The Cybersecurity Stop of the Month blog series explores the ever-evolving tactics of today’s cybercriminals and how Proofpoint helps organizations better fortify their email defenses to protect people against today’s emerging threats.
In today’s dynamic work environment, email is still a primary tool for communication. But people also engage across a variety of digital channels, like Facebook, Microsoft Teams, Slack and LinkedIn.
When it comes to threats, phishing continues to grow as an attack vector. And phishing messages that include malicious URLs are particularly popular. According to Proofpoint threat research, over the past three years there has been a 119% increase in URL threats delivered by email.
What’s more, threat actors are no longer limiting their phishing attacks to email. They’re launching more phishing attacks which use a combination of email, text message and other digital channels to target victims, which increases their chances of success.
Proofpoint recently observed a bad actor start a conversation in email and then try to pivot to SMS. Here, we’ll explore how this phishing attack unfolded and how Proofpoint can prevent this from happening to your organization.
The scenario
A bad actor sent a phishing email to a user within an organization that sounded like a benign message from an external vendor. However, there were two clear red flags:
1. The attacker tried to switch the conversation from email into another channel that was unlikely to be monitored by the security team.
2. The employee was asked for their phone number. (Asking for any personal information is a red flag.)
No malicious URL or payload was included in the email, so there was nothing to analyze. As a result, the organization’s existing email security solution was unable to identify the message as a phishing email, and it was delivered to the user’s inbox.
The threat: How did the attack happen?
Here’s how the attack unfolded:
1) Luring the victim. The attacker crafted an innocent sounding message, trying to convince the recipient to provide their phone number. They suggested that pivoting the conversation from email to text messaging (SMS) would be a faster and easier way to communicate.
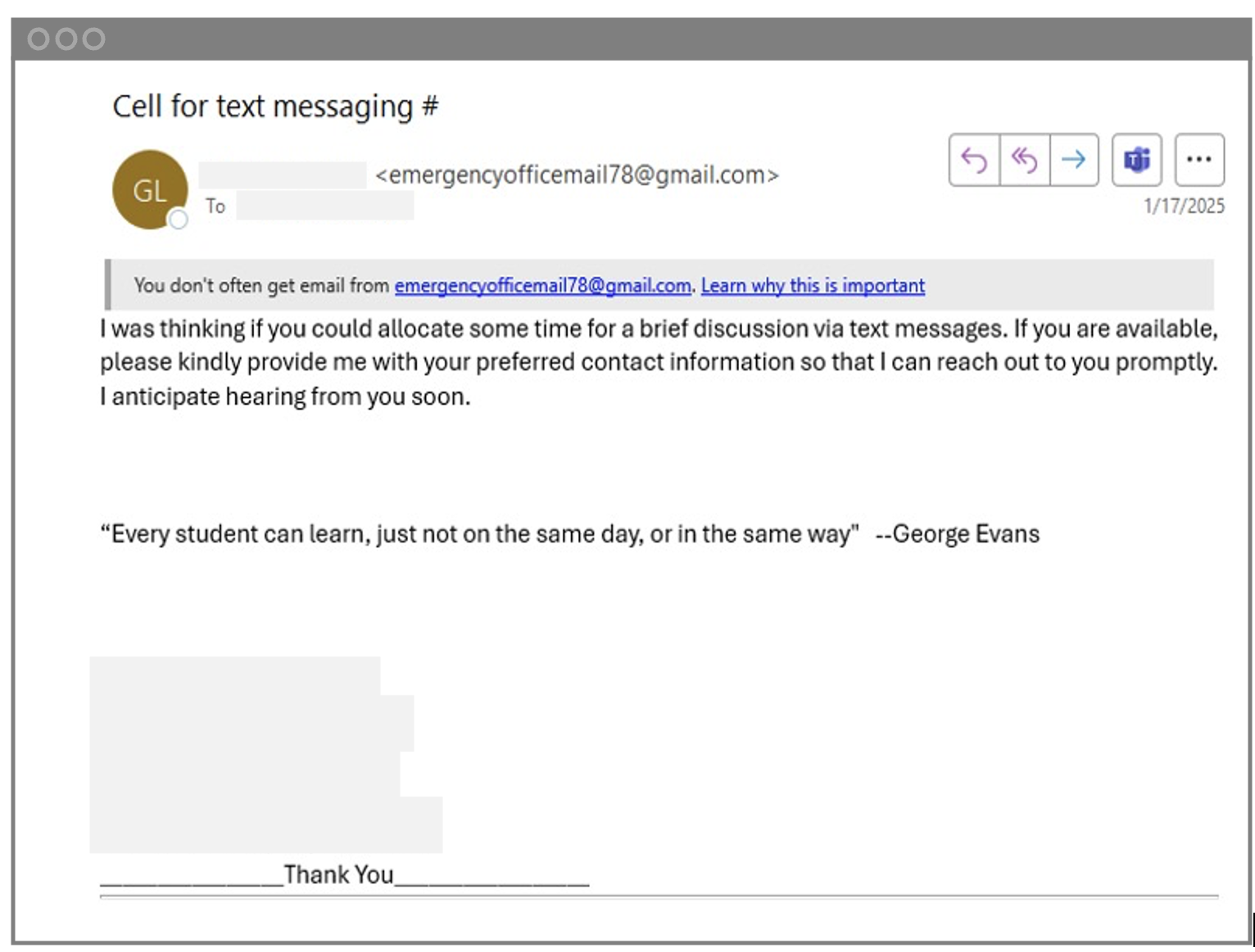
Phishing email used by threat actor.
