Microsoft – The Threat Actor’s Playground. A Blog Series.
This post is an ongoing series about people-centric email attacks that Microsoft email security misses due to its outdated detection technologies and inherent limitations. These attacks cost organizations millions of dollars in losses annually and create frustration for information security teams and users.
In this series, you’ll learn more about the attacks Microsoft is missing, and we’ll explain why these types of threats are slipping past Microsoft email security defenses. These threats are:
- Business email compromise (BEC)
- Ransomware
- Supplier fraud
- Account compromise
- Weaponized file sharing
Subscribe to our blog at the bottom of this page to stay up to date on these misses that may impact your organization. Also, use our Threat Assessment process to better understand your organization’s risks.
Supplier attack overview
Supplier scams are sophisticated and complex schemes to steal money. They can include credential theft and malware, but most frequently are BEC threats. According to the 2020 Internet Crime Report from the FBI’s Internet Crime Complaint Center, BEC schemes resulted in $1.9 billion in losses last year, the largest loss category of all cyber threats.
Popular BEC attack strategies include presenting a fraudulent invoice as legitimate or rerouting payment to a bank account controlled by the attacker.
According to Proofpoint research, 98% of 3,000 monitored organizations received a threat from a supplier domain within a seven-day period. Nearly three-quarters (74%) of these attacks were phishing or impostor incidents. Less than 30% of the threats sent from supplier domains were malware-related, which highlights how attackers are relying heavily on BEC-style social engineering to be successful.

Figure 1. Supplier fraud statistics
Millions of BEC attacks seen monthly
Proofpoint detects, on average, millions of BEC attacks per month. Not all of these attacks relate to supplier compromise; however, supplier fraud campaigns can have a big impact because they target the business-to-business (B2B) space, where suppliers routinely receive large payments for their goods and services.
In just the past month, and in a limited data set of threat assessments, Proofpoint detected more than 4,800 BEC threats, 84,000 attachment threats and 168,000 URL threats that slipped past Microsoft perimeter defenses. We found, for example, that:
- An international banking firm with more than 20,000 employees received over 1,800 BEC threats.
- A consumer product organization with about 9,000 employees saw over 8,000 URL and attachment threats delivered.
- A European media group with about 2,000 employees, received over 650 BEC threats that had slipped by Microsoft security.
Microsoft also has had many public instances of its own services like OneDrive hosting ransomware-linked malware shown in the below image.
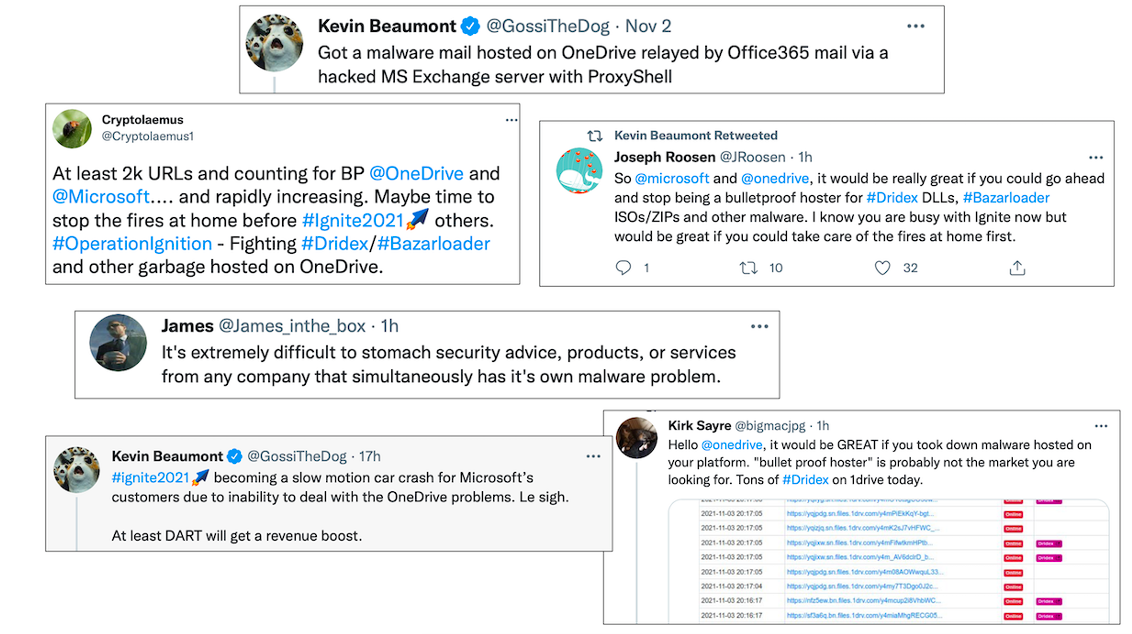
Figure 2. Tweets showing Microsoft hosting ransomware-linked malware on services like OneDrive
Following is a closer look at some of the supplier attack types missed by Microsoft that recent Proofpoint Threat Assessments surfaced.
