Enterprise cloud adoption shifts the cybersecurity landscape for both attackers and the organizations they target. As data moves to the cloud cyber threats move with it, evolving their targets and priorities.
Today, we are excited to announce the Proofpoint Cloud App Security Broker (PCASB). It enables organizations to maximize and sustain the advantages of cloud adoption – while delivering a new approach to disrupt attacks in a fast-changing threat landscape.
In combination with Proofpoint’s leading email security solution, which safeguards the most visible and targeted cloud application, PCASB delivers unparalleled protection for Office 365 and G Suite protection. It protects cloud apps such as Microsoft SharePoint Online, OneDrive, G Drive, Box, and more from advanced threats, accidental sharing of sensitive data, and compliance risks in the cloud.
The anatomy of a people-centered attack
Threat actors are targeting users, not infrastructure. Let’s take a look at series of attempts we recently saw in an audit of an 80,000 user organization’s Office 365 environment.
Let’s look at a new technique uncovered by Proofpoint researchers on how attackers are working at scale to gain access to Office 365 accounts. This method underscores the impact of user credentials and reveals how attackers leverage this access to spread internal BEC once a user’s account is accessed.
Step 1: Gain cloud app credentials
This drip campaign consists of an infrequent burst of login attempts with permutations of a user’s login. These login attempts originate from multiple addresses with a highly unusual user-agent for Office 365, commonly used in embedded Java applications. If you take Jonathan Doe (anonymized user), VP of Finance and CFO at company XYZ as an example, permutations were seen in the following manner:
"ID": "j-doe@xyz.com",
“ID": "j.doe@xyz.com",
"ID": "j_doe@xyz.com",
"ID": "jon-d@xyz.com",
"ID": "jon_doe@xyz.com",
"ID": "jond@xyz.com",
"ID": "jondo@xyz.com",
"ID": "jonathan-doe@xyz.com",
"ID": "jonathan@xyz.com",
"ID": "jonathan_doe@xyz.com",
"ID": "jodoe@xyz.com",
Most the time, the attacker’s misguess of the username results in a “UserAccountNotFound” error. On occasion, we also see “InvalidUserNameOrPassword”.
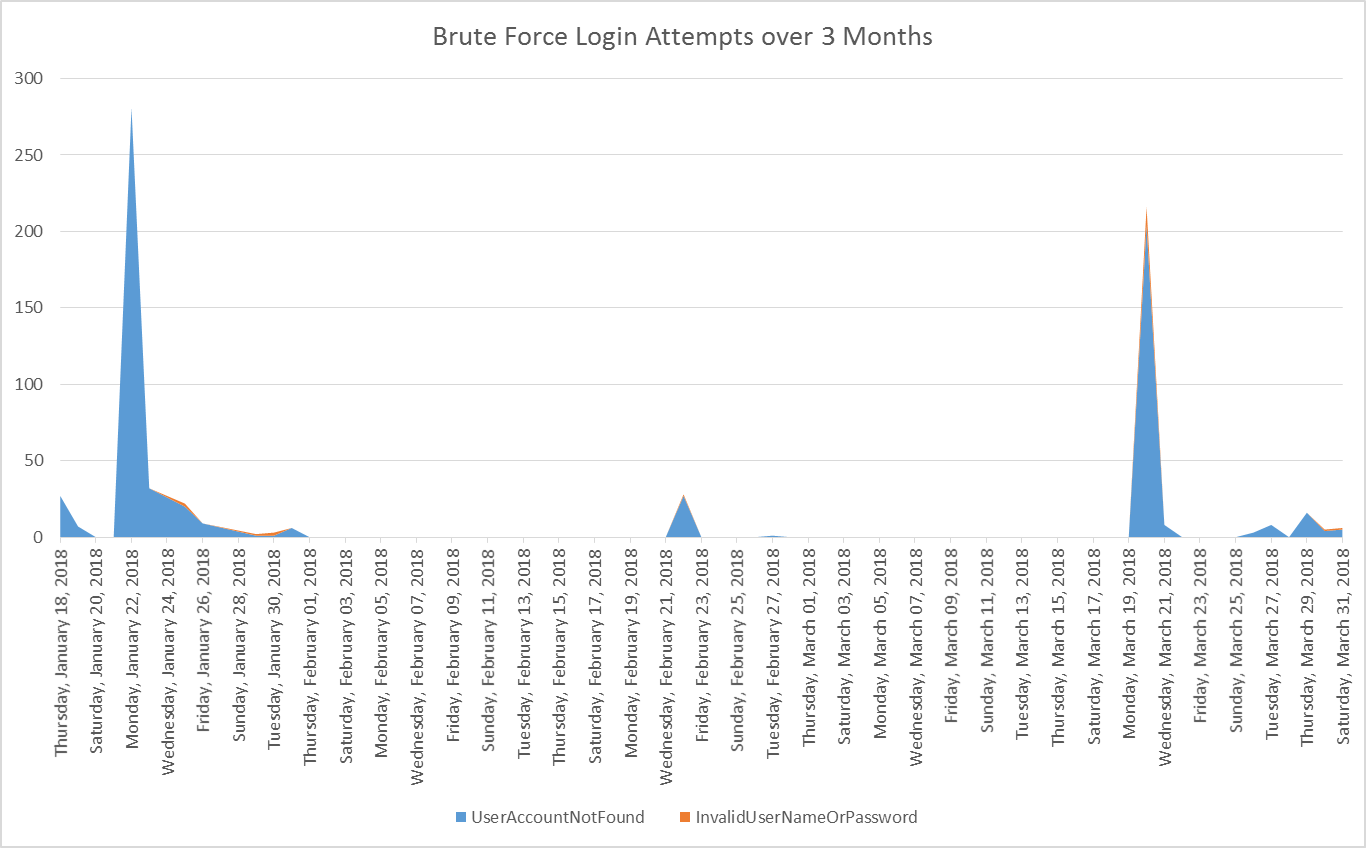
We saw this attack technique target multiple organizations, originating from the same user-agent and IPs. Here is the pattern we observed at the 80,000 user organization of this brute force campaign over a 3 month period. Weekends tend to be quiet periods for the attackers to avoid detection.
