ChatGPTのような生成AIツールは、ビジネスにさまざまな価値をもたらしています。生成AIツールは、コンテンツを書くことができ、文脈を整理することができ、執筆のスタイルやトーンを模倣することができます。 しかし、もし攻撃者がこれらの機能を悪用して、かなり説得力のある、的を絞った自動フィッシングメッセージを広範囲に展開したらどうなるでしょうか?
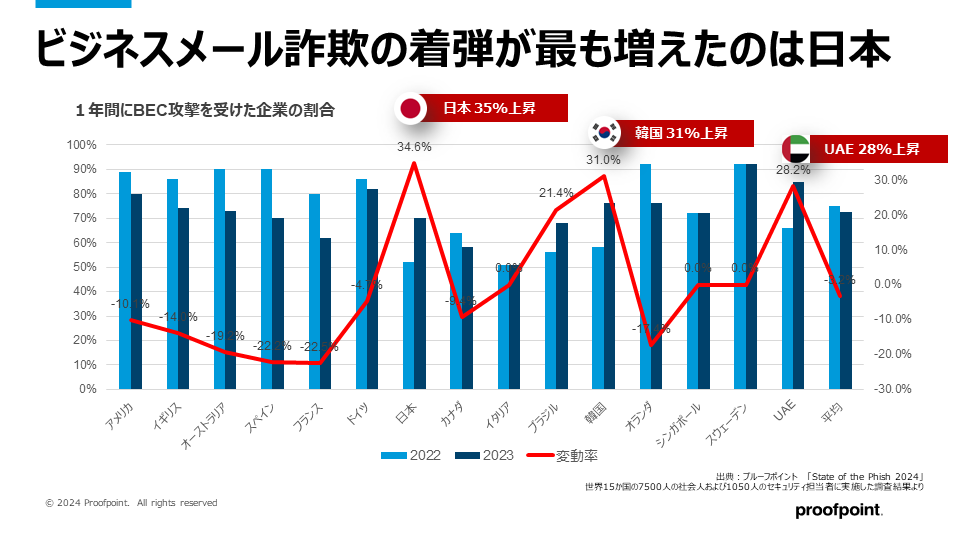
考える必要はありません。実際に起こっているからです。ChatGPTの登場からほどなくして、各地域の言語を用いたビジネスメール詐欺(BEC)攻撃が世界中で広まりました。プルーフポイントによる2024 State of the Phishレポートによると、BECメールはさまざまな国でよりパーソナライズされ、説得力のあるものになっています。日本では、前年と比べBEC攻撃が35%上昇しました。また、韓国では31%、UAEでは29%と、こちらも増加しています。どうやら、生成AIはサイバー犯罪者の生産性を高めているようです。攻撃者は、わずかな労力で高い利益が見込める攻撃方法を常に探しています。生成AIは、まさにそれです。攻撃者は、生成AIのスピードと拡張性を活かして、攻撃に役立つデータを迅速に、簡単に、大量に掘り当てることにより、ソーシャル エンジニアリングの規模を拡げ、威力を高めています。
悪意のあるメール脅威はますます巧妙になり、その頻度も増していく中で、プルーフポイントは、ユーザーの受信トレイに届く前に、こうした攻撃を阻止すべくイノベーションに取り組んでいます。このブログ記事では、生成AIによるメール脅威とはどのようなものか、そしてプルーフポイントの意味解析によってどう阻止できるかをご紹介します。
生成AIによるメール脅威が非常に危険である理由
