At Proofpoint, we’ve spent the last decade building a multilayered cybersecurity platform around one profoundly significant shift: in the modern digital workspace, people are the new perimeter. Today, users—not infrastructure—are the primary targets of cyber threats.
For this reason, protecting your people is now the most important thing you can do.
Our journey has been shaped by this reality. We’ve built market-leading solutions to stop phishing and data loss, detect account takeovers and educate users. But in today’s workplace, simply putting protection in place isn’t enough.
Protection without insight is like throwing darts in the dark, hoping to hit the bullseye. Without visibility of where human risk actually exists, security becomes a guessing game. You spend time, budget and effort trying to solve the wrong problems while the real risks go unaddressed.
The risks you can’t see are the ones that hurt you
Today’s cyberthreats continue to evolve, but so does human behavior. Your riskiest users today might not be your riskiest users tomorrow. One ill-judged click, one missed training or one misstep with sensitive data can change your entire risk landscape.
And yet most organizations still lack the ability to answer three simple but critical questions:
- Who in the organization is most at risk?
- What’s driving those risks?
- What can we do right now to address our biggest risks?
These are the human-centric security gaps that Proofpoint closes.
Introducing Human Risk Explorer
We’re proud to introduce Proofpoint Human Risk Explorer—a new solution designed to help organizations identify, understand and reduce human risk with precision and confidence.
Built into Proofpoint Prime Threat Protection and our data loss prevention (DLP) solutions, Human Risk Explorer integrates intelligence from across the Proofpoint platform—including threat activity, data exposure, behavior signals and awareness engagement—into a single, unified view of user risk.
Most importantly, Human Risk Explorer doesn’t just show you what’s happening—it tells you what to do next.
Stronger threat protection. Smarter data security.
With Human Risk Explorer, security teams can:
- Easily spot problems by tracking human risk trends over time, alongside industry benchmarks, to identify where your organization is most exposed.
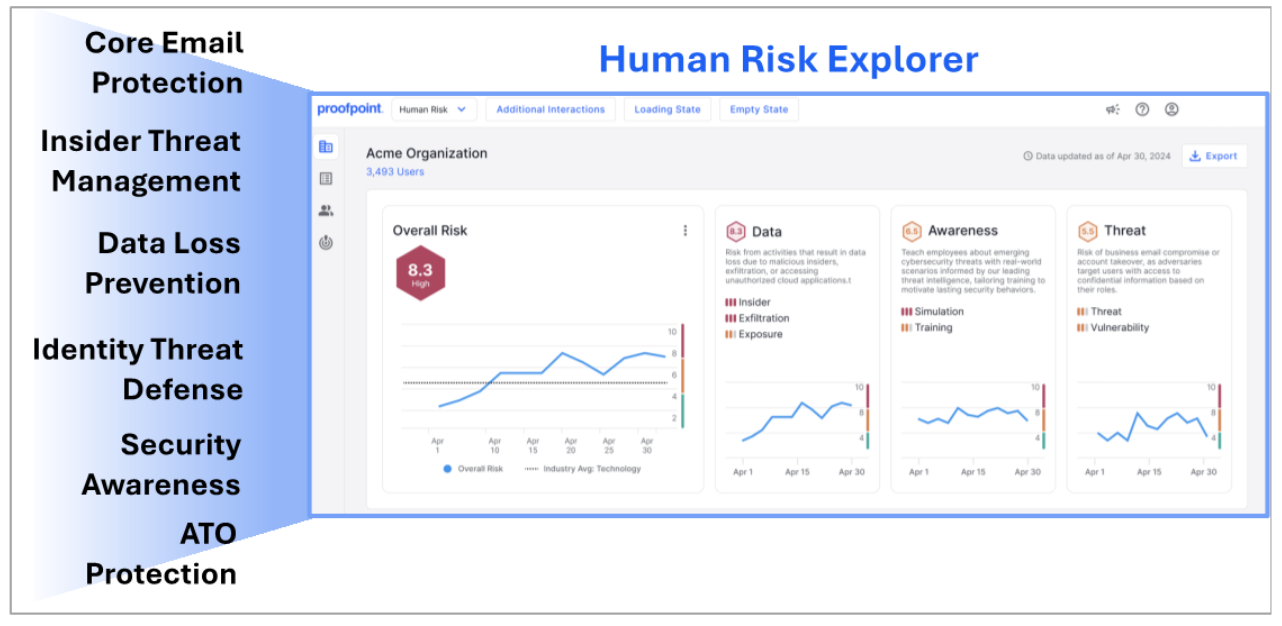
Figure 1: The Human Risk Explorer organization view. Risk scores are based on data collected across the Proofpoint human-centric security platform.
