Overview
Every year, Proofpoint observes a seasonal uptick in tax-related malware and phishing campaigns leading up to annual tax filing deadlines. In 2017, these campaigns focused on phishing and increasingly sophisticated social engineering, as well as banking Trojans and ransomware. In 2018, we observed sophisticated email campaigns that featured urgent tax-themed lures and convincing spoofs of IRS branding. Epitomizing one of the major trends of 2018, these campaigns distributed a variety of RATs including Orcus Rat, Remcos RAT, and NetWire. With tax season again upon us, we have seen a similar bump in tax-related campaigns both in the US and internationally. Malware payloads generally reflected the mix in the broader landscape, with a focus on RATs, downloaders, and banking Trojans, while common phishing emails remained pervasive.
Malware Campaigns
NetWire is a multiplatform RAT typically delivered via spammed email attachments that contain Microsoft Office files with embedded executables, including .jar files. Many NetWire campaigns primarily target verticals like financial services, businesses, and educational institutions. Recent NetWire campaigns in September and October of 2018, and later in early February 2019, targeted users in Australia, Canada, and the United States and employed tax-related lures with social engineering invoking a sense of urgency or creating an air of legitimacy with subject lines that included:
- Notice of Outstanding Income Tax Demand…
- IRS Update for 1099 Employees
- 2018 EF Tax Incentive Billing
- Your IRAS 2018 Tax Report
Campaign: “Australian Tax Office” lure dropping Netwire
On October 2, 2018, Proofpoint observed a campaign distributing thousands of messages with attached Microsoft Word documents. The documents contained macros that, when executed, installed NetWire malware (Figure 1). These documents also exploited CVE-2017-11882 (Equation Editor) on vulnerable devices.
Actors purported to be from the “Australian Taxation Office,” the legitimate Australian government tax agency. However, the emails were actually sent from an AOL account with a spoofed display name.
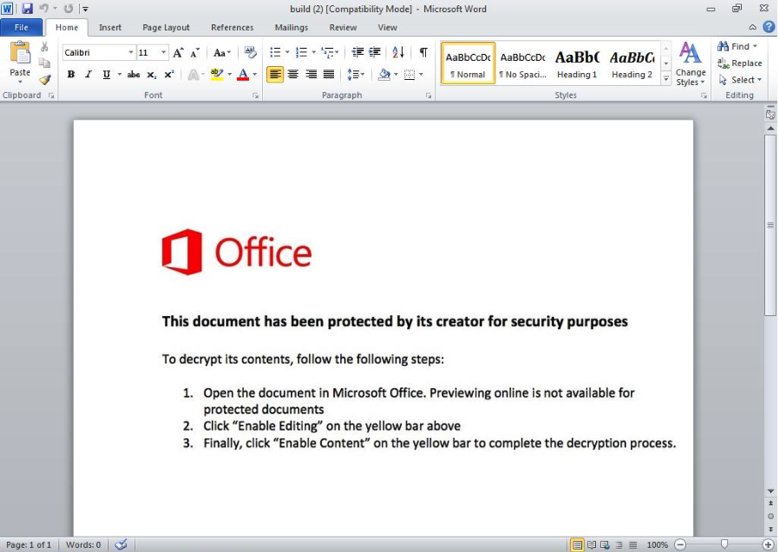
Figure 1: Lure document attached to fake Australian Tax Office emails with embedded macros that, when enabled, install NetWire RAT
Campaign: Canada Post lure dropping NetWire
Threat actors spoofing Canada Post and New Zealand Inland Revenue Department email addresses sent a campaign involving tens of thousands of messages using tax-related lures between September 26 and 28, 2018. The emails contained attached Microsoft Word documents with macros that, if enabled, downloaded NetWire.
Additional NetWire campaigns
We also observed several other campaigns that utilized tax-themed lures and convincing branding and graphical elements to deceive email recipients (Figure 2).

Figure 2: Malicious document attachment with fake error dialog that instructs the user to “Enable Editing” to view the document, which will instead download and install The NetWire RAT
Figure 3 shows another NetWire lure that purports to be from the Indian government demanding payment for outstanding taxes. In this case, victims follow a link with a URL shortener to download NetWire.
