Key Takeaways
- Proofpoint tracks multiple threats known as Sha Zhu Pan, or “Pig Butchering” threats.
- These are confidence-based threats similar to romance scams.
- The threat actors lure a victim into depositing cryptocurrency into a fake cryptocurrency exchange. The threat actor steals the money.
- These threats are typically managed by a large industry of professional fraud actors.
- They can be initiated on dating apps, or social media platforms, or via text messages.
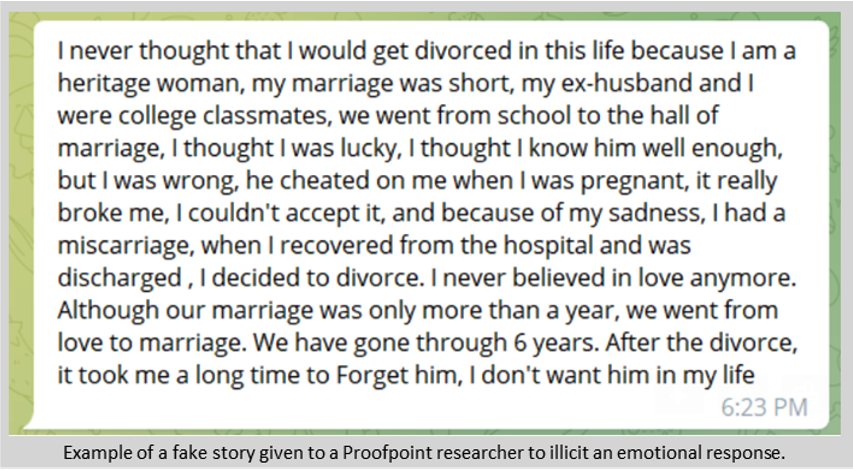
- Proofpoint researchers have spent the last three months engaged with numerous threat actors and developed detections to combat this growing threat. Based on our interactions the threat actors do little, if any, reconnaissance in the target selection phase
- Threat actors are trained to not click links. All attempts to send them tracking links were met with rebuke and often resulted in being blocked.
Overview
Oh, hey there dear reader. It is a pleasure to meet you. You seem very smart and tech savvy to be reading this blog. I bet we could be friends. Maybe something more? My uncle has taught me all about social engineering. He is highly intelligent and has many things to teach you. Let’s move this chat to WhatsApp and you can talk to him about Sha Zhu Pan or “Pig Butchering” ok?
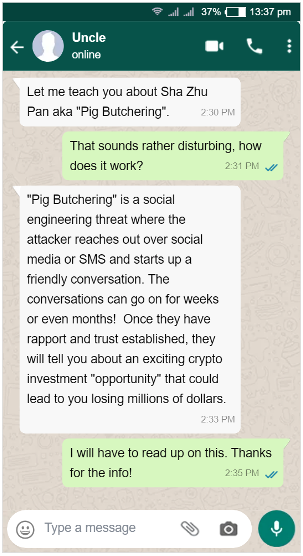
The Long Con
The Sha Zhu Pan (Shāzhūpán) or “Pig Butchering” threat initially became popular in China, before spreading to other parts of East Asia and eventually and more recently, English-speaking countries.
The U.S. Federal Bureau of Investigation (FBI) published an advisory in April 2022 detailing the cryptocurrency-based social engineering scheme that has become increasingly popular. Many victims of this type of attack have reported losing thousands to millions of dollars. According to the Global Anti Scam Organization (GASO), whose founder was a victim of a pig butchering campaign, the average victim loses almost $122,000 USD, and two-thirds of victims are women ages 25 to 40.
