Email-based threats against public sector organizations are rising in both scale and complexity. One of the most popular attacks that government finance and procurement teams are targeted with is business email compromise (BEC). Recently, these attacks have become even more difficult to spot with 40% of attacks now using AI-generated content, which further blurs the line between an authentic and a fraudulent request.
What makes BEC threats so dangerous is that they typically don't involve malicious links or malware payloads. Instead, cybercriminals rely on lies, impersonation, and social engineering tactics to bypass traditional security defenses. Attacks that don’t have payloads are a blind spot for many security vendors. They result in what's known as a "design false negative," which means that they go undetected because systems simply weren’t built to see them.
Recently, our threat research team identified and blocked a sophisticated BEC campaign that sailed right through a competitor's security gate. This attack highlights the critical need for a modern, multilayered defense strategy that looks beyond the obvious.
The threat: How did the attack happen?
The attack began with an email that appeared to be a legitimate request for a proposal (RFP) from a procurement director at a major U.S. federal agency. Sent to directors of procurement at various companies, the email requested a quote for a large computer equipment supply contract. Attached was a seemingly harmless PDF document with bid details.
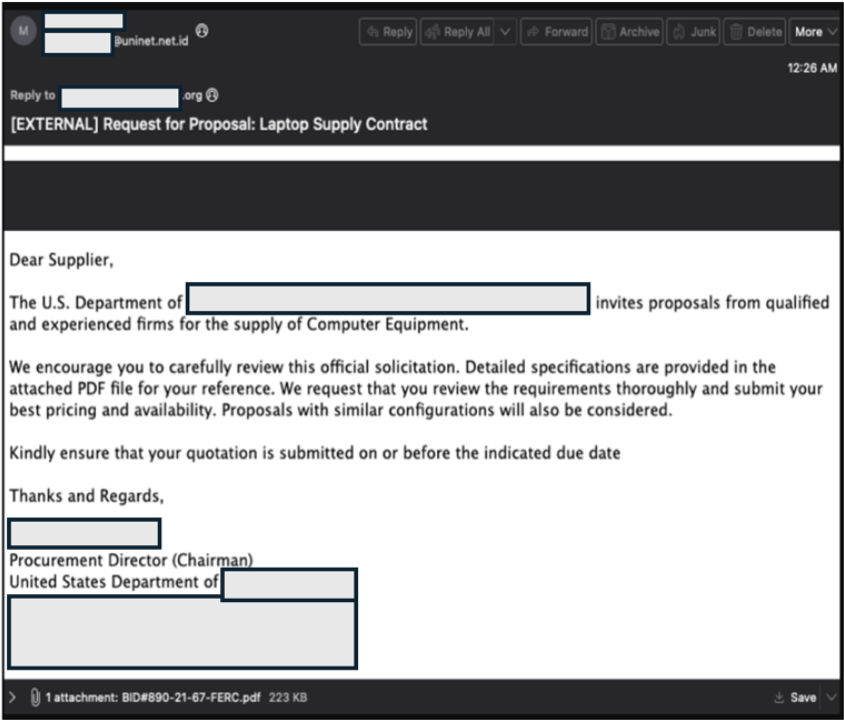
Email used by threat actor.
At first glance, the message seemed legitimate. However, a closer look revealed the attacker's subtle but effective tactics:
- Impersonation. The email impersonated a real government agency to build credibility.
- Payload-less lure. The attached PDF contained no malware, so it wouldn't trigger traditional antivirus or sandboxing analysis. The body of the email was clean and contained no suspicious URLs.
- Conversation starter. The attacker's goal wasn't a quick click. Instead, it was to initiate a conversation, establish rapport with the target, and then pivot to financial fraud, such as requesting payment to a fraudulent account.
- Domain spoofing. The attackers registered a lookalike domain, federalagency[.]org, to mimic the real agency's legitimate .gov domain. The new domain was created just last month—a major red flag.
- Header manipulation. The From field showed a plausible name, but the Reply-To header directed responses to the attacker-controlled federalagency[.]org domain, a classic BEC technique.
For the incumbent security solution, which relies heavily on spotting known bad links or malicious files, this attack was designed to be invisible. Their system, which primarily uses static dictionaries for display name spoofing, saw nothing technically wrong with the message and delivered it.
The detection: How Proofpoint stopped the attack
This threat was immediately identified and blocked for all our customers. We stopped this attack not because of one single feature, but because our Proofpoint Nexus AI platform employs a multilayered detection approach that combines AI, advanced analytics, and world-class threat intelligence.