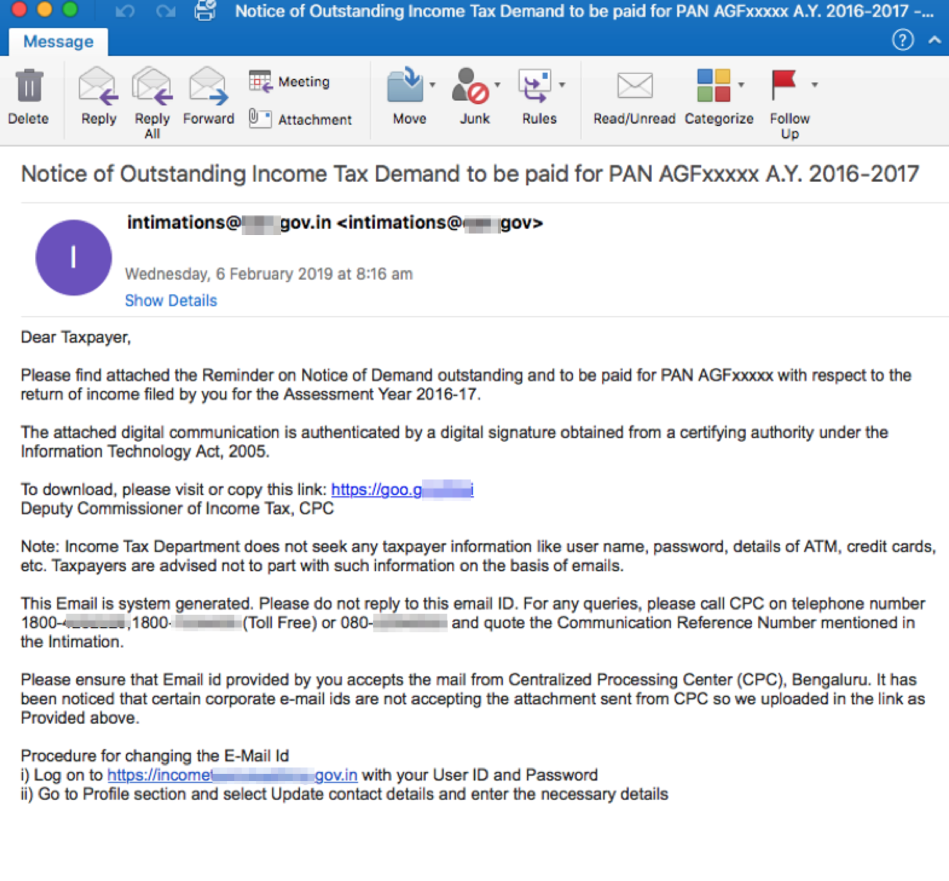
Figure 3: A campaign in early February 2019 used socially engineered tax-themed lures and spoofed email addresses to convince recipients to click on malicious URLs, which download Microsoft Office documents that contain the NetWire RAT
Fake Professor campaign
Figures 4 and 5 show an example email and faked document, respectively, used to install an instance of Remcos RAT on victim machines. Between January 10 and 11, 2019, Proofpoint researchers observed emails purporting to be from a fictitious professor sent to accounting and business services organizations. The documents included a retouched fake W2 and other supporting fake documents designed to convince the recipient that the sender was an actual individual submitting tax return information for preparation. When opened and the content enabled, macros in the attached Microsoft Word documents download and install Remcos RAT.
