This blog post is part of a monthly series, Cybersecurity Stop of the Month, which explores the ever-evolving tactics of today’s cybercriminals. It focuses on the critical first three steps in the attack chain in the context of email threats. Its goal is to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
The critical first three steps of the attack chain: reconnaissance, initial compromise and persistence.
So far in this series, we have covered the following types of attacks:
- Supplier compromise
- EvilProxy
- SocGholish
- eSignature phishing
- QR code phishing
- Telephone-oriented attack delivery (TOAD)
- Payroll diversion
In this post, we examine an attack technique called multifactor (MFA) manipulation. This malicious post-compromise attack poses a significant threat to cloud platforms. We cover the typical attack sequence to help you understand how it works. And we dive deeper into how Proofpoint account takeover capabilities detected and prevented one of these threats for our customer.
Background
MFA manipulation is an advanced technique where bad actors introduce their own MFA method into a compromised cloud account. These attacks are used after a cloud account takeover attack (ATO). ATOs are an insidious threat that are alarmingly common. Recent research by Proofpoint threat analysts found that in 2023 almost all businesses (96%) were targeted by cloud-based attacks. What’s more, a whopping 60% were successfully compromised and had at least one account taken over.
MFA manipulation attacks can work several ways with bad actors having multiple options for getting around MFA. One way is to use an adversary-in-the-middle (AiTM) attack. This is where the bad actor inserts a proxy server between the victim and the website that they’re trying to log into. Doing so enables them to steal that user’s password as well as the session cookie.