2) Pivoting to SMS. Once a bad actor moves the conversation from email to SMS, they can convince users to perform multiple unsafe actions. This might mean asking them to click on a malicious URL, directing them to a hoax website where they enter their login credentials, filling out forms that harvest personal information, or performing actions that reveal sensitive company information.
Threat actors know messaging, collaboration and text-based digital channels are inherently less secure and are not always monitored by security operations center (SOC) teams. As a result, these types of attacks can become a serious problem for organizations.
The detection: How did Proofpoint identify this attack?
Proofpoint delivers a complete, human-centric solution to protect organizations from the widest variety of attacks today. Proofpoint Nexus is our multilayered detection stack, which includes content and reputation analysis, look-alike domain lookup, predictive sandboxing, world-class threat intelligence, large language models (LLMs), behavioral and semantic analysis and computer vision technology. All these technologies work together to create a multilayered defense that can detect and mitigate malicious messages and payloads in highly sophisticated and evolving threats.
Proofpoint was able to detect this phishing attempt, and we would have blocked it had we been the incumbent. We analyze the body of an email, the headers, payloads and any embedded URLs. In this phishing attack, there weren’t any malicious payloads or URLs to create suspicion. However, our semantic analysis LLM determined the true intent of the sender.
In this exchange, the sender was looking to move the conversation to outside the organization and away from their secure email communication channel. We also determined that the sender was not someone with whom the employee communicated regularly. These combined insights would flag the email as suspicious, and the recipient would have been warned immediately. The email would have been categorized as a “lure,” and the security team would have been alerted.
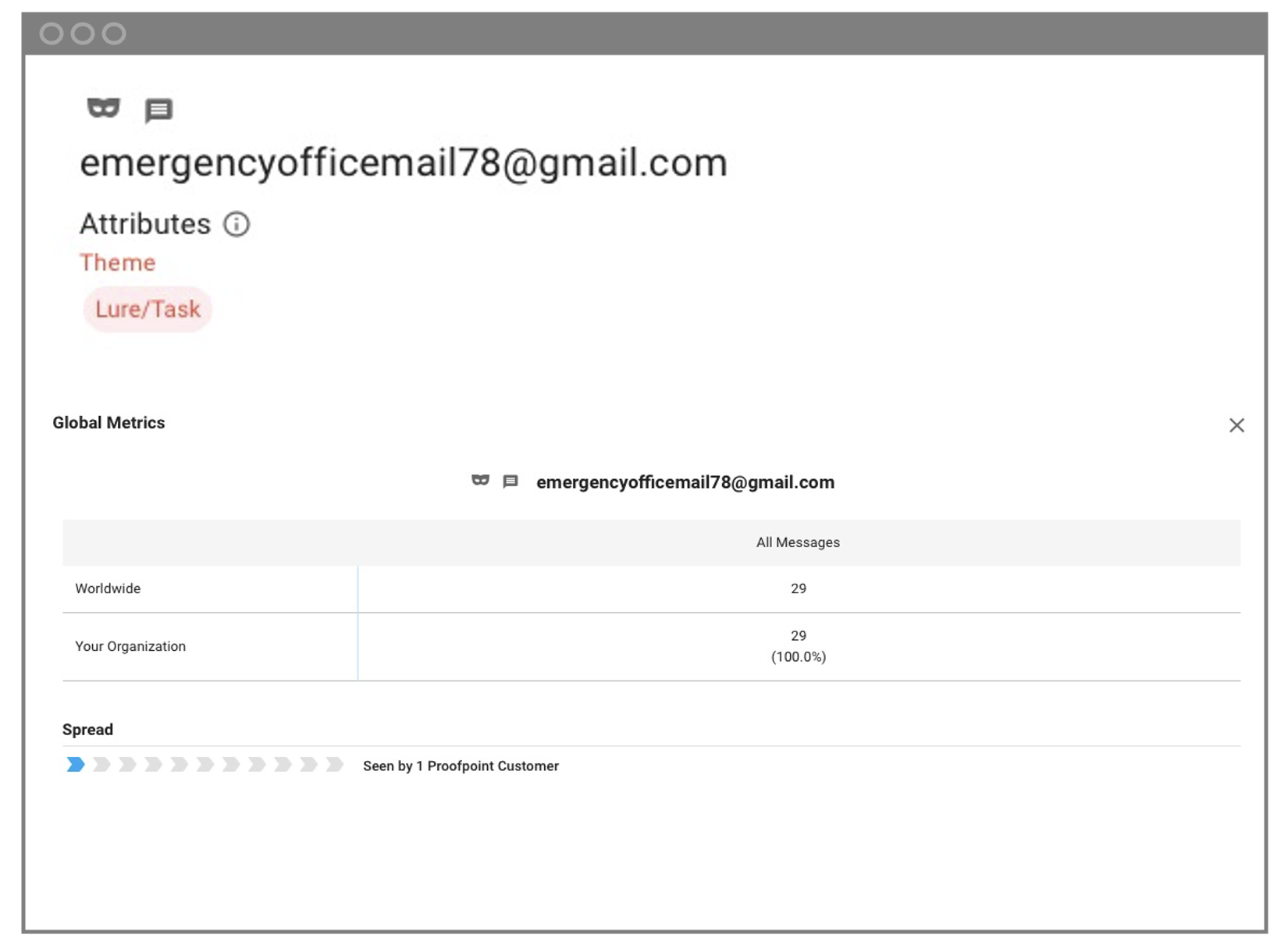
Proofpoint AI detection engines identified the threat as a lure.
