This blog post is part of a monthly series, Cybersecurity Stop of the Month, which explores the ever-evolving tactics of today’s cybercriminals. It focuses on the critical first three steps in the attack chain in the context of email threats. Its goal is to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
The critical first three steps of the attack chain: reconnaissance, initial compromise and persistence.
So far in this series, we have examined these types of attacks:
- Business email compromise (BEC) and supply chain attacks
- EvilProxy
- SocGholish
- eSignature phishing
- QR code phishing
- Telephone-oriented attack delivery (TOAD)
- Payroll diversion
- MFA manipulation
In this post, we look at supply chain compromise, which is a form of BEC. Supply chain compromise is not a new form of BEC, but we are seeing a rise in these attacks. The example in this blog post is one that Proofpoint recently detected. A law firm with 2,000 users was the intended target.
In our discussion, we cover the typical attack sequence of a supply chain compromise to help you understand how it unfolds. And we explain how Proofpoint uses multiple signals to detect and prevent these threats for our customers.
Background
Supply chain attacks are growing in popularity and sophistication at a rapid pace. TechCrunch reports that the largest supply chain compromise in 2023 cost the impacted businesses more than $9.9 billion. That incident had a direct impact on more than 1,000 businesses and over 60 million people.
In these attacks, a bad actor targets a company by compromising the security of its suppliers, vendors and other third parties within its supply chain. Instead of launching a direct attack on the target company’s systems, networks or employees, an attacker infiltrates a trusted entity within the supply chain, thereby exploiting the entity’s trust and access vis-a-vis the target.
Attackers know that enterprises with mature supply chains tend to have stronger cybersecurity defenses, which makes them challenging targets. So, rather than trying to break into “Fort Knox” through the front door, they will target the ventilation system.
Bad actors often use thread hijacking, also known as conversation hijacking, in these attacks. They target specific email accounts and compromise them so that they can spy on users’ conversations. When the time is right, they will insert themselves into a business email conversation based on the information they have gathered from the compromised email accounts or other sources. Sometimes, the attack will be bold enough to initiate new conversations.
Thread hijacking attacks, like other BEC campaigns, don’t often carry malicious payloads like attachments or URLs. Thread hijacking is also a targeted attack, so bad actors will often use a lookalike domain. (A lookalike domain is a website URL that closely resembles the address of a legitimate and well-known domain, often with slight variations in spelling, characters or domain extensions.)
This potent combination—the lack of an active payload and the use of a lookalike domain—makes it difficult for simple, API-based email security solutions to detect and remediate these types of attacks.
The scenario
Proofpoint recently detected a threat actor account that was impersonating an accounts receivable employee at a small financial services company in Florida. Through this impersonation, the adversary launched a supply chain attack on their intended target—a large law firm in Boston. They sent an impersonating message to the law firm’s controller asking them to halt a requested payment and change the payment information to another account.
Unlike API-based email security solutions that only support post-delivery remediation, Proofpoint detected and blocked the impersonating messages before they reached the controller’s inbox. As a result, the law firm was never exposed to the supply chain compromise.
The threat: How did the attack happen?
Here is a closer look at how this supply chain compromise attack unfolded.
1. Legitimate customer message
The customer sends an email to the supplier to confirm the wire payment information is correct.
