Welcome back to Proofpoint Cybersecurity Stop of the Month. In our latest blog series, we explore the ever-evolving tactics of today’s cyber criminals. We also focus on the critical first steps in the attack chain—reconnaissance and initial compromise—particularly in the context of email threats.
The aim of this series is to help you understand how to fortify your defenses, so you’ll be protected against emerging threats in today’s dynamic digital world.
The first two steps of the attack chain: reconnaissance and initial compromise.
In our previous post, we covered a BEC and supply chain attack. In this installment, we take a look at an insidious threat known as EvilProxy.
The scenario
During one of our recent email threat assessments, we discovered that a technology customer with 1,500 customers had been exposed to EvilProxy. An existing email security solution had failed to detect this threat.
What is EvilProxy? EvilProxy is a phishing toolkit that can steal user credentials and multifactor authentication (MFA) tokens. It works by sitting between the target and a legitimate webpage.
When the victim connects to a phishing page, they are presented with a fake login page that looks and acts like the real login portal. EvilProxy captures the user’s credentials and authentication session token. The bad actor can then log in on behalf of the user, bypassing MFA protections.
The threat: How did the attack happen?
Here’s a closer look at how the recent attack unfolded:
1. The deceptive message: The attack started with an email that looked like a legitimate DocuSign notice that was requesting a signature for a document. This seemingly harmless message was actually the gateway to a sophisticated cyber attack.
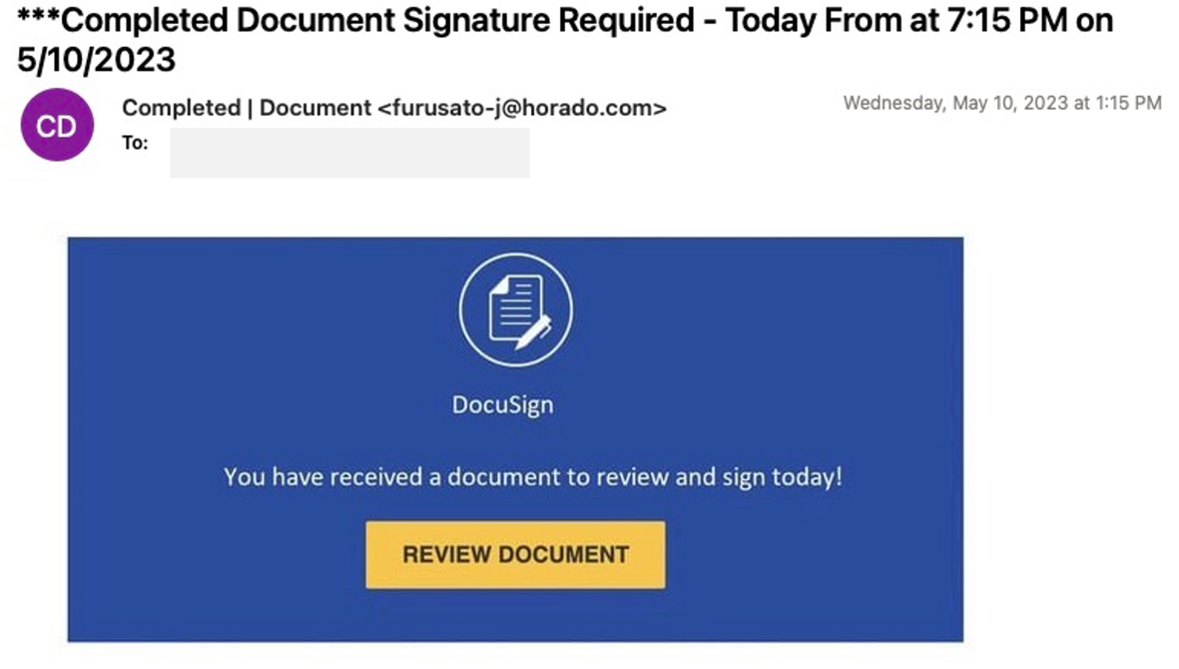
The initial deceptive email received by the customer.
2. The malicious URL: When victims clicked on the embedded URL in the email, they were sent to their own Microsoft login page, but it had the attacker’s proxy set up behind it. With this page, cyber criminals hoped to deceive users into entering their credentials willingly.
