

Manage Human Risk
Proofpoint human risk explorer
Empowering organisations with actionable human risk insights
Know Who’s At-Risk, What Sensitive Data is Exposed, and How to Reduce Human Risk Effectively
Managing human risk is complex due to ineffective security solutions, siloed data and limited visibility. Organisations need a holistic approach that consolidates risk signals, provides easy-to-understand insights, and delivers recommended mitigation actions to proactively reduce threats and optimise security efforts.
Unlock comprehensive insights from the Proofpoint Human-centric Platform
Easily track human risk across individuals, departments, and the entire organisation
Continuously monitor and track risk trends with a centralised view that enables quick issue detection with minimal manual investigation
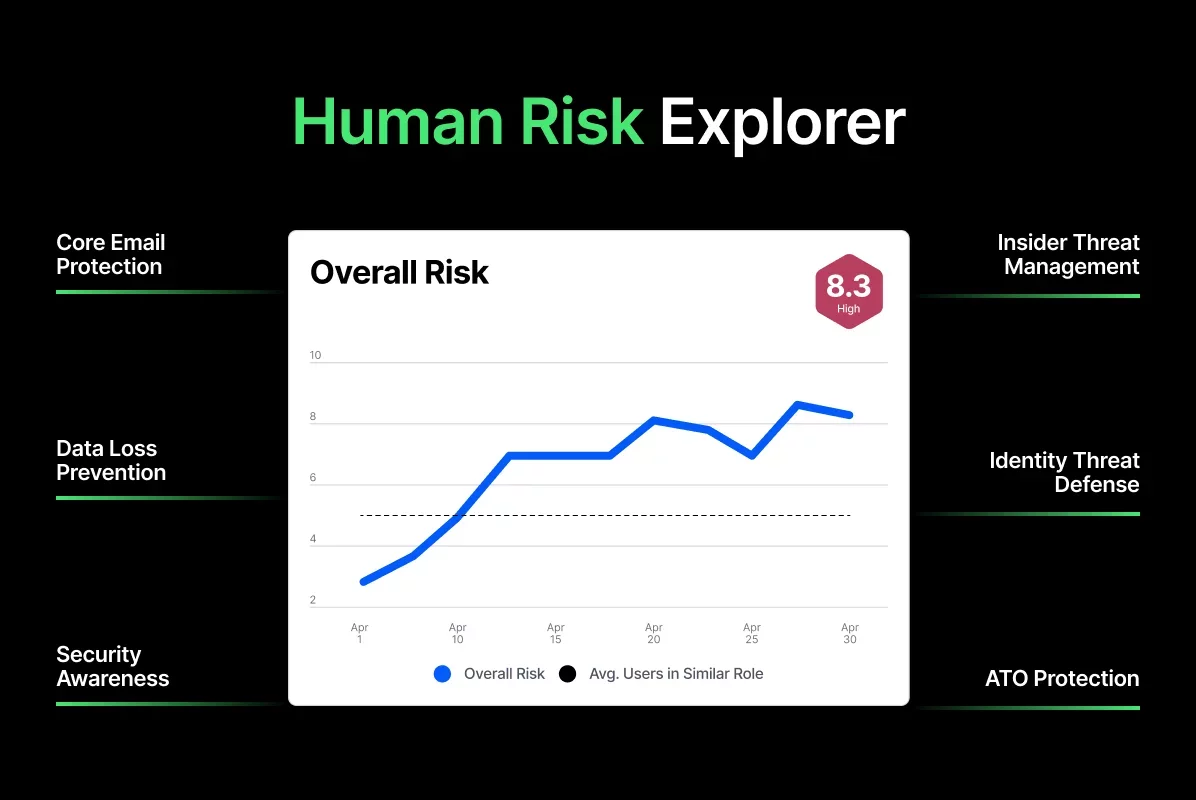
Understand exactly why risk levels are changing
Quickly investigate risk at any level—from organisation-wide trends to individual employee behaviours—to understand what’s driving human risk
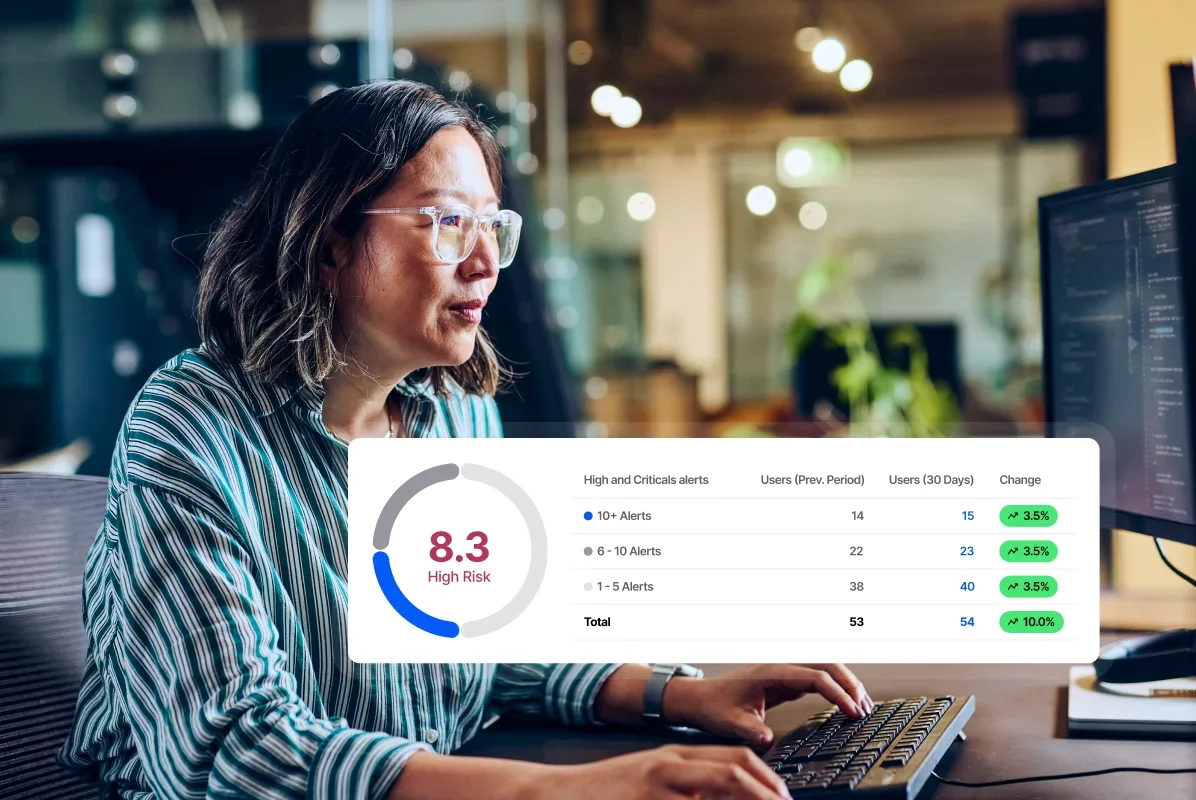
Enable faster mitigations with Proofpoint guidance
Address human risk with integrated and actionable mitigation recommendations that provide clear guidance on what actions to take, which security controls to apply, and why the recommendation was made

Key Features of Proofpoint Human Risk Explorer
Organisational, Departmental, and Individual User Risk Score Trending
Gain a quick, yet comprehensive snapshot of the organisation’s human risk posture that correlates risk signals across Proofpoint core email protection, insider threat management, identity threat defence, omni-channel enterprise data protection, and user education

Detailed individual user insights across threat, data, and awareness risks
Drill down into individual risk insights to clearly understand who is at-risk, what sensitive data is exposed due to risky behaviours, and whether your users understand organisational security policies and best practices

Integrated mitigation recommendations
Recommended Mitigation Controls provide the reason the mitigation is recommendation, a detailed task list on how to implement the mitigation, and which groups would benefit from the mitigation ensuring informed decision making and targeted risk reduction

Enforce Security Actions with Proofpoint Integrations
Seamlessly leverage Human Risk Scores within Proofpoint solutions like ZenGuide, ATO Protection, Insider Threat Management, and DLP to automate security controls when users exhibit risky behaviours—enforcing protections proactively and reducing manual effort

The latest developments in mitigating human risk

2024 State of the Phish – Today’s Cyber Threats and Phishing Protection
Read More
Proofpoint ZenGuide