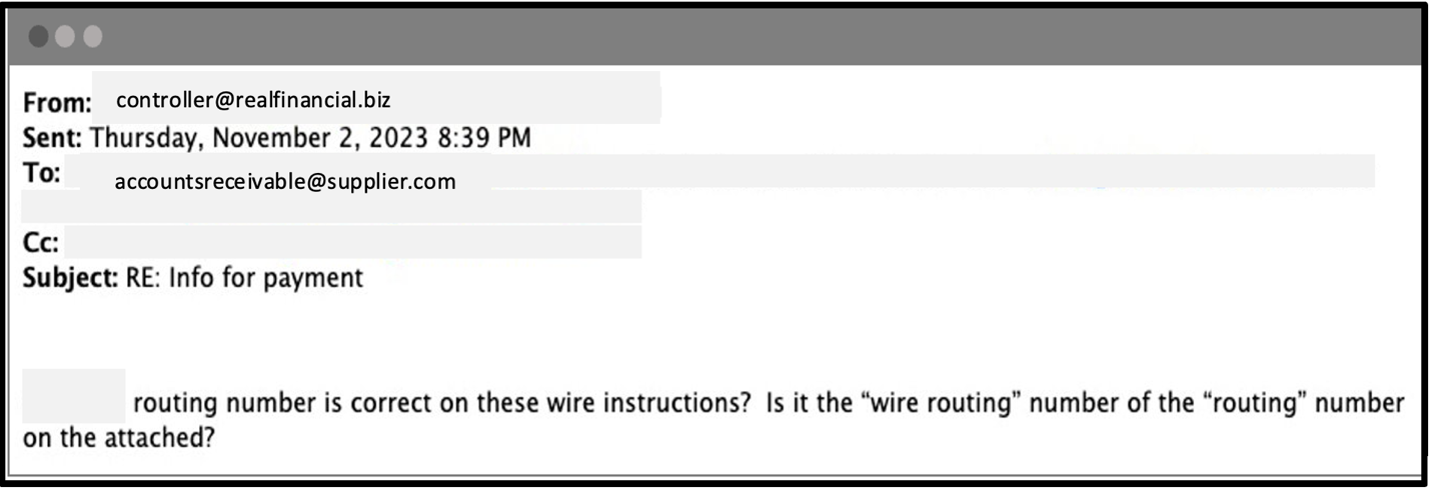
Supply chain compromise example: Email confirming wire payment information.
2. Legitimate supplier email
The supplier sends an email reply to verify the wire payment information.
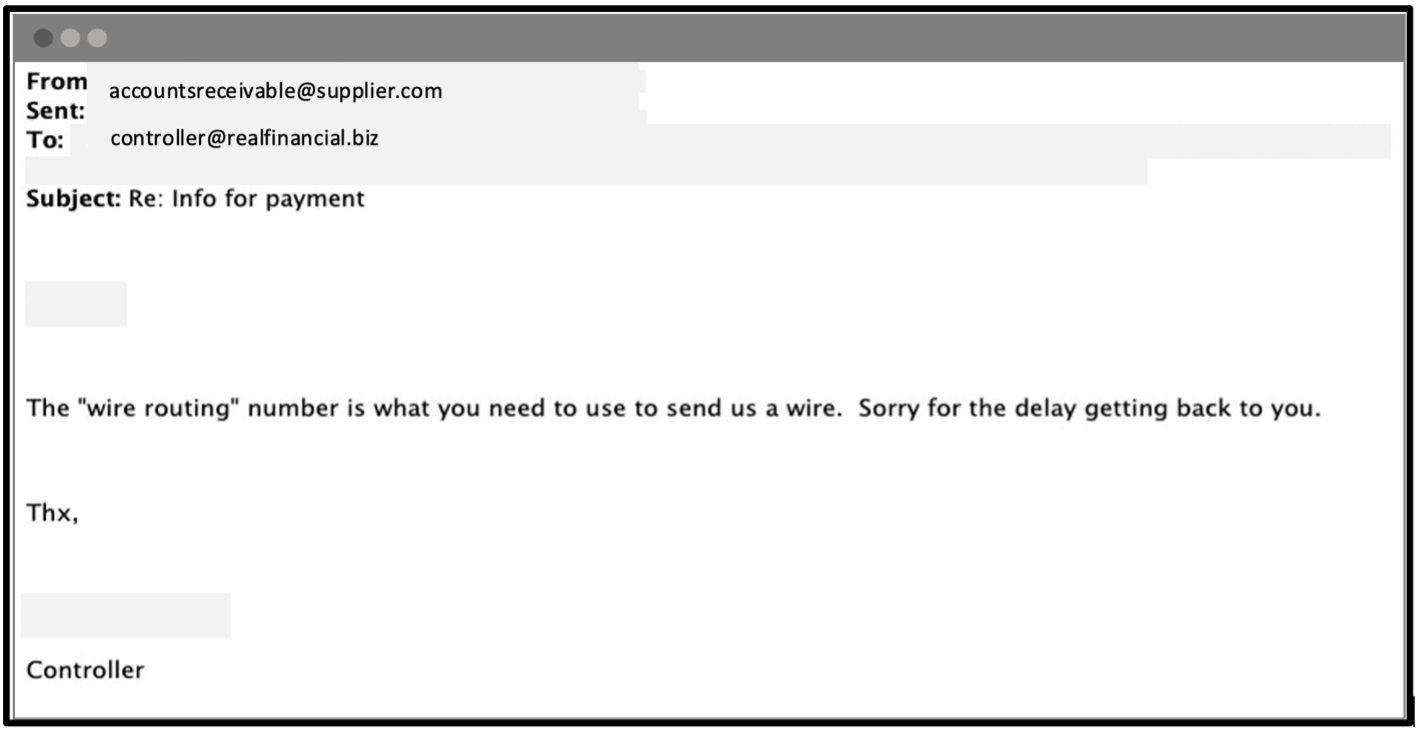
Supply chain compromise example: Email verifying wire payment.
