プルーフポイント、攻撃チェーンを断ち切る業界初のイノベーションを発表

新しい統合ソリューションは、「より多くの攻撃を事前に検知」、「漏えいしたアイデンティティによる影響の定量化」、「データ損失に対応する防護効率の向上」により、脅威、アイデンティティ、データにまたがる組織の最も重要な場面で直面する重大なリスクを解決
2023年9月6日(米国カリフォルニア州サニーベール/ニューヨーク州ニューヨーク ) -- サイバーセキュリティとコンプライアンス分野のリーディング カンパニーであるプルーフポイント(本社:米国カリフォルニア州) は、年次カンファレンス「Proofpoint Protect 2023」で、組織の経済的損失の主な原因であるビジネスメール詐欺(BEC)からランサムウェア攻撃やデータ漏えいまで、組織が現在直面している最大のリスクに対処する業界初のイノベーションを発表しました。今回発表された統合ソリューションは、「Proofpoint Aegis(脅威防護プラットフォーム)」「Identity Threat Defense(アイデンティティ脅威検知プラットフォーム)」「Proofpoint Sigma(情報防護プラットフォーム)」の各プラットフォームにまたがり、攻撃チェーンの最も重要な段階で脅威を阻止します。プルーフポイントのAI(人工知能)とML(機械学習)を活用した新たなイノベーションは、業界で最も包括的なデータセットの1つである数兆件の脅威活動を検知することで、これまでに無い可視性、柔軟性、奥深さをセキュリティ担当者に提供し、組織の攻撃対象領域全体で高度な敵対勢力を検知し、防護します。
AI(人工知能)とML(機械学習)は、正確な検知率、運用効率、自動化された防護を実現するために、強固な検知モデルと忠実度の高いデータパイプラインを必要とします。プルーフポイントのお客様は、メール、クラウド、モバイルコンピューティングにまたがる、最大かつ最も多様なグローバルサイバーセキュリティデータパイプラインからメリットを得ています。プルーフポイントは毎年、2兆8,000億通以上のスキャンされたメールメッセージ、17兆のスキャンされたURL、1兆3,000億のスキャンされたSMSおよびMMS、4,600万人のDLPエンドユーザーをソースとする比類ない量のデータを分析しています。
初期侵害の防止
メールは、侵害を成功に導く攻撃ベクトルの第一位です。Proofpoint Aegis(脅威防護プラットフォーム)は、ビジネスメール詐欺(BEC)、ランサムウェア攻撃、武器化されたURL、クレデンシャルフィッシングのための多要素認証(MFA)回避など、現在の高度な攻撃を解除する唯一のAI/ML (人工知能と機械学習)を搭載したクラウドベースの脅威防護プラットフォームです。「Proofpoint Aegis: 脅威防護プラットフォーム」の新しい機能強化は以下の通りです:
- 業界初、LLM ベースのメール配信前の脅威検知:
プルーフポイントは、Proofpoint CLEAR ソリューション にBERT大規模言語モデル(LLM)を実装することで、ソーシャルエンジニアリング攻撃による被害を未然に防ぐことができます。これは、業界初の受信トレイにメールを配信する前に検知・防止するソリューションです。
世界中の23万を超える組織におけるプルーフポイントのテレメトリーによると、メールを受信トレイに配信する前の保護が非常に重要なのは、配信後の検知では手遅れになることが多いためです。悪意のあるURLのクリックは7件に1件ほどがメール受信後1分以内に発生しており、BECへの返信の3分の1以上は5分以内に発生しています。ユーザーが攻撃の餌食になる可能性があるこれらの狭い時間枠は、悪意のある攻撃がユーザーの受信トレイに到達する前にブロックすることの重要性を強調しています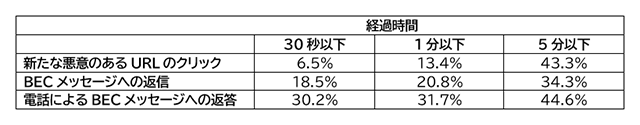
このLLMベースの検知は、従来から作成されているものと生成AIを使用して作成されたものの両方において、生成AIが作成した悪意のあるメッセージの検知に高い成果を上げていることが実証されています。プルーフポイントは、ChatGPTやWormGPT、その他の生成AIが作成した悪意のあるコンテンツを使用して、プルーフポイントのモデルをトレーニングしています。
- ブロックされた脅威に対する可視性の強化:
昨年、企業は BEC により 27 億ドル以上の損害を被りました※1、これはランサムウェア攻撃による損害の約 80 倍に相当します。第3四半期からは、標的型攻撃対策製品であるProofpoint TAP(Targeted Attack Protection)ダッシュボードに新しいサマリが追加され、新しいLLMベースの検知機能によって検知された脅威を含め、Proofpointが実行したBEC検知に関する説明が強化されます。この新しいサマリには、脅威がBEC攻撃であると判断された理由と、それに対応する対応スケジュールが記載されるため、セキュリティ担当者が脅威分析や経営陣への報告に費やす時間が短縮されます。
Attack Path Risk:攻撃経路のリスクを制御し、アイデンティティ脅威から防護
サイバー攻撃の世界的な増加は、攻撃者がその戦術と焦点をアイデンティティベースの攻撃に移すことによって可能となり、昨年は84%の組織がアイデンティティ関連における侵害に遭いました※2。攻撃者が最初にホストに侵入したとき、それが最終的なターゲットになることはほとんどありませんが、その代わりに、攻撃者は特権をエスカレートさせ、特権クレデンシャルを悪用するために環境全体をラテラルムーブメント(横方向に移動)します。
Proofpoint Aegis(脅威防護プラットフォーム)とIdentity Threat Defense(アイデンティティ脅威検知プラットフォーム)の間で、攻撃チェーン全体にわたる市場をリードするデータを統合することにより、セキュリティ担当者は、プルーフポイントの新機能であるAttack Path Risk を使用して、特権IDの乱用やラテラルムーブメントのために従業員のIDが侵害された場合のランサムウェア攻撃やデータ漏えいの攻撃経路の数を理解することができます。この機能は、プルーフポイントのTAPダッシュボード内で第4四半期に利用できるようになり、組織がProofpoint Aegis導入の際にIdentity Threat Defenseを追加した場合は、アナリストが迅速に修復と適応制御の優先順位を決定できるようになります。
Misdirected Email:誤送信メールを防ぎ、情報漏えいを防護
Proofpoint Sigma(情報防護プラットフォーム)は、コンテンツの分類、脅威のテレメトリー、チャネルをまたいだユーザーの振る舞いを統合し、クラウドネイティブなインターフェースでデータ損失と内部脅威を阻止する唯一の情報保護プラットフォームです。プルーフポイントは、世界最大の内部脅威管理(ITM)のプロバイダーであり、世界第2位のデータ損失防止対策(DLP)のベンダーで、売上高でも世界第2位となっています※3。Proofpoint Sigmaは、全世界で5,000以上の顧客と4,600万人以上のユーザーに導入され、毎月450億件の活動を分析し、Fortune 100企業の約半数から信頼を得ています。
ユーザーの行動異常検知とコンテンツスキャン用のML(機械学習)を活用したプルーフポイントの新しい Misdirected Email ソリューションは、第4四半期に提供され、ユーザーが誤ってメールやファイルを間違った受信者に送信することでデータ損失インシデントを引き起こす可能性を防ぎます。
Proofpoint Security Assistant:生成AIベースの分析により、攻撃チェーン全体にわたる脅威の強力な知見を提供
プルーフポイントは、23万を超えるグローバル企業や中小企業、150のISPおよびモバイルネットワークプロバイダーから成る膨大な顧客セットからのテレメトリーに基づき、独自のAIとMLによるイノベーションを継続して提供しています。Protect 2023で初めてプレビューされたProofpoint Security Assistantは、新しい生成AIユーザーインターフェースで、アナリストが自然言語で質問し、プルーフポイントのプラットフォーム全体にわたる何兆もの集約されたデータポイントに基づいて、実用的な知見と推奨事項を受け取ることができます。
DLP SOCアナリストは、第4四半期にProofpoint Sigma(情報防護プラットフォーム)においてテクノロジープレビューとして利用できるようになり、例えば、「何者かによって、情報窃取の試みがなされているかどうかを表示してください、そしてどのDLPコントロールを追加すべきか提示してください」といった質問を投げかけることができます。今後、プルーフポイントの生成AIベースのインターフェースは、Proofpoint Aegis(脅威防護プラットフォーム)とIdentity Threat Defense(アイデンティティ脅威検知プラットフォーム)にも拡張されます。セキュリティ担当者は、「ランサムウェアベースのデータ漏えいにつながる攻撃経路を最も多く持つ主要なVAP(Very Attacked People)を表示してください」といった質問をすることで、脅威に関する強固な知見を得ることができるようになります。