There’s no indication to the user that they’ve been attacked—it just seems like they’ve logged into their account as usual. However, the attackers have what they need to establish persistence, which means they can maintain access even if the stolen MFA credentials are revoked or deemed invalid.
The scenario
Recently, Proofpoint intercepted a series of MFA manipulation attacks on a large real estate company. In one case, the bad actors used an AiTM attack to steal the credentials of the firm’s financial controller as well as the session cookie. Once they did that, they logged into that user’s business account and generated 27 unauthorized access activities.
The threat: How did the attack happen?
Here is a closer look at how this MFA manipulation attack played out:
1. Bad actors used the native “My Sign-Ins” app to add their own MFA methods to compromise Microsoft 365 accounts. We observed that the attackers registered their own authenticator app with notification and code. They made this move right after they gained access to the hijacked account as part of an automated attack flow execution. This, in turn, allowed them to secure their foothold within the targeted cloud environment.
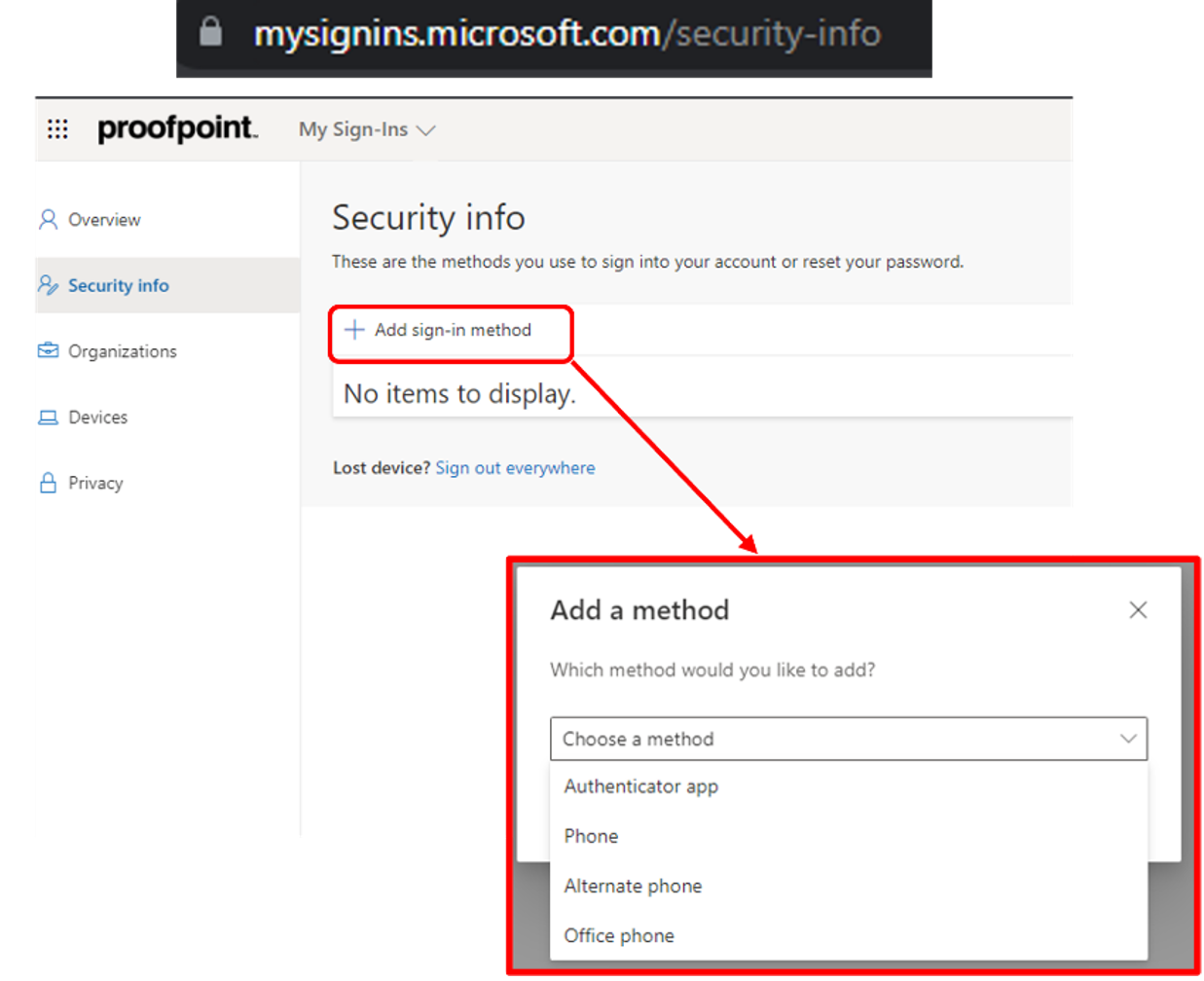
The typical MFA manipulation flow using Microsoft’s “My Sign-Ins” app.
2. After the compromise, the attackers demonstrated a sophisticated approach. They combined MFA manipulation with OAuth application abuse.
