The attackers have made it clear who they’re after: Your people. According to the 2021 Verizon Data Breach Investigations Report, 85% of breaches involve human error. And the main threat vector attackers are using is the most popular form of corporate communication—email.
Many organizations may be looking to cut costs in turbulent economic waters, hoping to claw back precious dollars into their budgets. The reality, however, is that “good enough” solutions end up costing organizations more since the most prevalent modern-day threats, including ransomware, Business Email Compromise (BEC), account compromise and malware, are delivered through email.
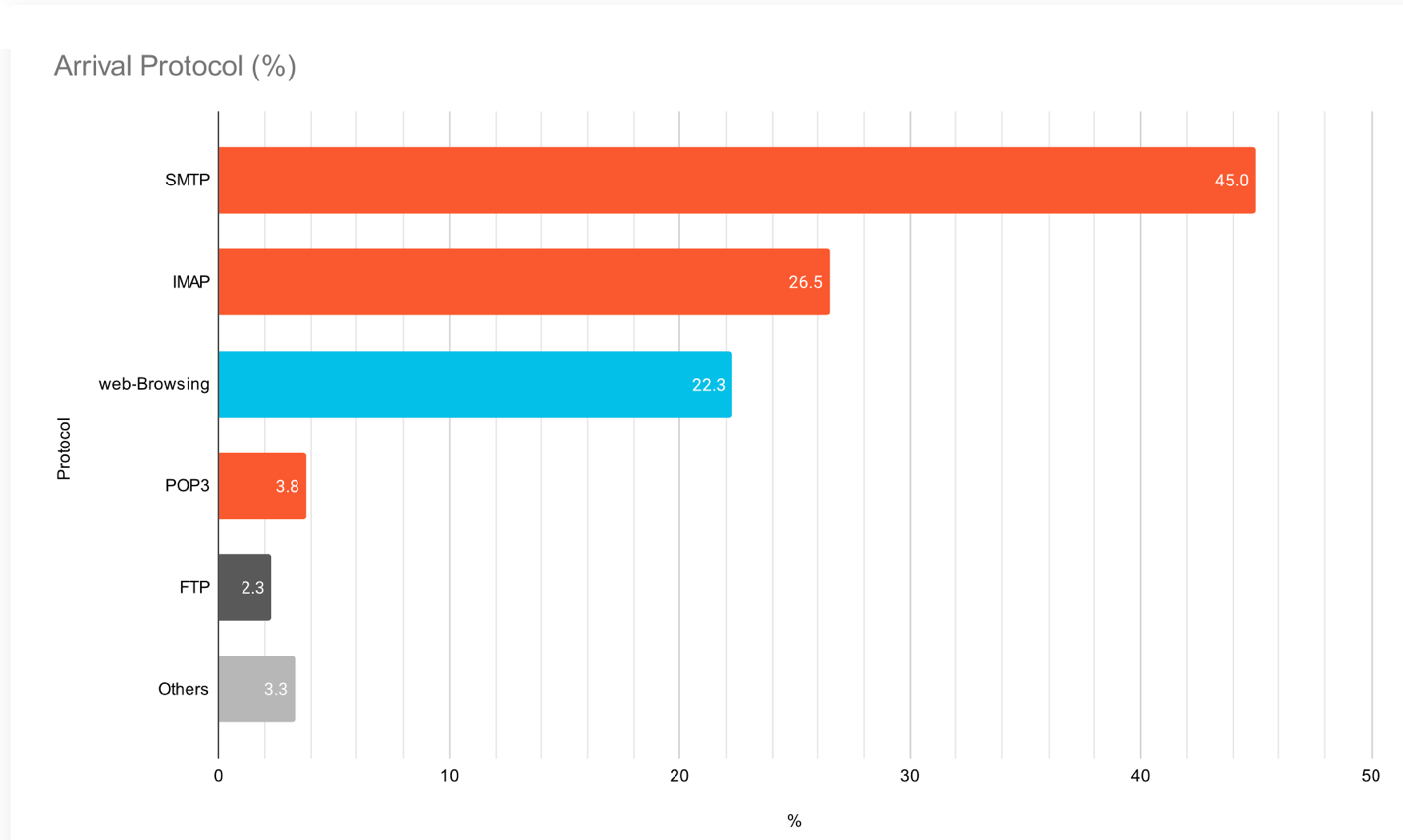
Figure 1. Research from Palo Alto Networks Unit 42 shows more than 75% of ransomware attacks originate through email
When the effectiveness of preventive detection and blocking is compromised, even slightly, information security teams spend more time cleaning up attacks—and dealing with related losses. With teams already overburdened, it isn’t feasible to downgrade such an important layer of defense.
A continued commitment to email security
Proofpoint has been awarded the 2021 Best Practices Global Market Leadership Award in Email Security from Frost & Sullivan. For seven consecutive years, Proofpoint has been the market leader in email security demonstrating our continued commitment to customers and leadership in the email security space. Here are some key highlights from the report:
- Proofpoint is the leader in the email security market, with a market share of 27.2% in 2020, accounting for over 50% market share in the Fortune 1000.
- Proofpoint has been outperforming the market for seven years, gaining significant market share every year including 2020, despite the challenges of COVID-19.
- Proofpoint continues to offer an aggressive road map and innovation, aligning the Proofpoint Threat Protection Platform to a shifting threat landscape focused on people-centric threats.
- Proofpoint continues to delight customers, with annual retention above 90% and over 70% of customers adopting at least three products.
Here’s what we think about when meeting the needs of the complex threat landscape for email security:
An integrated, layered growth strategy aligned to shifting needs
With more people working remotely and the migration to the cloud, it’s more important than ever to prevent people-centric threats like ransomware, BEC and compromised accounts.
Proofpoint is driving growth with our integrated platform by leveraging our unmatched depth and breadth of data, Nexus Threat Graph, investing in new detection technologies, and delivering multilayered defenses to prevent threats from activating.
Ultimately, this strategy helps our customers maximize risk reduction to the enterprise.
Relentlessly reinvesting in innovation
To meet the challenge of new and sophisticated threats, Proofpoint has continued to invest 20% of revenue—or 2x the industry average—into the research and development of new technologies and capabilities to identify and stop them. Some examples:
- Advanced BEC Defense, powered by Supernova, uses gateway telemetry, supply chain risk analytics and API data from cloud productivity platforms to uncover even the most sophisticated email fraud attacks accurately.
- The Supplier Risk Explorer dashboard provides teams with insight into risky or compromised suppliers, currently the source of the most costly type of email fraud attacks.
- Email Warning Tags that provide a safer email experience, offering distinct visual cues for end users to take extra precautions with suspicious email.
Innovations like these improve visibility into people-centric threats for information security teams, allowing them to detect and prevent them proactively and more easily.
Product differentiation that stands out—yet fits in
Many vendors offer stand-alone or point solutions for email security, but Proofpoint has built a comprehensive Threat Protection Platform to implement layered email security controls that incrementally reduce risk as they’re implemented.
Integration and sharing of threat data with cybersecurity leaders like CrowdStrike, Splunk, Okta, Palo Alto Networks, SailPoint and others mean simpler operability. Ultimately, through improved automation and streamlining of workflows, teams gain improved operational effectiveness and free up resources to work on other projects.
To learn more about key changes and challenges in email security, and how your organization can protect its people, read the full report here.











