This two-part blog series covers the latest innovations to Proofpoint Prime Threat Protection. Prime empowers security organizations with expanded defenses and simplified operations to address today’s emerging human-centric cybersecurity challenges.
As the digital workspace expands, the human-centric challenges faced by CISOs and security organizations are growing exponentially. Attackers exploit multiple platforms, making it harder to investigate threats, identify high-risk users and enforce security controls. Multiple stand-alone point products are often adopted to mitigate risk across multiple platforms. Fragmented, disconnected products create gaps, drains resources and operational efficiencies.
Proofpoint Prime provides comprehensive protection to stop multichannel, multistage attacks and build human resilience across your organization. In this blog post, we’ll highlight some recent enhancements to Prime that help you to simplify your security operations to mitigate human risk.
One interface to identify and track human risk
Proofpoint Prime’s new Human Risk Explorer transforms threats and human behaviors into insights that are actionable. What’s more, it provides security teams with a single, intuitive interface where they can identify, track and mitigate human risk.
Human Risk Explorer reduces the need for security teams to manually analyze risk, correlating human risk signals across Proofpoint security controls. AI-driven analytics provide deep visibility, including a user’s attack exposure, real-world behaviors (like mishandling sensitive data or clicking a malicious link) and business privileges. As a result, it can deliver a comprehensive, intelligence-driven risk score for an organization, department or person.
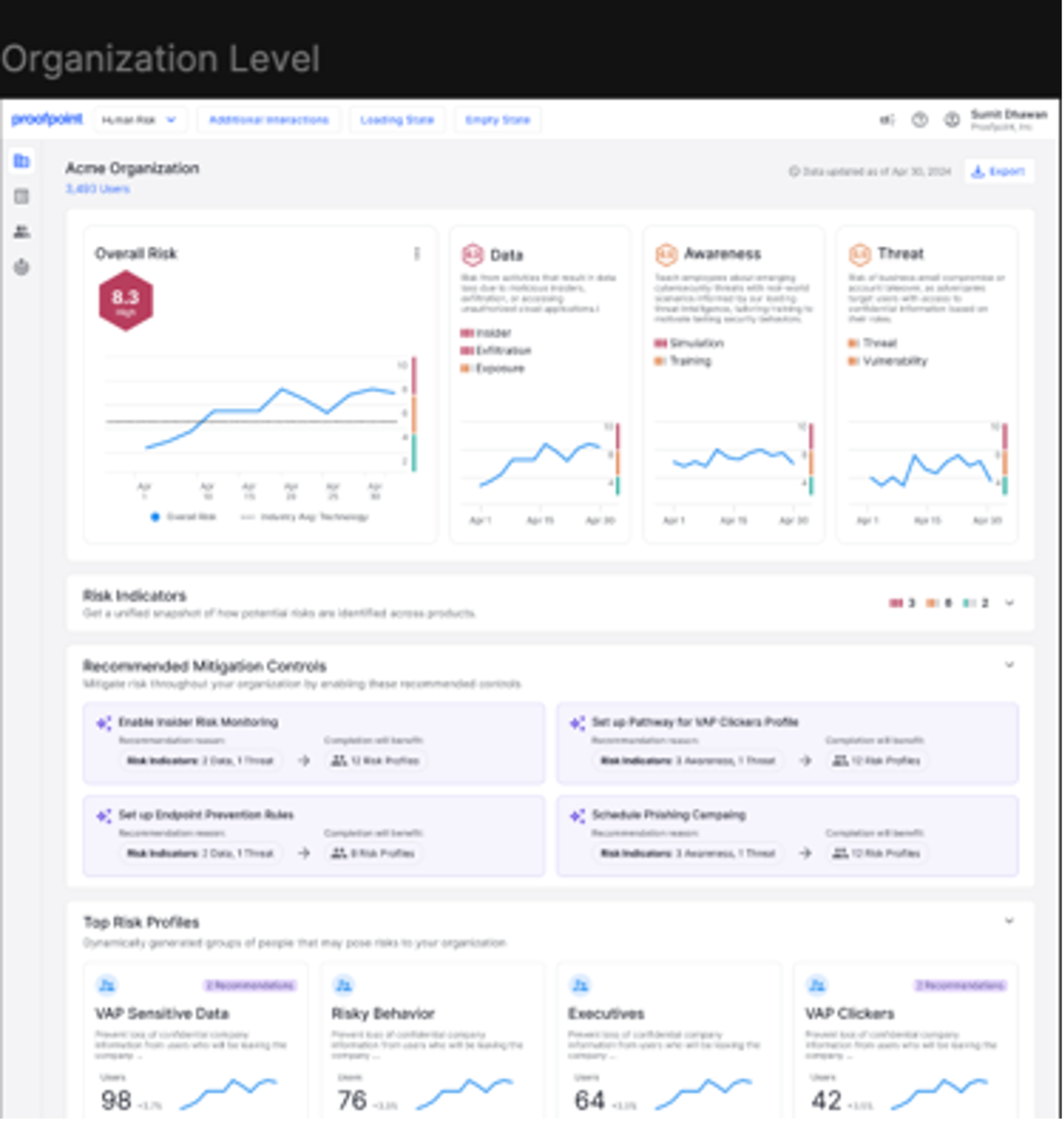
Proofpoint Human Risk Explorer.