Supplier attacks missed by Microsoft: Example 1
Supplier invoicing attacks are very common B2B-style threats. While schemes that target consumers like gift card fraud and lures like COVID-19 schemes represent a substantial number of BEC threats, the targeted or opportunistic nature of supplier fraud means the losses from these low-volume attacks can be substantial.
Supplier invoicing fraud attack overview:
- Environment: Microsoft 365
- Threat Category: BEC
- Attack Type: Supplier Invoice Fraud
- Target: Payment Distribution
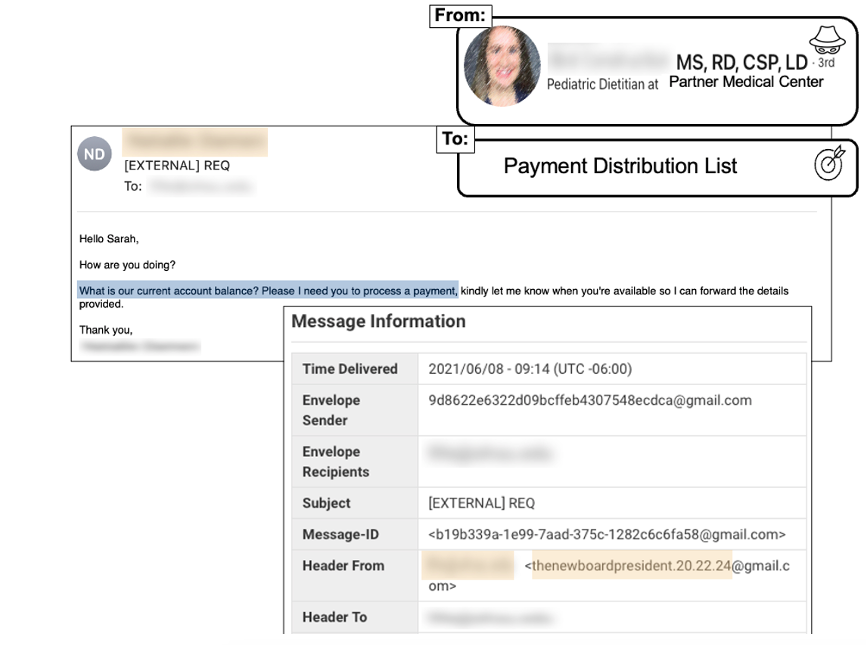
Figure 3. Example of supplier fraud missed by Microsoft
The anatomy of the attack:
This supplier invoicing attack bypassed native Microsoft email security controls. The impostor, purporting to be a former employee who joined a partner organization, used a Gmail account to request account information and attempt financial fraud.
The use of name impersonation, accompanied by a message sent from Gmail or another free email service, is a common tactic Proofpoint sees bad actors using to bypass email authentication checks like SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). Supplier attacks may also use malicious URLs or attachments in compromised accounts to get access to financial information or other high-value data.
Supplier attacks missed by Microsoft: Example 2
Supplier impersonation attacks are dangerous, but compromised accounts can be much more damaging. Users may feel a greater level of comfort engaging with these threats because even upon closer inspection, these messages appear to be legitimate because they’re sent from a legitimate domain.