Bad actors choose SMS-based phishing (smishing) attacks over other types of phishing for various reasons. First, these attacks expand their target landscape beyond email. According to Proofpoint threat research, over the past three years there has been a whopping 2,524% increase in URL threats delivered by smishing. This underscores the intensity with which threat actors are starting to target communication channels that are outside of email.
Second, research shows that people are more likely to open links in text messages. SMS click-through rates hover between 8.9% and 14.5%. By comparison, emails have an average click rate of 2%.
These factors show why threat actors are beginning to use these types of attacks more frequently. They believe that targeting users within less secure digital channels, such as SMS, will give them a higher rate of success compared to email-focused attacks.
Proofpoint understands that the threat landscape is evolving beyond email. This is why we extend phishing protection across messaging, collaboration and social media platforms. Proofpoint’s Nexus AI technology uses our industry-leading threat intelligence to conduct URL reputational analysis and block malicious URLs at the time users click. This prevents users from engaging with malicious websites and content—anywhere, anytime.
The remediation: What are the lessons learned?
It’s important to implement proactive measures to protect your organization against these types of phishing campaigns. Here are some tips:
- Adopt semantic analysis detection. AI-based threat detection should be able to identify and block malicious payloads and URLs. It should also be able to scan the body of an email and understand the underlying intent of the message. Based on that analysis, the email can then be proactively blocked, or the user can be warned of a possible threat.
- Extend phishing protection beyond email. Threat actors are using digital channels as a new attack vector to launch phishing using social engineering and malicious URLs. Extend phishing protection beyond email to secure your messaging and collaboration apps. Real-time URL inspection at click-time prevents malicious URLs from credential harvesting or spreading malware across your organization.
- Strengthen employee security education. Regular training sessions can change employee behavior over time, making them more vigilant and proactive. Users should learn to recognize phishing attempts and to be skeptical of unsolicited messages in any digital channel. Training should also emphasize the importance of inspecting email details and identifying when there’s an intent to pivot conversations into other channels such as SMS, Microsoft Teams or Slack.
Proofpoint delivers human-centric protection
The surge in sophisticated phishing attacks is a stark reminder of how dynamic the threat landscape really is. Threat actors understand that people are using multiple channels to communicate and collaborate, such as Teams, Slack and SMS. Attackers are finding new ways to get past organizations’ defenses by targeting users across these typically less secure and unmonitored digital channels. That’s why you need to be proactive when it comes to security.
While email remains the primary threat vector, cybercriminals are now also exploiting messaging platforms, collaboration tools, cloud apps and file-sharing services. Proofpoint Prime Threat Detection provides a single, comprehensive solution to help defend against these human-centric threats, both current and emerging.
To learn more about Proofpoint Prime Threat Protection, download our solution brief.
Read our Cybersecurity Stop of the Month series
To learn more about how Proofpoint stops advanced attacks, check out our other blogs in this series:
- Uncovering BEC and supply chain attacks (June 2023)
- Defending against EvilProxy phishing and cloud account takeover (July 2023)
- Detecting and analyzing a SocGholish Attack (August 2023)
- Preventing eSignature phishing (September 2023)
- QR code scams and phishing (October 2023)
- Telephone-oriented attack delivery sequence (November 2023)
- Using behavioral AI to squash payroll diversion (December 2023)
- Multifactor authentication manipulation (January 2024)
- Preventing supply chain compromise (February 2024)
- Detecting multilayered malicious QR code attacks (March 2024)
- Defeating malicious application creation attacks (April 2024)
- Stopping supply chain impersonation attacks (May 2024)
- CEO impersonation attacks (June 2024)
- DarkGate malware (July 2024)
- Credential Phishing Attack Targeting User Location Data (August 2024)
- Preventing Vendor Impersonation Scams (September 2024)
- SocGholish Haunts the Healthcare Industry (October 2024)
- Preventing Vendor Email Compromise in the Public Sector (November 2024)
- How Proofpoint Stopped a Dropbox Phishing Scam (December 2024)
- E-Signature Phishing Nearly Sparks Disaster for Electric Company (January 2025)
- Credential Phishing that Targets Financial Security (February 2025)
- Luring Victims with Free Crypto to Steal Credentials and Funds (April 2025)