3. Fraudulent supplier email
The attacker then enters the mix. They take advantage of this opportunity by sending an email to the customer from a different account that appears very similar to the original one but with a slight variation in the email address. This is known as a lookalike domain. One should pay attention to the additional letter in the sender's domain. To make the email seem more legitimate, the attacker copies the entire email conversation, making it seem like they are continuing the original conversation.
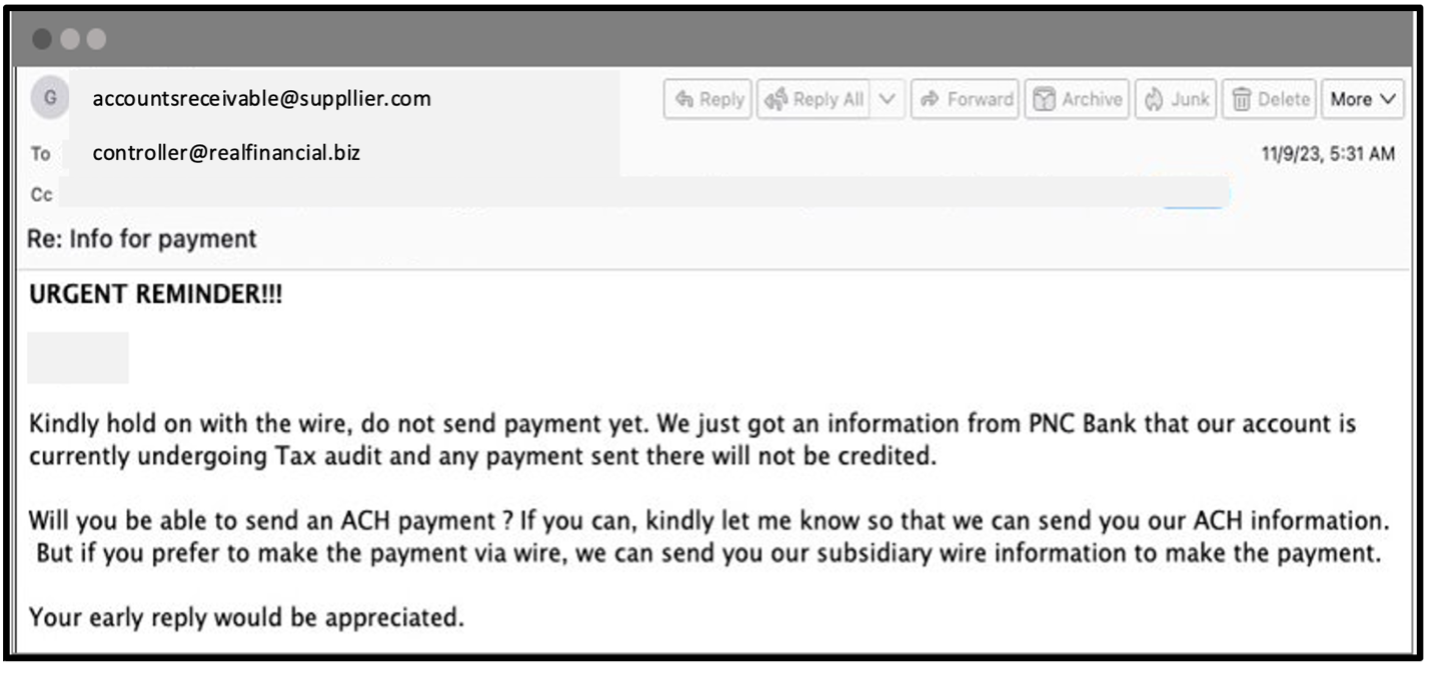
Supply chain compromise example: Fraudulent email.
4. Supply chain compromise attack sequence
The bad actor requests that the wire payment be sent to another account through an automated clearing house (ACH). The attacker is the owner of that new account.