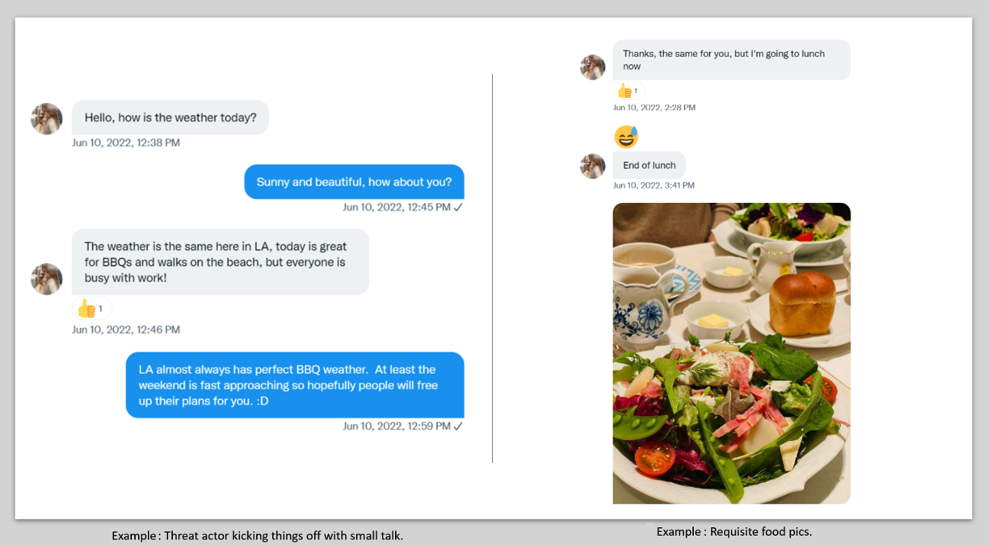
This threat starts with an innocuous conversation with an attractive stranger on social media. They often pretend to have the wrong number, or they just jump right into the pleasantries. In between gushing compliments and photos of their lunch they usually begin to discuss how they own a restaurant, beauty or nail salon, or other similar small business. Congratulations, you have just met your handler.

After chatting with the target for a few days, the threat actor will mention how they enjoy travel and the finer things in life, and that they couldn’t have done it without the sage guidance of their mentor typically a friend or relative (like a kindly uncle).
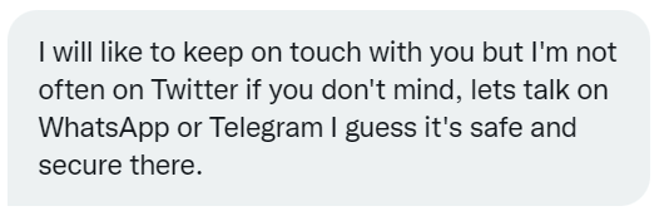
If the victim is on a social media platform like Twitter, LinkedIn, or Tinder they will start suggesting taking the conversation to Telegram or WhatsApp. They will entice a target with suggestive language, such as “let’s take this to a more private chat ?” and send racy “selfies” to encourage the victim to reciprocate and send compromising photos.
Once there, the conversation may continue along as a friendship, or they may shift the conversation similar to romance fraud and ask victims for risqué photos or videos. When they feel enough of a rapport has been established, they will invite the victim to chat with their “mentor” to discuss how they can make money.
This Little Piggy Had Roast Beef
This next phase of the fraud varies based on the threat actors’ preferences. The handler or “kindly uncle” may send the victim cryptocurrency investing white papers or help them setup a Coinbase or Crypto account. Obtaining a cryptocurrency wallet if the victim does not have one already is an integral part of the scheme. The fraudsters may work with the victim on an individual basis or invite them to a chat group, typically on WhatsApp, Discord, or Telegram, where dozens of other people are making money by following a “Plan Analyst,” the person who runs the individual or group chats and shares crypto advice to lend credibility to their grift.
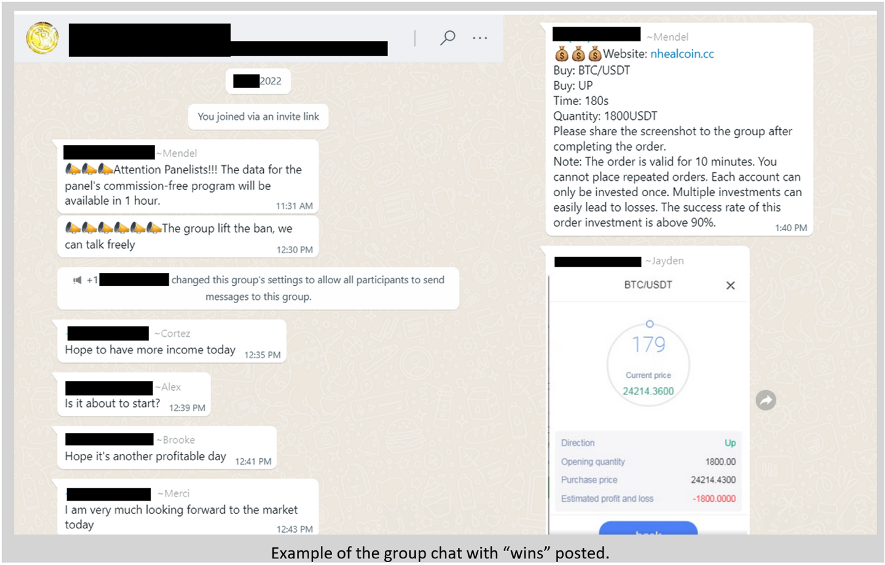
Proofpoint researchers found that once on WhatsApp or Telegram, they started receiving invitations to private cryptocurrency trading groups, and other Pig Butchering threat actors reached out frequently. Most did not seem to be aware the researcher was already in an existing group. It appears that the threat actors’ contact lists get shared without any context or enrichment.
