This blog post is part of a monthly series, Cybersecurity Stop of the Month, which explores the ever-evolving tactics of today’s cybercriminals. It focuses on the critical first three steps in the attack chain in the context of email threats. The goal of this series is to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
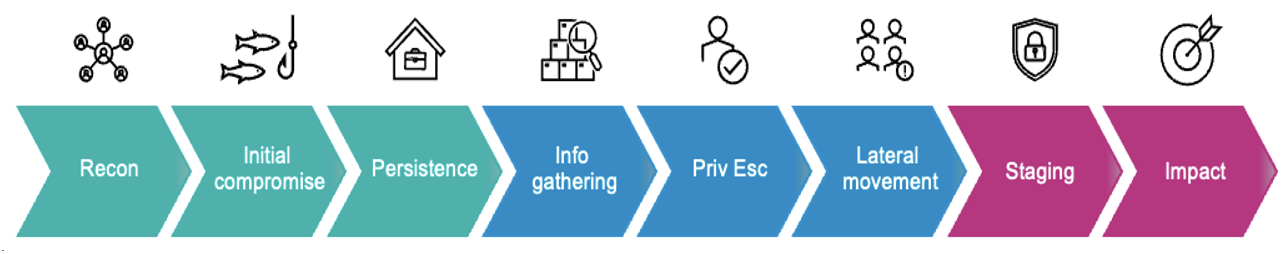
The critical first three steps of the attack chain—reconnaissance, initial compromise and persistence.
So far in this series, we have examined these types of attacks:
- Supplier compromise
- EvilProxy
- SocGholish
- eSignature phishing
- QR code phishing
- Telephone-oriented attack delivery (TOAD)
- Payroll diversion
- MFA manipulation
- Supply chain compromise
- Multilayered malicious QR code attack
In this post, we examine an emerging threat—the use of malicious cloud applications created within compromised cloud tenants following account takeover. We refer to it as MACT, for short.
Background
Cloud account takeover (ATO) attacks are a well-known risk. Research by Proofpoint found that last year more than 96% of businesses were actively targeted by these attacks and about 60% had at least one incident. Financial damages reached an all-time high.
These findings are unsettling. But there is more for businesses to worry about. Cybercriminals and state-sponsored entities are rapidly adopting advanced post-ATO techniques. And they have embraced the use of malicious and abused OAuth apps.
In January 2024, Microsoft revealed that a nation-state attacker had compromised its cloud environments and stolen valuable data. This attack was attributed to TA421 (aka Midnight Blizzard and APT29), which are threat groups that have been attributed to Russia's Foreign Intelligence Service (SVR). Attackers exploited existing OAuth apps and created new ones within hijacked cloud tenants. After the incident, CISA issued a new advisory for businesses that rely on cloud infrastructures.
Proofpoint threat researchers observed attackers pivoting to the use of OAuth apps from compromised—and often verified—cloud tenants. Threat actors take advantage of the trust that’s associated with verified or recognized identities to spread cloud malware threats as well as establish persistent access to sensitive resources.
The scenario
Proofpoint monitors a malicious campaign named MACT Campaign 1445. It combines a known tactic used by cloud ATO attackers with new tactics, techniques and procedures. So far, it has affected dozens of businesses and users. In this campaign, attackers use hijacked user accounts to create malicious internal apps. In tandem, they also conduct reconnaissance, exfiltrate data and launch additional attacks.
Attackers use a unique anomalous URL for the malicious OAuth apps’ reply URL—a local loopback with port 7823. This port is used for TCP traffic. It is also associated with a known Windows Remote Access Trojan (RAT).
Recently, Proofpoint researchers found four accounts at a large company in the hospitality industry compromised by attackers. In a matter of days, attackers used these accounts to create four distinct malicious OAuth apps.
The threat: How did the attack happen?
Here is a closer look at how the attack unfolded.
1. Initial access vectors. Attackers used a reverse proxy toolkit to target cloud user accounts. They sent individualized phishing lures to these users, which enabled them to steal their credentials as well as multifactor authentication (MFA) tokens.

A shared PDF file with an embedded phishing URL that attackers used to steal users' credentials.
2. Unauthorized access (cloud account takeover). Once attackers had stolen users’ credentials, they established unauthorized access to the four targeted accounts. They logged in to several native Microsoft 365 sign-in apps, including “Azure Portal” and “Office Home.”
3. Cloud malware (post-access OAuth app creation). Attackers then used the accounts to create and authorize internal (second-party) apps with selected scopes and permissions. (Examples included Mail.Read, Mail.Send, offline_access and profile.)
Our researchers learned that the MACT Campaign 1445 attackers use specific naming patterns for the apps that they create, like a short random string or the compromised account’s email address.
The attackers used application registration to create “single tenant” or “multitenant” apps.