VerizonのData Breach Investigations Report(2023年データ侵害調査レポート)によれば、データ侵害の4分の3(74%)には人的要因がからんでいます。オンライン詐欺、ランサムウェア攻撃、認証情報の窃取、MFA(多要素認証)回避、その他の悪意のあるアクティビティの根本原因を分析してみれば、この数字はもっと高くなるでしょう。 また、2013年10月から2022年12月にかけて、BEC詐欺による被害額は7兆8000億円(500億ドル)を超えています。これは、現在起こっているソーシャル エンジニアリングの一部でしかありません。
メールは最大の脅威経路であり、調査結果がそれを裏付けています。攻撃者は、メールを使用して人を標的にすることで大きな成果を上げてきました。今後、攻撃者による生成AIの使用が拡大していけば、メールによる攻撃はますます巧妙になっていくでしょう。
これまで、私たちは文法上の誤りやおかしなフォント、不特定多数向けの挨拶文など、明らかに警戒が必要な不審なメッセージを目にしてきました。しかし、生成AIにより状況は大きく変わりました。攻撃者は生成AIに、誰かの書き方を模倣した、文法的に完璧なメッセージを、しかも多言語で書かせることができます。そのため、世界中の企業で、見破ることが非常に難しい偽メールが大量に送りつけられています。
これを阻止するにはどうすればいいのでしょうか?まずは、メッセージの意図を知ることです。
意味解析により脅威を受信前に阻止する
プルーフポイントは、意味解析によりメッセージの意図を察知する、業界初となる脅威検知エンジンを開発しました。意味解析とは、特定の文脈において単語や文が何を意味するかを調べるプロセスです。テキストデータから、そこに潜む意味や意図を抽出することを目的としています。