Supplier compromised account credential attack overview:
- Environment: Microsoft 365
- Threat Category: Credential Theft
- Attack Type: Phishing via Supplier Compromise
- Target: Customer Project Manager
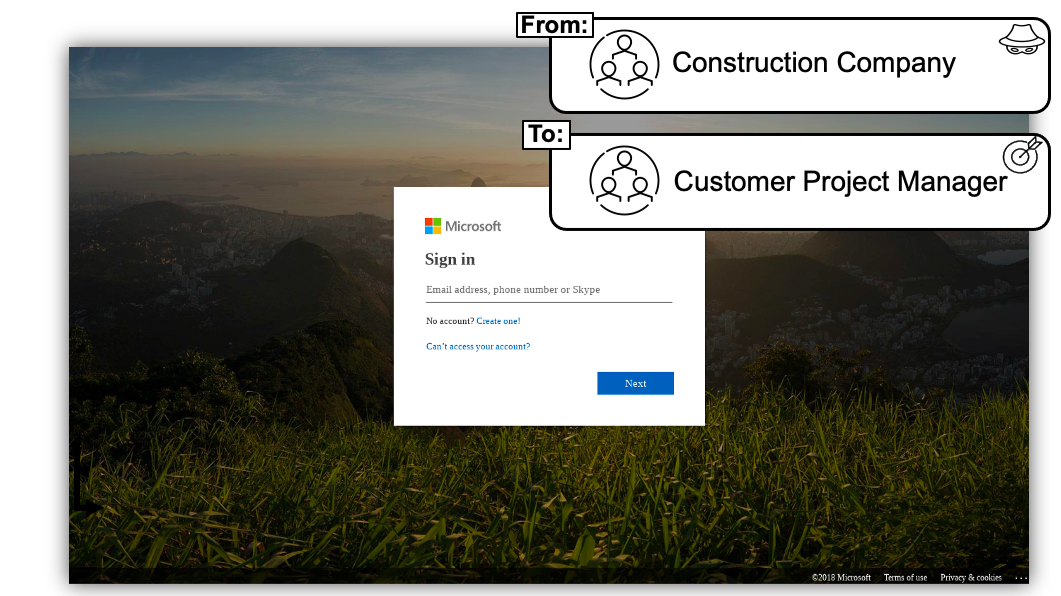
Figure 4: The above credential page impersonates a Microsoft Office 365 login, but Microsoft failed to detect and stop this attack from reaching a user
The anatomy of the attack:
This credential harvest attack was sent from a legitimate, compromised account belonging to a construction company the customer communicates with regularly. As the image in Figure 3 shows, the page is using Microsoft brand impersonation, with the attacker attempting to harvest Office 365 credentials.
Microsoft failed to stop this attack for a few reasons:
- Microsoft’s reputation scan did not detect the URL; this feature often struggles to detect new malicious URLs—including this one, which impersonated the Microsoft brand.
- This message was sent from a legitimate domain, so static reputation analysis wouldn’t identify the sender as malicious.
- The envelope didn’t trigger obvious spoof use cases.
Supplier attacks missed by Microsoft: Example 3
Here’s another example of a recent supplier fraud attack that slipped past Microsoft security: an attachment-style threat from a compromised supplier account.
Supplier compromised account attachment threat overview:
- Environment: Microsoft 365
- Threat Category: Information Harvesting
- Attack Type: Malicious Attachment
- Target: Hidden via BCC in Email
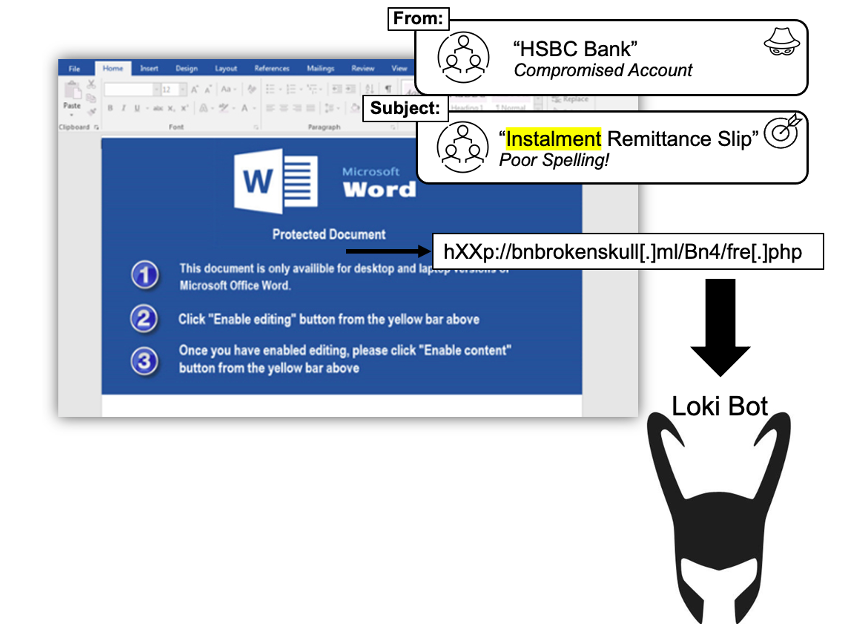
Figure 5. Example of a Loki Bot attack missed by Microsoft
The anatomy of the attack:
In this attack sent from a compromised client, the message contained Word documents that exploited various Equation Editor vulnerabilities to download Loki Bot. This bot can steal passwords from browsers, FTP/SSH applications and email accounts.
