacked, so that your team can respond faster and be more precise in applying mitigation controls.
In this blog series, we will dive deeper into finding from the Proofpoint Threat Protection Platform. Actionable insights are metrics and insights, based on our combined data, detection and research. They provide the additional detail and context you need to fully understand your threats and the specific actions you can take to defend against them.
Transform your approach to cybersecurity
Research shows 82% of breaches involve some form of contact with your people. So, understanding the risk your people pose is obviously invaluable to a modern cybersecurity approach.
Today’s security teams also face increasing demands on their time while working with fewer resources, making it more difficult to spend time on the most important actions.
With Proofpoint, you can take the individualized, prescriptive actions needed to fully protect your people. Access to Actionable Insights can help your team transform into a more proactive force by focusing on targeted controls that will create the most value for your organization.
Here’s a look at some critical questions about your cybersecurity risks that Actionable Insights from Proofpoint can help you to answer:
Who poses the highest risk in our organization?
The Very Attacked People™ (VAPs) report shows all the people in your organization, organized by how frequently they are attacked. Unlike other attack indices, this ranking is determined not only by the volume of attacks, but also the sophistication and uniqueness of attacks via our Attack Index score.
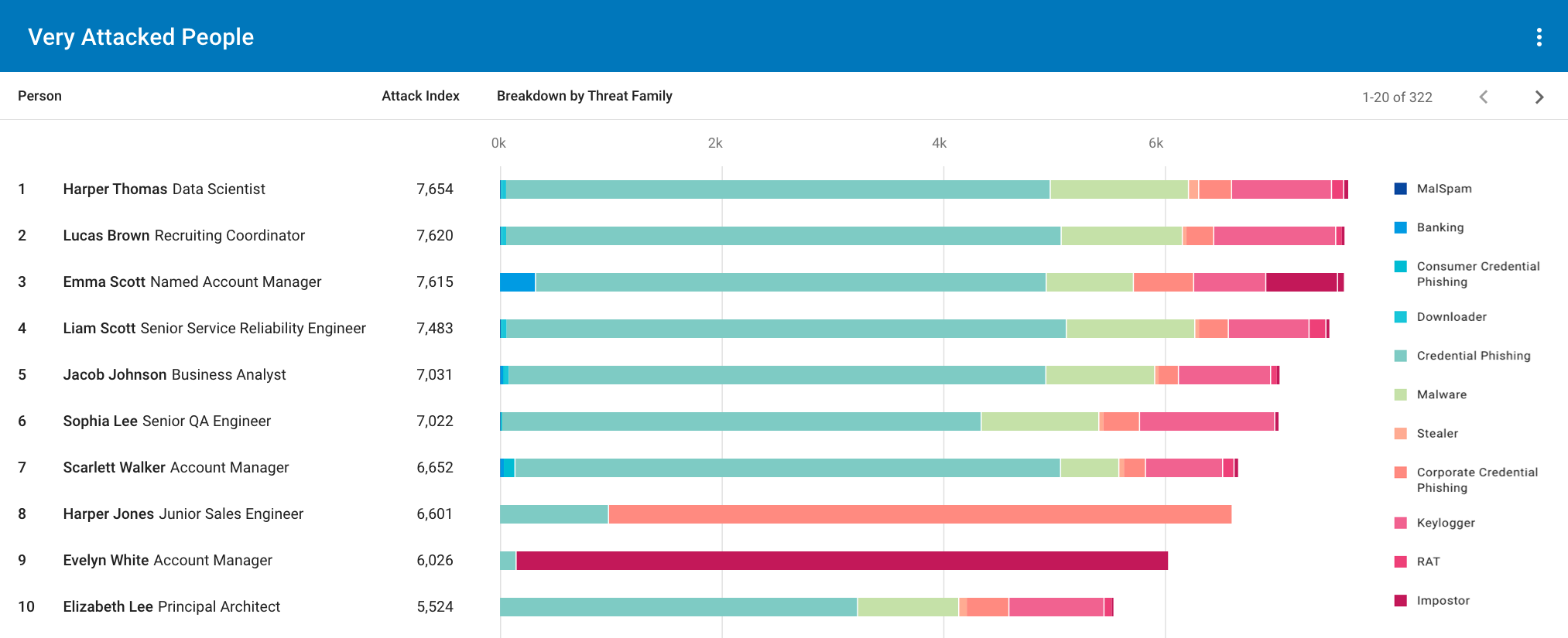
Figure 1. Example of a VAP report.
The VAP report shows threat type breakdowns—such as credential phishing and malware—for each VAP and highlights the people you’ve tagged as VIPs. You can use the VAP report to dig deeper into the activity of those users to understand why they’re being targeted by specific threat types.
The People report gives you a clearer picture of threat activity across all your users. In the example below, we show a People report filtered to display threats seen only in our organization—that is, those threats targeting our company specifically.
