In June 2025, cybersecurity headlines claimed that a massive trove of 16 billion stolen credentials had surfaced on hacker forums. While the number was attention-grabbing, there’s no indication of a recent data breach. Instead, this appears to be a collection of credentials from older breaches, many of which have been publicly available for years. Additionally, no official statements have been issued by the tech giants that were mentioned in the story (Google, Apple, and Facebook).
What is new is the attention that the story is getting. And that attention—however misleading—is a powerful reminder that exposed credentials remain a significant threat to individuals and organizations alike. Threat actors routinely collect and repurpose previously exposed credentials to launch broad credential-based attacks, such as credential stuffing and brute-force login attempts. Even old credentials can be exploited, especially when users consistently reuse passwords.
Why do these collections matter?
The concern is scale. Such a massive cache of passwords on the dark web is a goldmine for cybercriminals, even if it’s redundant or stale. Given the significant attention this collection has received over the past couple of weeks, its heightened visibility makes it even more concerning. It enables widespread credential stuffing and password spraying attacks against countless targets. Security teams should expect to see an uptick in account takeover (ATO) attempts in the coming weeks and months, as attackers scramble to exploit the latest collection.
Similar to the “Collection #1” data dump in 2019—which exposed 773 million unique email addresses and 21 million passwords—these reemerged collections can spark waves of cyberattacks. Dubbed “the tip of the iceberg,” it soon expanded into multiple collections, which totaled billions of records. Afterward, Proofpoint researchers observed a surge of account takeover activity as threat actors rushed to use the credentials in phishing and fraud campaigns.
History shows us that when credentials flood the criminal market, ATO-based threats spike. We should expect adversaries to use this latest cache of 16 billion credentials in many of the same ways that they used Collection #1. This means everything from hijacking email and cloud accounts to infiltrating sensitive systems.
The modern account takeover threat landscape
Account takeovers (ATOs) have become one of the most common threats that organizations face. Attackers prize ATOs because they allow them to operate as trusted users inside networks. It’s far easier (and stealthier) to log in with valid credentials than to exploit a software vulnerability.
Indeed, recent Proofpoint threat research confirms the scale of the ATO problem. The numbers are astonishing, and no industry is immune. Many organizations face dozens or even hundreds of compromised accounts.
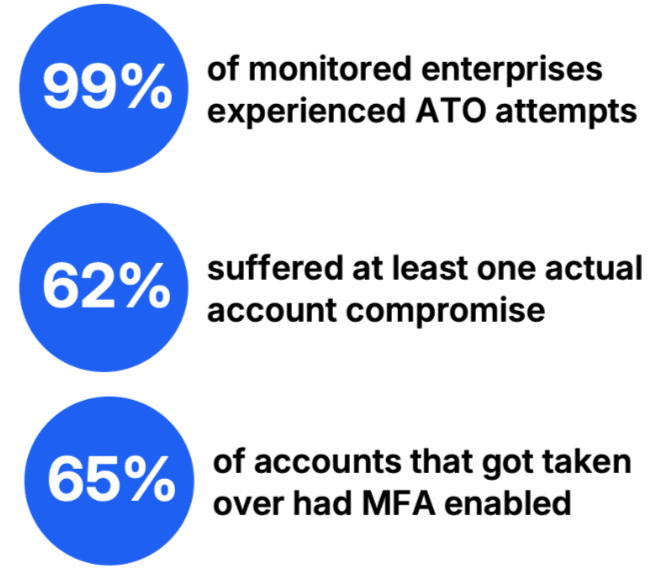
The scale of the ATO problem confirmed by Proofpoint research.
Threat actors use multiple techniques to bypass multifactor authentication (MFA). This includes SIM swapping, social engineering, and MFA fatigue attacks. There is also an emerging adversary-in-the-middle (AiTM) attack where bad actors set up a reverse-proxy phishing site. This site mirrors a legitimate login page. When users unwittingly enter their credentials, attackers steal the session cookie and hijack the session token. (You can view a live simulation of this attack here.)
Once inside, attackers have a gateway to a host of email and cloud resources. For example, they can pivot into the victim’s single sign-on portal. From there, they can access all the apps that are connected to an organization’s identity provider. This means they can evade detection and perform actions like creating mailbox rules, deleting emails, accessing emails, and stealing data. They can also send phishing and business email compromise (BEC) messages internally and externally.
