Email authentication is a critical measure to help prevent threat actors from sending email under the pretense of being from your organization. This tactic is referred to as domain spoofing and, if left unprotected, allows cyber criminals to weaponize your sending domains for malicious cyber attacks.
How is Domain Spoofing possible?
To understand how domain spoofing can happen, we need to step back and talk about the process of email sending in general.
For simplicity’s sake, let’s use the example of a newly formed company. The business decides on an awesome company name and registers its domain name to get its website up and running. It also sets up email addresses that leverage the domain name to get communications flowing.
The company is now the proud owner of www.awesomecompanyname.com and has created the email address: email1@awesomecompanyname.com. But there’s a problem: The SMTP protocol used to support the sending of email1@awesomecompanyname.com wasn’t built with any security controls, so now it can easily be forged.
It may be hard to believe there is nothing stopping anyone from changing the “from” entry in an email to state that it’s coming from email1@awesomecompanyname.com, but that is how domain spoofing is possible.
The whole goal of domain spoofing is to convince an unsuspecting target that they’re dealing with a legitimate and often trusted sender. Without additional security measures, bad actors could exploit the SMTP relay weakness described above to initiate malicious attacks—putting a company’s brand reputation at risk.
Email Authentication to the rescue
To combat domain spoofing, Sender Policy Framework (SPF) was introduced, followed by Domain Key Identified Mail (DKIM), with the goal of validating that email is coming from an approved sending IP address and the message hasn’t been tampered with in route.
A company can create an SPF record that contains a list of all the “approved” IP addresses that can send email on the organization’s behalf. This allows a system receiving an email to do a quick check to determine if the email is coming from an authorized server. If the sending IP address isn’t on the SPF list, it fails authentication.
DKIM goes a step further by using public and private keys, allowing a receiving system to compare the keys in the email to confirm that it came from who it says it did and that nothing in the email was changed after it was sent.
Someone sending a domain-spoofed email would fail both SPF and DKIM authentication.
It seems simple enough—but it’s not
Maintaining accurate and up-to-date SPF and DKIM records is a challenge. It’s even more complicated for larger organizations that have a vast number of sending domains to protect and which may not have direct access to records to make changes.
SPF and DKIM records are often managed by a separate team or external company in charge of their Domain Name System (DNS). This can lead to additional costs and delays in getting changes made. These delays can not only impact deliverability, but incorrect records could also increase security risks.
How Hosted SPF and Hosted DKIM can help:
SPF was first introduced over 20 years ago and in the world of technology, that is a lifetime ago. And with the rapid migration to the cloud, the traditional approach to SPF is now insufficient.
To start, the current process of manually adding IP addresses to a DNS record is ripe for human error. Breaking an SPF record could ultimately lead to the rejection of legitimate emails. Also, SPF wasn’t designed to handle the large number of sending addresses that we now see, especially with the increasing use of software-as-a-service partners that most companies use. You need only look at the 10 SPF DNS lookup limit to see that current times require an updated solution.
A macro-based hosted SPF solution can overcome the lookup limitation and provide automation to reduce the risk of errors. It can also be updated in real time without the need for time-consuming and sometimes costly change requests to the DNS team.
Not all Hosted SPF solutions are the same, so in addition to being macro based, selecting a solution that obfuscates IP Addresses will make it harder for attackers to gain insights that they can exploit.
In the case of DKIM, where selectors and keys need to be updated consistently to ensure the highest level of protection, the value of having a hosted solution can be even higher. It takes a special skill set to manage these long and complex DNS records correctly, and even the smallest error can create a parsing issue that stops legitimate email from being received.