生成AIへの責任あるアプローチ
顧客データの完全性、プライバシー、セキュリティは、プルーフポイントにとって最も重要です。 プルーフポイントは、各生成AIツールが当社の企業理念に準拠しているかどうかを厳格に評価しています。例えば、生成AIツールは社内で展開されたバージョンを使用しており、LLMプロバイダーがプルーフポイントの保有するデータを使用してモデルをトレーニングすることは許可していません。
プルーフポイント米国本社のサイバーセキュリティ戦略担当副社長、Ryan Kalember(ライアン・カレンバー)は次のように述べています。「攻撃チェーンの重要な部分は、人を中心としたアプローチなしには効果的に対処することはできません。プルーフポイントは、ほかのどのサイバーセキュリティ企業よりも多くの人のコミュニケーションを分析することで、メール詐欺、ランサムウェア攻撃、データ窃取、その他の重要なリスクに対する攻撃チェーン全体にわたって、攻撃者のプレイブックを破壊する業界初のイノベーションを提供することができます」
※1:参照: FBI IC3 2022 Internet Crime Report (インターネット犯罪レポート)
※2:参照:ホワイトペーパー:2022 TRENDS IN SECURING DIGITAL IDENTITIES
※3:参照:Gartner Research - Market Share: All Software Markets, Worldwide, 2022
プルーフポイントの各ソリューションの詳細については、以下のリンクよりご覧ください。
- Proofpoint Aegis Platform(脅威防護プラットフォーム):
https://www.proofpoint.com/jp/products/aegis - Proofpoint Identity Threat Defense Platform(アイデンティティ脅威検知プラットフォーム):https://www.proofpoint.com/jp/products/identity-threat-detection-response
- Proofpoint Sigma(情報防護プラットフォーム):
https://www.proofpoint.com/jp/products/sigma
無料デモのご予約は:
https://www.proofpoint.com/jp/free-demo-request
Microsoft365ユーザー向け無料の簡易アセスメントのご予約は:
https://www.proofpoint.com/jp/learn-more/email-rapid-risk-assessment
Proofpoint | プルーフポイントについて
Proofpoint, Inc.は、サイバーセキュリティのグローバル リーディング カンパニーです。組織の最大の資産でもあり、同時に最大のリスクともなりえる「人」を守ることに焦点をあてています。Proofpointは、クラウドベースの統合ソリューションによって、世界中の企業が標的型攻撃などのサイバー攻撃からデータを守り、そしてそれぞれのユーザーがサイバー攻撃に対してさらに強力な対処能力を持てるよう支援しています。また、Fortune 100企業の85%を含むさまざまな規模の企業が、プルーフポイントのソリューションを利用しており、メールやクラウド、ソーシャルメディア、Web関連のセキュリティのリスクおよびコンプライアンスのリスクを低減するよう支援しています。
詳細は www.proofpoint.com/jp にてご確認ください。
© Proofpoint, Inc. Proofpointは米国及びその他の国々におけるProofpoint, Inc.の商標です。本ドキュメントに記載されている会社名、製品名、サービス名は、一般に各社の登録商標または商標です。本ドキュメントの記載内容、製品及びサービスの仕様は予告なく変更されることがあります。











![[TV出演] TBSテレビ「Nスタ」にてチーフエバンジェリスト増田幸美のコメントがフリップで紹介](/sites/default/files/styles/image_75_75/public/misc/260216-tv-nsta.jpg.webp?itok=9G_sjUDN)