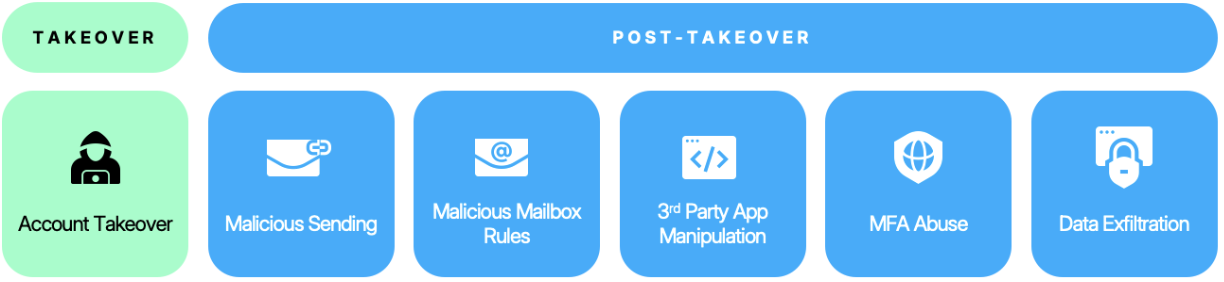
Example of post-takeover malicious activities.
Strengthen your defenses against ATOs
With over 16 billion stolen credentials now circulating, defending against ATOs is more critical than ever. A strong, layered defense requires a combination of technical controls, visibility, automation, and user readiness. What follows are the foundational elements organizations should implement to reduce ATO risk and respond with confidence.
Enforce strong authentication policies
Ensure MFA is enabled for all users, especially for email, VPN, and critical cloud apps. Where possible, use phishing-resistant MFA methods such as FIDO2 security keys or authenticator apps. Review MFA configurations regularly for any irregularities or unauthorized changes.
Configure conditional access policies
Use identity provider capabilities from solutions such as Microsoft Entra ID (formerly Azure AD), Okta, or Ping Identity. These platforms manage user authentication and access control, and can be used to enforce security policies like:
- Blocking logins from TOR networks, unknown, or unmanaged devices
- Requiring step-up or risk-based MFA for higher-risk sign-in attempts
This helps prevent unauthorized access even if credentials are stolen.
Harden and audit your cloud environment
Conduct regular security audits of your cloud tenants and identity providers. Look for any unused or misconfigured accounts, excessive privileges, or enabled but unmonitored third-party app integrations. Clean up shadow admin accounts and enforce least privilege. Remove cached credentials and old OAuth application grants where possible, as these are often exploited in attacks.
Monitor and detect anomalous activity
Trivial detections based on logins from unusual countries, multiple failed logins, or impossible travel between distant locations, are not sufficient to detect modern techniques. You need a solution that can flag suspicious login events in real time. Look for one that uses machine learning, behavior analytics, and extensive threat intelligence telemetry for both login and post-login activities. Proofpoint Prime Threat Protection with ATO protection can help provide visibility into the full multistage attack sequence. This helps security teams spot threats faster and with greater accuracy.
Automate remediation to reduce dwell time
When an ATO is detected, time is everything. Prime enables automated response actions such as suspending accounts, resetting credentials, removing malicious mailbox rules, and revoking unauthorized OAuth applications. This helps contain the attack.
Strengthen user resilience
Attackers often exploit users through phishing, credential reuse, and manipulation. Prime helps reduce this risk by delivering targeted, contextual education, which is based on a user’s behavior, role, or exposure to threats. What’s more, Prime empowers users to report suspicious email activity. All of this helps make users more resilient and enables them to become part of your organization’s defense against threats.
Plan and drill your incident response
Develop a specific plan for ATO scenarios. This plan should define how to investigate and contain an ATO. For example, remediation steps should cover checking the account, MFA settings, mailbox setting, data permissions, OAuth application grants, and more. If you’re required to disclose the attack to your partners, customers, or the public, make sure you have a plan for how to discover and assess the scope of disclosure—for example, which emails and files were potentially accessed by an attacker.
Protect your people from ATOs
With a collection of 16 billion stolen credentials circulating on the dark web, the threat of ATOs continues to grow. To defend against these attacks, you need a comprehensive, multilayered strategy that combines identity controls, user readiness, and threat intelligence.
Proofpoint Prime Threat Protection provides a foundation for your security strategy. Prime delivers multichannel threat defense, multistage ATO detection, impersonation protection, and human risk–based guidance and insights. Together, they help you protect what matters most: your people.
Want to learn more about how Proofpoint Prime Threat Protection can help you stop account compromise and improve your operational efficiency? Download the ESG Economic Validation Report for Prime Threat Protection.











