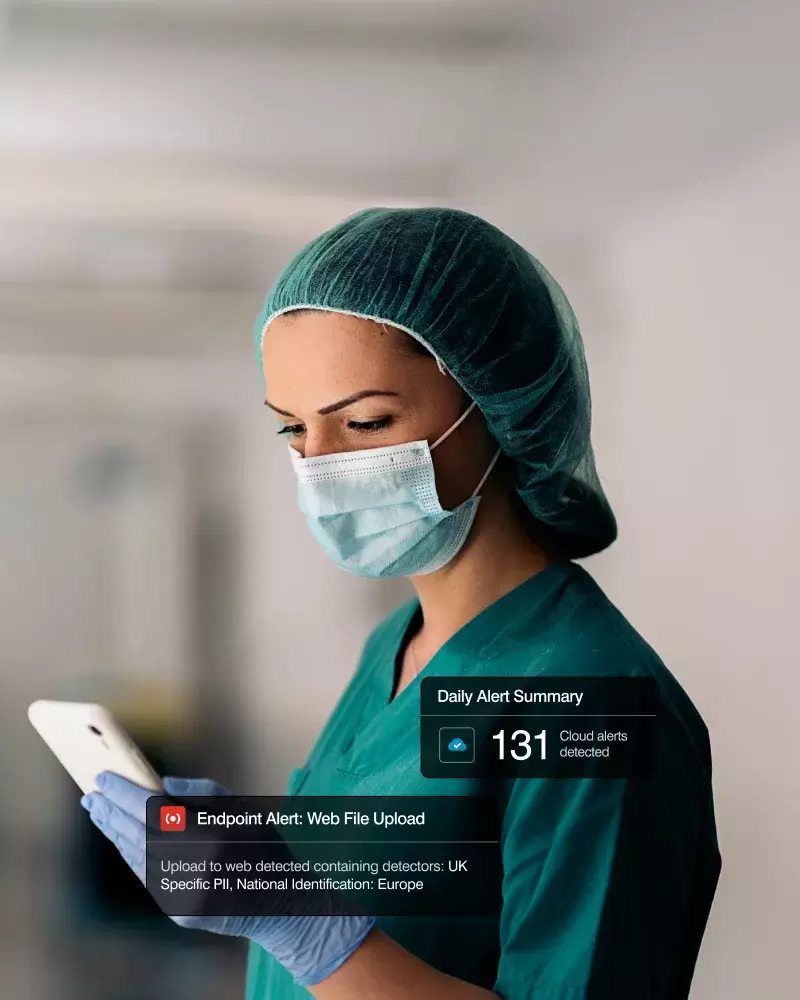
Traditional DLP needs to transform
Organizations struggle with the limitations of legacy data loss prevention (DLP) solutions because their content-driven alerts lack insights. Analysts scramble to investigate cross-channel incidents using multiple dashboards and siloed tools, draining resources and wasting valuable time.
Prevent data loss from careless compromised and malicious users.

Proofpoint employs a human-centric approach for
deep visibility into user behavior and content, enabling effective detection and prevention of significant data loss risks. We update traditional DLP strategies by integrating protection across endpoints, web, and email. Our cloud-native architecture and modern privacy controls ensure quick deployment and straightforward maintenance.
Through our unified console and advanced analytics, we streamline incident management and enable analysts to effectively counteract careless or malicious behaviors, thus safeguarding data efficiently.
