Over the last month, Proofpoint researchers have been tracking a new trend in malicious email campaigns: attached JavaScript files. While threat actors have been using attached Microsoft Office files with embedded malicious macros for years and both users and most antivirus applications are generally aware of the dangers of .exe files (executables) attached to emails, the use of .js directly in email has only been used occasionally in the past. Moreover, these campaigns are appearing in unprecedented volumes with hundreds of millions of messages being sent across our customer base.
So why .js? According Bryan Burns, Vice President of Threat Research at Proofpoint,
“Users have been trained to not click exe attachments, but many may not know what a “js” file is, or that it can be just as dangerous. The icon looks like a document which is somewhat confusing to users unfamiliar with this file type.”
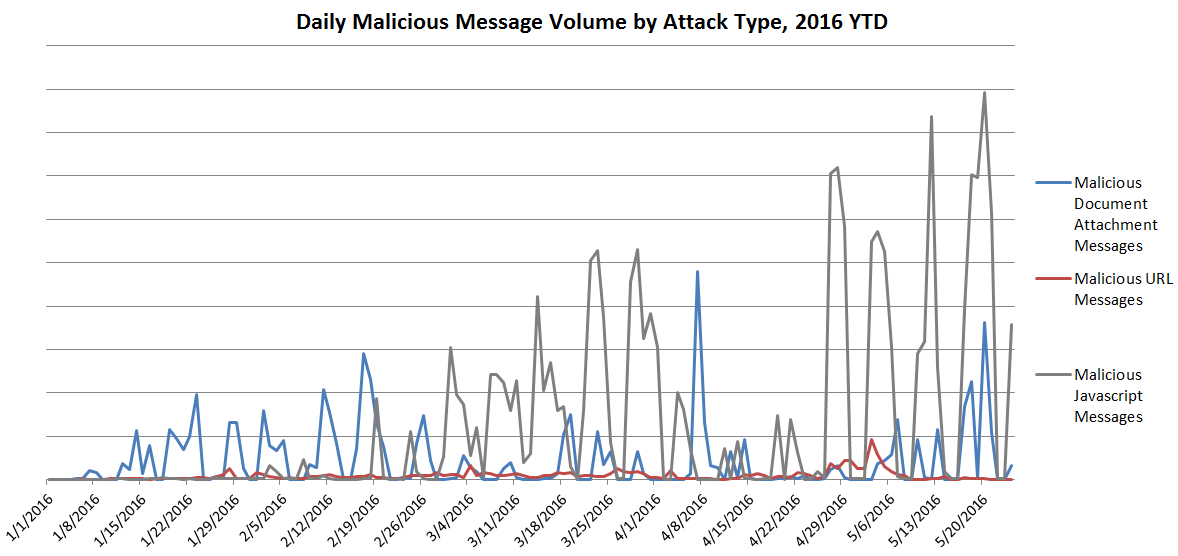
The sheer message volume is also a distinguishing feature of these campaigns. The graph below shows the relative volumes of .js attachments versus other malicious documents in recent campaigns, with .js messages exceeding all other document attachments combined by 4-8 times at their peaks:
These are, in fact, the largest campaigns observed in recent years by Proofpoint researchers, relying on massive botnets to distribute huge volumes of malicious emails. The botnets are worldwide, but India and Vietnam are by far the largest sources of sending IP addresses for these campaigns. The figure below shows the relative number of messages originating from each country.