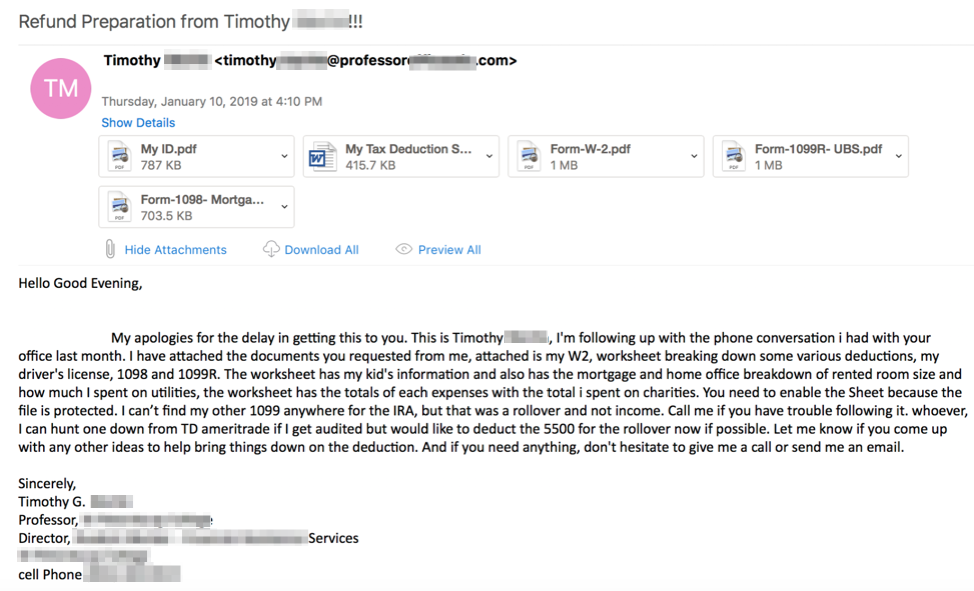
Figure 4: Email with specific references of legitimate tax forms like the “W2”, “1098”, and “1099R”. This email used a personalized subject line, spoofed sender address, and fake tax-related documents

Figure 5: Spoofed tax form used to convince recipients that the actor is a legitimate tax preparer
Additional malware campaigns
Tax-themed email lures are not limited to the United States. Figure 6, for example, shows an email targeting Singapore residents with messages purporting to be from the local taxation authority. When recipients open the attached Microsoft Word document and enable content, malicious macros download and install the Ave Maria RAT.
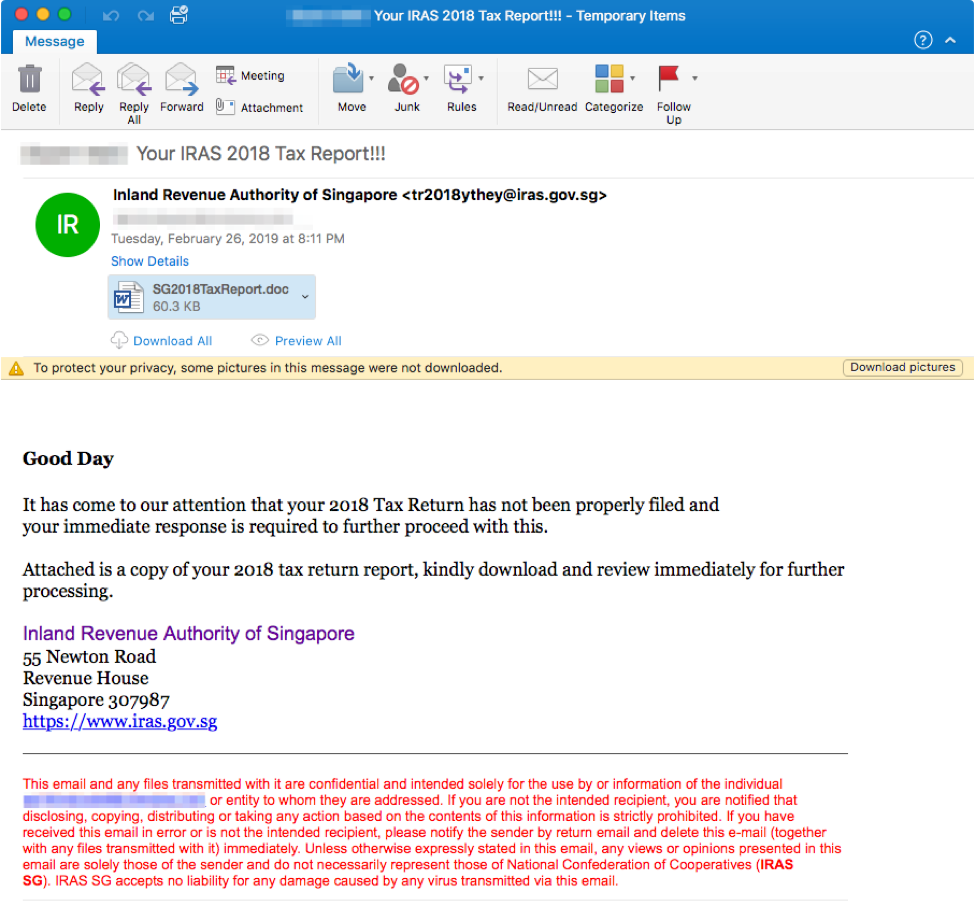
Figure 6: Email with spoofed “Inland Revenue Authority of Singapore” sender address and tax-themed subject line
Tax-themed lures are also used to distribute banking Trojans such as The Trick. In particular, in the example from Figure 7 the threat actors target US victims with IRS form names despite foreign top-level domains. Other campaigns observed by Proofpoint researchers leverage stolen branding and seemingly legitimate privacy language to convince victims to open an attached spreadsheet with malicious macros that install The Trick when they are enabled.