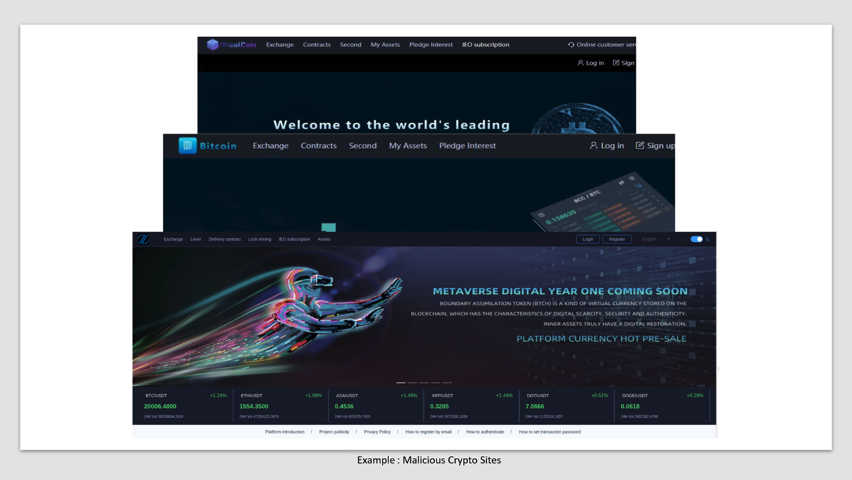
Ultimately, the victims will all be led to a fake cryptocurrency website or mobile application (see examples below). The threat actors will tell victims to purchase a small amount of cryptocurrency, typically Tether (USDT), on Coinbase.com or Crypto.com. Actors will ask the victims to send screenshots of their account to confirm they are playing along and to lay the groundwork for further instructions later. Victims will be directed to make a specific purchase (usually less than $1,000 USD) using the fake crypto site during a set window of time.
If the victim complies, they will be “rewarded” with a 10 to 20% profit almost immediately in their account balance. These wins are made up though and the money has already left the platform and into the threat actors' wallet. The handler will be very congratulatory but will urge caution as cryptocurrency can be a very volatile investment. They say, however, if people stick with “The Plan” they will make even more money. These under $1,000 purchases will go on for a bit, depending on how long it takes for a victim to begin fully trusting the threat actor, and the victim’s balance on the site will continue to grow. Once they have gained trust, the actor will tell the victim it is time to invest a larger sum. The threat actors are engaging in a well-known behavioral procedure called “classical conditioning,” in which a person’s behavior is trained to respond to a reward. In this case, investing a small amount in a fake platform and receiving a seemingly legitimate payout enough times so that a larger investment feels logical.
This Little Piggy Went to Market
Once the victim is accustomed to using the platform and increasing their account balance – or “fattened up” in Pig Butchering parlance – they will be encouraged to make larger investments. Threat actors will encourage victims to take out loans, refinance their house, sell stock holdings, etc.
If the victim starts to worry or wants to take out money, threat actors will allow them to take out a small sum, but explain the rest must remain due to taxes, international law, or anything else to placate the victim.
If this fails, threat actors will use more coercive tactics. Some victims have reported the threat actors have threatened to release any compromising photographs or videos that were previously shared, threatened to report the victim for tax fraud, or claimed that fees must be paid before closing the account. In the end, very little, if any, of the victims’ money will return to their accounts. The threat actors will shut down the website and domain and a new domain will be set up for their next victims.