- With OAuth abuse, an attacker authorizes and/or uses a third-party app to steal data, spread malware or execute other malicious activities. Attackers also use the abused app to maintain persistent access to specific resources even after their initial access to a compromised account has been cut off.
3. The attackers authorized the seemingly benign application, “PERFECTDATA SOFTWARE,” to gain persistent access to the user’s account and the systems, as well as the resources and applications that the user could access. The permissions the attackers requested for this app included:
- Complete permanent access to the user’s mailbox
- Offline access to data
- User profile access
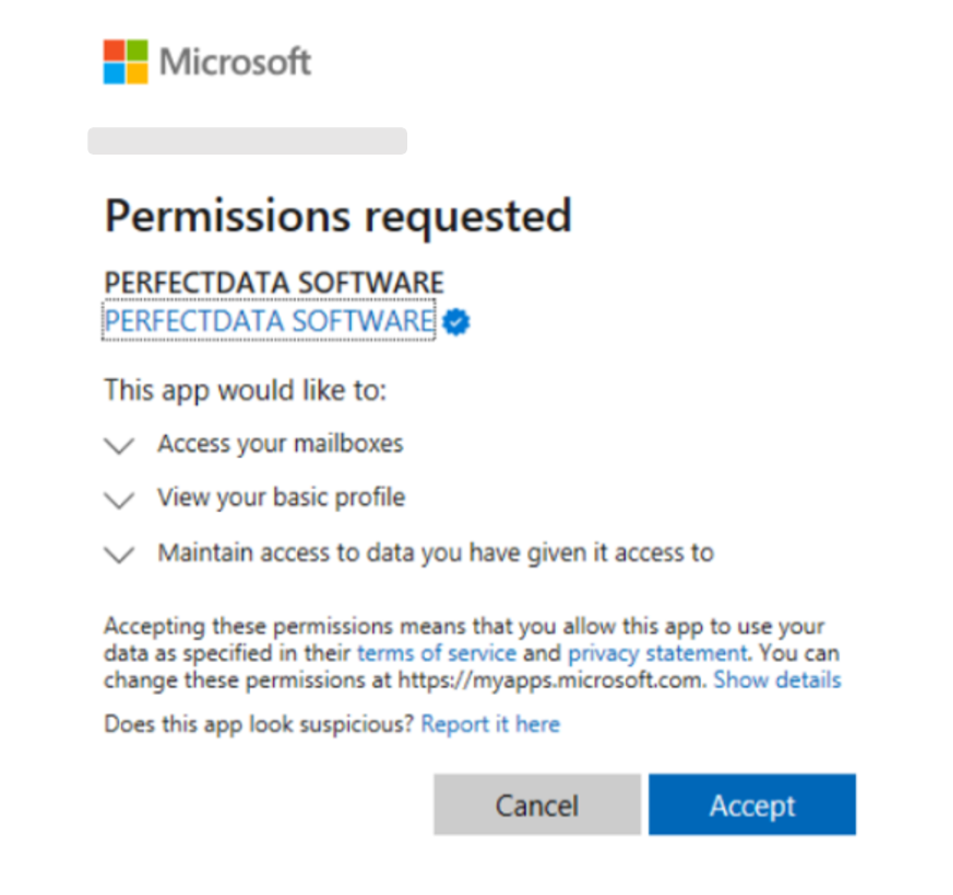
The permissions request for the “PERFECTDATA SOFTWARE” app, showing its associated scopes.
If these permissions had been granted, the attackers would have been able to steal sensitive data on a continuous basis. Also, they would have been able to spread malicious threats to internal or external user accounts.
Detection: How did Proofpoint prevent this attack?
Proofpoint TAP Account Takeover played a pivotal role in detecting and preventing these malicious activities. The platform leveraged user and entity behavior analytics (UEBA) and internal intelligence feeds to identify unauthorized access and post-compromise activities.
Proofpoint TAP Account Takeover automated the remediation of the malicious sessions and revoked the abused PERFECTDATA SOFTWARE app. That allowed the security team at the real estate company to take immediate, corrective action. In short, they broke the attack chain.
Proofpoint cloud threat researchers also advised the company as it was investigating this incident. They helped to ensure that all attacker-controlled MFA methods were removed for good, helping to reduce risk for the future.