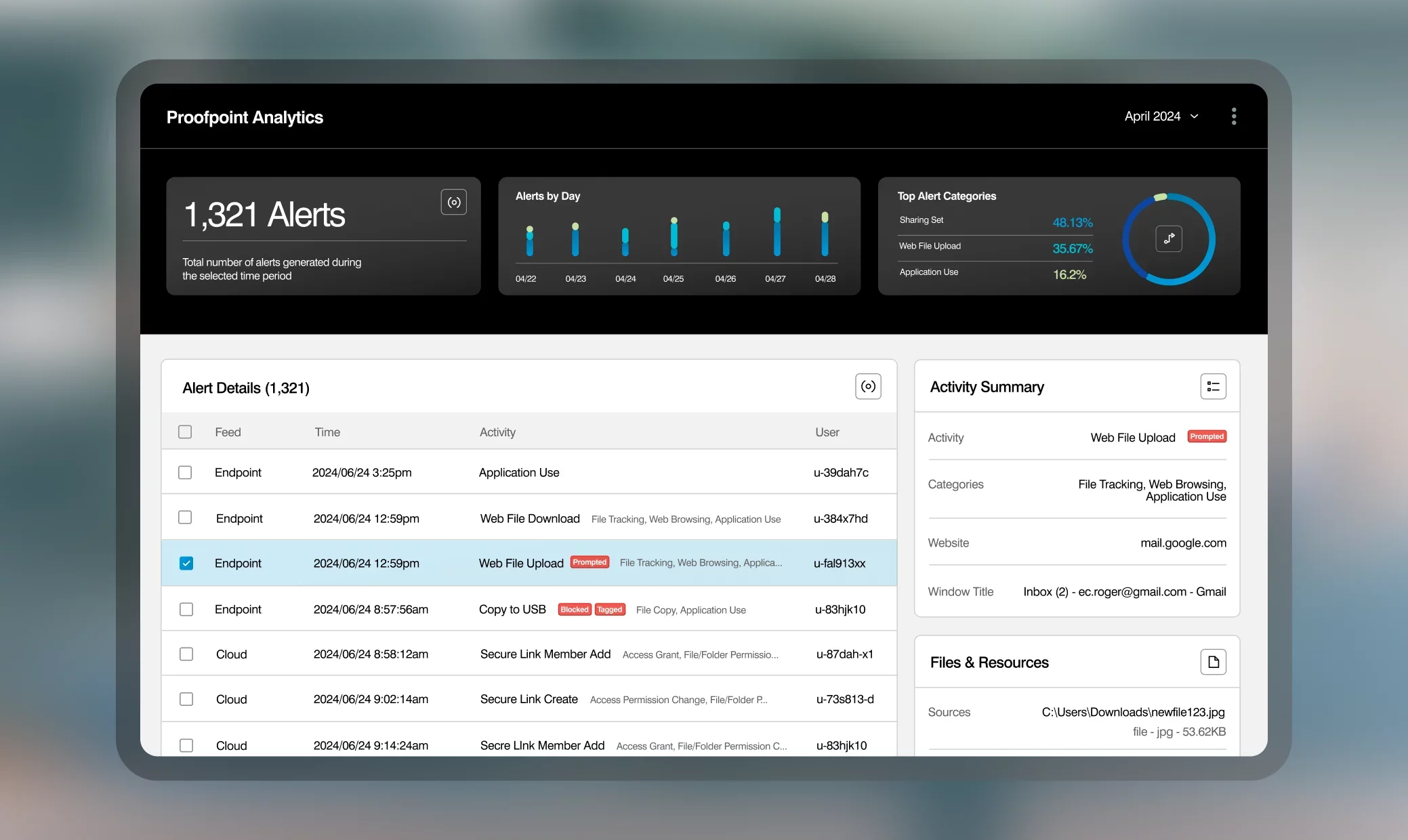
Quickly detect and resolve data loss risk across email, cloud and endpoints. Triage all DLP alerts, investigations, and response in a single console.
Deploy quickly, scale automatically and maintain with ease.
Prevent data loss with a user behavior and data detection
Key benefits of our stop data loss product
Extend your email DLP to cover broader use cases
Proofpoint’s enterprise DLP approach enables you to extend data detection from email to protect data in cloud and endpoint to address today’s most worrisome use cases, like protecting cloud data and controlling the acceptable use of GenAI tools.

Detect and resolve data loss risk
Accurately identify sensitive content and get deep visibility into user behavior and intent. With Proofpoint, your analysts can decisively assess data loss risk and respond effectively the across email, cloud and endpoints. See how users interact with data and what potentially risky tools they download and install.
