Updated August 11, 2023.
Welcome back to Proofpoint Cybersecurity Stop of the Month. In our latest blog series, we explore the ever-evolving tactics of today’s cyber criminals. We also focus on the critical first steps in the attack chain—reconnaissance and initial compromise—particularly in the context of email threats.
The aim of this series is to help you understand how to fortify your defenses, so you’ll be protected against emerging threats in today’s dynamic digital world.
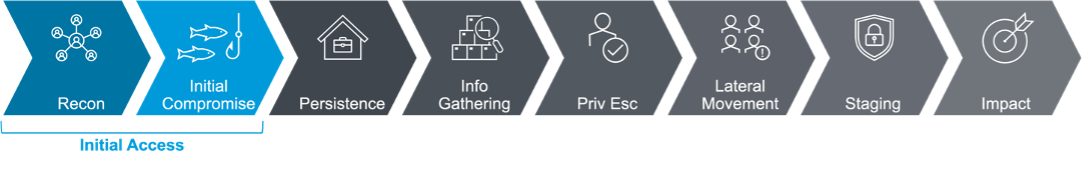
The first two steps of the attack chain: reconnaissance and initial compromise.
In our previous posts, we covered a business email compromise (BEC) and supply chain attack, and an EvilProxy attack. In this installment, we look at an insidious threat known as SocGholish.
The Scenario
During one of our recent email threat assessments, we discovered a technology customer with 4,000 users who had been exposed to a SocGholish attack that their previous email security solution had failed to detect.
What is SocGholish? SocGholish is sophisticated malware that works in multiple stages:
- First stage: malicious injects. The bad actor compromises a legitimate website and injects malicious code. The malicious code profiles users to screen for ideal candidates for further attack, at which point the second stage begins.
- Second stage: SocGholish. If the victim meets certain criteria, the JavaScript injected during the first stage smuggles in SocGholish. SocGholish is often presented as a fake browser update. If clicked, the update downloads SocGholish to the victim's device. SocGholish ushers in the third stage.
- Third stage: phone home. With SocGholish installed on the end user’s device, the malware communicates with C2 proxies from which further instructions are received. As part of the process, the bad actor may choose to initialize a fourth stage.
- Fourth stage: follow-on malware and infection. Once installed, SocGholish continues profiling the victim's device and makes subsequent calls to C2 servers for delivery of follow-on malware, often including Remote Access Trojans or ransomware.
SocGholish is a challenging malware to defend against. It is widespread, and it can evade even the most advanced email security solutions. In June alone, we saw SocGholish evade detection by prior layers of security in thousands of instances worldwide. Globally, Proofpoint detected SocGholish in over 1,000 Proofpoint customers.
The threat: How did the SocGolish attack happen?
Here’s a closer look at how the recent attack on the technology company unfolded.
1. The initial message
Victims received an email with an invitation to submit a paper for publication to a well-known academic journal. The email itself wasn’t malicious, nor was it crafted by the bad actor. As is characteristic of SocGholish campaigns, the malicious code doesn’t manifest itself until the user arrives at the compromised—but legitimate—website.
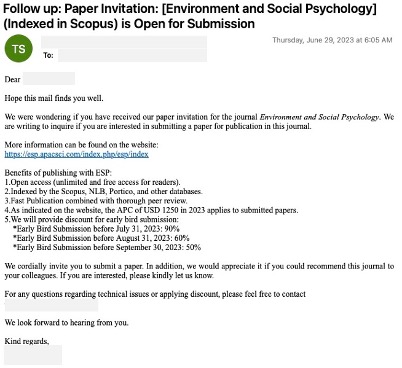
The initial email received by our customer.
2. The compromised URL
If a user clicks through to the URL within the email, the JavaScript injected at the destination begins its profiling of the user to determine eligibility for further attack. Selected users are presented with a full-page pop-up indicating their browser requires an update.
