Overview
The first quarter of 2019 was dominated by consistent, high-volume Emotet botnet campaigns, while banking Trojans, downloaders, and information stealers continued to round out the email threat landscape. At the same time, imposter threats and related email fraud continued to evolve, while both seasonal and event-based trends shaped threats on the web.
Among the key takeways from Proofpoint’s Q1 2019 Threat Report:
Email remains by far the most common vector for delivering malware and orchestrating phishing attacks, while imposter attacks and related email fraud continue to shift and adapt. Q1 saw seasonal dips in the volumes of most email attacks as threat actors typically take holidays and retool for the coming months, but consistent, high-volume Emotet campaigns compensated, keeping overall malicious message volumes similar to previous quarters.
While we had classified Emotet as a banking Trojan throughout 2018 for quarter-to-quarter comparisons, reflecting its origins as a banker and ongoing distribution of banking malware as a secondary payload, in 2019 we designated the malware as a botnet, consistent with its use for spam distribution, information theft, downloading additional malware and more. Figure 1 shows an email threat landscape dominated by botnets, all of which are attributable to Emotet.
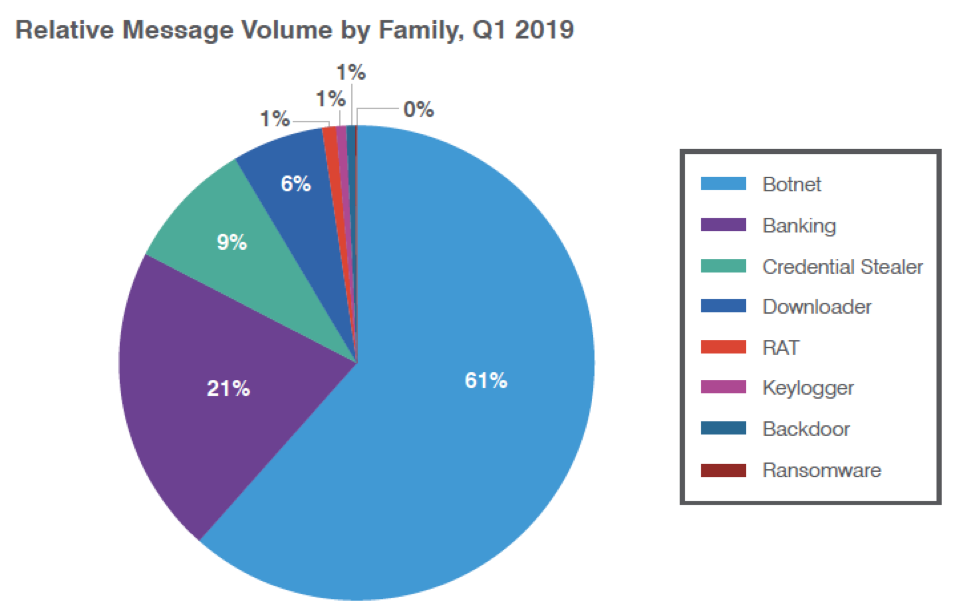
Figure 1: Relative distribution of malicious payloads, Q1 2019
Figure 2 shows the changes in the proportions of top malware families between Q4 2018 and Q1 2019. While much of the decline in banking Trojan activity is related to the reclassification of Emotet, it should be noted that Emotet has frequently been observed downloading banking Trojans as secondary payloads, complicating the picture. Also of note is the marked decline in other families, reflecting both seasonal changes and a functional shift in the preferred malware payloads of crimeware threat actors.
