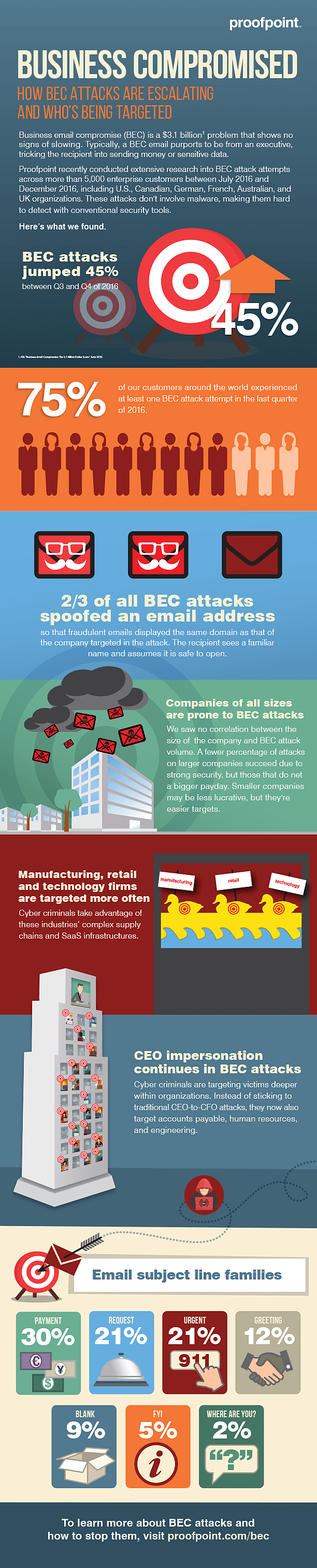
Business email compromise (BEC), or impostor email is one of the biggest cyber threats facing organizations today. And to stay at the forefront of today’s threat intelligence landscape, Proofpoint recently conducted extensive research into attack attempts across more than 5,000 enterprise customers between July 2016 and December 2016, including U.S., Canadian, German, French, Australian, and UK organizations. The research findings below show a clear acceleration in attack sophistication and volume.
BEC attacks, which are often malware-free, evade technologies that detect and block malicious payloads - including URLs and attachments - and trick people into sending money and other critical information to the imposter. BEC threats look no different than any legitimate business email communication and attackers are successfully targeting the people within organizations by constantly shifting their tactics and approaches.
Here’s what our global threat intelligence team uncovered (infographic below):
Fraudsters are Targeting Organizations of All Sizes
With the rise of impostor email attacks, most organizations will find themselves in the crosshairs of a BEC attack. BEC attacks increased by 45% during the last three months of 2016 compared to the prior three months, and 75% of Proofpoint customers experienced at least one attempted attack during that time. These targeted threats are directed at companies of all sizes and in all geographic locations. And while no industry is immune, manufacturing, retail, and technology organizations are generally targeted more frequently as cybercriminals look to take advantage of complex supply chains and SaaS infrastructures that are commonly leveraged in these industries.
Exploiting the Right People
Through social engineering, fraudsters can identify and target specific individuals based on the information or funds they’re looking to steal. Initially, BEC attackers simply spoofed the CEO-to-CFO relationship, but there has been a clear shift to target victims deeper within organizations. Criminals are impersonating CEOs and other executives to trick various employee groups such as accounts payable for wire transfer fraud, human resources for confidential information, and engineering for intellectual property. And with 70% of BEC message subject line families including terms such as “urgent,” “payment,” and “request,” people are being tricked into these scams through a false sense of urgency.
Impostor Email Techniques: Domain Spoofing Soars
Domain-spoofing makes up nearly two-thirds of all BEC attacks and is the most common form of impostor email. These threats make it look like the message is coming from a trusted email domain, when in fact it’s not. Dialogues may then be continued via a reply-to redirect. Display name spoofing is also prevalent –about 37% of these attacks – and changes the visual queue of the “header from” line within the message. This tricks people into thinking the email is from a legitimate sender. Lookalike domain spoofing (changing out numbers and letters within the domain name to mimic a legitimate domain) and business partner spoofing (spoofing trusted partners’ domains) are also common forms of BEC attacks.
Proofpoint has a Winning Solution
Proofpoint provides a comprehensive, multi-layered approach to block every type of BEC threat. Leveraging DMARC authentication, our technology helps organizations reject all malicious emails that look to spoof their trusted domains. Anti-spoofing policies and dynamic classification capabilities stop attacks such as display name spoofing and lookalike spoofing at the email gateway. Security teams can also detect and block BEC-related content such as W2 forms and employee tax information from leaving the organization. By cutting off every BEC attack channel, organizations not only safeguard employees and their brand, but also extend protection to partners and customers.
Proofpoint BEC Research Infographic
To learn more about how to combat business email compromise, visit our site at www.proofpoint.com/bec.