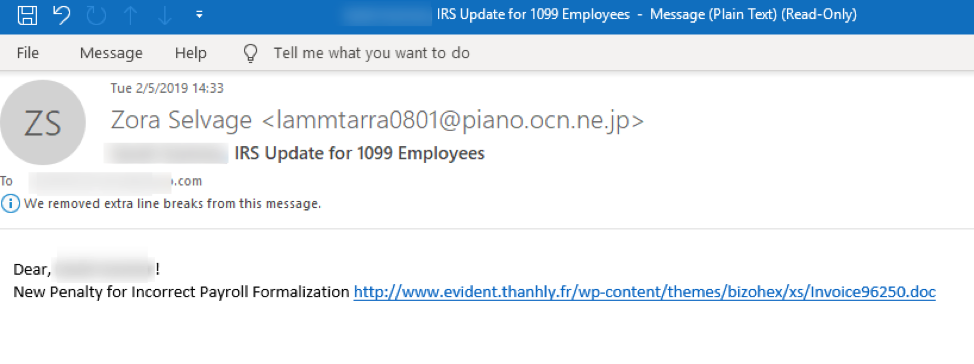
Figure 7: An email from a campaign in early February 2019 that features a tax-themed subject line, and that contains URLs that download malicious Microsoft Word documents with macros, that once enabled, install “The Trick” banking Trojan
Tax-Related Phishing Campaigns
This year, we also observed a significant increase in tax-related phishing campaigns, in which actors sent thousands of emails with HTML attachments or URLs that linked victims to spoofed login pages and online forms with stolen branding from the IRS and other local tax authorities. To ensure that the phishing attempts remained undetected, actors often redirected victims to the official tax authority websites after stealing their credentials. As a result, many victims were likely unaware that they had just disclosed their tax information to phishers.