Automated adaptive security controls and risk-based training
Human Risk Explorer identifies users who are high risk through enhanced human-risk scoring. This score helps analysts with prioritizing security efforts, applying adaptive security controls and providing additional education to those who are the most at-risk.
Security teams can give users the tools, knowledge and motivation to be more resilient against emerging threats through targeted education. Training can be tailored to suit users’ roles, behaviors and unique risk profiles.
By automating adaptive learning experiences, users get in-the moment interventions that guide them to identify and safely respond to targeted threats. With the Adaptive Groups and Pathways features, analysts can automatically enroll high-risk users into targeted campaigns. This saves them both time and the effort when it comes to building robust learning experiences that shape safe decision-making and strengthen human resilience.
A personalized Learner Dashboard helps to engage and motivate users. This dashboard is where users can access all their security training activities and assignments. They can also see their personal risk score along with their performance for training modules and phishing tests.
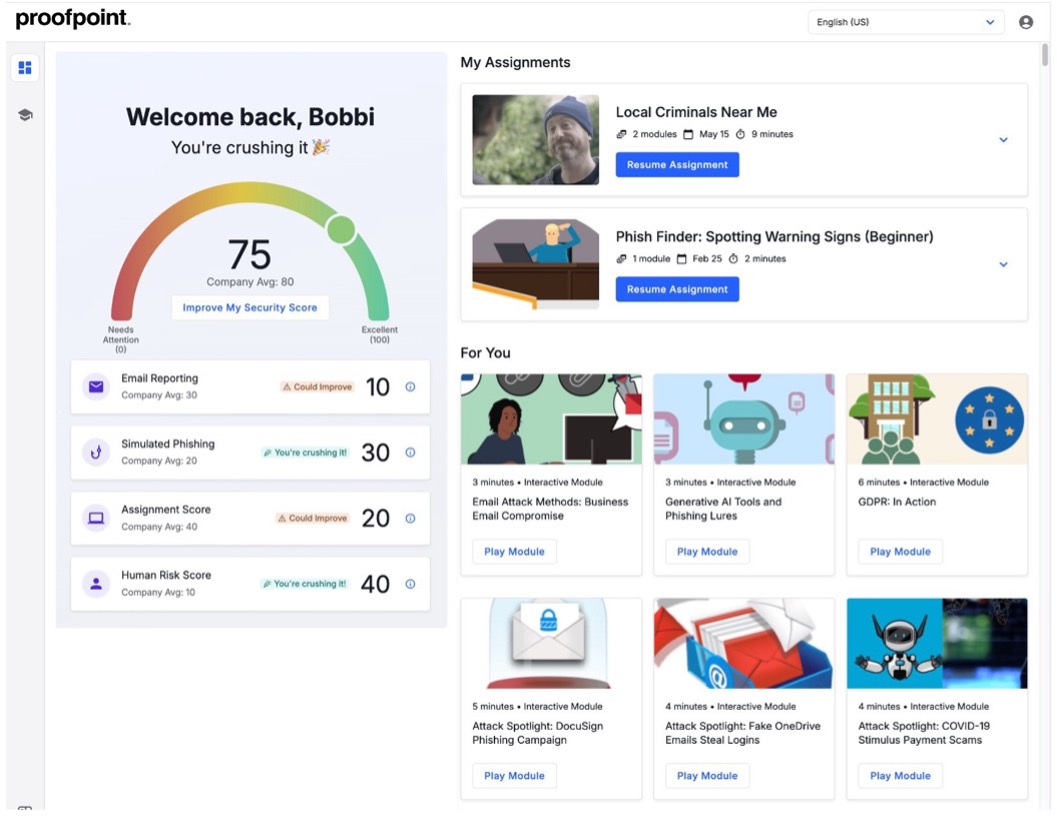
Proofpoint personalized Learner Dashboard.