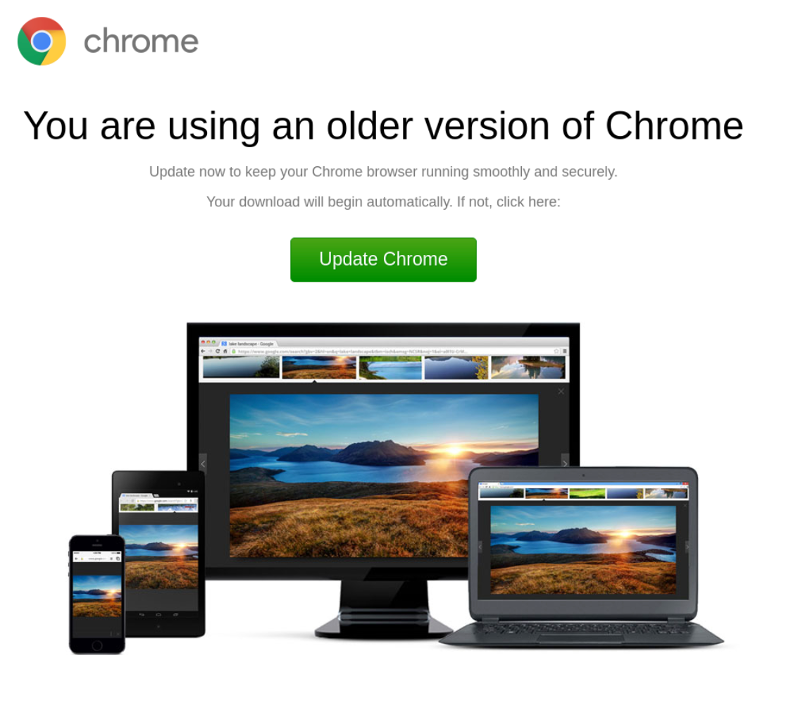
The fake browser update request.
3. Installation of SocGholish
If the user downloads the browser update package, SocGholish profiles the user’s device, its configuration, and what it can access. SocGholish then communicates with C2 proxies for further communication and any follow-on malware to be installed on the device.
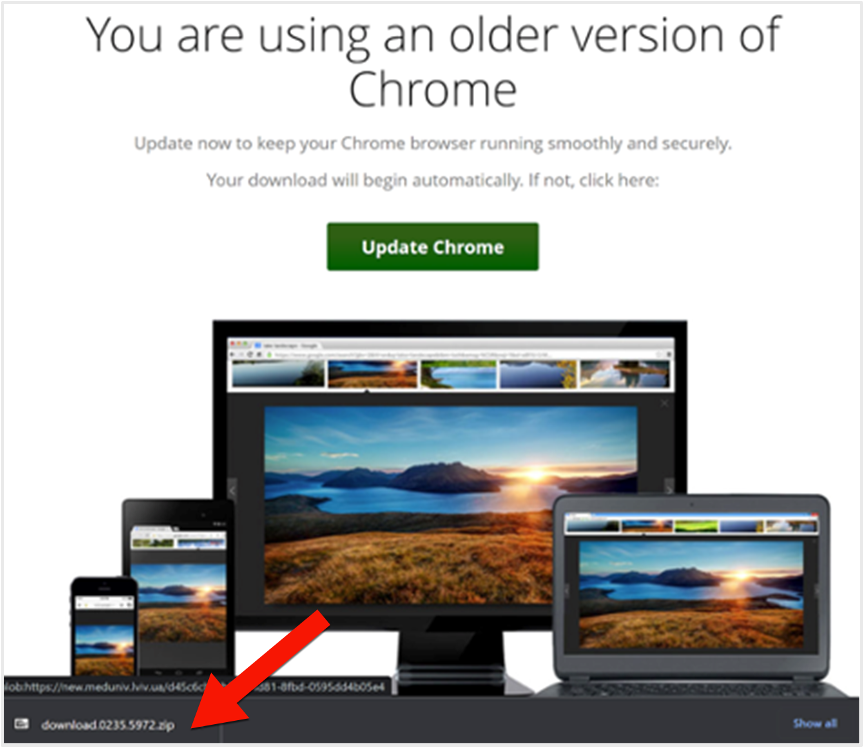
The file downloaded by initiating a fake browser update.