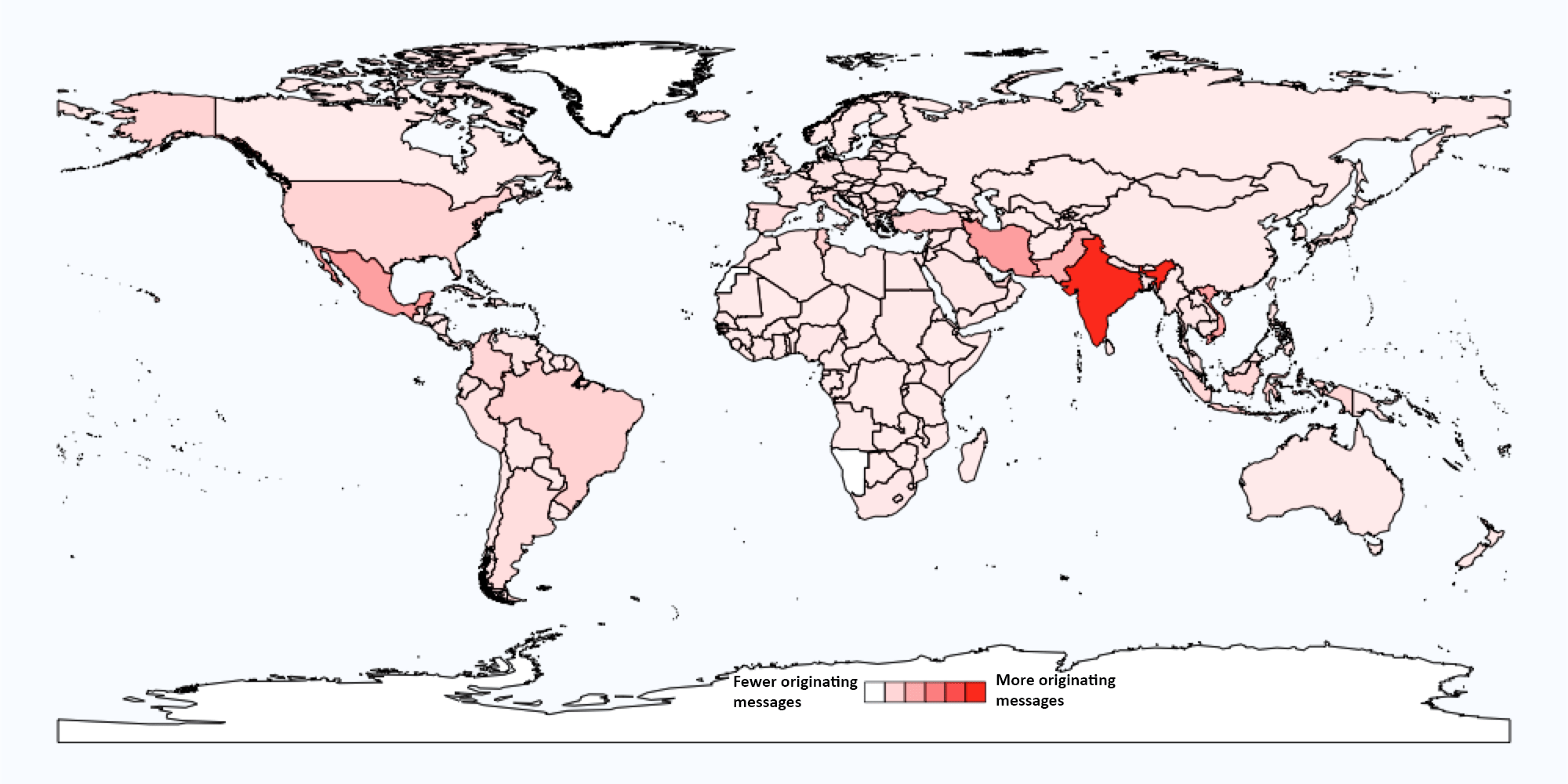
Relative sending volumes by country for recent JavaScript campaigns.
The size of the campaigns suggests that threat actors are attempting to capitalize on user naiveté regarding this rarely-used approach. While many of the emails in these campaigns have the .js files attached without modification, others use obfuscated JavaScript, come with different file extensions, or appear in compressed files to further obscure the malicious nature of the attached files for recipients.
Although this technique has been used before with ransomware variants like Teslacrypt and CryptoWall, these campaigns are almost exclusively dropping Locky and Dridex. We have observed little in the way of industry or vertical targeting, but, because Dridex uses country- and bank-specific injects, we have seen some geo targeting in the US, the UK, and Western Europe. Locky, on the other hand, has taken much more of a shotgun approach with simply very high volumes and little targeting.
In addition, the email lures used with these campaigns have not changed dramatically from other campaigns using standard Microsoft Office document attachments. The threat actors' goal remains to entice recipients to click on the attached files, although recipients don't need to go through the extra step of enabling macros. The JavaScript files just execute when opened, attempting to install the malware directly.
These campaigns are of concern because
- Their massive volumes dramatically increase the risk of finding recipients without sufficient electronic protections or who don't recognize potentially malicious file attachments and
- The files are not immediately recognizable as malicious (like .exe files) and don't generate macro-related warning messages.
For both organizations and individuals, this means that using antimalware solutions capable of detecting advanced threats becomes more important than ever. At the same time, we need to ensure that users remain vigilant in email best practices and are aware of the growing variety of attached documents that may be malicious.