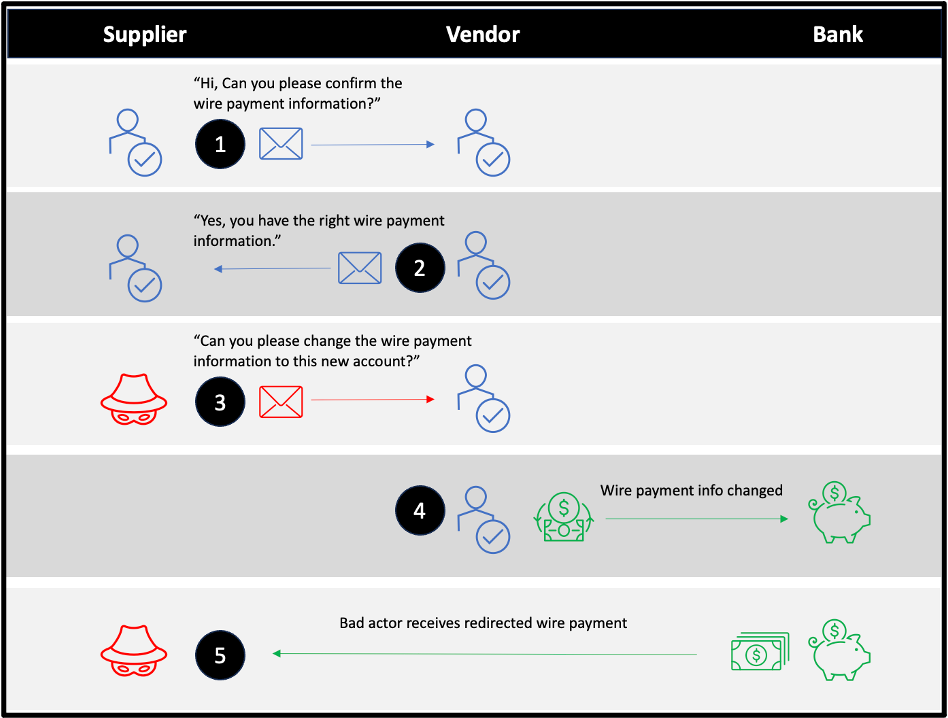
Supply chain compromise example: Attack sequence overview.
Detection: How did Proofpoint prevent this attack?
As noted earlier, supply chain compromise attacks are hard to detect because they rarely have malicious payloads. The bad actor’s goal is to use social engineering to convince the recipient of the impersonated email to change the wire payment information.
To detect these types of malicious messages, an email security tool must interpret the contextual tone as well as the intent of the message. That is how it can decipher the true objective of a message before it can be delivered to a user’s inbox.
Proofpoint uses multiple detection signals, analytic engines and behavioral artificial intelligence (AI) to determine whether business emails are legitimate or malicious. The commonality and frequency of communication from senders, lookalike domains and payment urgency are some of the signals that we use to detect and flag emails that may be malicious.
In this scenario, a supplier asked a vendor to change payment account information. Such a request is not an uncommon event in business, and that’s why API-based email security tools struggle to detect supply chain compromise attacks. These tools are very dependent on uncommon sender signals. As a result, they create a lot of false positives and alerts. This limited behavioral AI approach helps to explain why many businesses complain about the excessive noise that unusual sender patterns create.
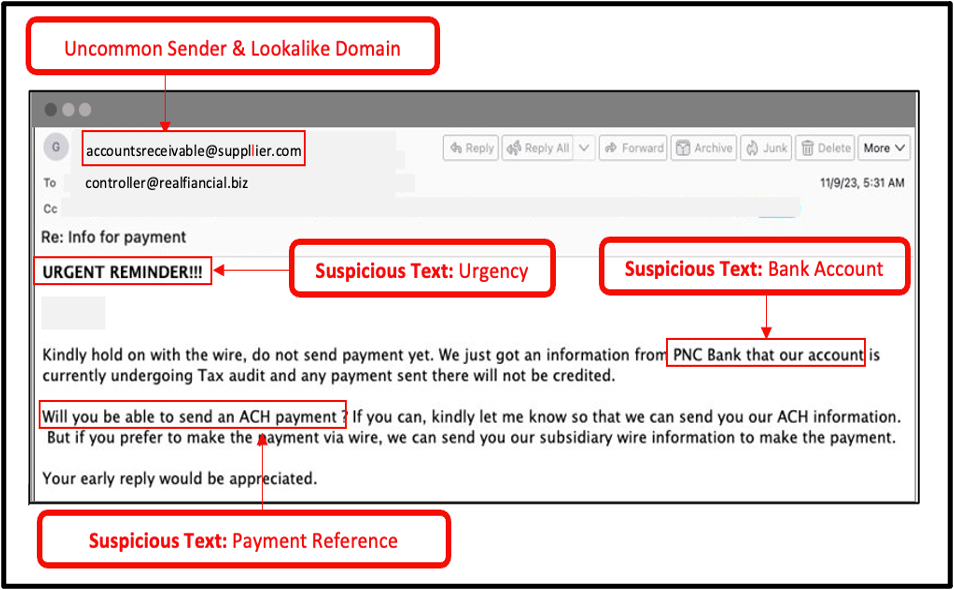
Multiple detection signals identified in a fraudulent supplier email.