Microsoft missed this attack for various reasons:
- The message originated from a legitimate domain, so static reputation analysis didn’t identify the message as malicious.
- The message passed SPF authentication.
- The malicious payload used sandbox evasion and file obfuscation techniques.
Proofpoint’s advanced email security would have detected and also blocked this threat from activating. In fact, Proofpoint would have detected and blocked the messages in all the above examples of supplier fraud attacks that Microsoft missed.
How Proofpoint stops supplier attacks
Proofpoint is the only vendor that provides an end-to-end, integrated solution to combat supplier
attacks. We’ve built multilayered detection techniques, including a recently launched BEC detection platform known as Supernova, to defend against constantly evolving threats. This platform uses inbound and outbound gateway telemetry, supply chain risk analytics, and API data from cloud productivity platforms to uncover the most sophisticated email fraud attacks.
Our Nexus Supplier Risk Explorer feature in the Proofpoint Email Fraud Defense solution also helps organizations be more proactive in detecting and preventing supplier fraud risks, including attacks with malicious payloads. Our unmatched data set—which comes from global scale, and our deployments protecting the number one threat vector at more of the Fortune 100, Fortune 1000, and Global 2000 than any other security provider—trains the machine-learning components of URL and attachment protection in Supplier Risk Explorer.
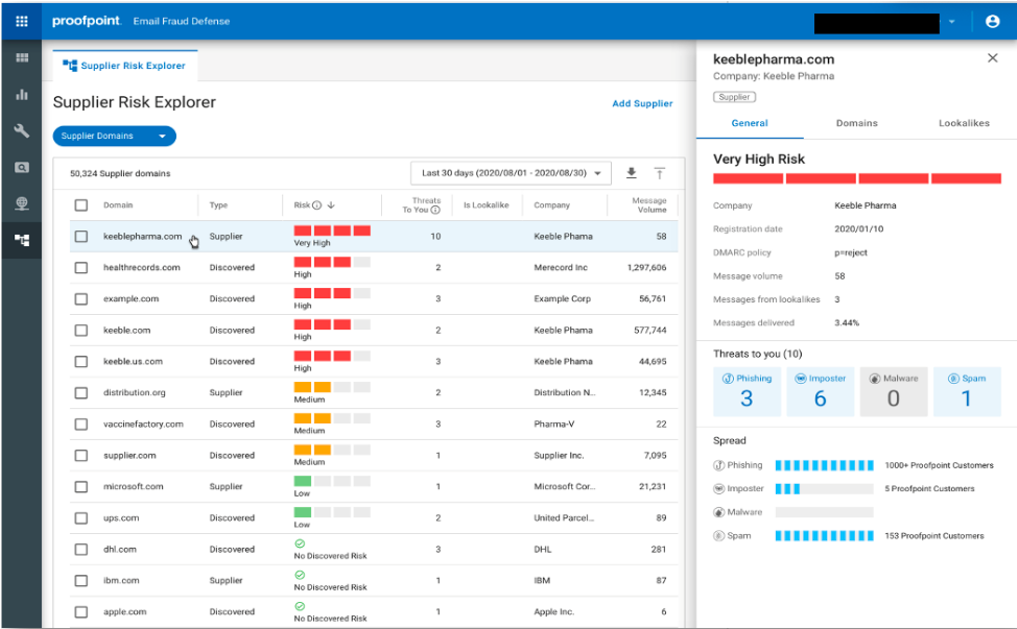
Figure 6: Supplier Risk Explorer from Proofpoint identifies supplier domains and provides visibility into which suppliers pose a risk to your organization
Recommendations to stop supplier attacks
Proofpoint takes a layered approach to stopping supplier attacks with our Threat Protection Platform. Some of these layers include our leading detection, isolation, authentication, education and automated remediation capabilities. We also use machine learning and advanced sandboxing technology to stop BEC, ransomware, phishing, account takeover, and other types of threats.
To learn more about how the Threat Detection Platform from Proofpoint can stop supplier attacks and other threats targeting your environment, contact us for a free Threat Assessment.