Across industries, the digital workspace is fast becoming the agentic workspace, where people and agents collaborate. This transformation promises enormous gains in operational efficiency but also brings fresh data security challenges. Here, every interaction—whether human or AI-driven—carries the potential for data exposure, exfiltration, or misuse. Now more than ever, organizations need to locate their data, understand its purpose and value, and protect how it is used.
Piecemeal solutions that use multiple point products leave critical gaps in visibility and protection. To solve this problem, Proofpoint has launched Data Security Complete—a unified solution that secures your data everywhere it lives and governs how both people and AI interact with it.
A unified solution for data security
Data Security Complete is the industry’s only unified solution, providing visibility and control for every piece of sensitive data. Unlike fragmented stacks of point products that provide incomplete protection, increase administrative costs, and overwhelm teams with complexity, our unified data security solution delivers consistent, end-to-end coverage across every channel. By bringing together multichannel Data Loss Prevention (DLP), Insider Threat Management (ITM), and Data Security Posture Management (DSPM), Data Security Complete eliminates inefficiencies and lowers administration costs by up to 58%.
With Proofpoint Data Security Complete, organizations can embrace the agentic workspace by:
- Preventing exfiltration and loss by blocking misdirected, accidental, or malicious data movement across email, cloud, web, and endpoints
- Detecting insider risks early by correlating user content and context, dynamically adjusting controls, and accelerating investigations with irrefutable evidence
- Securing data at rest by discovering and classifying sensitive data in cloud and hybrid environments, then remediating risks with one-click controls
- Enabling safe AI innovation by enforcing acceptable use policies for generative AI and securing sensitive data from unintended exposure
In this new era, organizations must secure AI agents with the same rigor as their people. Data Security Complete secures sensitive data across all channels, and the Proofpoint Secure Agent Gateway extends those protections into every agentic workflow. Learn more about Secure Agent Gateway in our blog: “Stop customer-deployed AI agents from losing data with Proofpoint Secure Agent Gateway.”
