Every year, Verizon publishes its Data Breach Investigations Report (DBIR) which has become a bellwether for our cybersecurity industry. The DBIR reveals top trends that tell us how threat actors are operating, who they’re targeting and how. In this post, we’ll cover four key findings that will help reveal how best to optimize your cybersecurity budget in 2021 and beyond.
The Dataset
This year, Verizon analyzed 79,635 incidents, of which 29,207 met their quality standards. 5,258 of those were confirmed data breaches, sampled from 88 countries around the world. In the full report, they include breakouts for 11 main industries and revisit the various geographic regions studied in the prior report to see how they fared over the last year.
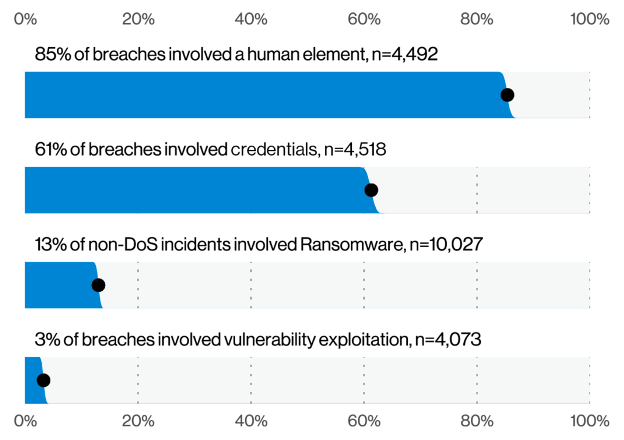
Key Finding #1: 85% of Breaches Profiled Involved a Human Element
Perhaps the most important stat in this latest DBIR is this: 85% of breaches profiled involved a human element. This finding shows that now, more than ever, is the time to orient your cybersecurity investments toward solutions that focus on protecting people first.
A people-centric security strategy is one that manages security risk by focusing on threats that target and exploit people. This starts with identifying your Very Attacked People™ (VAPs) and gaining an understanding into:
- Risky behaviors they may be (knowingly or not) engaging in
- How they are targeted—do they receive a high volume of threats? Or a low volume of highly sophisticated threats?
- How they access valuable data and manage sensitive systems
You also want to invest in a security solution that allows you to quantify risk. The Proofpoint Attack Index, for example, not only identifies targeted people but also surfaces interesting threats from the noise of everyday activity, empowering you to report on individual and overall risk and prioritize the best way to fight back.
Just as critical to identifying and managing risks coming from the outside in is identifying risks from the inside out. Insider threats are quickly becoming one of the greats cybersecurity threats that organizations face today. Your people-centric security solution must all you to
- Get visibility into data loss via negligent, compromised and malicious users by correlating content, behavior and threats
- Prevent sensitive information from leaking outside your organization
- Streamline incident response
To learn more about how Proofpoint can help you build a people-centric cybersecurity strategy, click here.
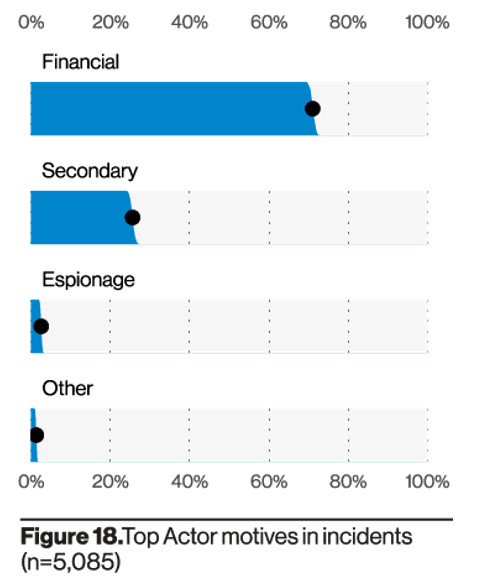
Key Finding #2: Financially Motivated Attacks Are the Most Common
Verizon uncovered that financially motivated attacks continue to be the most common. And the two most common cybercrime terms found on criminal forums are “bank account” and “credit card” related.
Proofpoint and federal research indicates that BEC is a favorite attack leveraged to steal money from targeted organizations—it has resulted in more than $26 billion in potential losses since 2013. Investing in a solid BEC defense is fivefold:
- Detect and block imposter threats before they enter.