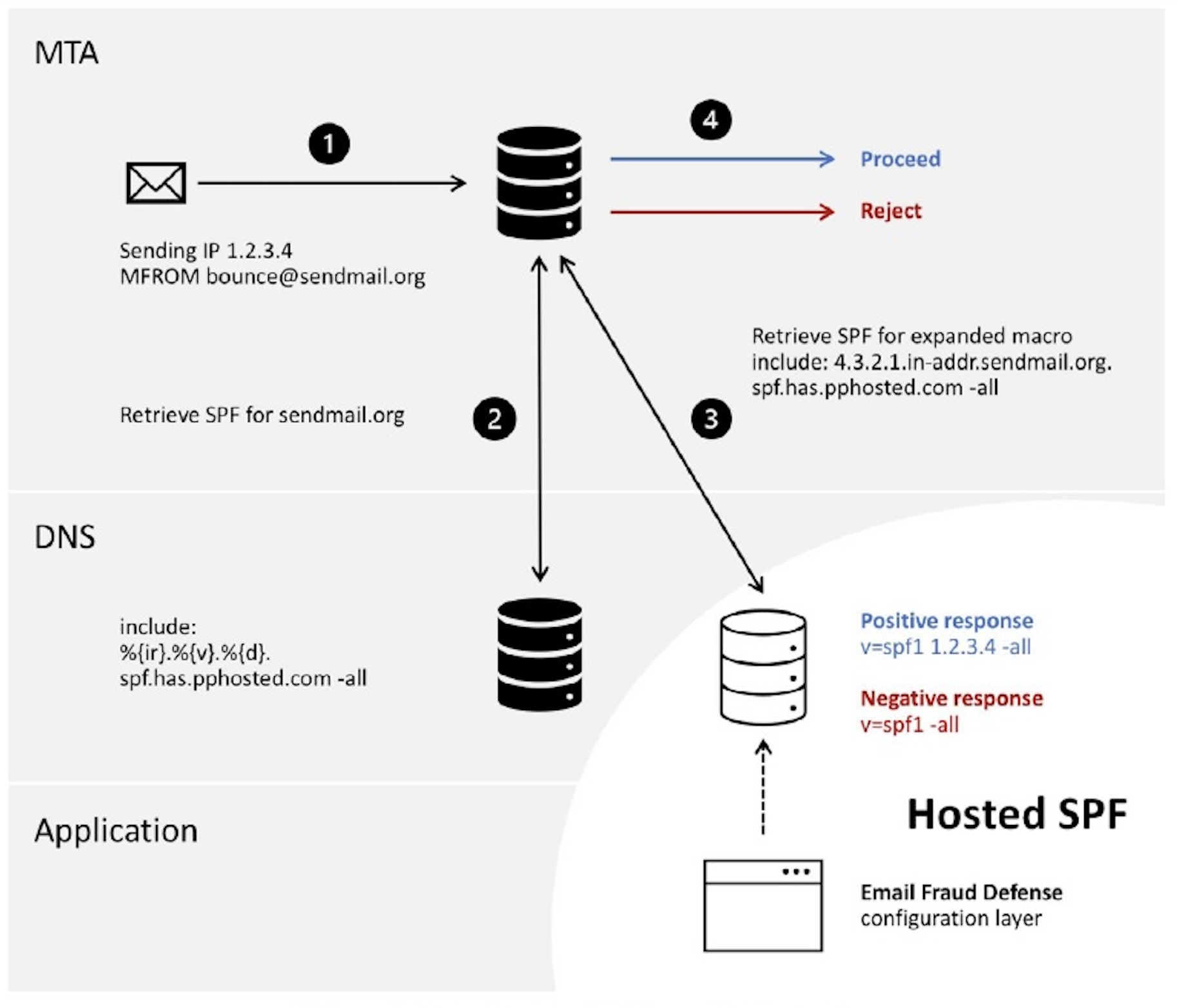
Figure 1: How Proofpoint hosted SPF works
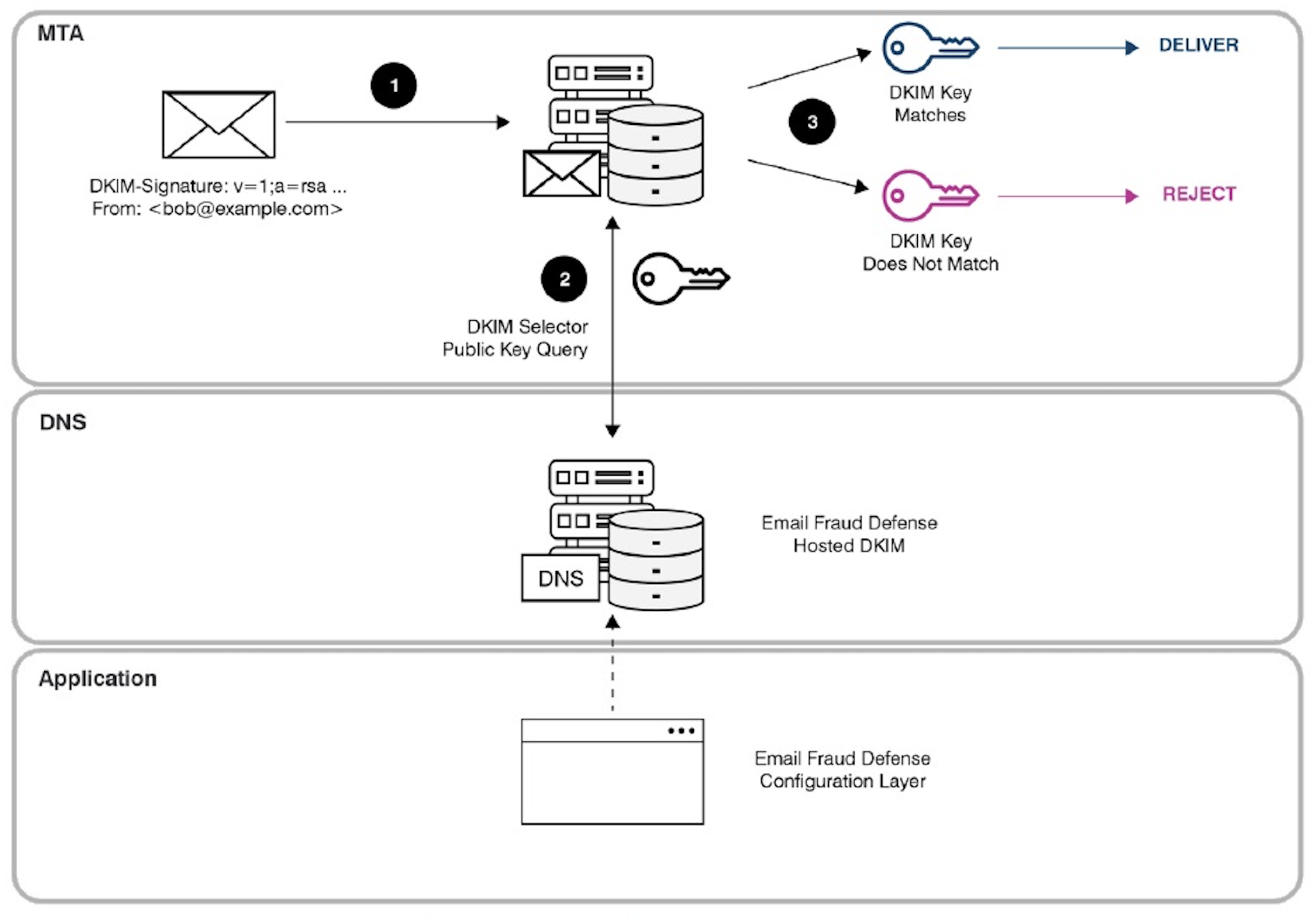
Figure 2: How Proofpoint hosted DKIM works
Hosted DKIM introduces automation, which can simplify selector and key management and also eliminate manual data entry, reducing the risk of errors.
Like hosted SPF, hosted DKIM updates can support near-real time changes, without requiring the creation of a change ticket to be submitted to the DNS team. The hosted services can do the updates directly.
A modern alternative that overcomes traditional limitations
Email authentication is vital to ensuring that email domains aren’t spoofed and preventing bad actors from using a company’s trusted domain name in phishing and other malicious email attacks.
SPF and DKIM, along with DMARC, which informs a company what to do if an email message fails either SPF or DKIM authentication, are essential components that must be configured correctly and maintained regularly to optimize protection.
Hosted SPF and hosted DKIM services provide a modern alternative that can remove traditional limitations, reduce errors and streamline the updating process.
To learn more about how to protect your brand reputation from domain spoofing and help ensure maximum deliverability of legitimate emails, check out Proofpoint Email Fraud Defense on our website or contact us today!











