Phishing emails are constantly evolving, preying on people’s emotions and taking advantage of the heightened fear and uncertainty around issues like COVID-19 to distribute malware, steal credentials and commit fraud. Since the beginning of the pandemic, cyber criminals have siphoned millions of dollars from businesses using various phishing tactics and other social engineering tools. And according to the latest “Verizon Data Breach Investigations Report,” 85% of data breaches involved a human element and 61% of breaches involved credentials.
Over the last several years, especially in the business world, it has been increasingly difficult to authenticate people and their communication. And the rapid rise in remote work has made users the new targets for attackers. The Anti-Phishing Working Group reports that in 2020 alone, phishing increased by 300%. Last year, 83% of respondents said they experienced a successful phishing attack, according to research for “2022 State of the Phish Report.” That’s 30% higher than the global average and a 14% year-over-year increase.
These trends help to underscore why an effective phishing prevention strategy requires more than just well-educated people or threat-blocking—it demands a multilayered approach to defense.
How does phishing prevention fit into my cybersecurity strategy?
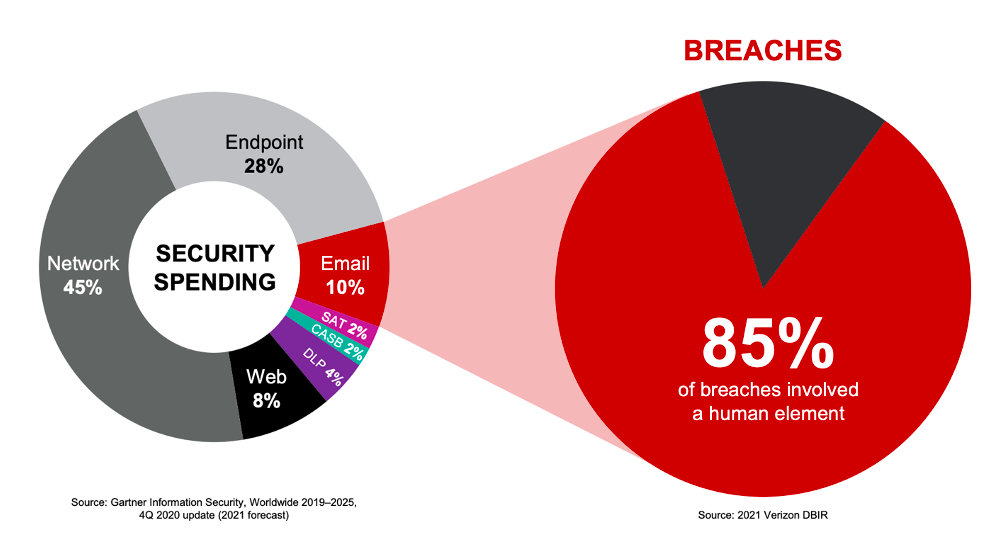
Figure 1. Security spending, according to Gartner, is not aligning with breaches and where they are originating. Organizations should consider investing more in people-centric security technology to reduce the risk and impact of breaches.
As the threat landscape continues to evolve, organizations need to invest in multilayered defenses to stop threats that target people. It’s important to shift budgets as necessary to the threats causing the greatest risk and impact to organizations.
With phishing, only one threat can lead to a compromised account, major data breach or ransomware attack. An effective email security solution should offer multilayered protection from malicious messages including advanced detection, actionable visibility, automated remediation, authentication, data loss prevention, and adaptive security controls like browser isolation and security education. These controls enable security teams to have confidence that they can secure users from email threats.
Key layers to prevent phishing
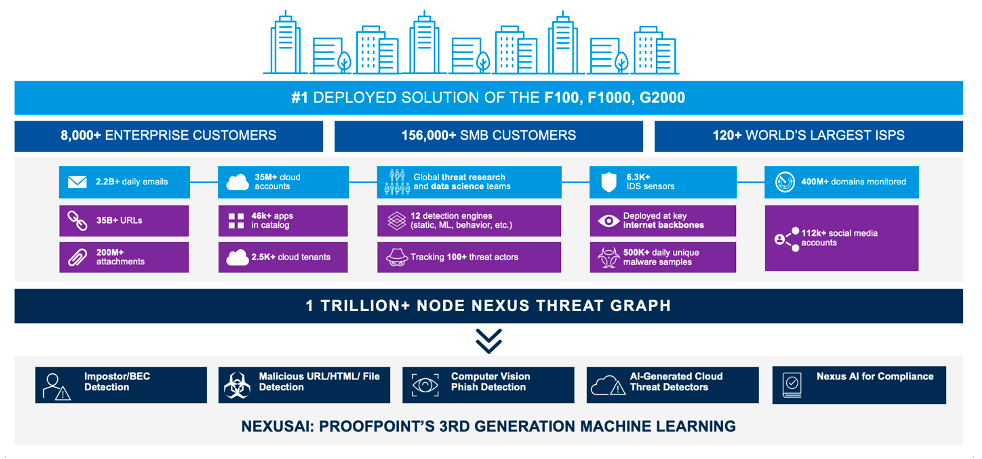
Figure 2. A platform should have a wide breadth of visibility to ensure threats can be detected and stopped quickly. Proofpoint Email Security and Protection is the most deployed solution in the F100, F1000 and Global 2000, and it spans multiple vectors.