Automated response to account compromise
In the case of potential account compromise, Human Risk Explorer correlates information on a wide range of pre- and post-account activities—like suspicious logins and account activities—with user behaviors and high-risk user groups, such as Very Attacked People (VAPs).
With built-in integrations for dynamic risk groups, security analysts can prioritize at-risk users and take immediate action. When a user’s risk score reaches a critical threshold, certain security controls can be automatically enforced, such as stricter rules for ATO remediation.
This ability to refine response strategies and automatically remediate threats has many benefits. Not only does it significantly reduce attacker dwell time, but it also boosts security analyst efficiency and saves valuable time
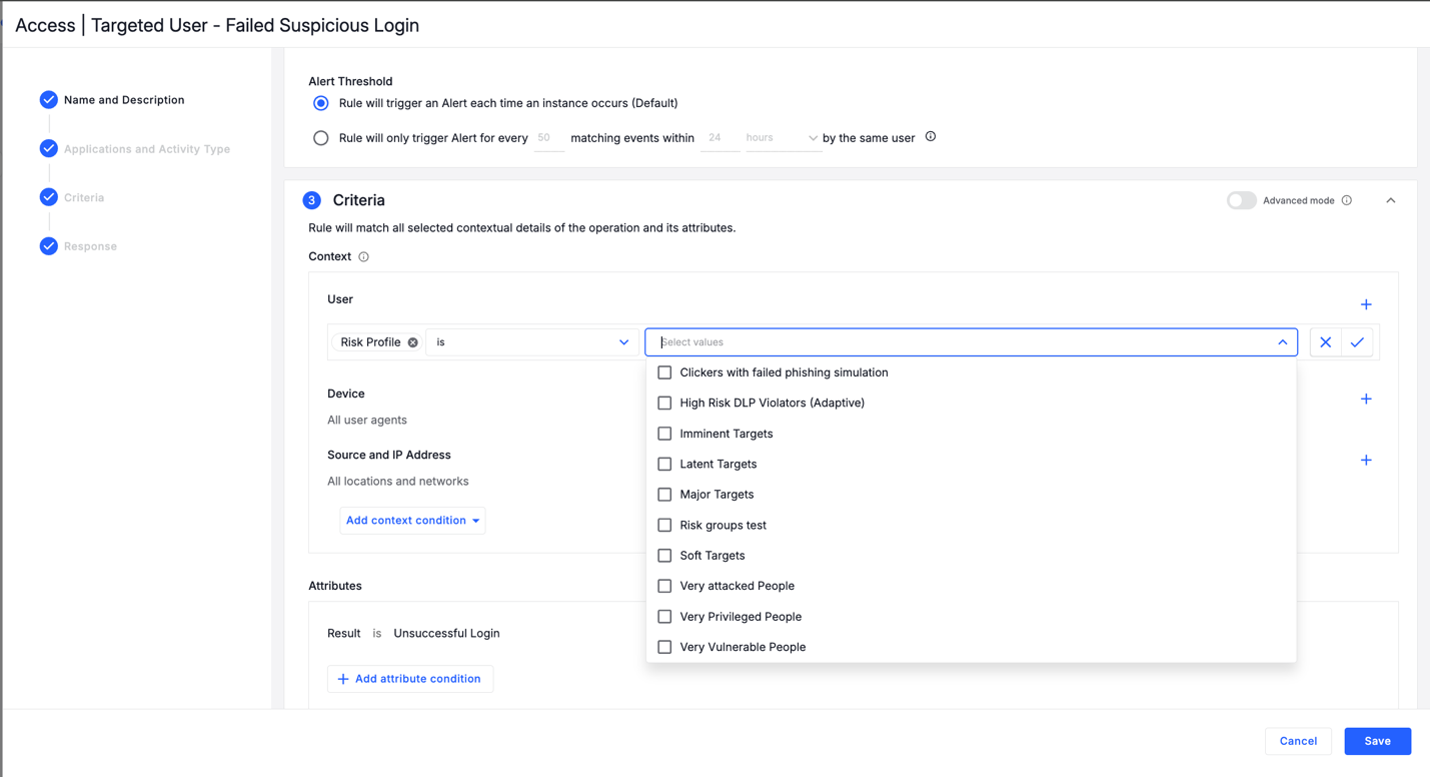
Automate adaptive security controls: Apply ATO remediation to at-risk user.
One unified view to manage every threat
Another innovation of Proofpoint Prime is Threat Protection Workbench. It delivers a new approach to how SOC teams operate. From the moment of login, they’re met with an analyst-friendly and intuitive UI that’s tailored to their daily responsibilities. Whether they’re responding to a high-risk phishing alert, evaluating a suspicious sender or investigating a broader threat campaign, everything they need is available in one unified view.