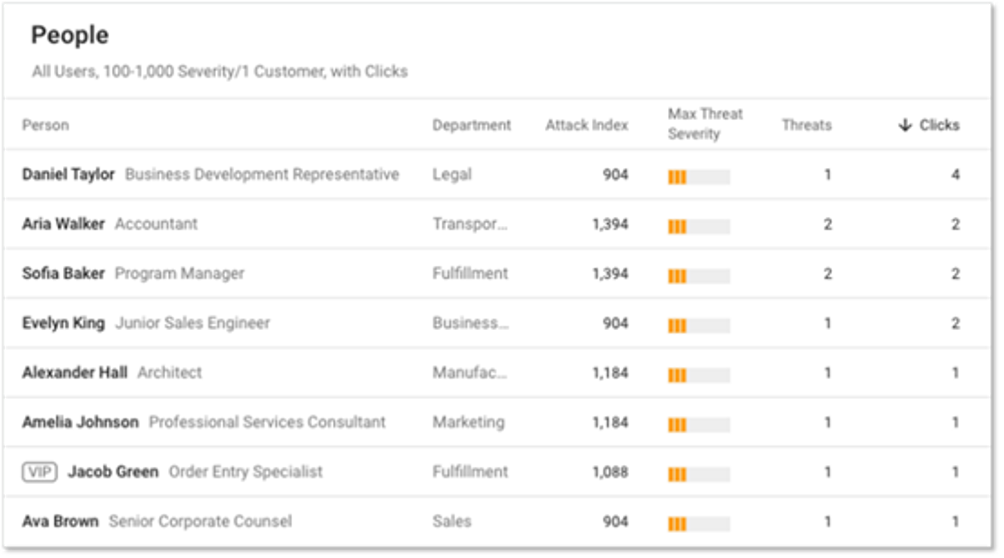
Figure 2: VAP Report
We’ve sorted the People report by clicks to identify our “Top Clickers.” The overall Attack Index score and the severity of the threat for each individual is also visible. Also, we can see which users we’ve tagged as VIPs, which helps us better understand why these users are being targeted and how they might be interacting with threats.
Using insights to implement targeted controls
Actionable Insights about the people in your organization are valuable to inform downstream controls that you can implement to improve your security posture. Some examples of these actions include:
1. Assigning targeted awareness trainings and simulations.
We see many customers assigning their VAPs and Top Clickers to more frequent and targeted phishing simulations and education compared to the general population of users.
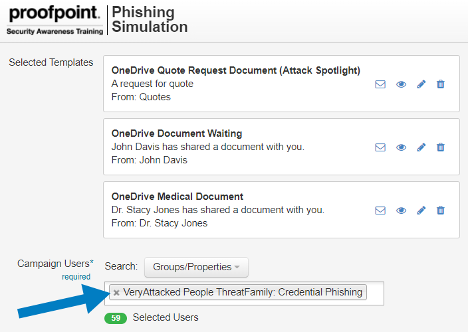
Figure 3: Example of phishing simulation
Your organization could, for example, group VAPs who are targeted most often with business email compromise (BEC) attacks and use Proofpoint Targeted Attack Protection (TAP)-guided trainings to assign them related BEC trainings. You could also follow up with BEC phishing simulations.
2. Tightening security policies.
Isolating browsing for VAPs, VIPs and Top Clickers offers a powerful line of defense against targeted URL threats that may reach these users. You can also apply automatic URL-sandboxing or stricter multifactor identification (MFA) policies.
Another strategy is placing the users you’ve identified as Top Clickers into more restrictive isolation groups.
3. Sharing reports internally.
Sharing reports with key stakeholders, like your CISO and board of directors, helps drive impact to your executives to increase awareness of threats and elevate the discussion around people-centric risk. It also helps decision-makers understand the need to implement adaptive controls or invest in security awareness training programs specifically for VAPs and Top Clickers.
You can also use Actionable Insights reports to engage and get buy-in from your high-risk individuals, business units or departments regarding security controls and policies.
4. Implement stronger authentication and identity and access management (IAM) policies.
Many of our partners ingest VAP lists to inform additional actions on their end. You can use these integrations to automate additional controls for your organization, such as restricting password recovery or adding heightened MFA policies. For instance, you could create stepped-up authentication policies for VAPs who are targeted with credential phishing attacks.
Actionable Insights deliver value
The benefits of using Actionable Insights from Proofpoint include strengthening your organization’s security, making progress toward building a security culture and:
- Increasing your operational efficiency. By protecting people first, your security teams can spend their limited resources on actions that will have the highest impact. You can also decrease the likelihood of a successful attack with automated security policies from vendor integrations.
- Lowering your risk exposure. Targeted security awareness training leads to decreased clicking and increased reporting of malicious emails—resulting in stronger protection and fewer successful attacks. And by tightening security policies on your most at-risk users, you can decrease the likelihood of a successful attack.
Learn more about Actionable Insights from Proofpoint here.