These campaigns impersonated legitimate tax authorities from around the world. Actors created convincing imitations of the websites of several official tax authorities: the US Internal Revenue Service, Canada Revenue Agency, and the New Zealand Inland Revenue Department, among others. Examples appear in Figures 8-15.
Domestic Phishing
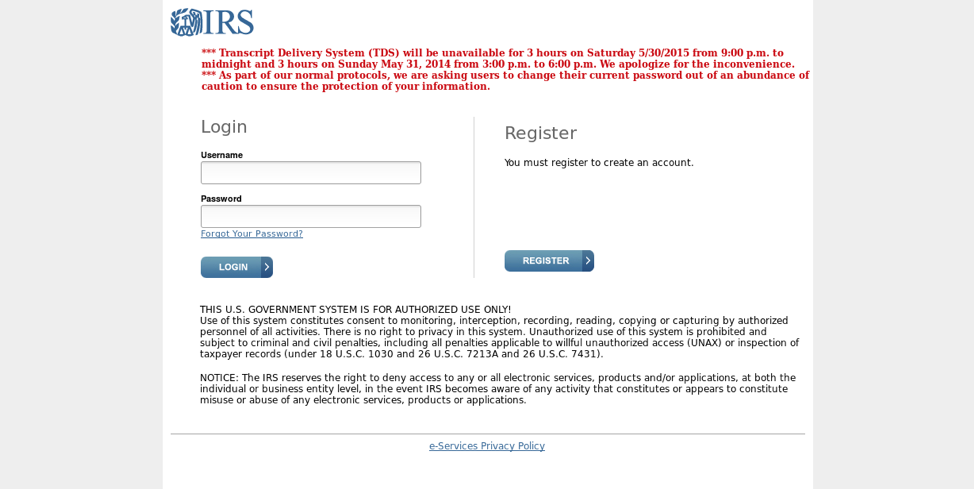
Figure 8: A fake login page with stolen IRS branding that is used for credential phishing
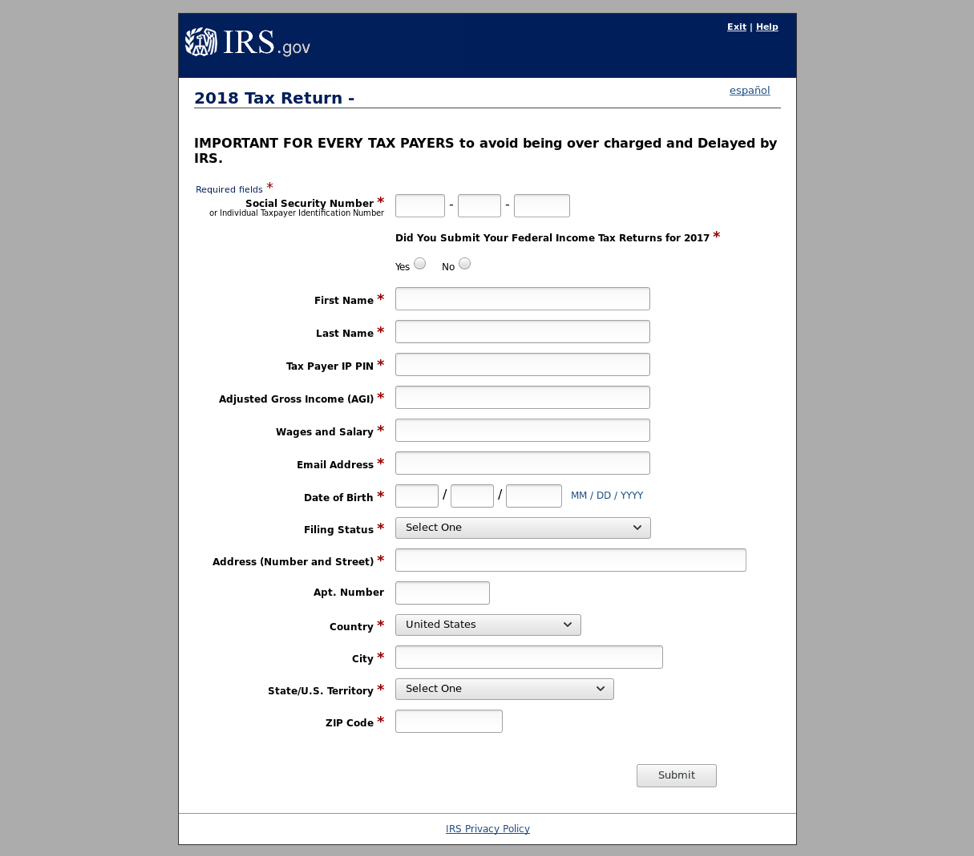
Figure 9: IRS-themed credential phishing page with stolen branding, featuring a socially engineered message at the top of the form to incite a sense of urgency
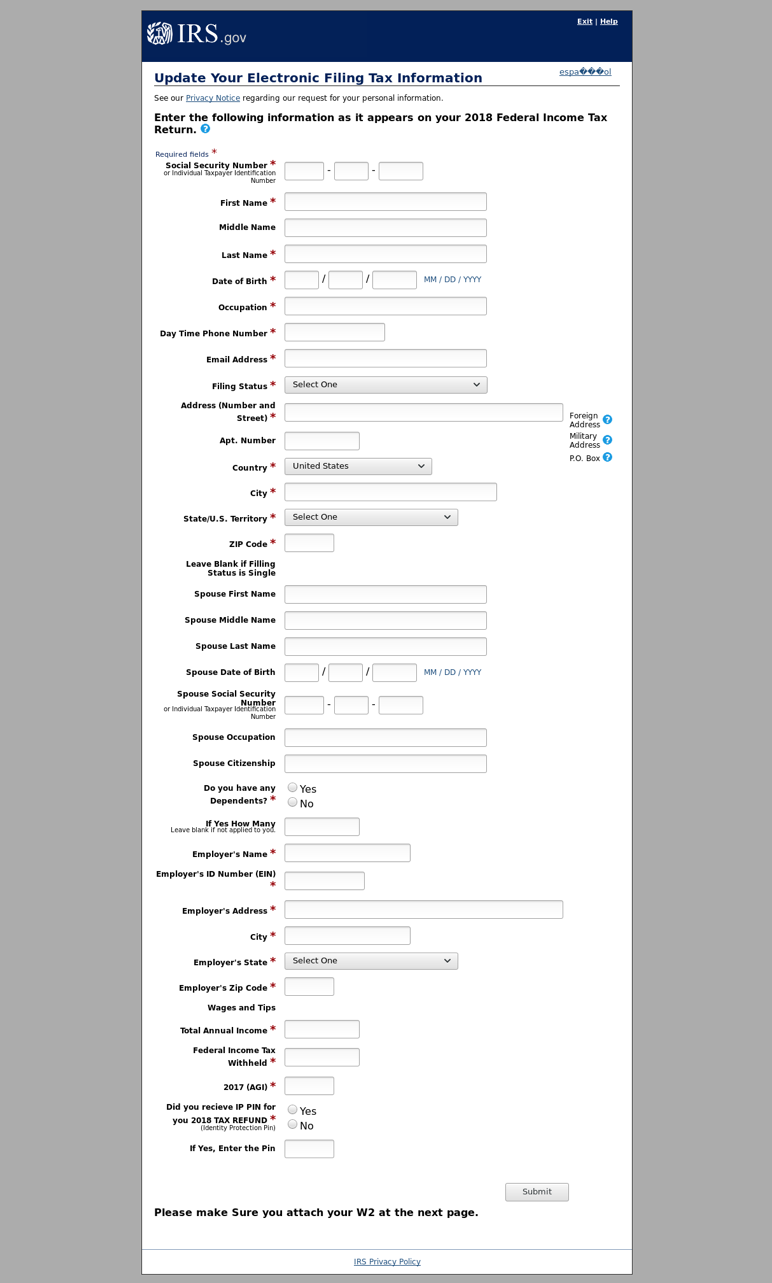
Figure 10: Another IRS-themed phishing page using stolen branding designed to steal a range of personal information
International Tax Phishing
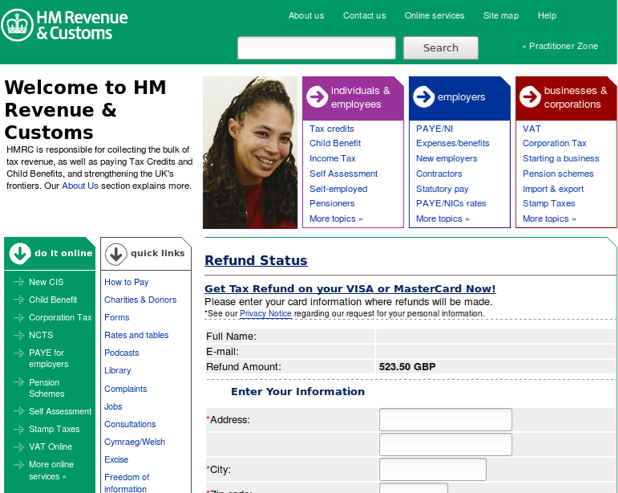
Figure 11: Fake HMRC web form used for credential phishing (UK)