Human Risk Explorer aggregates data across the Proofpoint human-centric security platform to show changes in risk scores over time at the organizational, departmental or user level. It also provides industry benchmarking, helping you to compare your human risk posture against similar organizations. This highlights outliers and areas that most need attention.
- Understand what’s affecting your risk posture with clear explanations of key risk indicators and user behaviors.
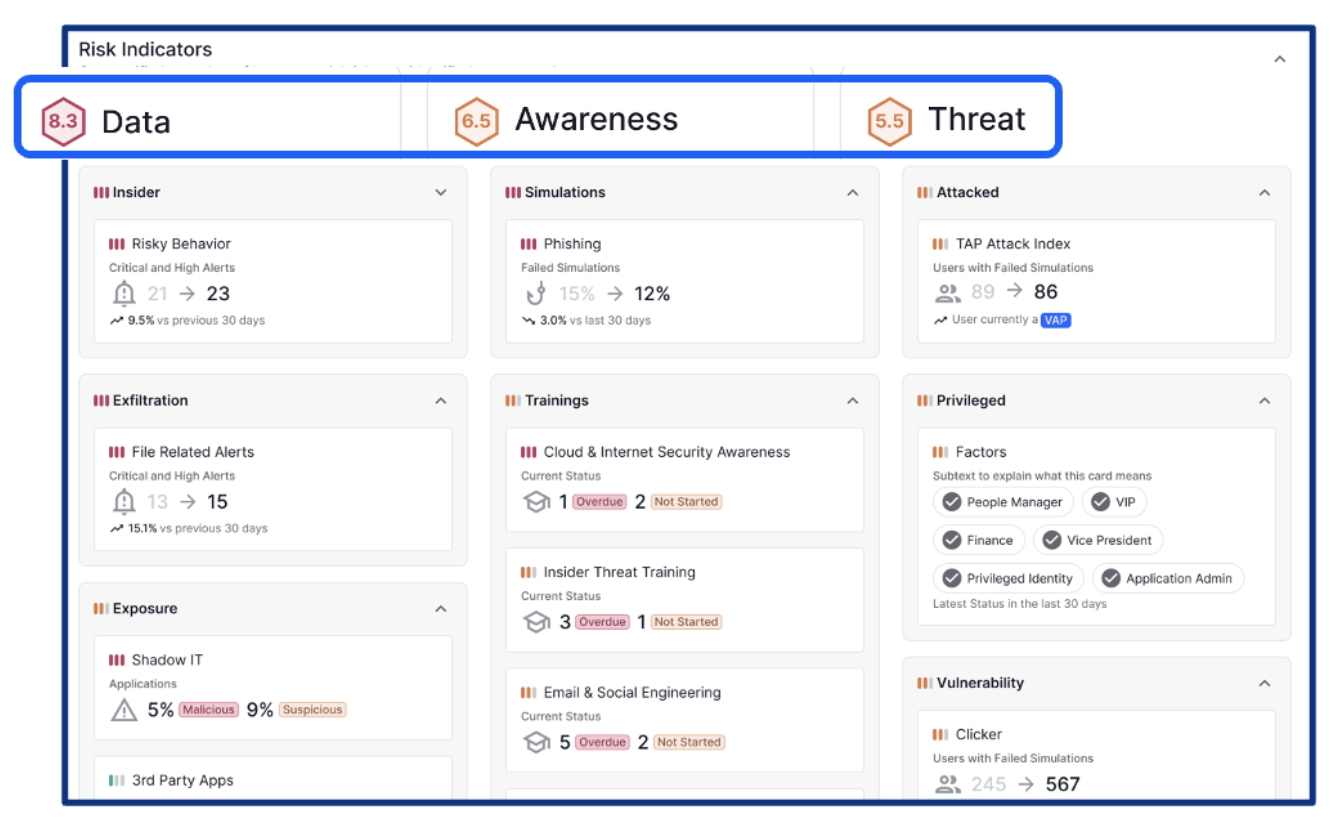
Figure 2: Human Risk Explorer provides a detailed breakdown of risk indicators.