Another set of suspicious activity began when 9 logins for an employee appeared from Nigeria out of 400+ that are typically from a North American corporate. While this alert alone may not be noteworthy, within 2 weeks, 8 more user accounts within the same organization were accessed 45 times from the same ISP in Nigeria using the same peculiar user-agent.
A third discovery involved a login event to Office 365. This login used a particular email client (one that is rarely seen) which bypasses Office 365 MFA. The email client accessed the user's account from an IP in South Africa, which is non-standard for the user. We saw 10 more accounts accessed in this same manner across from approximately 50 IP addresses.
Step 2: Launch targeted attacks
Once the threat actor gains access to a user account, we see internal BEC or phishing attacks, propagating laterally to the key target of interest.
In the 80,000 user organization, the threat actor eventually gained access to a user's account. They found an internal service-desk email template. This was replicated and used to spread internal phish - with hopes to gain access to more accounts.
In one of the discoveries above where the attacker used a rare email client, the attackers went through 2-3 user accounts a day, browsing the user's emails.
Step 3: Avoid detection and profit
Threat actors will steal data. We also see threat actors erase their tracks and access that stolen data later by creating backup codes and changing recovery email and phone details. Through this calculated impersonation, the threat actor profits by attacking the organization from within.
Email attacks and cloud access are two sides of the same coin
A threat actor will have a user-centric view of how they will gain access to the credentials and data the user creates. They will phish the user. They will try to access the account.
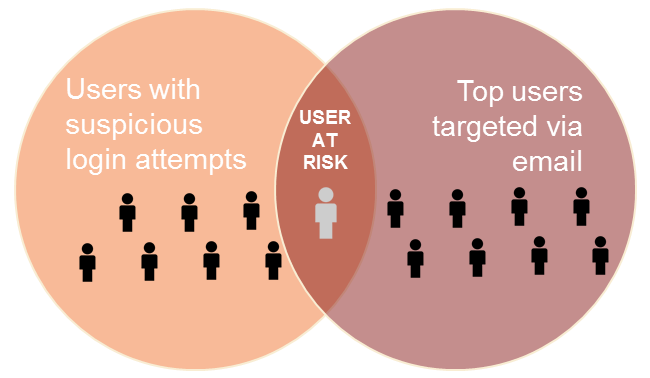
In the attack from Nigeria, 1 of the 9 users with unauthorized access is also one of the top targeted users via email in the organization. This user also exhibited a higher than average click rate for phishing URLs. Combined, it is a clear indication of a user at risk.
Historic email click activity shows the user had clicked on a URL to a legitimate business website. Post email delivery, the website was hacked and the attacker planted a phishing kit. The Gmail address to which the stolen credentials were to be sent was discovered inside the kit’s source code. This unique insight – linking between unauthorized access and attacks via email enabled us to root out 20 more users that were targeted by this phishing attack.
Correlating visibility and threat intelligence across vectors delivers a unique advantage. It helps security teams identify where to begin the hunt.
New architecture, new shapes of risk
In addition to attacks to compromise credentials, there are many other shapes of risk we see:
Over-sharing of sensitive data
- OneDrive directory shared publically
- Termination letters shared with the entire organization
- Corporate passwords shared with a personal account
Third-party Add-on Apps that were granted access to Office 365 and G Suite data
- An email and calendar third-party app - with the ability to store or disclose all user email and contacts or credentials
- A document editing app – with the ability to download assets to a third-party storage location
- G Suite scripts sending copies of an email to personal accounts
Risky mobile devices putting corporate data at risk
- Jailbroken devices with malware or bad apps
- Connecting to a Wi-Fi connection puts the user’s data at risk for man-in-the-middle attacks
- Credential phishing via SMS or mobile message apps
A unique cloud security approach
Effective cloud protection means you need an integrated approach:
1. You need a people-centric understanding of security – because attackers focus on your users. They will use email to phish your user’s corporate credentials. They will try other tactics to gain and maintain access to your user's accoun
2. Correlation of threats across email and cloud is critical for threat detection accuracy. Consider:
- A user exposed to phishing then has suspicious access to his or her corporate Office 365 account.
- Anomalous user login patterns trigger the inspection of recently clicked URLs in email – to discover that a legitimate website was hacked with a credential phishing kit post-email delivery
- A user exposed to phishing correlated with excessive downloading of sensitive data may confirm unauthorized access since attacker tradecraft can disguise location and user-agent details.
3. Advanced malware, data exposure, third-party apps and mobile access are new forms of risk as organizations move to the cloud.
Learn more
The move to the cloud changes the way organizations need to be protected. We encourage every Office 365 and G Suite customer to audit your cloud application for risk today.
Proofpoint Cloud App Security Broker (PCASB) helps you secure applications such as Microsoft Office 365, Google’s G Suite, Box, and more. Our unique risk-aware, people-centered approach gives you visibility and control over your cloud apps, so you can deploy cloud services with confidence. Our powerful analytics help you grant the right levels of access to users and third-party add-on apps based on the risk factors that matter to you. Learn more here