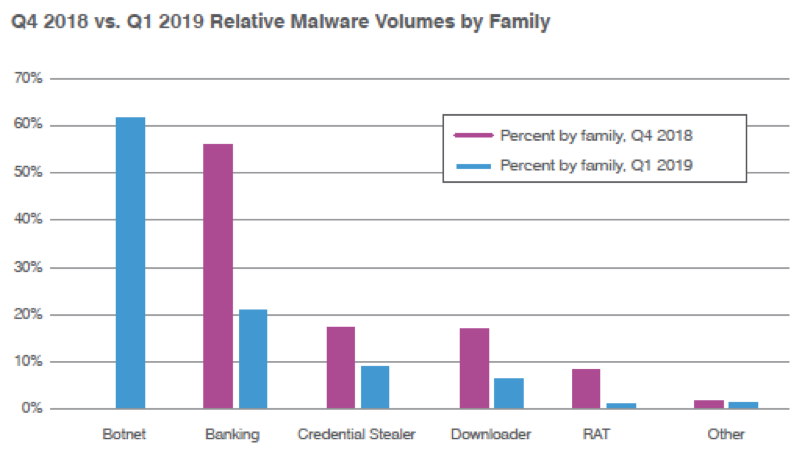
Figure 2: Relative malware volumes by family, Q4 2018 vs. Q1 2019
Email fraud, including business email compromise or BEC, leverages various identity deception techniques to trick recipients into completing actions under fraudulent pretenses. Imposter emails, frequently associated with email fraud, showed continued evolution, with subject lines referencing “Payments” displacing “Other” subject lines as the most common subject in imposter emails (Figure 3). This may be a sign of seasonal changes or part of a larger trend with threat actors focusing more narrowly on specific, effective attacks. Similarly, we also observed more attacks involving a single spoofed identity and a single attacked identity in an organization versus a higher proportion of so-called “many-to-many attacks.” We will continue to observe this data to determine whether this is an anomaly or a more significant adjustment in technique.
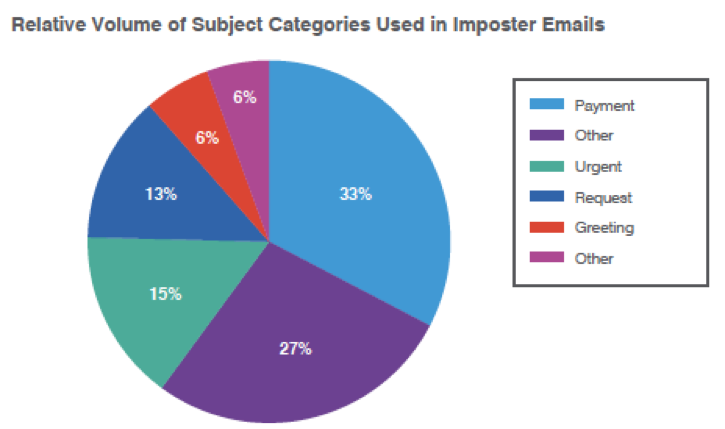
Figure 3: Q1 2019 relative volume of subject lines used in email fraud attacks
Web-based attacks and Coinhive
Proofpoint researchers regularly track Coinhive and other cryptocurrency-related threats. With the shutdown of Coinhive in March, we observed a spike in late January to 4.9 times the weekly average for the quarter while detected events dropped to near-zero after Coinhive shut down.
At the same time, detected web-based social engineering attacks like fake antivirus updates also declined, likely representing a seasonal downturn common to many aspects of the threat landscape.
Domain fraud
An inspection of over 350 million domains revealed a number of trends first noted in 2018 and continuing to play out in the first quarter of 2019. In particular, over three times as many fraudulent domains had an SSL certificate as legitimate domains while the proportion of domains identified as potentially fraudulent that resolved to an IP address was 26 percentage points higher than for all domains across the web. Lookalike domain registrations spiked at the end of the quarter, again suggesting that threat actors are tooling up for the coming months.
Proofpoint Recommendations
The Q1 Threat Report provides insight into the shifting threat landscape that can inform your cybersecurity strategy. Here are our top recommendations for how you can protect your company and brand in the coming months:
Assume users will click. Social engineering is increasingly the most popular way to launch email attacks, and criminals continue to find new ways to exploit the human factor. Leverage a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
Build a robust email fraud defense. Highly targeted, low-volume email fraud attacks often have no payload at all and are thus difficult to detect. Preventing email fraud requires a multilayered solution that includes email authentication and domain discovery, as well as dynamic classification that can analyze the content and context of emails, stopping display-name and lookalike-domain spoofing at the email gateway.
Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand. Look for a comprehensive digital risk solution that scans all domains related to your brand and reports potentially fraudulent activity.
For more information, download the complete Q1 2019 Threat Report.











