Threat actors are constantly changing their tactics and techniques. A multi-layered approach to defense is the best way to keep up with today’s increasingly sophisticated and quickly evolving threats.
Proofpoint and Microsoft have joined forces to create just such a tool with the new Proofpoint and Microsoft Defender for Endpoint integration.
The Integration
Proofpoint Targeted Attack Protection (TAP) provides expansive threat intelligence. Microsoft Defender for Endpoint adds deep visibility on user devices. Together, this integration provides a powerful defense against cyber threats. Not only can it prevent targeted attacks, but it can stop malicious emails and URLs from being delivered to people.
The benefits go beyond improved threat protection across email and endpoints. When you add Proofpoint Threat Response Auto-Pull (TRAP), you can remediate emails that have turned malicious after delivery. This eases the workload for security operations center (SOC) teams by reducing the time they need to investigate incidents. Plus, it helps them prioritize their remediation efforts.
Here’s a closer look at why you should integrate Proofpoint with Microsoft Defender.
World-class threat intelligence
The Proofpoint Targeted Attack Protection (TAP) solution uses world-class threat intelligence to provide a clear view of the threat landscape. It constantly analyzes and correlates over a trillion data points across email, cloud, network, endpoint and social networking sources to build its threat intelligence and keep it up to date. Its analysis is unrivaled.
Proofpoint TAP protects against emails that contain malicious URLs, attachments or business email compromise (BEC) threats.
Greater endpoint visibility
Microsoft Defender for Endpoint is the most widely used endpoint protection solution in the industry. It protects endpoints by managing vulnerabilities and defending against mobile threats.
Microsoft Defender provides deep visibility into activity on users’ devices. For example, it can identify which user saved a malicious file to their device and then track the file as it spreads to other parts of the system.
In contrast, Proofpoint solutions focus on the cloud and provide visibility into outside threats.
Multi-layered protection
When it comes to detecting malicious files, URLs and other threat-related activities, Proofpoint and Microsoft enhance each other.
Through this integration, Proofpoint TAP has visibility into file activity on customer endpoints. It allows TAP to identify the users and devices affected by cyber threats and gather metadata about file activity on each device. It analyzes data such as users who clicked on malicious URLs and the impacted devices. This data enables SOC teams to better understand attacks.
It’s also highly valuable to SOC teams because it broadens their understanding of the overall threat landscape.
How it works
Proofpoint TAP detects a malicious file or non-rewritten URL that was delivered through email. It alerts Proofpoint TRAP to quarantine any related messages. If the file is malicious, Proofpoint shares the file hash with Microsoft Defender’s Custom Indicator list for endpoint protection. Then, Defender provides TAP visibility into endpoint activity for the SOC team to use. This data may include affected users and devices. It may also include metadata about file activity on each device.
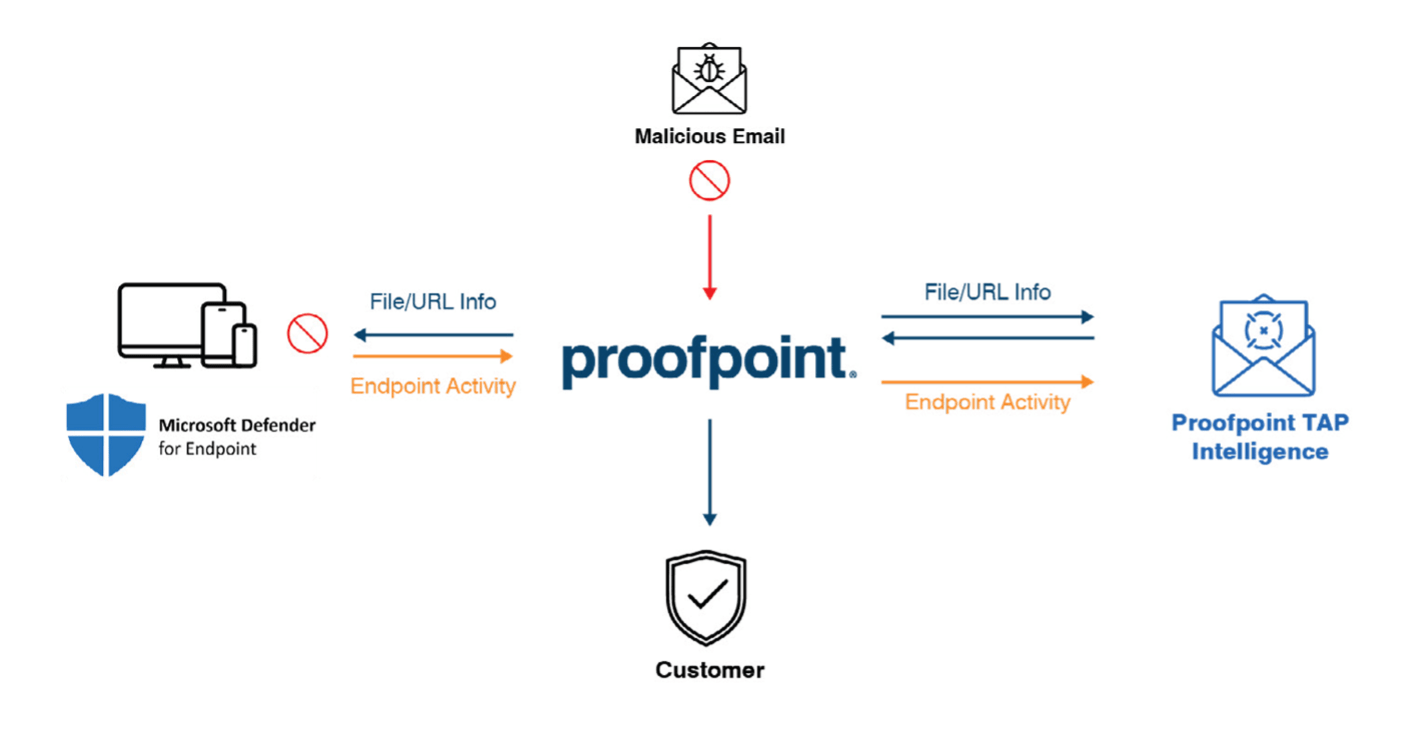
An overview of how Proofpoint and Microsoft Defender work together.
Proofpoint and Microsoft Defender deliver value
In today’s increasingly sophisticated threat landscape, you need a solution that keeps you safe against threats. When you combine Proofpoint products with Microsoft Defender you get outstanding threat protection across email and endpoints.
This integration offers multi-layered threat protection that provides deep visibility into user threats on user devices, as well as context into threats. This protects you against costly threats. It also increases your SOC team’s productivity because it reduces the time it takes to investigate incidents. Plus, it makes it easier for them to prioritize remediation efforts.
Download the brief to learn more about the Proofpoint and Microsoft Defender for Endpoint integration.