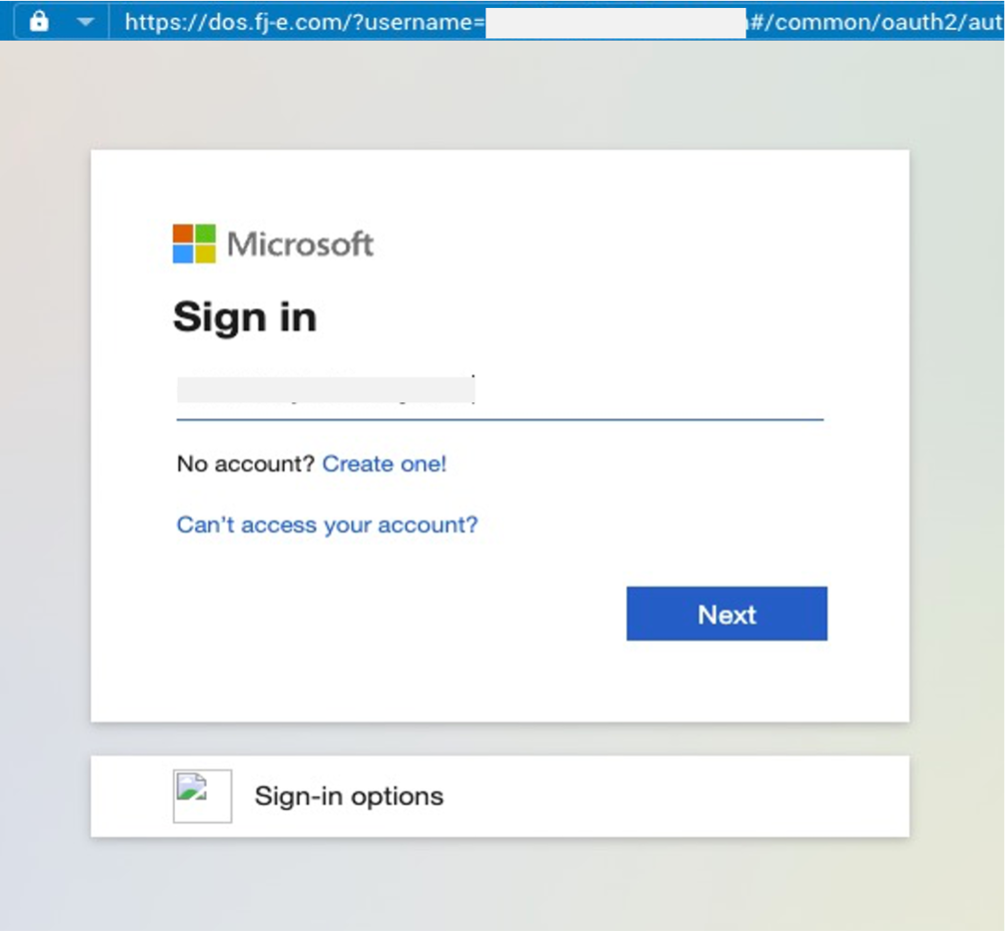
The malicious Microsoft sign-in page.
3. The EvilProxy phish framework: The EvilProxy phishing framework was the driving force behind this attack. Attackers employed a reverse proxy technique to intercept user login attempts through their actual Microsoft sign-in page. This is how they secretly extracted MFA codes and user credentials.
4. Undermining MFA verification: With the MFA codes and login credentials in their possession, the malicious actors gained free access to the compromised accounts. They obtained full control by bypassing MFA verification. That meant they posed a significant threat to the tech company and its 1,500 end users.
Detection: How did Proofpoint detect the attack?
EvilProxy and other threats that bypass MFA are becoming more frequent as bad actors adapt to enhanced security controls. Traditional methods, such as URL or IP reputation, are not enough to stop these threats.
Proofpoint uses advanced machine learning to identify the behaviors and message characteristics that are often found in credential phishing attacks. We also sandbox messages and inspect them in-depth to home in on malicious URL redirect patterns and EvilProxy frameworks.

Detecting malicious URLs in Proofpoint and the redirect chain.