On The Killing Floor
While the Pig Butchering scam is a relatively new trend in the English-speaking world it has been endemic in East Asia, especially China, for many years. In addition to cryptocurrency-based lures, these criminal enterprises have used gold, forex, stocks, and other subjects to exploit their victims. Such schemes are successful due to the intimate nature of the conversations leading up to the “slaughter”. The emotional manipulation, friendly tone, and sheer duration of the pre-exploitation phase allows genuine feelings to develop. These emotions are then exploited to manipulate the victim. Genuine emotions also fuel under-reporting of these types of losses, as people feel shame about being duped and betrayed by someone they trusted, and do not wish to share with family, friends, or even law enforcement. Some victims have reported becoming suicidal. Causing shame and embarrassment are key goals for threat actors that leverage this type of social engineering to exploit victims, similar to romance fraud. This ensures their schemes have longevity due to victims keeping their exploitation private.
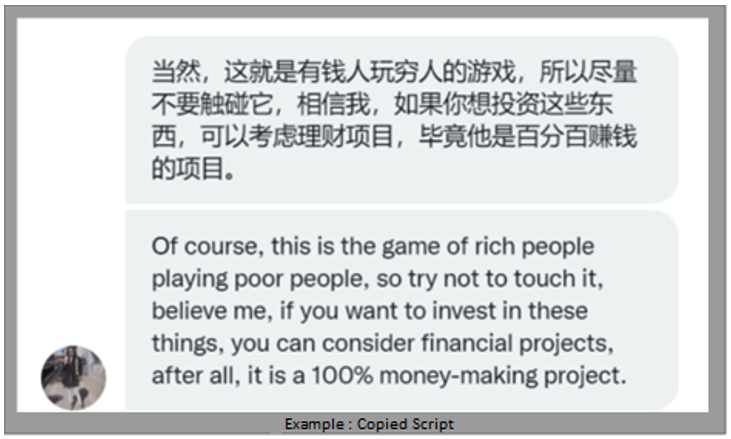
Another reason the threat actors are so successful is the sheer scope of the criminal enterprise. According to GASO, many people are employed to write curated scripts, and these branching scripts are constantly refined as more and more people are duped. They utilize trainers to instruct new recruits on how to react when things go off script. Below is an example of our researcher receiving a script copied from its native Chinese and pasted into the chat by accident.
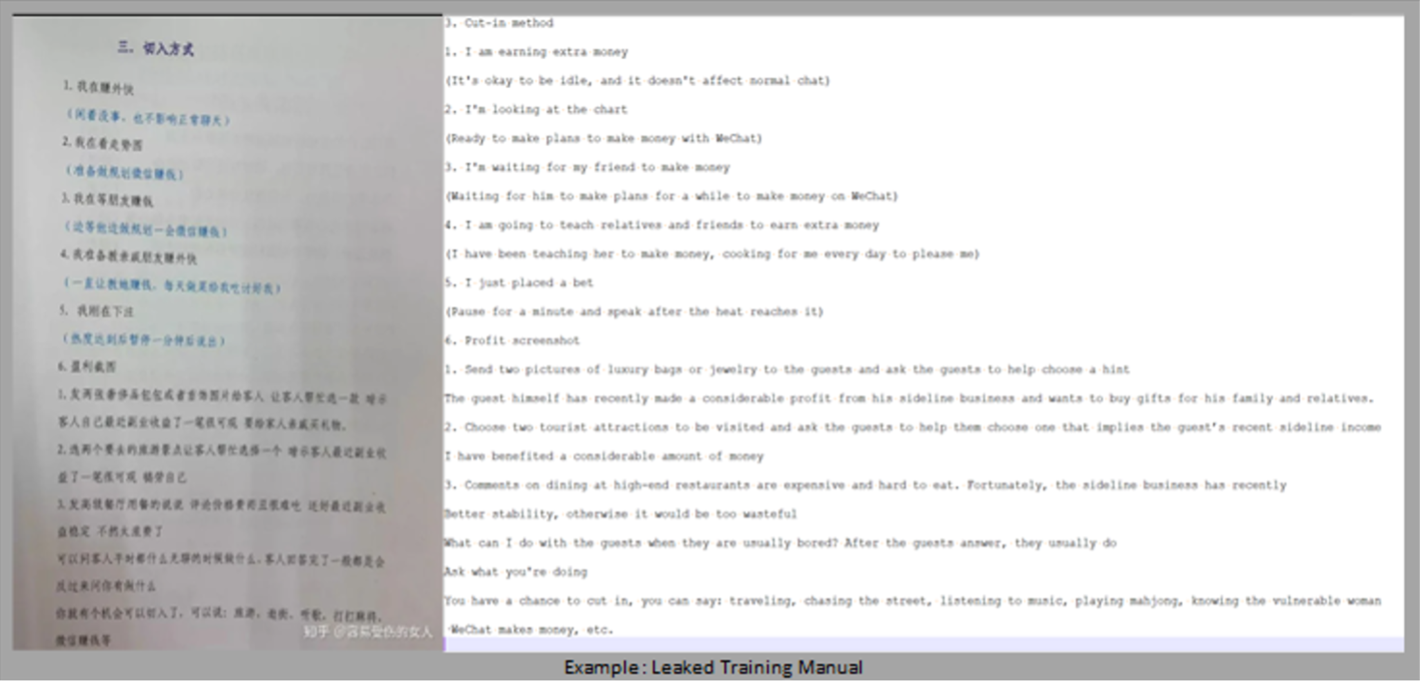
Some alleged training documents have been leaked online from people who claim to be inside of these organizations.