Threat Protection Workbench combines Proofpoint Nexus insights, detection capabilities and built-in integrations. It empowers SOC teams with faster threat identification and remediation while maximizing efficiency.
SOC analysts can quickly assess and respond to threats thanks to detailed forensic information, which is directly accessible within the Workbench. Analysts can view the full message body, delivery information, headers and threat details all on one screen.
They can retrieve and analyze quarantined emails as well as delivered emails (in Microsoft 365 environments). This gives them critical insights into attack tactics. Rendered screenshots offer a straightforward method for them to assess phishing attempts and social engineering strategies without the need for additional tools.
Accessible threat intelligence for one-click remediation
Threat Protection Workbench taps into Proofpoint Nexus threat intelligence to give analysts visibility into key threat attributes, threat severity and the distribution of messages across the organization. Click tracking shows user interactions with malicious URLs. And the extraction of indicators of compromise (IOCs) highlights risky URLs and attachments.
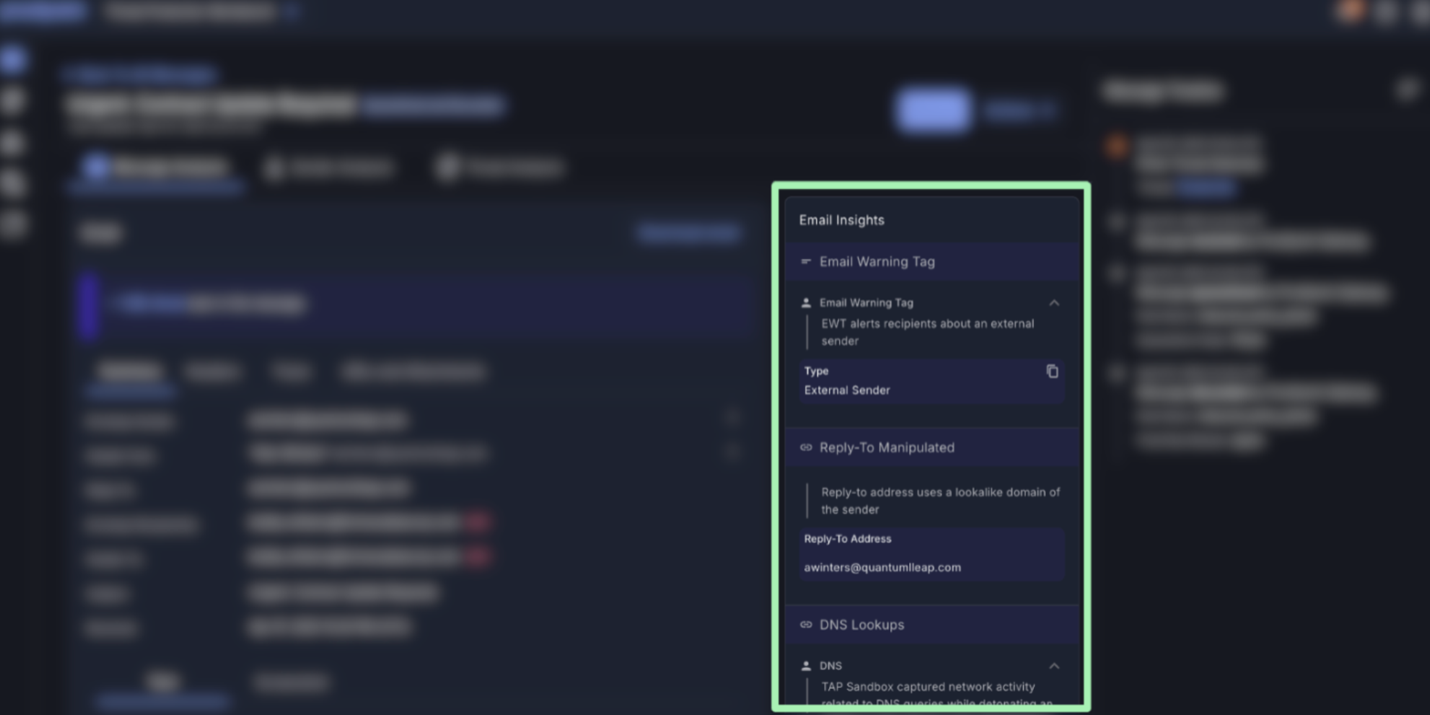
A clear, easy to understand threat summary powered by Nexus Generative AI in Proofpoint Threat Protection Workbench.
Teams also get threat summaries that are powered by generative AI. These summaries translate complex threat data into simple, actionable insights. As a result, teams can assess and respond to threats faster.