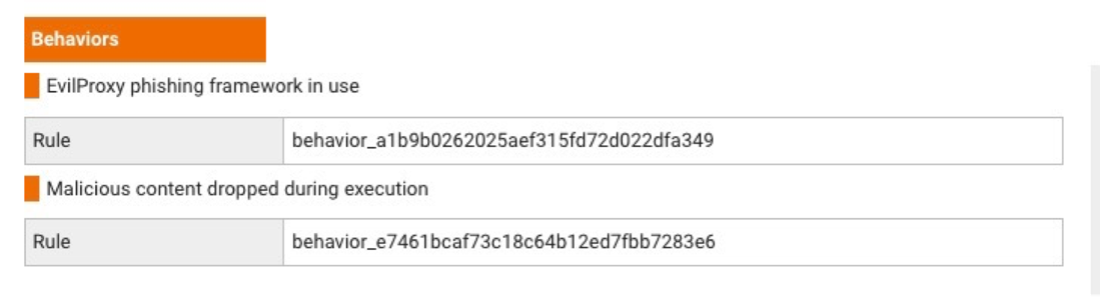
Detecting the EvilProxy phishing framework in Proofpoint.
Remediation: What are the lessons learned?
To safeguard against threats like EvilProxy, it is crucial to implement proactive measures like:
- User education: Your employees and customers are your first line of defense. Make sure they get security awareness training about all types of phishing attacks, including deceptive emails and fake login pages. This can significantly reduce their chances of being a victim.
- Robust email security: Advanced email security solutions can detect and block phishing attempts before they reach users’ inboxes. Look for a solution that uses machine learning algorithms to identify and stop these threats, like the threat detection platform from Proofpoint.
- Cloud security: A good cloud security platform can identify account takeover (ATO) attacks as well as prevent unauthorized access to your sensitive cloud resources. It covers both initial- and post-compromise activities. And it lets your security team get a closer look into which services and applications are being abused by attackers. Make sure to look for a solution that automates remediation. This reduces attackers' dwell time and keeps damages to a minimum.
- Supply chain protection: Defend your supply chain from attacks that come from email. Proofpoint Supplier Threat Protection uses advanced AI and the latest threat intelligence to detect the supplier accounts that have been compromised and prioritize the accounts that should be investigated.
- Multi-layered authentication (MFA): Strong authentication measures, like MFA, can be a big boost to your security posture. But keep in mind that the scenario we just discussed shows how traditional MFA solutions can be ineffective. That’s why it’s important to use cloud ATO automated tools, which can remediate these types of incidents promptly.
- Ongoing threat assessments: Keep your eye on the ball when it comes to watching for new threats. Regular threat assessments can help you identify your company’s vulnerabilities and enhance your incident response capabilities.
Proofpoint TAP Account Takeover protection
With Proofpoint TAP Account Takeover (TAP ATO), we extend the advanced threat detection capabilities of our Targeted Attack Protection (TAP) solution. We use artificial intelligence, correlated threat intelligence and behavioral analytics to detect and automatically remediate:
- Compromised accounts
- Malicious mailbox rule changes
- Third party-apps authorized
- Oversharing of sensitive files by cyber criminals
TAP ATO reduces dwell time with a broad range of remediation options. It speeds up response by correlating events and outlining the entire attack sequence. A timely response is essential as bad actors continue to find different methods to gain access to users’ accounts. Some examples include:
- Threats such as EvilProxy
- Password stuffing
- Data breaches
- Brute-force attacks
- Persistent access tokens
TAP ATO can help your team to investigate malicious activities and respond to threats faster, which helps to limit the risks to your business.
Proofpoint helps break the attack chain
The EvilProxy threat highlights why it’s so important to have robust cybersecurity measures. Today’s sophisticated cyber threats can only be stopped by companies when they stay vigilant and adopt proactive defenses to protect themselves and their customers. Another important step is to deploy cutting-edge technologies and collaborate with trusted cybersecurity partners, like Proofpoint.
We invite you to stay tuned to this blog series, where we will continue to uncover the latest threats, share our detection methodologies and more. By shedding light on the attack chain, we aim to break it and to empower businesses to proactively defend against these emerging threats.
Stay informed, protected and ahead of the game
To learn how to protect yourself against threats like EvilProxy, download our e-book, The Definitive Email Cybersecurity Strategy Guide.