They likely employ IT staff to stand up websites and apps as the speed at which it is done would require a professional. Threat actors appear to have been trained to not click links. When our researcher sent URLs capable of obtaining IP/location data, they were rebuked by the threat actors and typically resulted in our researcher being blocked.
While some of these actors willingly participate in criminal activity, many are reportedly unwilling victims themselves. According to a recent report in Vice, many people conducting Pig Butchering fraud in Cambodia are victims of human trafficking and are being held against their will by people who force them to conduct illicit activity. Recently, Cambodian authorities announced a crackdown on the illegal employment schemes supported by human trafficking and slave labor.
This Little Light of Mine
The recent increase in this type of scam is concerning. Exposure has forced threat actors to pivot into new markets which may explain the rise in reported cases in English-speaking countries and an increase in Pig Butchering message lures received on social media platforms. Only by shining a light on these practices can we force these criminals back into the dark pits they climbed out of.
While education is the cornerstone defense against social engineering- based threats, unfortunately it isn’t foolproof. Throughout these engagements, Proofpoint analysts have been adding malicious crypto sites and their email verification domains to block lists and Proofpoint threat detection rules. Emerging Threats network IDS detections are also being developed to detect the malicious crypto sites.
Ways to spot a pig butcher:
- The 3 P’s – Pretty Polite People messaging you out of the blue.
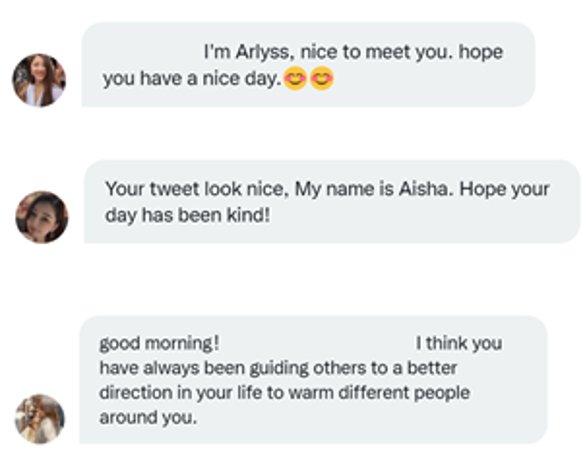
- They will ask to switch platforms – often citing it as safer.