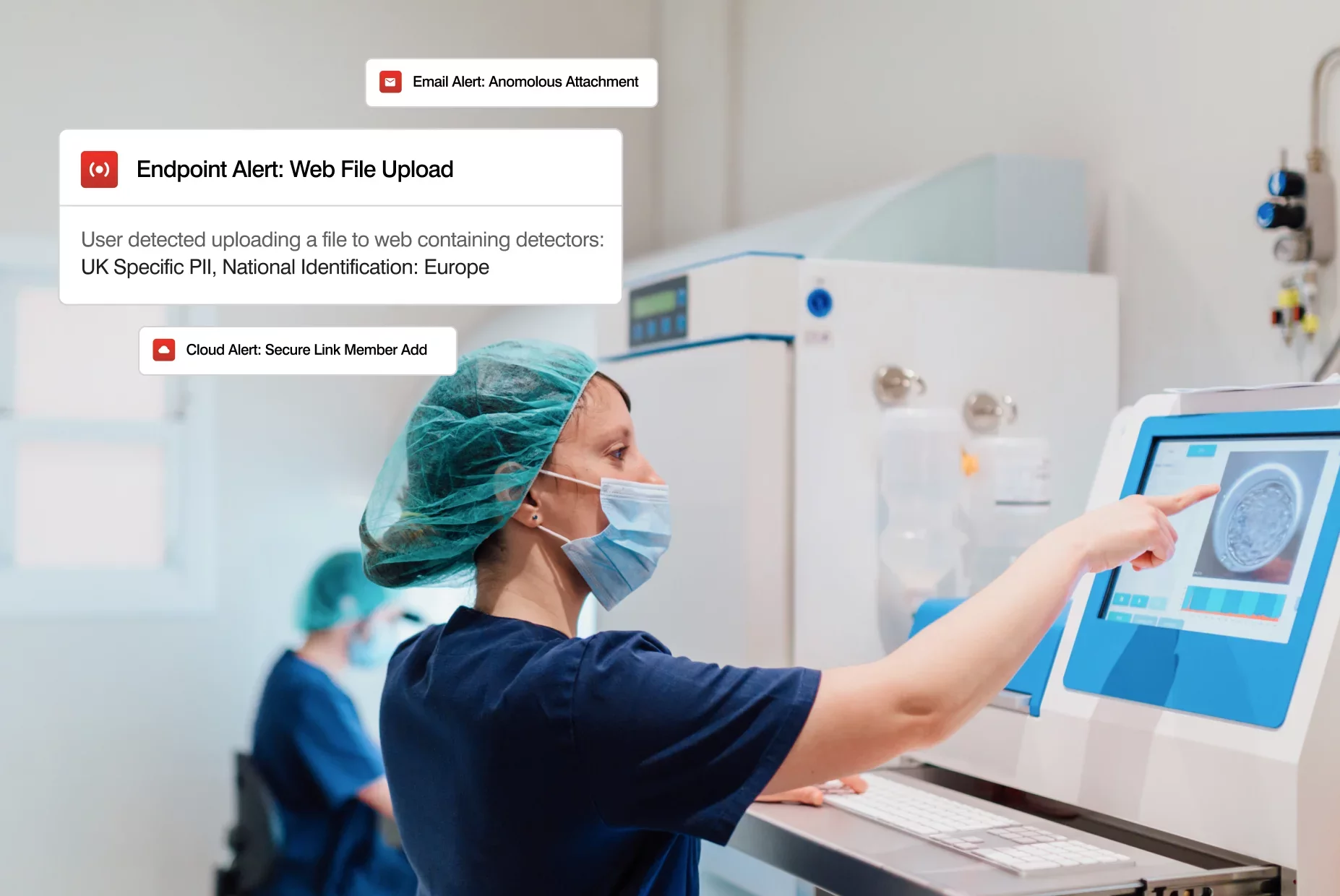
Streamline incident response and resolution
With a unified console, your analysts can streamline alert triage on email, cloud, and endpoint. Analyze user activity, file changes, and file sharing to speed up investigations and response. Explorations instantly reveal changing user patterns and risky behavior.