4. Persistent access. Attackers used internal apps to maintain persistent access to valuable resources like mailboxes and files within a compromised environment.
Note: Until a malicious app is deleted or revoked, it remains active. And it continues to have access to select assets. In other words, attackers have the chance to enjoy extended dwell times with this strategy.
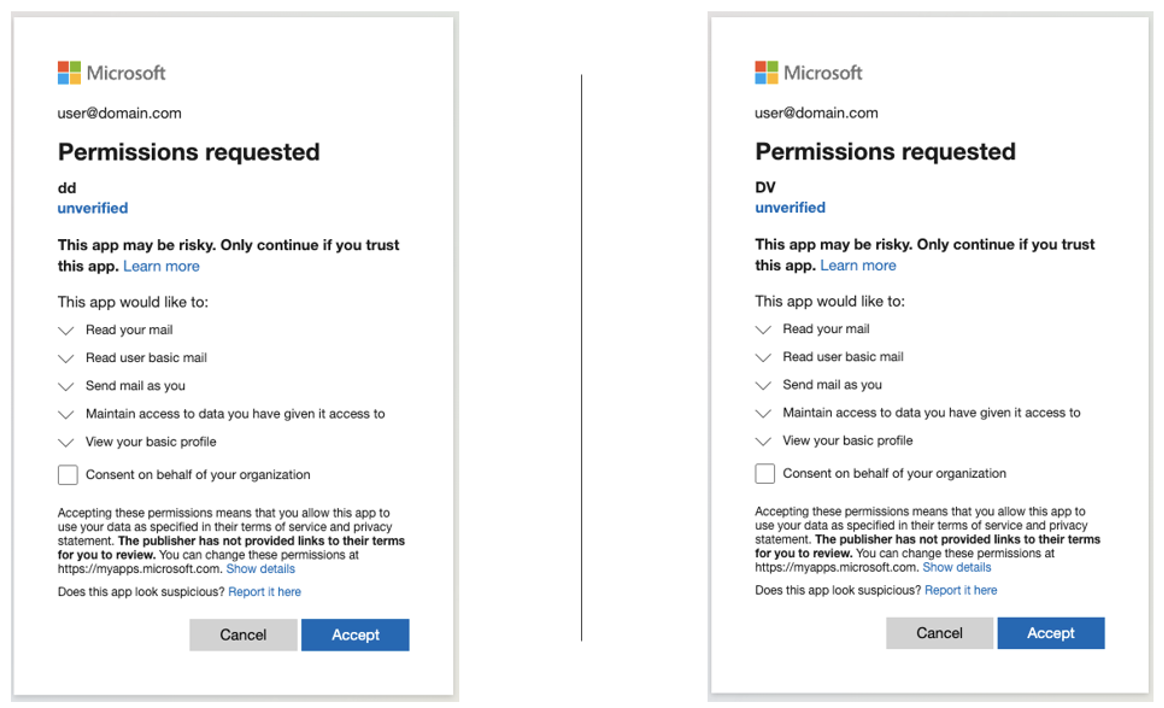
Malicious apps that the attackers created by using hijacked user accounts.
Attackers combined the creation of malicious OAuth apps within the compromised environment with MFA manipulation execution. They used the native “My Sign-ins” application to register an authenticator app with notification and code.
5. Obfuscation. Next, attackers created new mailbox rules to hide outbound malicious activity and cover their tracks.
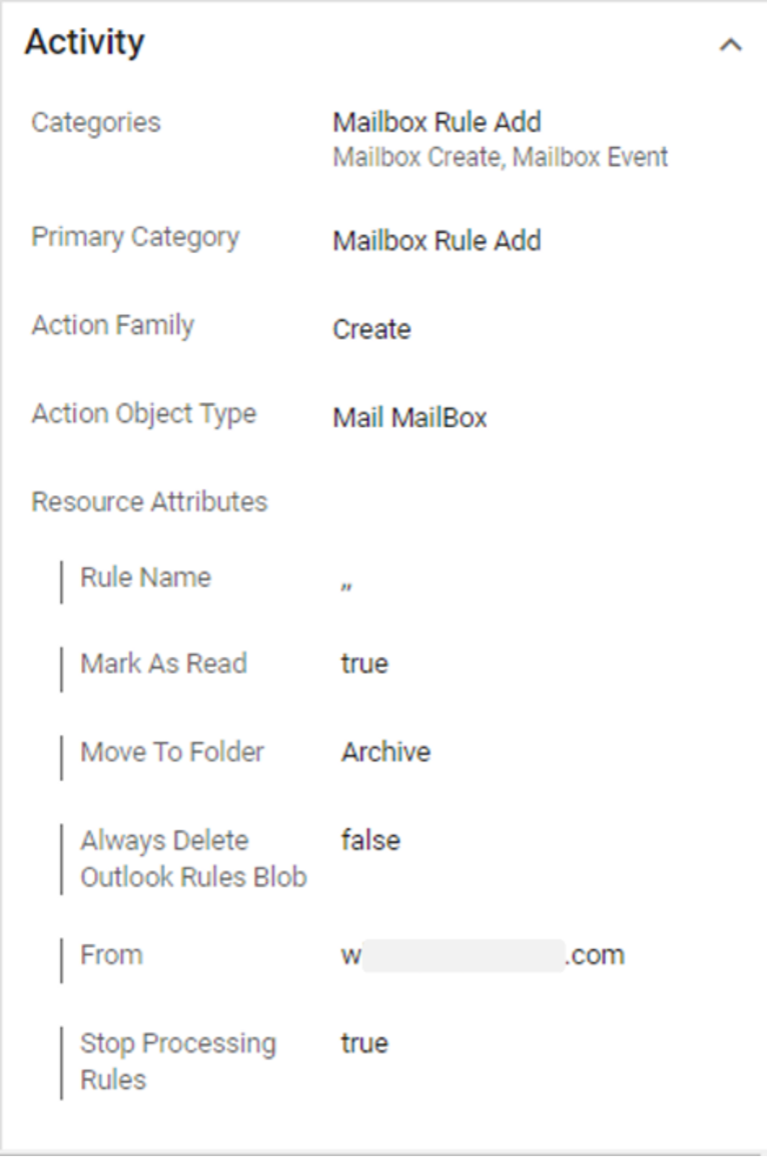
Malicious mailbox rule that attackers created post-compromise, which is designed to archive incoming emails from a targeted external account.
6. Proliferation of threats. Attackers can use the permissions of a malicious app to spread internal and external email-borne threats. These threats include phishing, malware and spam.
Attackers will use malicious apps to move laterally within a compromised environment. If the malicious apps are configured as “multitenant,” they can be shared across environments as part of a supply chain attack. To use MACT threats in this way, attackers rely on the credibility and reputation of the compromised cloud tenants.
Detection: How Proofpoint prevented this attack
It is not easy to detect OAuth-based cloud malware within cloud tenants. You need a security tool that features:
- Accurate threat intelligence
- User and entity behavior analytics (UEBA) capabilities
- Retrospective insights
In this case, several indicators helped Proofpoint to find the MACT incident before the attackers could capitalize on the foothold that they had established.
Proofpoint TAP Account Takeover (ATO) automatically detected the authorization of four malicious apps based on dedicated “spotters.” These advanced detection logics analyze and condemn suspicious OAuth apps.
Proofpoint found the incident from the unauthorized access side as well. It flagged the suspicious login events as “Successful Suspicious Login” actions. And it enriched these events with contextual threat intel and forensic evidence. It also identified a series of malicious post-access activities as high-severity threats. These included creating mailbox rules and manipulating MFA.