To reduce noise detection, Proofpoint combines a multitude of signals. That helps us to ensure that we don’t overly rely on one or two signals that can create a high level of false positives. Instead, we combine the uncommon sender signal with an analysis of the language in the body of the message. This allows us to extract the tone and interpret the intent of an email.
We continuously train our AI and machine learning techniques with millions of email messages seen daily from the worldwide Proofpoint threat intelligence ecosystem. That allows us to provide a higher level of confidence when we detect and block these types of messages.
Based on the email’s content, intent and language, Proofpoint deciphered that the message in our example scenario was a fraudulent financial request. This campaign featured only a few impersonating messages and was targeted at one customer. No other Proofpoint customer had seen this attack before.
Our multilayered threat intelligence combined with behavioral AI and our advanced machine learning detection stack allowed us to prevent this threat from being delivered to the user’s inbox.
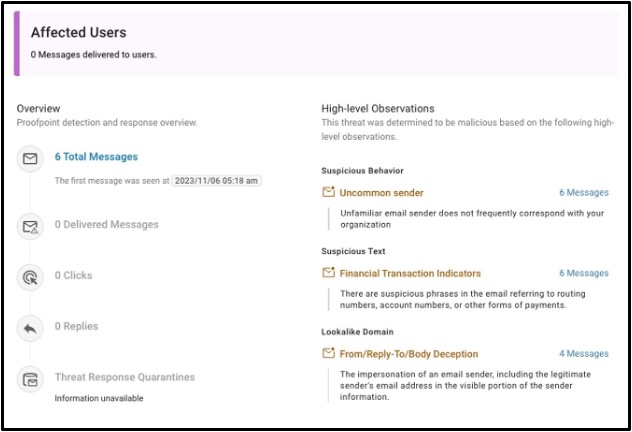
Condemnation summary outlining the signals that Proofpoint detected to block this threat.
Other post-delivery email security tools that claim to offer AI typically cannot prevent the delivery of these types of messages. That leads to gaps in visibility and detection. And it leaves businesses open to increased financial risk and fraud due to longer malicious email dwell time in users’ inboxes.
We constantly train our AI on a wide variety of emails, including clean and malicious emails. That context and diversity of data play a vital role in our ability to create a resilient and highly effective AI. Our pre-delivery, AI-driven detection engines allow us to continue to identify and block supply chain compromise threats proactively—and protect users with human-centric security.
Remediation: What are the lessons learned?
To keep your business safe from threats like supply chain compromise that use social engineering, you should use proactive measures like:
-
Detect threats pre-delivery. According to Proofpoint research, one in seven users will click on an email within one minute. The only way to keep users safe is to block malicious messages before they are delivered. Look for a tool that combines machine learning algorithms and advanced threat intelligence to identify and block threats. Keep in mind that API-only email tools typically claim to detect threats like supply chain compromise, but they only do so after a threat has been delivered to users’ inboxes.
-
Educate your users. Your employees, contractors and partners are your first line of defense. Make sure that they get security awareness training about all types of attacks. Deceptive emails, suspicious tasks and unusual requests are among the topics you may want to cover.
-
Protect your third-party ecosystems. Your suppliers are prime targets for impersonation attacks through email. Make sure you protect them with supplier threat protection that uses advanced AI and the latest threat intelligence to detect and remediate compromised supplier accounts.
Proofpoint delivers people-centric protection
In this blog, we explored the challenging nature of thread-hijacking threats and their various techniques. By identifying and remediating compromised supply chain accounts, Proofpoint provides organizations with people-centric protection for their users and businesses.
To learn more about how Proofpoint can help your business defend against email threats like BEC, download our e-book, The Definitive Email Cybersecurity Strategy Guide.