プルーフポイントの意味解析は、大規模言語モデル(LLM)エンジンを活用し、Microsoft 365およびGoogle Workspaceにおいてユーザーの受信トレイに届く前に高度なメール脅威を阻止します。
どのような単語が使われていても、どの言語で書かれていても、あるいは武器化されたペイロード(URL、QRコード、添付ファイルなど)がメールに含まれていようといまいと、阻止します。プルーフポイントの意味解析により、脅威検知エンジンは、メッセージの意味と攻撃者の目的を察知できます。
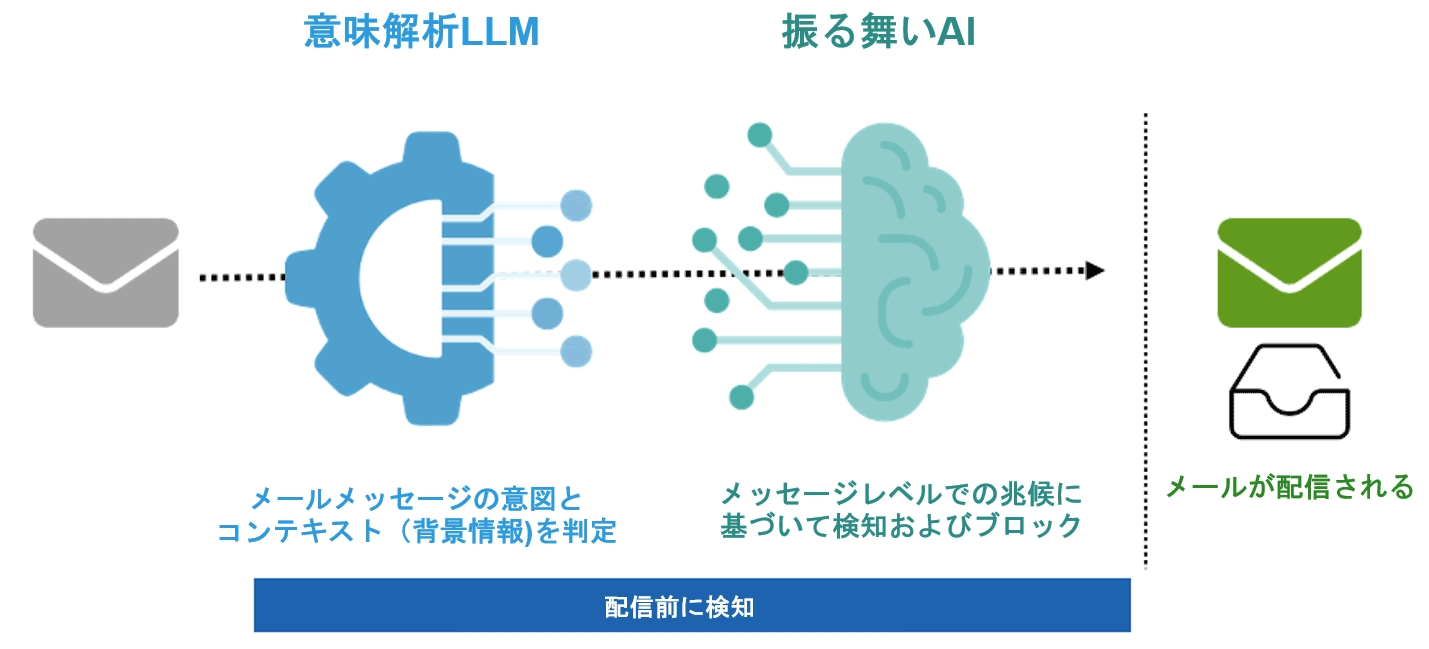
プルーフポイントの意味解析の役割
仕組み
Proofpoint Threat Protectionの脅威検知能力をさらに高めるため、意味解析機能が加わりました。メールは、MLベースの脅威検知エンジンにかけられ、詳細に分析されます。これはメールがユーザーに届く前に行われます。その仕組みを詳しく見ていきましょう。
ステップ1
意味解析の目的は、テキストデータから、そこに潜む意味や意図を抽出することです。さまざまな方法や技術を使用してこれを実現できます。プルーフポイントでは、LLMテキスト エンベディングをプロセスに使用しています。
プルーフポイントの脅威アナリストによって定義された分類に従って意味を検知するよう、モデルを調整しています。このアプローチにより、意味上の類似性をとらえることができるため、メール内で使用されている言葉の意味をよりよく理解することができます。
LLMベース意味解析手法により、プルーフポイントは、強力な表現学習を使用して、メール内のテキストの意味をよりよく理解し、分析することができます。わずかに異なる文章や異なる言語であっても問題なく、複雑な意味上の関係や文脈的な差異をとらえることができるため、優れたテキスト分類や意向分析が可能です。
以下の不審メールの例で、意図を露呈させるフレーズを見ていきましょう。これは、緊急性をあおって振込先を変更させようとするメールです。
