Finding a good plumber, electrician or appliance repairman is like finding a needle in a haystack. Once you find a good one, though, they’re worth keeping on speed dial. This is where our customer comes into play. The business, operating across the United States, Canada and Europe, provides a network of reliable, locally operated repair franchises that homeowners can access through an app by requesting and scheduling appointments.
In this blog, we share why the world’s largest home services company selected Proofpoint over Abnormal Security. Although this company is a Proofpoint customer, they have asked for anonymity so that they can share their story and experiences openly.
Rapid growth fuels new security challenges
During the last five years, the company has experienced significant growth. Today it has more than 30 brands and 5,500 franchises globally with sales topping $4 billion last year. Unfortunately, all this success comes with new security challenges.
As a business that uses a franchise model, it has a decentralised structure, which opens it up to multiple attack vectors. This situation is made worse by the franchises themselves, which typically lack cybersecurity expertise, resources and training. As a result, our customer struggled to protect its headquarters and its global franchises from email-borne threats.
Here are just a few cybersecurity threats that they faced daily:
- Advanced phishing. In these highly sophisticated attacks, bad actors try to trick people into handing over their login credentials, financial information or personal data. Typical examples include spear phishing and business email compromise (BEC).
- Malware attacks. Malware is malicious software or code that bad actors use to disrupt, damage or access networks, systems and devices. Examples include ransomware, rootkits and botnets.
- Social engineering. People can be easy to manipulate. With these attacks bad actors use emotion (usually fear and urgency) to trick people into performing an action. This might be sending the attacker money or handing over their sensitive customer data or credentials. Pre-texting, vishing and impersonation are examples.
Building a defence-in-depth foundation
Before becoming a Proofpoint customer, the company relied on Microsoft 365 E3 native email security to stop threats. This was problematic. Microsoft E3 is good at identifying commoditised threats, which are launched by unskilled bad actors using prepackaged cybercrime tools. However, it struggles to identify advanced email threats, which are on the rise, like malicious URLs, payload-less phishing and BEC attacks.
The security and IT teams understood that something needed to be done and agreed that a defence-in-depth approach was needed to fortify the company’s defences. So, they decided to take a test drive of Abnormal Security and Proofpoint, doing a proof-of-concept (POC) of each to see which worked best.
There were several key requirements for these POCs:
- Effectiveness at stopping threats pre-delivery
- Visibility and insights into threats
- Platform scalability
Pre-delivery efficacy: Proofpoint wins
Both the security and IT teams were not confident that Microsoft could stop email threats pre-delivery. That’s why enhancing this capability was a POC priority. Unlike Proofpoint, Abnormal doesn’t offer any pre-delivery detection or analysis—it has a 0% pre-delivery detection efficacy rate.
Compare that to Proofpoint. Our solution has a 99.99% pre-delivery detection efficacy rate and identifies and stops threats before they are delivered to user’s inboxes. That means users can’t engage with threats at all, which reduces the downstream burden on security teams.
Proofpoint uses a multilayered detection stack to accurately identify the widest array of both known and emerging threats. Our broad set of detection technology means that we can apply the right technique to the right threat at the right time. By combining our existing attachment defence with our pre-delivery hold, and sandboxing suspicious messages with URLs, we ensure that fewer malicious URLs and dangerous payloads are delivered to users’ inboxes. This includes QR codes or any malicious files that are attached to emails.
And thanks to our pre-delivery Nexus language model detection, we also stop threats like BEC. Our engine uses semantic analysis to understand the intent and context of an email message’s language, such as a sense of urgency or a reference to a financial transaction.
Besides not providing any pre-delivery threat detection capabilities, the customer concluded that Abnormal’s post-delivery behavioural AI detection only provided surface-level insights (‘this is a phishing threat’) and didn’t provide any deeper or advanced analytics (‘this phishing threat came from threat actor X’ and ‘is targeting these people in the organisation’). At the end of the POC, the teams found that Proofpoint’s pre-delivery, post-delivery and click-time-detection capabilities made it the clear winner when compared to Abnormal’s post-delivery only tool.
Visibility and insights: Proofpoint wins
With Microsoft 365, the security and IT teams couldn’t see which franchise users were falling for advanced email threats. They suspected that some franchises might have repeat offenders who clicked on malicious URLs and some might have a high number of people being targeted by bad actors.
During the Abnormal POC, the teams found that they couldn’t get the insights they were looking for. Abnormal doesn’t provide any threat intelligence visibility or telemetry into unknown or emerging threats across the global threat landscape. As a result, it has a major detection blind spot.
Compare that to Proofpoint. With our people-risk visibility, you get unique insights into your Very Attacked People™ (VAPs) and the threats targeting them. This gives you valuable knowledge about your people—how attacked they are, how vulnerable they are and what privileges they have.
During the Proofpoint POC, the teams noted that enhanced visibility into people risk had several advantages. It helped them identify franchises that had poor security practices or were repeat offenders. These insights ensured they could use targeted adaptive controls—like browser isolation, security awareness training and step-up authentication—to better protect the people and business.
Unlike Abnormal, Proofpoint global threat intelligence provided valuable data to reveal new and emerging threats in the ever-changing threat landscape. Proofpoint is your early threat warning system. We proactively provide overviews of executive-level, global and vertical threat data so that you’re always informed about what’s going on in the email threat landscape. We also provide detailed insights into which specific threat actors are targeting your business. That includes how they’re evolving their tactics and techniques.
Proofpoint threat intelligence is also easy to understand. Not only does it explain why a threat was condemned, but it also provides a timeline, a list of affected users and other points observed by our behavioural AI.
The customer said that our richer and deeper threat visibility was incredibly valuable. And when they compared Abnormal’s intelligence and visibility to Proofpoint’s, they found Abnormal’s to be very limited.