Detection: How did Proofpoint detect the attack?
Most email security vendors can detect malicious JavaScript. But SocGholish is a unique challenge because it is so evasive by nature.
The profiling techniques that SocGholish uses to gather data about victims, such as their IP address, operating system, browser, and local language, make detection difficult for many email security solutions. SocGholish is also known to use evasion tactics that are sandbox-aware so it doesn’t manifest if it detects a simulated environment such as a threat analyst’s sandbox. Moreover, solutions that claim to leverage AI/ML analysis for email security also struggle to detect SocGholish because the email message is not malicious and would not be considered anomalous based on previous sending patterns.
Beyond being able to observe these suspicious profiling behaviors, Proofpoint also analyzes network activity to identify malicious behaviors associated with the malware phoning home to C2 proxies. Additionally, we’ve seen redirections to a DNS service associated with SocGholish; the malware employs compromised scripts that SocGholish exploits. The injection behaviors resemble patterns observed in similar malicious campaigns, further complicating detection and mitigation.
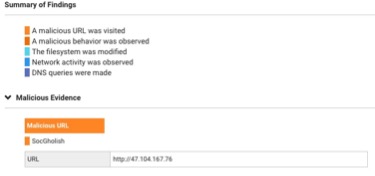
TAP Dashboard Forensics report showing activities indicating a SocGholish attack.
Proofpoint provides advanced threat detection abilities that would have identified and blocked this threat before it could be delivered. That’s because Proofpoint combines:
- Network activity analysis
- Heuristic examination of webpages
- Dynamic analysis of HTML content, payloads and other artifacts
In the attack above, Proofpoint detected unusual sending patterns and sandboxed the URLs before users clicked on any links. Without deep URL behavior analysis, solutions that rely solely on anomaly detection struggle with attacks like SocGholish since the email message and the URL are both legitimate.
The predictive sandboxing of selective URLs is a distinct feature that is unique to Proofpoint. This feature is instrumental in detecting novel, never-before-seen URL threats.
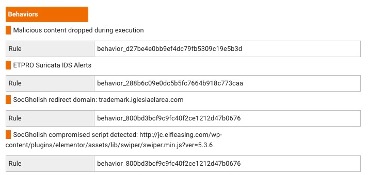
TAP Dashboard Forensics report showing specific behaviors indicating a SocGholish attack.
On top of the predictive analysis we provide, Proofpoint will proactively sandbox URLs after they have been deemed safe or cleared. Ongoing monitoring helps to ensure that any potential compromise or weaponization is detected fast.
The threat actor TA569, which is commonly associated with SocGholish, has demonstrated persistence in maintaining control over injected sites. We have observed instances where cleaned webpages are compromised again, with the site being re-injected with similar or different attacks.
Proofpoint prioritizes frequent and thorough scanning of URLs. This diligent approach is a critical factor in our ability to detect and defend against these types of threats.
What are the lessons learned?
Here are some tips for safeguarding against threats like SocGholish:
- Be careful about clicking on links in emails or on websites
- Keep your software up to date, including your web browser
- Use a security solution that can detect and block malicious JavaScript code
- Stay informed about the latest malware threats and tactics
- Consider adding Remote Browser Isolation (RBI) for an additional layer of security against novel URL threats
Proofpoint helps to break the attack chain
The SocGholish threat is a reminder that robust cybersecurity measures are a must in today’s threat landscape. It’s vital to remain vigilant and be proactive about protecting your business, users and customers from evolving dangers. Using leading-edge technologies and collaborating with trusted cybersecurity partners can help you stay ahead of threats.
We invite you to stay tuned to this blog series. By shining a light on the attack chain, we hope to disrupt it and empower businesses to take proactive steps in defending themselves against emerging threats. Together, we can strengthen cybersecurity and make the digital world safer for everyone.
Stay informed, protected and ahead of the game
To learn more about how you can protect yourself against threats like SocGholish, download the Proofpoint e-book, The Definitive Email Cybersecurity Strategy Guide.