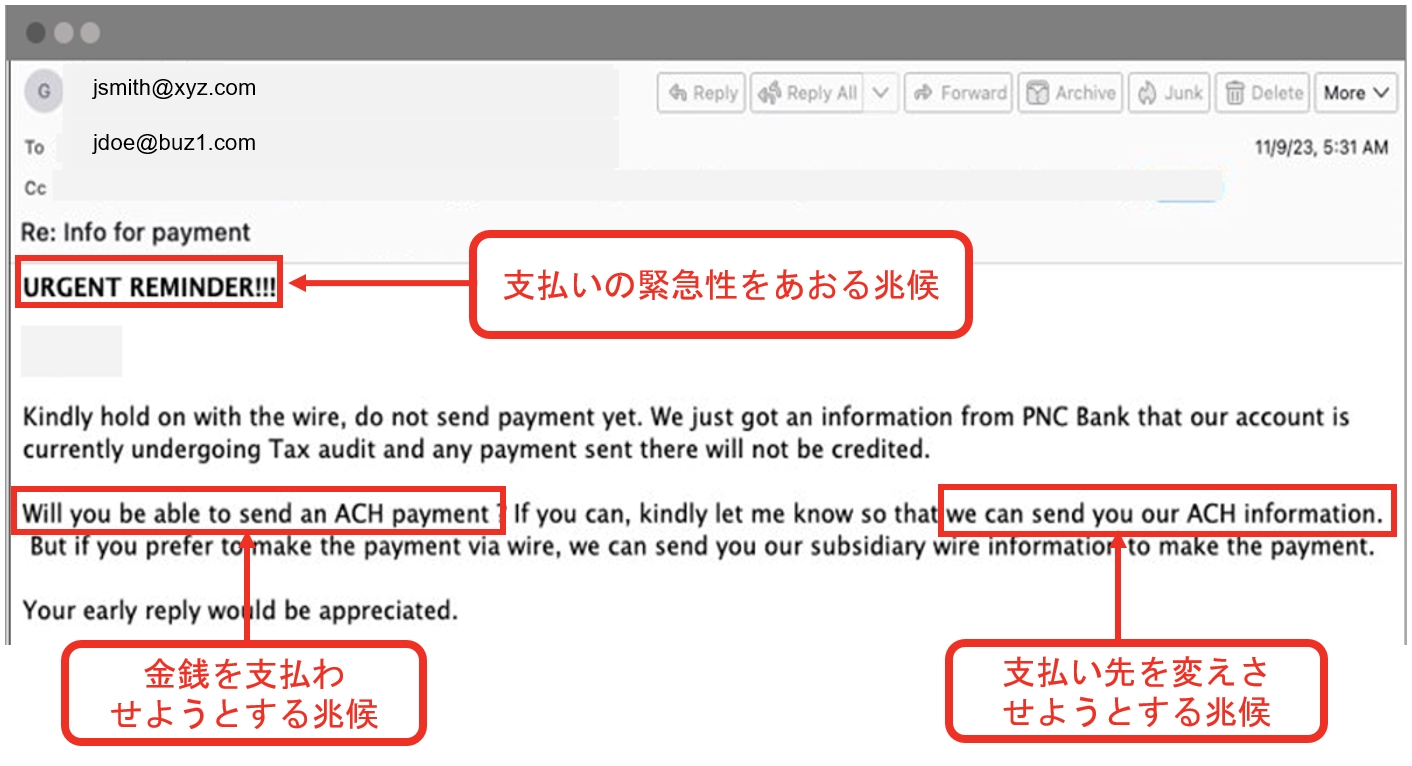
プルーフポイントの意味解析は以下のとおりです。
プルーフポイントの意味解析により、このメッセージの意図は「銀行詐欺」であると判定されました。
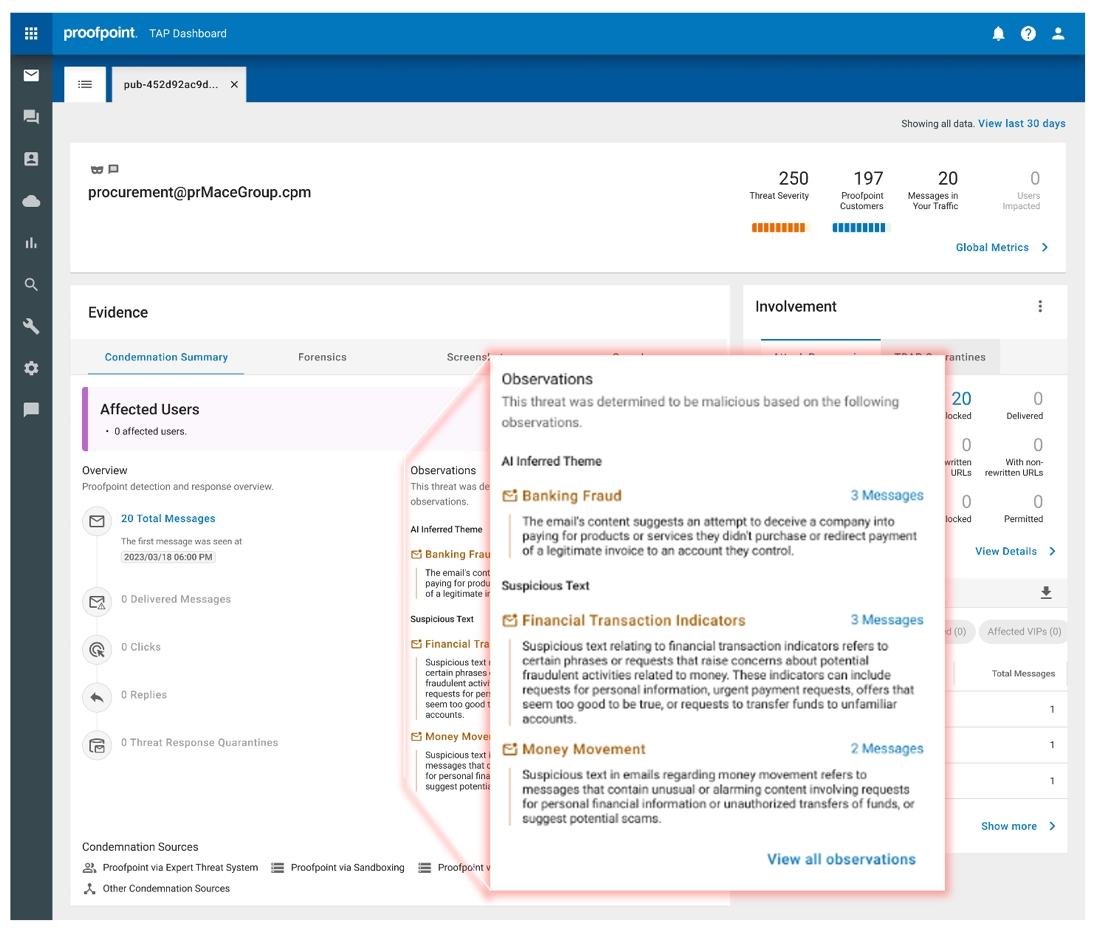
意味解析の説明可能性の例
ステップ2
プルーフポイントは、振る舞いAI検知エンジンを使用して、以下のようなメール主要属性から、異常の兆候を見つけます。
- 送信者
- 受信者
- ヘッダー
- メッセージ特性
- 画像
- URLリンク
- 添付ファイル
- その他多数
このアプローチにより、プルーフポイントでは毎月数千万の高度なメール脅威を検知し、ブロックすることができます。具体的には、50万人を超える顧客で検知される、ビジネスメール詐欺(BEC)、電話を用いた攻撃実行(TOAD)、マルチファクタ認証(MFA)回避攻撃などです。また、これらのメールがユーザーの受信トレイに届く前にブロックします。
継続的なイノベーションへの取り組み
昨今のメール脅威状況は、巧妙な攻撃が日々無数に現れていることから、フラグメント化が特徴となっています。フィッシング詐欺からランサムウェア攻撃にいたるまで、攻撃者は絶えずその戦術を進化させており、メールシステムや人の行動における脆弱性につけこんでいます。こうした脅威に対抗するには、完全かつ包括的なアプローチが重要です。メール配信チェーンにおいて(受信前から受信後やクリック時にいたるまで)継続的な脅威検知と分析を提供する最新のアプローチにより、組織は、生成AIのような新しい脅威に対しても、隅々まで保護を実現することができます。