Platform scalability: Proofpoint wins
When it came to platform scalability, Abnormal Security appeared to hit the mark at first. It did a good job of detecting specific threats, and its automated remediation removed unwanted spam and phishing threats. But its limitations soon became clear. As a point tool, it focused on a limited type of email threats. As such, it couldn’t match the volume of new incoming threats and the scale of the customer’s continued growth.
Unlike Abnormal, Proofpoint has superior threat scalability. Our Nexus advanced AI, machine learning and language models are built to digest and analyse vast amounts of threat data, including 1.3 trillion emails, 1.8 trillion URLs and more than 1 trillion attachments per year. This ensures we have effective and efficient threat detection.
Our multilayered threat detection stack is highly accurate at stopping the widest variety of threats, including advanced phishing, BEC and social engineering attacks. Because we have a broad set of detection technology, we can apply the right technique to the right threat.
For example, our robust sandbox technology can detect malicious URL-based threats. And our behavioural analysis stops BEC threats. Plus, we continually analyse messages—both before they’re delivered and after they’re in users’ inboxes. This means there are multiple opportunities to detect threats.
All these factors convinced the teams that Proofpoint could better support the company’s rapid growth.
A simple decision
After the Abnormal POC, the customer found that they were not impressed with the overall experience. The large number of false positives was overwhelming. There was no threat intelligence visibility. And post-delivery detection and remediation was ineffective. Additionally, the customer found that it wasn’t economical to purchase Abnormal as it required them to upgrade to a Microsoft 365 E5 licence for the security they were looking for. Simply put, they couldn’t receive all the email security protection they required from Abnormal alone.
As a result, the customer moved forward with Proofpoint and purchased our People Protection solution to complement their native Microsoft 365 email security.
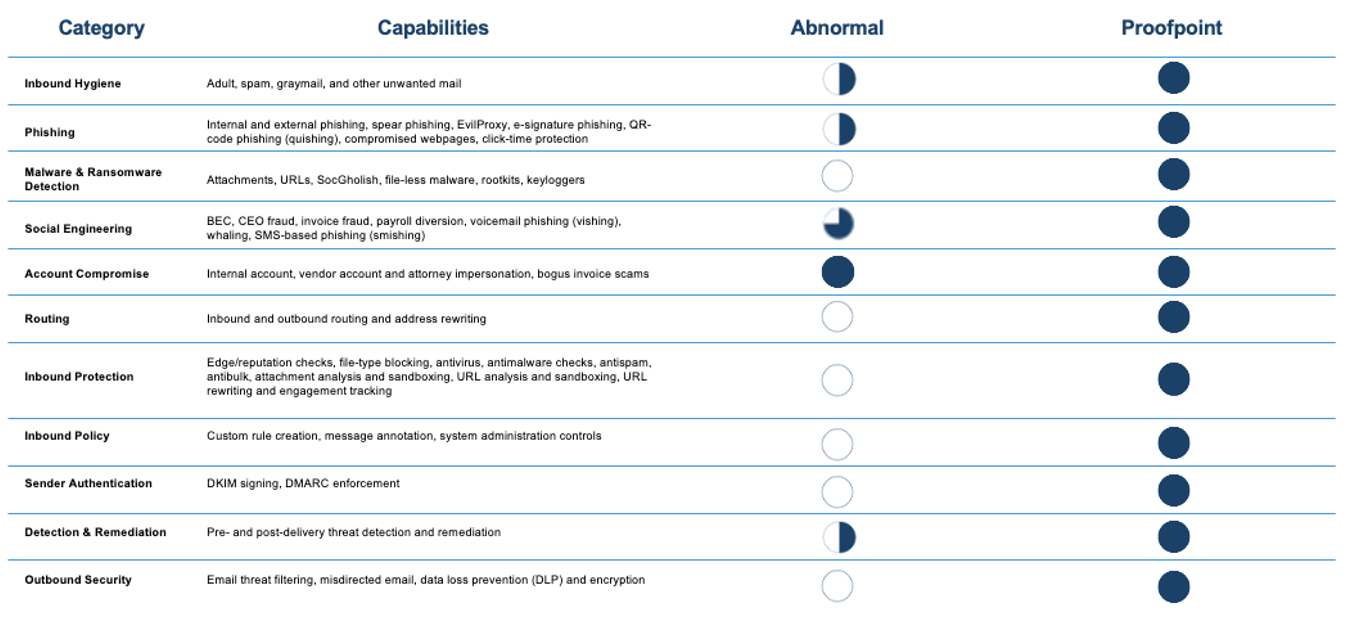
A comparison of Abnormal Security and Proofpoint.
This company’s experience and conclusions are not unusual. Our research shows that when businesses choose Proofpoint, their ability to detect and prevent malicious messages jumps by more than 36%.
When you consider all the risks, Abnormal’s appeal fades quickly. Abnormal has hidden costs and complexities that burden organisations with extra costs for maintenance, operations and support. This drives up the total cost of ownership. And keep in mind that Abnormal cannot exist without Microsoft. This means that your company’s email security solely depends on Microsoft’s basic email security capabilities.
The next evolution: human-centric security
To stay safe against commoditised and advance email threats, you need to supplement native Microsoft email security. This starts with a defence-in-depth strategy. Proofpoint provides a comprehensive solution with continuous detection and analysis from pre-delivery to post-delivery and to click-time, throughout the entire email delivery lifecycle.
You can achieve end-to-end protection with our AI/ML-driven threat detection, behavioural analysis and automated remediation. Our human-centric security is vital in your efforts to protect your people and defeat the wide range of modern email threats.
To learn more, download our Microsoft and Proofpoint: More Secure Together solution brief.