- Get visibility into your BEC risks and identify what users are the most vulnerable.
- Make users resilient against BEC threats by training them to identify and report suspicious imposter email.
- Automate your threat detection and remediation process.
- Fight brand spoofing and protect your reputation.
To learn more about how to protect your company from financially motivated attacks like BEC, download Stopping BEC and EAC Scams: A Guide for CISOs.
Key Finding #3: Phishing Remains the Top Tactic in 2021
Despite how far we’ve come in cybercrime defense, attackers continue to innovate with and lean on their favorite tactic year after year: phishing. According to Verizon, phishing was present in 36% of breaches, (up from 25% last year) which can be attributed, in part, to the COVID-19-related phishing lures as the worldwide stay-at-home orders went into effect in early 2020.
Additionally, ransomware this year surfaced as a major attack type, appearing in 10% of breaches, doubling its frequency from last year. 23% of ransomware attacks were directly delivered by email and 30% via direct access, i.e. credential compromise. The trend of “naming and shaming” victims is likely part of the reason ransomware jumped: attackers exfiltrate and encrypt their stolen data and then threaten to reveal it publicly if the victim does not pay the ransom.
There’s no silver bullet to stopping phishing and ransomware. In today’s changing threat landscape, you need a layered approach and visibility that grants insight not only into your threats but also into your most vulnerable users. Here are just a few ways Proofpoint tackles this persistent problem for our customers:
- The Nexus Threat Graph provides visibility into threats across multiple vectors including email, cloud, network and social and correlates threats to monitor and block malicious emails—including phishing—before they reach users.
- Targeted Attack Protection (TAP) helps customrs stay ahead of attackers by analyzing and blocking advanced threats like ransomware before they reach the inbox.
- VAP™ reports reveal what users are targeted most and our training modules allow customers to train those targeted users with the kinds of attacks they are most likely to see.
- The Proofpoint Closed-Loop Email Analysis and Response (CLEAR) solution automates remediation, easing the burden on valuable incident response resources.

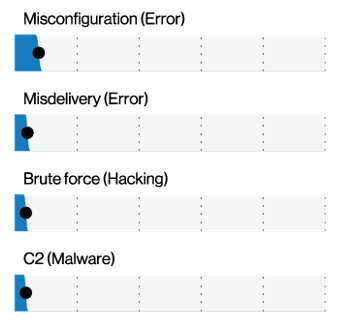
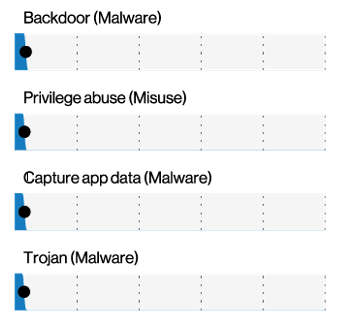
Key Finding #4: Investing in the Cloud Is Critical
While servers still dominate the threat landscape, digital transformation is influencing how attackers navigate their targets.
This year, the DBIR revealed that compromised external cloud assets were more common than on-premises assets in both incidents and breaches. That said, there were 10 times as many Unknowns (incidents where the information on the location of the assets was not available) as there were cloud assets. Still, this shows that in concordance with the ever-increasing shift to personal devices, cloud apps and collaboration tools, the cloud deserves, as Verizon puts it, a “seat at the grown-up security table and a piece of your budget pie.”
For all their benefits, cloud-based applications create new risks and make compliance much more challenging. Managing these risks without squandering the cloud’s many benefits can be a delicate balancing act. Investing in a Cloud App Security Broker (CASB) solution can help.
Key capabilities you should look for when investing in CASB include:
- Visibility into threats targeting your users and automated response.
- Data security, including data loss prevention (DLP)
- Cloud and third-party (OAuth) apps governance
- Adaptive access controls for additional layers of security for high-risk users
To learn more, download our guide, Getting Started with CASB.
Learn More
For more research into today’s the threat landscape, check out the latest quarterly threat report and analysis from Proofpoint here. And to find out more about how to optimize your cybersecurity budget with a people-centric cybersecurity portfolio, please don’t hesitate to reach out.