Using a platform solution or multilayered approach to phishing protection offers your organization unmatched visibility into threats and how they’re targeting your people. And by leveraging threat intelligence that spans across email, cloud, networks, domains and social, a platform can better detect and stop phishing attacks activated by users.
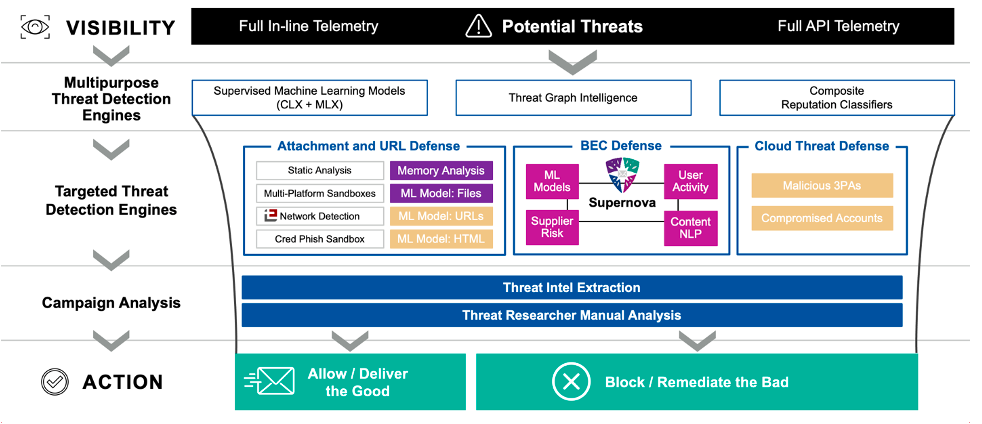
Figure 3. The advanced detection stack from Proofpoint ensures more threats are detected and stopped, without burdening security teams with false positives. According to measurements, detection efficacy averages over 99.999%, with less than 1 in 4 million messages being false positives.
Advanced security platforms should include advanced detection of malicious payloads like URLs and attachments alongside content, behavioral and supplier signals using artificial intelligence and machine learning. That’s because new phishing attacks, like business email compromise (BEC), can often carry non-malicious payloads, making them harder to detect. Companies like Proofpoint use sophisticated technology to detect, catch and analyze billions of messages every day and block phishing threats from ever getting to your people in the first place.
Speed and automation are also critical in terms of recovery. The ability to automate your incident response post-delivery or from user-reported messages can help remove risk further without increasing operational overhead. Email security incidents with lengthy remediation cycles can be a distraction and burden to IT teams and divert resources from more critical projects.
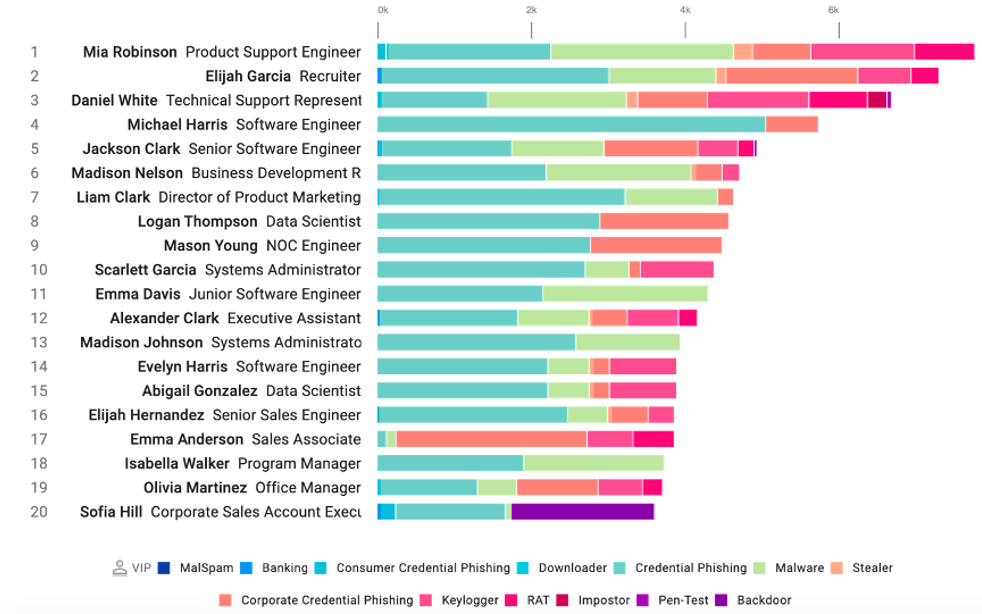
Figure 4. Actionable visibility like Very Attacked People™ (or VAPs) help organizations more strategically reduce risk with controls like browser isolation or security awareness training.