With one-click, analysts can quickly remediate threats, reducing the time between detection and mitigation. Analysts can add domains or URLs to block lists, preventing further exploitation from malicious emails or links.
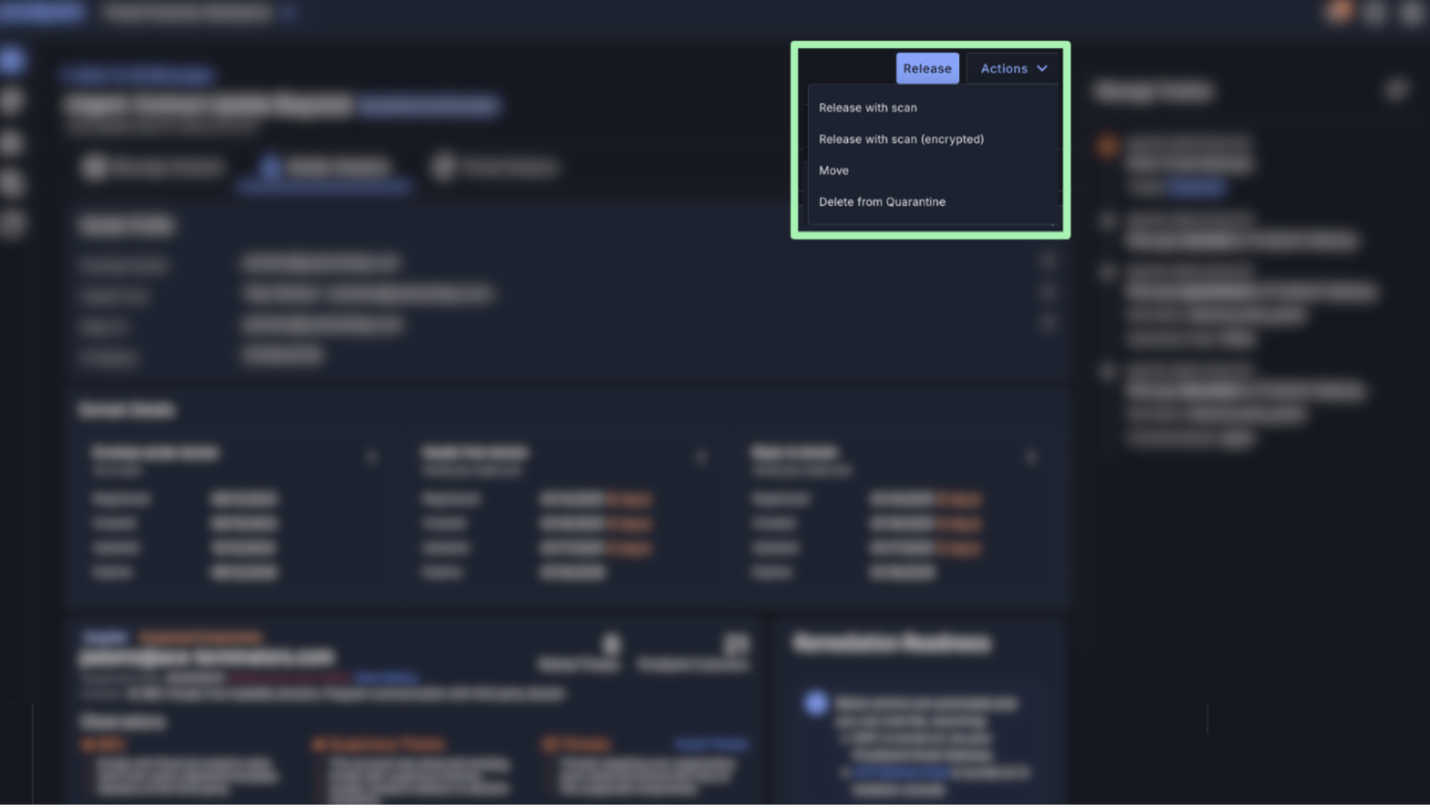
Analysts can take one-click remediation actions in Proofpoint Threat Protection Workbench.
Struggling to protect your modern workspace? Proofpoint can help
Proofpoint delivers the only human-centric cybersecurity platform with a comprehensive, adaptive approach to protecting your greatest assets and biggest risks: your people. That’s why almost 2 million customers of all sizes, including 85 of the Fortune 100, rely on Proofpoint.
To learn more about these recent enhancements, join our May 7th post-RSA chat. And for more information on our holistic approach towards human-centric threats, visit us at Proofpoint.com or contact us today.