Innovations that set Data Security Complete apart
Data Security Complete isn’t just another DLP product—it’s a leap forward in data-centric security. Let’s explore the advanced capabilities that make it unique.
Autonomous Custom Classifiers
Traditional DLP depends on static rules and manual tuning, leading to false positives, blind spots, and administrative burden. Proofpoint’s Autonomous Custom Classifiers solve this by using AI models that adapt continuously to how employees handle data.
Our classifiers learn from real usage, identifying patterns in how sensitive data moves across repositories and communication channels. By understanding business context, they reduce false positives and ensure alerts are meaningful. Organizations can scale without endless rule-writing, ensuring that data security posture evolves naturally with their business.
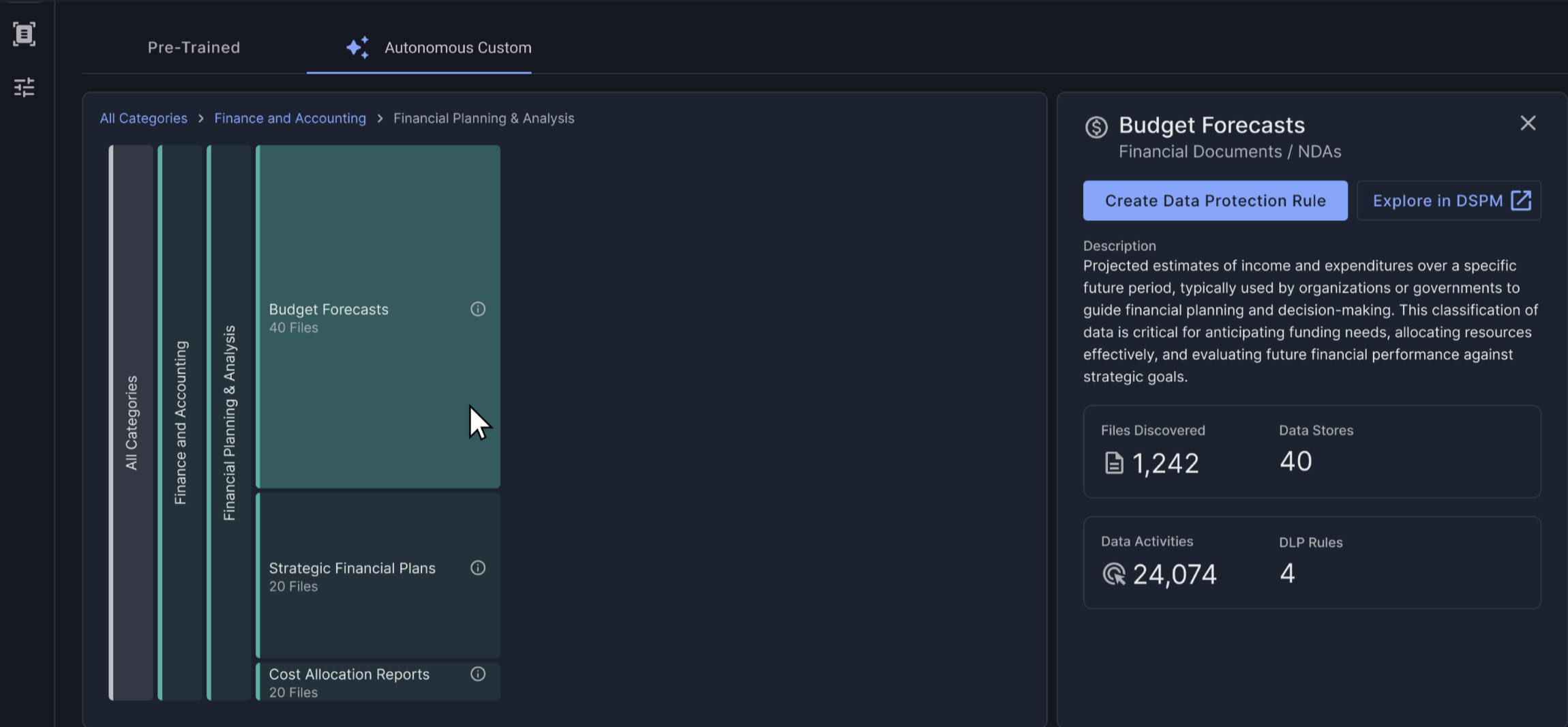
Figure 1: Autonomous Custom Classifiers understand business context to classify documents across all data stores. This dramatically reduces false positives and ensures that alerts are both accurate and actionable.
Risk visualization and prioritization using the Data Risk Map
You can’t protect what you can’t see. An important outcome from taking a unified approach to data security is that you have a single consolidated and intuitive view of where sensitive data resides, how it’s moving, and who’s accessing it. We call this the Data Risk Map.
This visibility shows teams where to act, transforming data security from reactive firefighting to proactive data governance.
From the Data Risk Map, Proofpoint provides end-to-end visibility into data flows for incident response. This cross-channel data lineage capability is powered by Proofpoint Nexus® data lineage models. It traces sensitive data from its origin through every manipulation, copy, and transfer—right up to its egress channels.
For incident response and risk analysis, this traceability means security teams can see exactly where a file originated, how it traveled, and who interacted with it. They can then apply controls based on the file origin and this extra contextual intelligence.
By combining visibility with contextual intelligence, Proofpoint turns data lineage into a powerful tool for reducing insider risk, preventing exfiltration, and simplifying compliance.