Just as important as detection is the ability to identify email security risks and who in your organization is most vulnerable to them. More importantly, you need to understand which users are being targeted. Providing adaptive security controls like browser isolation can further protect your riskiest users and help reduce risk faster for your IT staff.
Integrated browser isolation capabilities allow the best of both worlds for organizations. They let users freely browse the web or unknown URLs while still providing effective security controls to keep malicious content from executing on users’ corporate devices. Isolation also allows IT teams to further regulate users by enabling policies to manage potentially risky actions rather than setting “allow all” or “block all” policies.
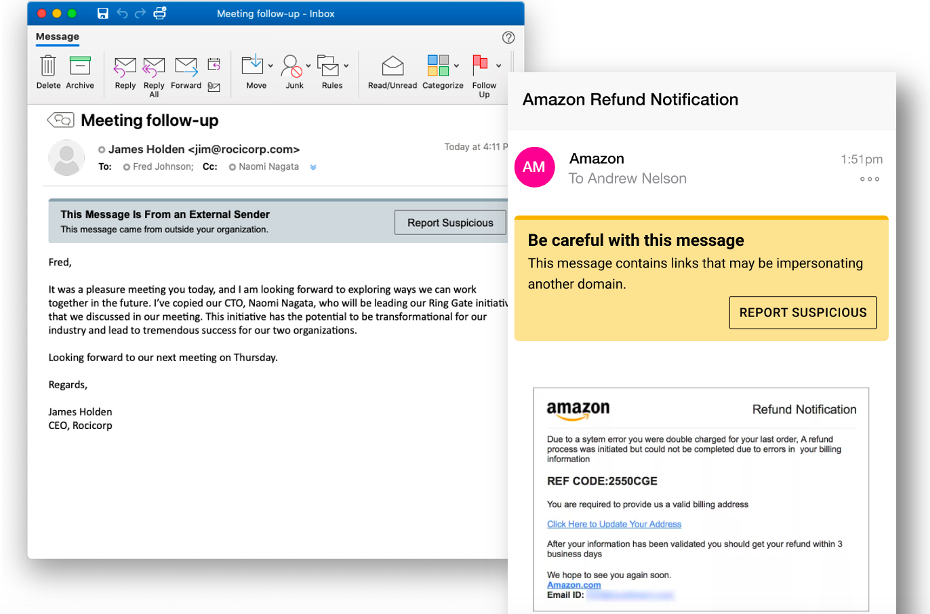
Figure 5. HTML-based email warning tags with a “Report Suspicious” button make it easier for users to spot and report potentially malicious messages regardless of the device or application they’re using.
Educating your users on the latest phishing and social engineering techniques will also help reduce risk and generate a culture of cybersecurity within the organization. Security awareness training and contextual guidance in-email with users will reduce successful compromises.
By understanding who within your organization is most targeted or how you can better protect your VAPs is essential, since user behavior isn’t predictable and phishing attacks can target anyone. A successful security awareness program can cut phishing risk by up to 90% and help drive positive behavior change if done correctly. It also helps you ensure compliance and minimize user downtime. And when you educate your users to spot and prevent phishing emails, they become part of your line of defense.
Email warning tags can also help reinforce good behavior and allow users to report suspicious emails more easily by responding directly from the tag itself. Users can receive nudges if the message is from an external sender, potentially an impostor or impersonating a domain. Email warning tags and nudges help reduce risk while educating users on how to identify potential threats.
Using the right email authentication protocols will help protect your customers, employees and bottom line from email fraud. By simplifying DMARC authentication, you can stop email fraud and safeguard your trusted domains. And you can gain insight into fraud risks posed by suppliers, including impostor threats, phishing, malware and spam.
Email Data Loss Prevention (DLP) also mitigates the risk of a data breach via email and keeps your sensitive and confidential information from leaking outside your organization through email. It accurately classifies sensitive information, detects data exfiltration transmissions via email and stops critical data loss. You can better protect your data from phishing attacks and accidental mistakes by defending your content across cloud services, email, endpoint and on-premises file shares.
Next steps: See how phishing impacts your organization
The cybersecurity landscape is constantly evolving, especially in the world of phishing. It’s critical for organizations to enable a multilayered approach and always communicate with employees about the latest phishing and social engineering tactics.
Keeping organizations safe with a holistic platform approach and enabling employees to be more aware of threats will help considerably to reduce risk and create a more secure environment.
Interested in seeing phishing threats in your environment? Take our free Email Rapid Risk Assessment. In less than five minutes you can:
- Understand your risk posture that uncovers threats your email security solution is missing
- Gain visibility into who at your organization is being targeted, like your Very Attacked People (VAPs)
- See how Proofpoint can provide the best integrated, layered protection against evolving threats