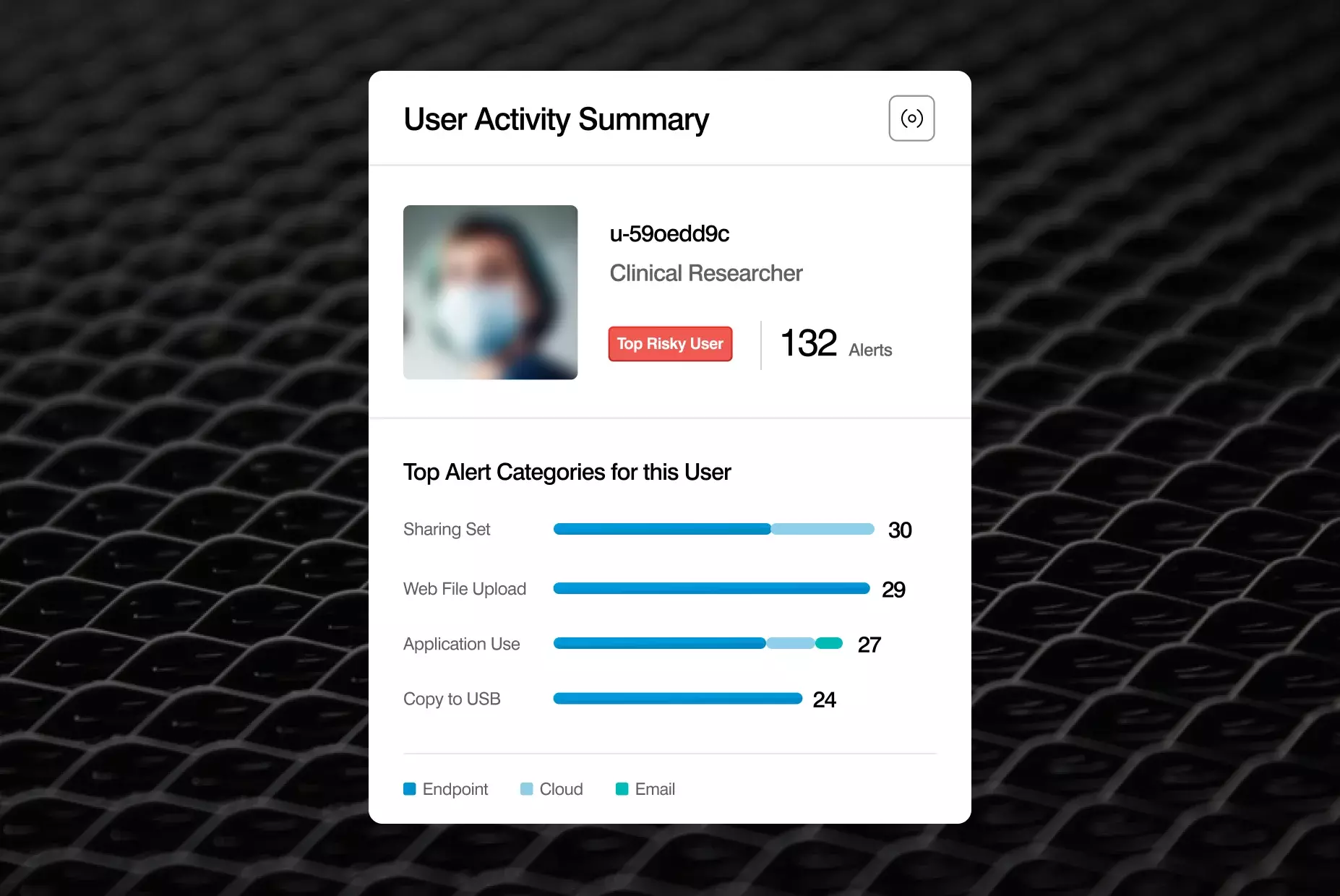
Deploy easily, protect user privacy
Thanks to its modern cloud-native architecture and lightweight endpoint agent, Proofpoint is easy to deploy, scale and maintain. It is also engineered with privacy by design. Beyond anonymizing user activity and limiting analysts’ access to specific users’ data, it also meets data residency requirements across multiple regions.
Managed services that shorten time to value
Let our highly skilled team of experts get you up and running quickly and provide ongoing management. Optimize your technology investment, augment your staff and mature your organization’s data protection strategy.