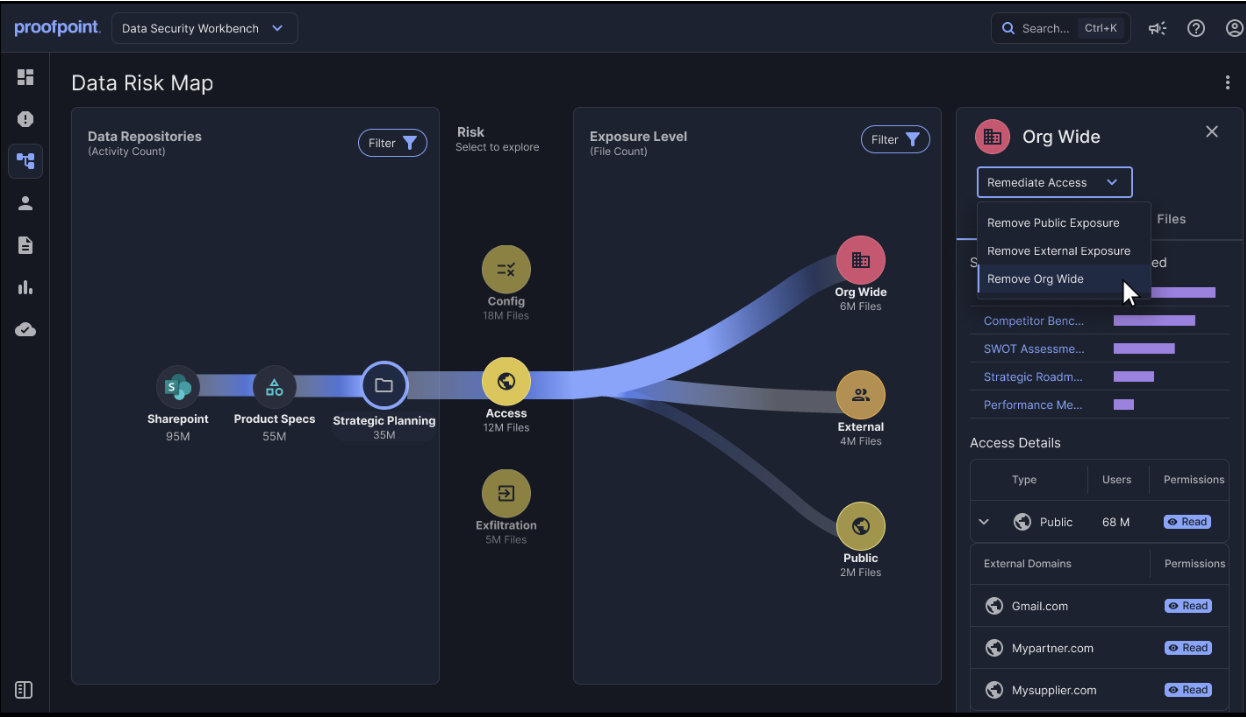
Figure 2: Data Security Complete includes cross-channel data lineage that traces sensitive data from its origin through every manipulation, copy and transfer—right up to its egress channels.
One-click remediation actions for Microsoft 365 and Google Workspace
In the Data Risk Map, security teams can take one-click remediation actions for Microsoft 365 and Google Workspace. Teams can instantly revoke unauthorized access, adjust risky file-sharing permissions, or quarantine exposed files. These actions accelerate threat containment and ensure sensitive data stays protected across the collaboration platforms employees use every day.
Governance of safe AI data use
Generative AI tools such as ChatGPT, Copilot, and Gemini bring huge productivity gains, as do third-party applications that are AI enabled. But they also pose new risks when sensitive data is uploaded or processed without oversight.
Proofpoint’s AI Data Governance module provides a framework for safe enterprise AI use. Organizations can discover both sanctioned and unsanctioned AI use, apply prebuilt policies to prevent exfiltration and privacy violations, and govern access with automated workflows for security teams and content owners.
With visibility into what data is fueling AI models, businesses can align adoption with compliance requirements while preventing careless or malicious exposures. Proofpoint empowers organizations to embrace AI with confidence, maximizing innovation without sacrificing security.
Your next steps
Data security is no longer optional—it’s mission critical. As attackers grow more sophisticated and the agentic workspace broadens insider risks, organizations need a modern solution that works as hard as they do.
Proofpoint Data Security Complete is available now. To learn more, visit Proofpoint Data Security Complete or contact your Proofpoint representative to schedule a demo.