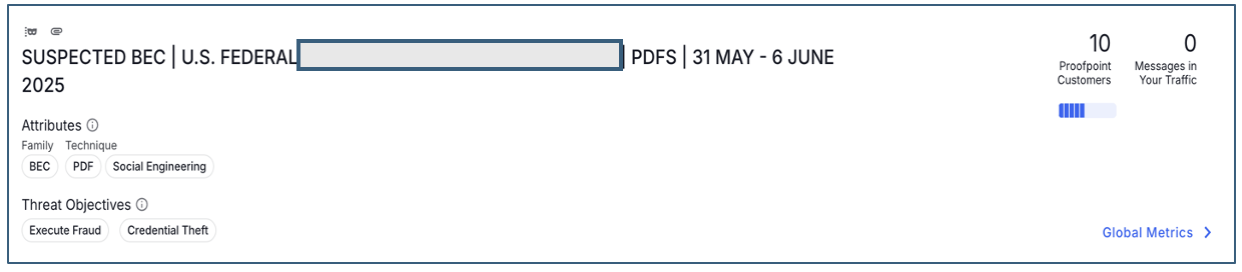
Proofpoint Nexus AI detection engines identified the threat as a lure.
Here’s how our threat research team and Nexus detection stack worked together to stop this threat:
Unmatched threat intelligence
We weren't seeing this attack for the first time. Our threat research team has been tracking this specific threat actor and their TTPs (tactics, techniques, and procedures) since 2022. We know they target supply chain professionals who work with government entities. This intelligence is continuously fed into our detection engines, allowing us to recognize and proactively block their campaigns.
Advanced BEC detection
Our Nexus detection stack is purpose-built to stop impersonation attacks. It analyzed multiple signals in real time and immediately identified the threat. Our Nexus Relationship Graph (RG) recognized that the email came from an uncommon sender—someone who does not frequently correspond with anyone at this government agency. Our Nexus Machine Learning (ML) engine identified that the domain was a suspicious lookalike that had been recently registered—and that there was a mismatch between the From and Reply-To fields. Together, these factors resulted in the message receiving a BEC score of 100, leading to an immediate block.
Deep content analysis
Our intelligence extends to the content itself. Through our research, we know that the real federal agency embeds a specific digital tag in their official PDFs. Our Nexus Threat Intelligence (TI) engine recognized that the attacker's PDF was missing this tag and flagged the situation as strongly suspicious. Furthermore, the subject line, message body, and RFP language were all consistent with previous campaigns from this tracked actor.
This combination of deep historical intelligence and advanced Nexus detection capabilities allowed us to see what others couldn't: a dangerous impersonation attack hiding in plain sight.
The stakes are higher than one email
BEC attacks accounted for 73% of all reported cyber incidents in 2024, underscoring their disproportionate impact on government and regulated sectors, including numerous federal entities. When a BEC threat like this succeeds, the consequences can be severe and multifaceted.
- Financial loss. The primary target—the supplier—could be tricked into sending funds to a fraudulent account, resulting in significant financial loss.
- Brand abuse. The reputation of the impersonated government agency is damaged, making legitimate partners and suppliers wary of future communications.
- Erosion of public trust. These attacks undermine citizen and business confidence in the security of government operations and services.
Threat actors are constantly evolving, and security providers must evolve with them. Payload-less threats that rely on social engineering are becoming more common because they work. Defending against them requires a solution that can analyze context, behavior, and reputation—not just files and links. Our success in blocking this campaign is a testament to our continued investment in the intelligence and technology needed to stop the threats of today and tomorrow.
Learn more about Proofpoint Core Email Protection.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, check out our other blogs in this series:
- Uncovering BEC and Supply Chain Attacks (June 2023)
- Defending Against EvilProxy Phishing and Cloud Account Takeover (July 2023)
- Detecting and Analyzing a SocGholish Attack (August 2023)
- Preventing eSignature Phishing (September 2023)
- QR Code Scams and Phishing (October 2023)
- Telephone-Oriented Attack Delivery Sequence (November 2023)
- Using Behavioral AI to Squash Payroll Diversion (December 2023)
- Multifactor Authentication Manipulation (January 2024)
- Preventing Supply Chain Compromise (February 2024)
- Detecting Multilayered Malicious QR Code Attacks (March 2024)
- Defeating Malicious Application Creation Attacks (April 2024)
- Stopping Supply Chain Impersonation Attacks (May 2024)
- CEO Impersonation Attacks (June 2024)
- DarkGate Malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)
- Preventing Vendor Email Compromise in the Public Sector (November 2024)
- How Proofpoint Stopped a Dropbox Phishing Scam (December 2024)
- E-Signature Phishing Nearly Sparks Disaster for Electric Company (January 2025)
- Credential Phishing that Targets Financial Security (February 2025)
- Luring Victims with Free Crypto to Steal Credentials and Funds (April 2025)
- Stopping Phishing Attacks that Pivot from Email to SMS (May 2025)
- Adversary-in-the-Middle Attacks that Target Microsoft 365 (June 2025)
- Detecting and Responding to an Account Takeover (July 2025)











