Email is the lifeblood for many companies, even more so in today’s remote work environment. It’s also the lifeblood for attackers who continue to exploit email as the most used — and effective — attack vector. From ransomware to credential phishing to business email compromise (BEC) to supply chain attacks, it’s clear that email continues to be the number one threat vector. Because email is such a massive threat vector, selecting the right enterprise email security solution is critical to your business.
Forrester recently published The Forrester Wave™: Enterprise Email Security, Q2 2021, which evaluates enterprise email security providers to help security teams select the right solution for their needs. We’re pleased to announce that Forrester has recognized Proofpoint as a leader in enterprise email security.
Forrester’s evaluation also gave Proofpoint the highest score in the current offering category, which includes criteria such as email filtering, threat intelligence, data leak prevention, integrations, incident response, and support and customer success.
In this blog, we dive into what we believe sets Proofpoint apart from other solutions.
The Most Effective Threat Detection
Given the dynamic nature of the threat landscape, it’s critical that your email security solution accurately detects and stops a wide variety of threats. Why? Attackers are relentless. If your email security solution is only effective at detecting one type of threat, you’re still exposed to other threats. Not only does that increase your risk of a breach and financial losses, but it also increases the workload for your security teams.
Proofpoint delivers the most effective detection across multiple threats — credential phishing, ransomware, business email compromise and more. We continuously innovate our detection technology to help our customers stay ahead of the threat landscape, investing 20% of our revenue back into R&D.
Our high standard of detection efficacy is driven by our history of machine learning/AI, the broad data we analyze across multiple vectors and our expert human threat analysts. We analyze 2.2B+ emails, 35B+ URLs, and 200M+ attachments per day. We monitor 35M+ cloud accounts and 400M+ domains. And our global threat research team tracks 100+ threat actors.
Unique People-centric Visibility
Email threats inherently target people. They require a person on the other end to click a link, download and open an attachment, enter credentials on a malicious website or simply reply to a fraudulent request for payment.
If attackers are targeting your people, you need to understand who your Very Attacked People (VAP) are. Who is most attacked in your organization? What threats are targeting them? Proofpoint provides you with this unique insight.
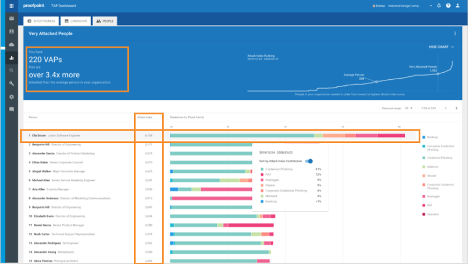
Proofpoint provides visibility into your VAPs
In fact, Forrester’s evaluation notes, “Proofpoint differentiates with its ‘Very Attacked Person’ capabilities.” According to the Forrester report, “Proofpoint’s unique Very Attacked Person concept illuminates who the most targeted people are in a client organization, to provide additional protections or target them for extra training. This focuses protection where it’s most needed.”
Operational Impact
As a result of the economic downturn caused by the global pandemic, security teams are being asked to do more with less. Attackers are ruthless and security professionals are stretched. What security teams need are solutions that reduce the burden.
Proofpoint stops more threats before they reach the inbox and become incidents, reducing the incident response load. Equally, if not more important, is that we accurately detect and stop bad messages without blocking good emails. Email security solutions that generate a ton of false positives ultimately undermine the productivity of security teams, messaging teams and end-users.
Proofpoint also provides SOAR capabilities that automate key incident investigation and response actions related to email threats. The volume of alerts combined with the high likelihood that email threats can do your organization real harm and the need for a rapid response creates the perfect storm for automation. We can automatically identify all instances of a malicious email across the organization and remove them all, including forwarded messages and messages sent to distribution lists. Customers have shared that this capability is game-changing, as what once took hours of highly manual work is now done in minutes.
Integrated Platform
The report highlights the importance of integration stating, “The best email security solutions integrate across customer environments with solutions like EDR, web content security (including browser isolation), and security awareness and training (SA&T).” Forrester’s evaluation gave Proofpoint the highest score in the Integrations criteria.
We believe this high mark is a testament to our Threat Protection Platform which includes integrated isolation for VAPs, threat-intel driven security awareness training, and integrations with leading EDR solutions like CrowdStrike and VMware Carbon Black.
We’re honored that Forrester recognized Proofpoint as a leader in enterprise email security. We’re also thankful to the 8000+ organizations around the world that trust us year over year to protect their number threat vector.
Download a complimentary copy of the report today to learn more about why Forrester recognizes us as a leader.