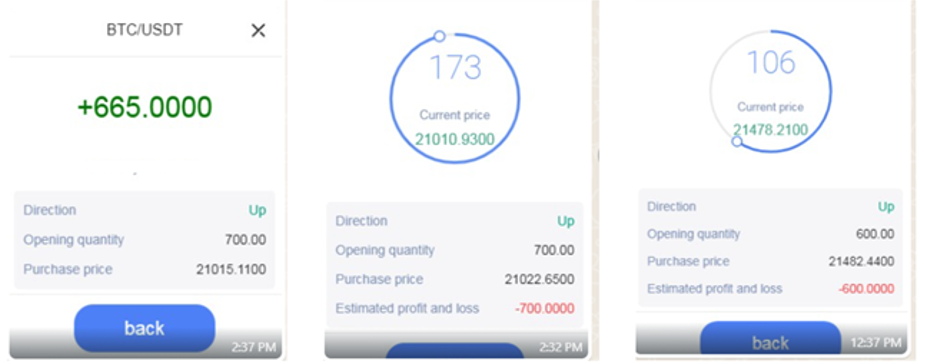
- If you are invited to a crypto chat room and people start posting screenshots that resemble examples below you should exit immediately.
Indicators of Compromise
|
Indicator |
Description |
|
zvip[.]zone |
Pig Butchering Domain |
|
xtfkskpk[.]buzz |
Pig Butchering Domain |
|
meymytum[.]xyz |
Pig Butchering Domain |
|
vwtryf[.]xyz |
Pig Butchering Domain |
|
eumfpbva[.]xyz |
Pig Butchering Domain |
|
nhealcoin[.]cc |
Pig Butchering Domain |
|
zvip[.]zone |
Pig Butchering Domain |
|
hitbicvip[.]com |
Pig Butchering Domain |
|
hitbic[.]net |
Pig Butchering Domain |
|
oslint[.]com |
Pig Butchering Domain |
|
maskexc[.]com |
Pig Butchering Domain |
|
coinss[.]pro |
Pig Butchering Domain |
|
qklyz[.]com |
Pig Butchering Domain |
|
coinline[.]pro |
Pig Butchering Domain |
|
skgroup[.]vip |
Pig Butchering Domain |
|
galaxycoin[.]vip |
Pig Butchering Domain |
|
nhchain[.]vip |
Pig Butchering Domain |
|
lanbing[.]club |
Pig Butchering Domain |
|
fwhtoken[.]com |
Pig Butchering Domain |
|
s-coin[.]vip |
Pig Butchering Domain |
|
walletput[.]com |
Pig Butchering Domain |
|
okx-us[.]net |
Pig Butchering Domain |
|
mitokenex[.]com |
Pig Butchering Domain |
|
flyscoin[.]com |
Pig Butchering Domain |
|
autoecofxmarkets[.]com |
Pig Butchering Domain |
|
ensf[.]agency |
Pig Butchering Domain |
|
shopwse[.]com |
Pig Butchering Domain |
|
beybit[.]com |
Pig Butchering Domain |
|
bihuo[.]top |
Pig Butchering Domain |
|
bn93[.]com |
Pig Butchering Domain |
|
sklge[.]com |
Pig Butchering Domain |
|
tgbone[.]com |
Pig Butchering Domain |
|
rkez[.]xyz |
Pig Butchering Domain |
|
bitget-tw[.]com |
Pig Butchering Domain |
|
cme-cn[.]com |
Pig Butchering Domain |
|
kucoinusa[.]com |
Pig Butchering Domain |
|
266wrd[.]com |
Pig Butchering Domain |
|
financeaka[.]cc |
Pig Butchering Domain |
|
ettsmc[.]ltd |
Pig Butchering Domain |
|
bilinkbitex[.]com |
Pig Butchering Domain |
|
engiegpg[.]com |
Pig Butchering Domain |
|
aax[.]news |
Pig Butchering Domain |
|
ftxcn99[.]com |
Pig Butchering Domain |
|
pinduoyu[.]com |
Pig Butchering Domain |
|
hkdbitexchange[.]com |
Pig Butchering Domain |
|
acefinex[.]com |
Pig Butchering Domain |
|
acefinex[.]net |
Pig Butchering Domain |
|
acefinex[.}vip |
Pig Butchering Domain |
|
eumfpbva[.]xyz |
Pig Butchering Domain |
|
meymytum[.]xyz |
Pig Butchering Domain |
|
okx-us[.]net |
Pig Butchering Domain |
|
s-coin[.]vip |
Pig Butchering Domain |
|
vwtryf[.]xyz |
Pig Butchering Domain |
|
xtfkskpk[.]buzz |
Pig Butchering Domain |
|
mitokenex[.]com |
Pig Butchering Domain |