These actions were not only timely but highly actionable. Plus, they were compelling enough to shorten investigation times to a minimum. The ability to act quickly is crucial for effective incident response. In the case of our customer, their security team was able to move fast to stop an ongoing attack and prevent damage.
Remediation: What are the lessons learned?
Your business should take proactive measures to stop account takeover and cloud malware threats. Here are a few you should consider.
- Implement continuous monitoring. By continuously monitoring your line-of-business apps and applying auto-remediation, you can prevent attackers from establishing persistent access to valuable resources. This can also stop them from launching more attacks.
- Invest in account takeover tools. Include robust tools in your security stack that can detect and block complex attacks like:
- Account takeover detection
- Anomaly discovery
- Behavior analytics
- It’s also a good idea to use comprehensive ATO detection tools that provide actionable alerts, contextual threat intelligence and attack sequence identification that is in line with MITRE ATT&CK® standards.
- Empower your users. Your users are a vital part of your defense. Conduct regular trainings to educate them on how to:
- Recognize malicious apps and tenants that seem credible
- Treat unexpected consent requests as suspicious
- Promptly report unusual application authorizations
- Streamline your response processes. It’s important to define clear processes for how your teams will investigate and mitigate specific threats and scenarios. For example, you might create a procedure for responding to second-party malicious app detection. To make sure your processes are effective, test them regularly with simulated exercises.
These remediation strategies can go a long way toward helping your business enhance its resilience against cloud malware and other advanced threats.
Proofpoint delivers human-centric security
This MACT incident is a stark reminder of how the threat landscape is always changing. In this case, attackers took advantage of a company’s settings for creating OAuth applications to create malicious assets after they got into their environment.
Proofpoint delivers human-centric security that can help you strengthen your people-centric defenses. We provide comprehensive visibility into user behavior and data activity. That insight can help detect and block unauthorized access to your users and resources as well as prevent data exfiltration attempts in real time.
To learn more about how Proofpoint can help you defend against cloud threats and more, download our e-book, The Definitive Email Cybersecurity Strategy Guide.