プルーフポイントは20年にわたり、AI、機械学習(マシンラーニング)、検知エンジン技術の面でイノベーションに取り組んでいることを実証してきました。この20年で、革新的な250以上の特許を取得しています。シンプルなメールセキュリティ ツールは、単一レイヤーの検知スタックを使用して受信メールを分析しています。しかしプルーフポイントは、継続的な検知スタックにより、イノベーションにおいて市場の一歩先を行きます。
Proofpoint Threat Protection は、最新の脅威を高精度で特定するマルチレイヤーの検知スタックを搭載しています。 プルーフポイントは、さまざまな検知技術を使用してさまざまな脅威をとらえています。プルーフポイントの広範な検知技術セットにより、適切な技術を適切な脅威に適用することができます。
振る舞いAIと共に意味解析を活用することで、プルーフポイントは、高度なメール脅威に対する高精度の検知と有効性を企業に提供します。
プルーフポイントは「人」を中心としたセキュリティを提供
防御側にとって、ユーザーを悪意のあるメールから保護するために、プロアクティブなアプローチを採用することがかつてないほど重要になっています。プルーフポイントによる受信前の意味解析と振る舞いAI検知により、悪意のあるメールがユーザーの受信トレイに届く前に阻止することができます。マルチレイヤーの検知スタック アプローチにより、企業は悪意のあるメッセージを継続的に検知し、分析することができます。これにより、最も巧妙なメール脅威からでさえも従業員を保護できます。
プルーフポイントが先日発表した、新しい意味解析LLM検知エンジンは、すべてのProofpoint Threat Protection の顧客に提供されます。 従業員と企業を保護するために、Fortune 100企業の87%がプルーフポイントを利用している理由についてはこちらのソリューション概要をご覧ください。