Key features that stop data loss
Insight into user activity and intent
Proofpoint works across managed and unmanaged endpoints and cloud to detect sensitive data (including within images) and reveal user activities, including:
- File renaming and changes to file extensions
- Website and application usage
- USB and cloud drive uploads
- Software downloads and installs (like data backup of hacking tools)
- Windows registry changes
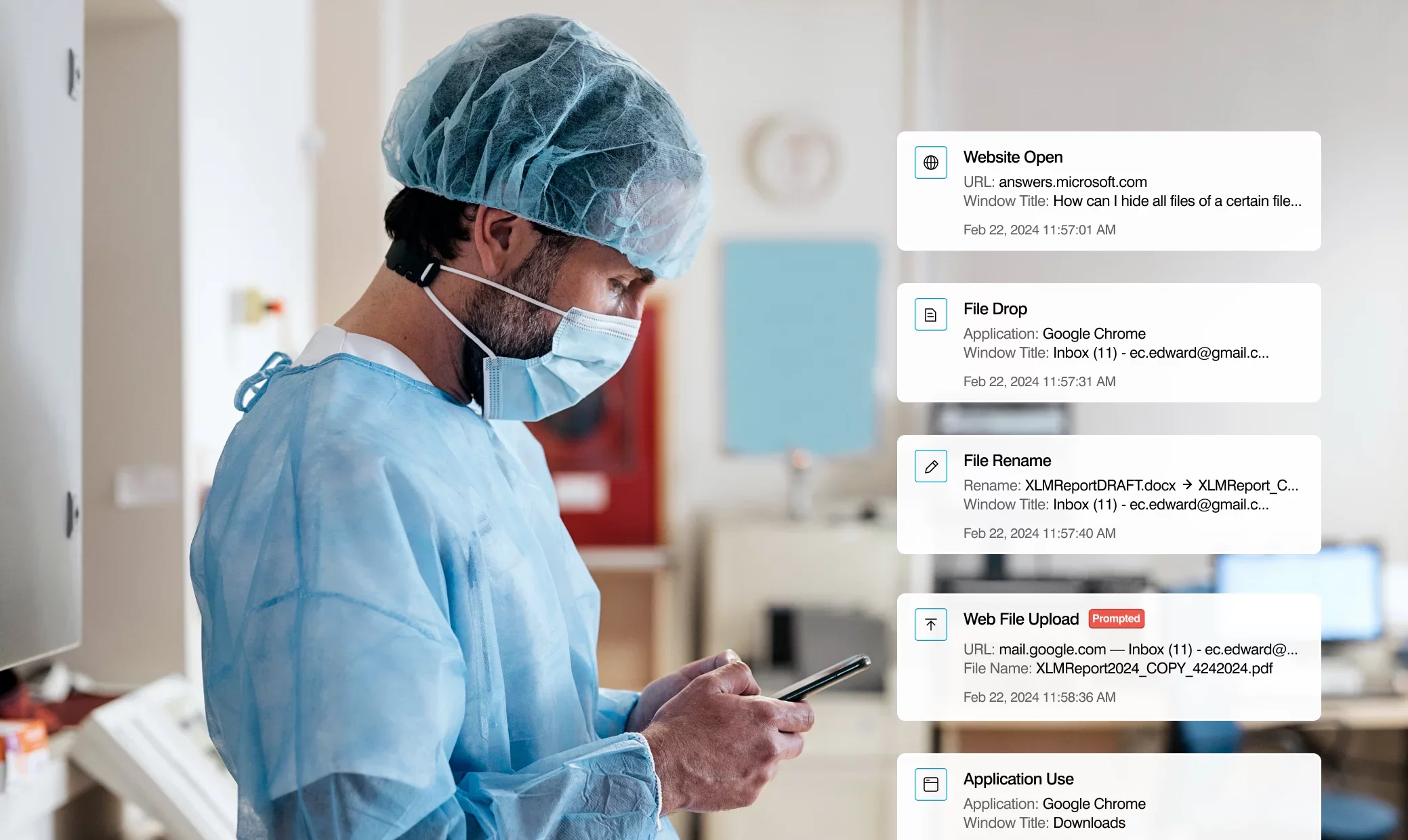
Unified console
Build custom explorations to proactively manage data risk with sophisticated search and filtering features. Search for data exfiltration and risky activities, including uploading data to new tools such as generative AI. A timeline view of user activities helps you understand the “who, what, where, when and why” behind each incident.
Modern cloud-native architecture
Proofpoint can easily scale to hundreds of thousands of users per tenant and works with the rest of your security infrastructure, such as Microsoft, Okta, Splunk, ServiceNow. Centralized policy and administration streamline workflows. And our stable, lightweight user-mode endpoint agent won’t conflict with other security tools.
Granular privacy controls
Flexible access controls ensure analysts only see data on a need-to-know basis. It anonymizes identifying user information and masks sensitive content to protect personal data, ensure privacy and eliminate analysts’ bias. Data centers in the U.S., Europe, Australia and Japan, can also help you meet data residency and storage rules.
The latest developments in data loss

2024 Data Loss Landscape Report
Read More
Redefining Data Loss Prevention (DLP)

DLP Transform
Protect more than your people: Defend Data
Get Started