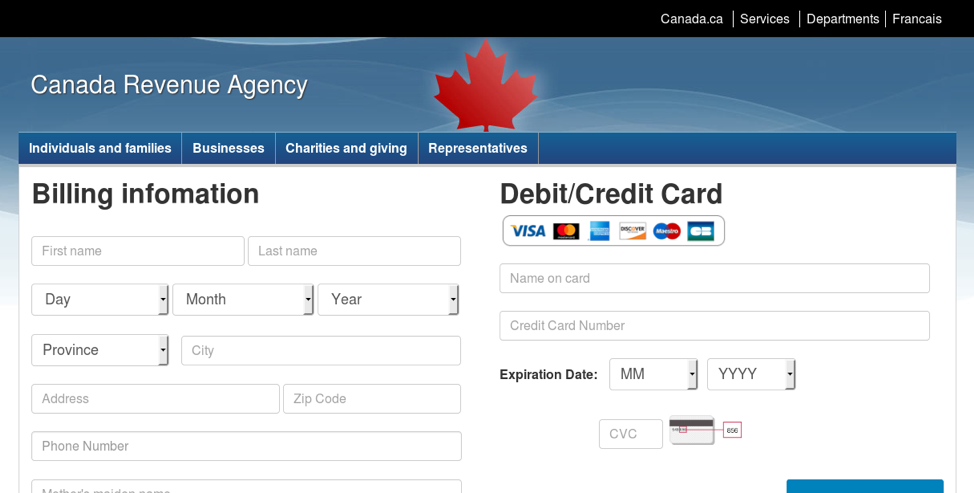
Figure 12: Fake Canada Revenue Agency page used for credential phishing (Canada)
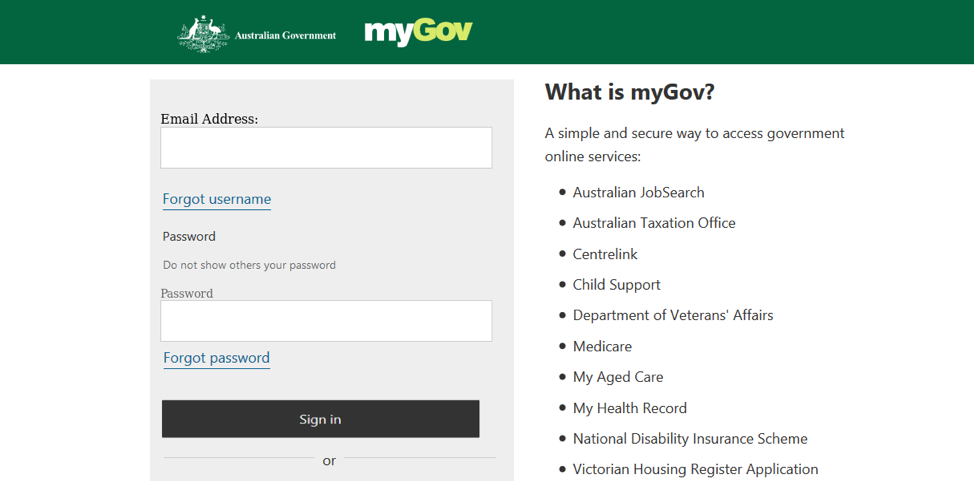
Figure 13: Fake “myGOV” login portal used for credential phishing to steal tax information. This portal login is indistinguishable from its genuine counterpart (Australia)
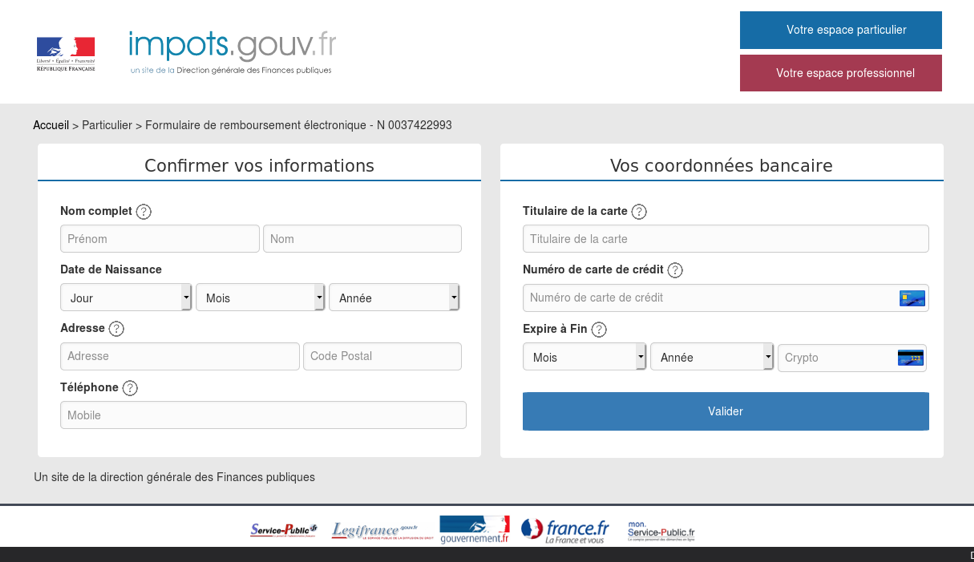
Figure 14: Fake “Ministry of Public Action and Accounts” login page used for credential phishing (France)
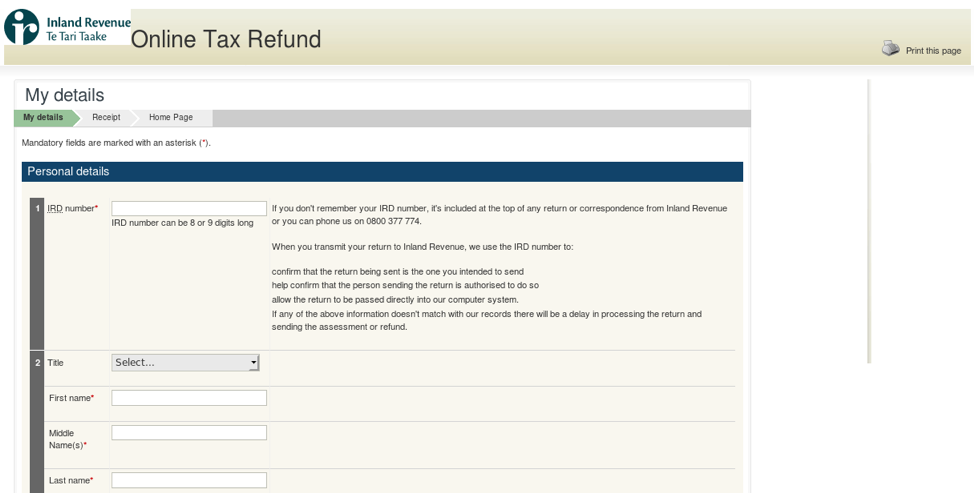
Figure 15: Fake Inland Revenue tax refund phishing page (New Zealand)
Conclusion
As in years past, Proofpoint researchers observed the expected seasonal increase in tax-themed campaigns. 2019 saw a continuation of a trend towards high numbers of RATs first observed in 2018. Regardless of the payload, however, actors utilized social engineering techniques in subject lines, spoofed emails addresses, and “decoy” links that led to the websites of legitimate government tax offices, many of which were outside of the U.S. In fact, the campaigns we tracked spanned a range of geographies, demonstrating the effectiveness of tax themes as nearly universal lures. As tax day approaches, filers should stay vigilant, and be wary of increasingly convincing lures, stolen branding, and more.
References
[1]https://www.iras.gov.sg/irashome/default.aspx
[2] https://en.wikipedia.org/wiki/Australian_Taxation_Office
[3] https://en.wikipedia.org/wiki/Canada_Post
[4] https://en.wikipedia.org/wiki/Inland_Revenue_Department_(New_Zealand)
[5] https://en.wikipedia.org/wiki/Ministry_of_Public_Action_and_Accounts
Indicators of Compromise (IOCs)
|
campaign |
IOC |
IOC Type |
Description |
|
Australian Tax Office|2 October 2018 |
6d156bd6869abb03a23e1374167729fb4991b2e60ef837a4a4e77d087c8f0ae0
|
SHA256 |
build(2).doc for October 2-3, 2018 NetWire cmpaign |
|
Netwire|Canada Post| 26-28 September 2018 |
21838cf11faa5a9a026892e919e44a28ab4bef7eaf0d3484459599e0dbfcd550
|
SHA256 |
Build.doc for September 26- 30 Netwire Campaign |
|
NetWire|Canada Post|26-28 September 2018 |
389c0f5655625ea8c9d2a4f309196f45c635dc1c619f92346306ab180f185031 |
SHA256 |
Build.doc for September 26-28 NetWirecampaign |
|
Netwire|Canada Post|26-28 September 2018 |
3689ddd122369a5bb02d5b7a79103499cf0dcf90dd93745d71934005c36c42c9
|
SHA256 |
build (1).doc for “NetWire” campaign |
|
Ave Maria | "Your IRAS 2018 Tax Report!!!" | 26-27 February 2019 |
92db1c61b920199689757add0e5eb0f59f311e96ff2c5b46469beb6433503bea |
SHA256 |
Sg2018taxreport.doc.docm for the February 26-27 “Ave Maria” Campaign
|
|
March Tax Phishing Campaign |
hxxp[:]//dual-it.com/wp-content/themes/twentynineteen/js/Espace-Client/ |
URL |
Credential Phishing login page for March tax phishing campaign |