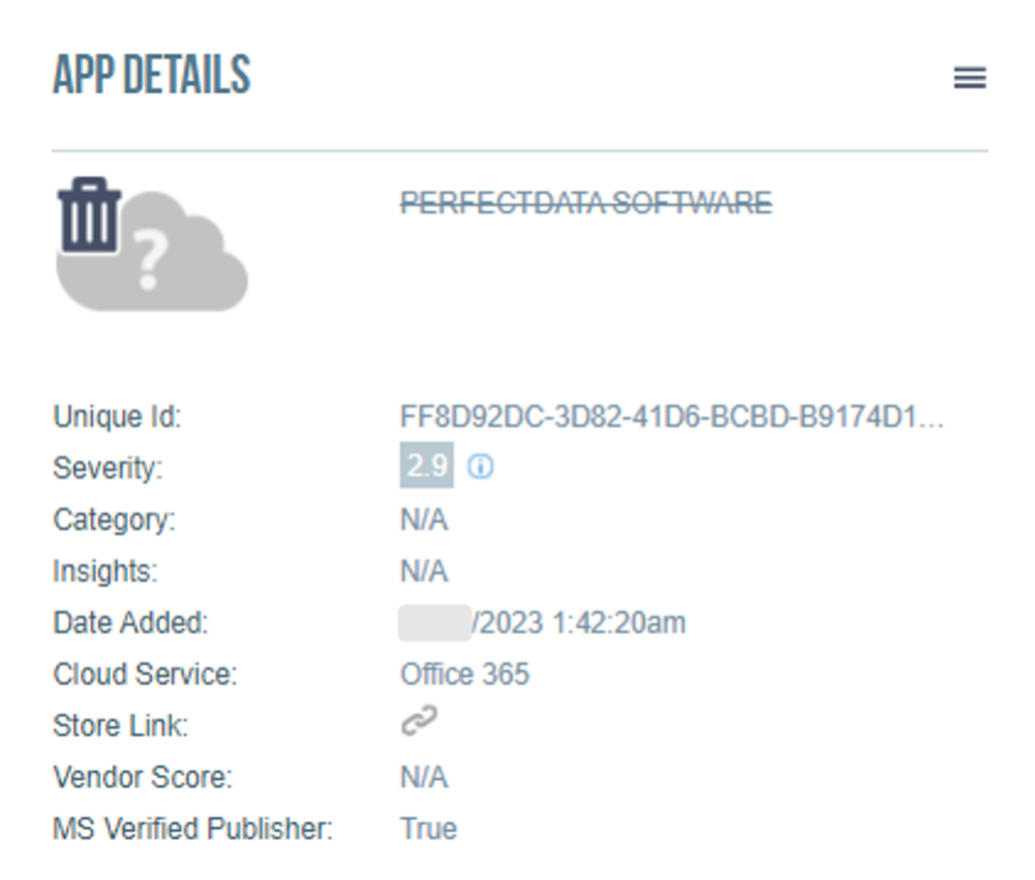
The abused third-party app was revoked automatically after Proofpoint TAP Account Takeover detected it.
Remediation: What are the lessons learned?
You can create a more secure digital environment for your company’s people and data. Here are some proactive measures that you can take to keep your business safe from threats like MFA manipulation:
- Conduct regular security audits. Doing so can help you identify and assess any potential vulnerabilities in your cloud environment. As part of that work, be sure to look for any irregularities in your MFA configurations and access logs.
- Configure your system to monitor MFA configurations. And don’t forget to enable auto-remediation. This will help to ensure that you detect unauthorized changes and mitigate them promptly. This approach can stop attackers from establishing persistence through manipulated MFA methods.
- Educate your users. Help your users to understand the risks of MFA phishing and manipulation. Conduct regular training sessions to educate them on how to recognize phishing attempts and suspicious activities. Stress that they should move fast to report unusual account behaviors.
- Integrate your security tools. Your security stack should include:
- Account takeover detection
- Anomaly discovery
- Behavioral analytics
- Real-time threat intelligence feeds to detect and block sophisticated attacks
- Create an incident response plan. Map out several MFA manipulation scenarios. Then, define how you will investigate and mitigate these incidents. Be sure to test how effective your plan really is by conducting regular simulated exercises.
Proofpoint helps break the attack chain
This MFA manipulation attack directed at a real estate firm is a good reminder of how the threat landscape is always changing. In this instance, the attacker exploited a vulnerability in an MFA system. This allowed them to bypass authentication and attempt to gain access to sensitive financial data.
To stop MFA manipulation attacks, you need to be able to detect and remediate compromised accounts in your email and cloud environments. Proofpoint TAP Account Takeover provides comprehensive visibility to help your business to detect and block attacks in real time. Our platform blocks targeted phishing attacks that could be used to trick employees into revealing MFA credentials.
By breaking links at multiple points in the attack chain, we can help your business prevent data loss and protect critical assets. The adoption of a people-centric security approach can help you to fortify your defenses against such attacks.
To learn more about how Proofpoint can help you defend against MFA manipulation, third-party app abuse and other advanced threats, download this data sheet.