Each risk score is broken down into clearly labeled risk indicators, such as susceptibility to phishing, likelihood of data mishandling or repeated exposure to advanced threats. With plain-language explanations, these make it easy to understand what’s contributing to elevated risk, even for non-technical viewers.
- Prioritize your most at-risk users through data-driven investigations that focus attention where it matters most.
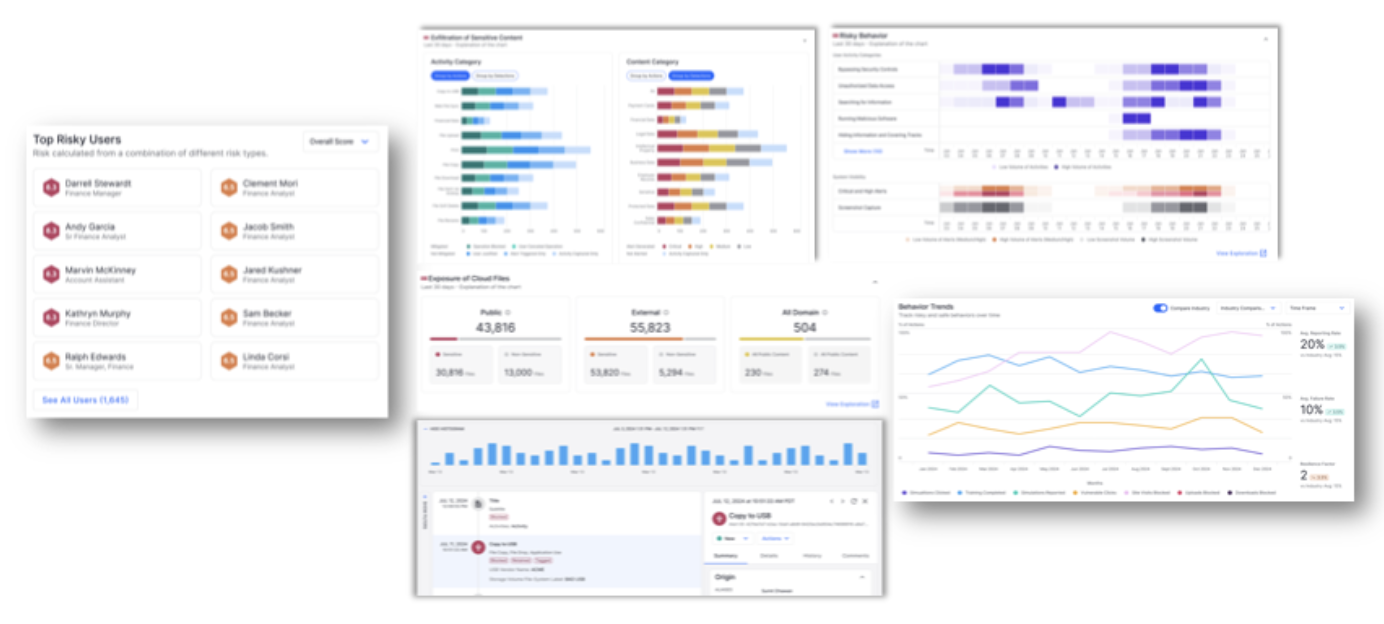
Figure 3: Human Risk Explorer enables investigations of risk insights for individual users.
Risk scores are calculated using data from multiple Proofpoint products. This aggregated data takes account of email threats, DLP incidents, user behavior, identity profiles and user training engagement. To focus investigations on the most urgent risks, security teams can filter and sort users by risk level, behaviors or specific profiles (for example, “Very Attacked People,” “Clickers,” or “Leavers”).
- Take the right next step with guided recommendations and automation for training, escalation or policy enforcement.
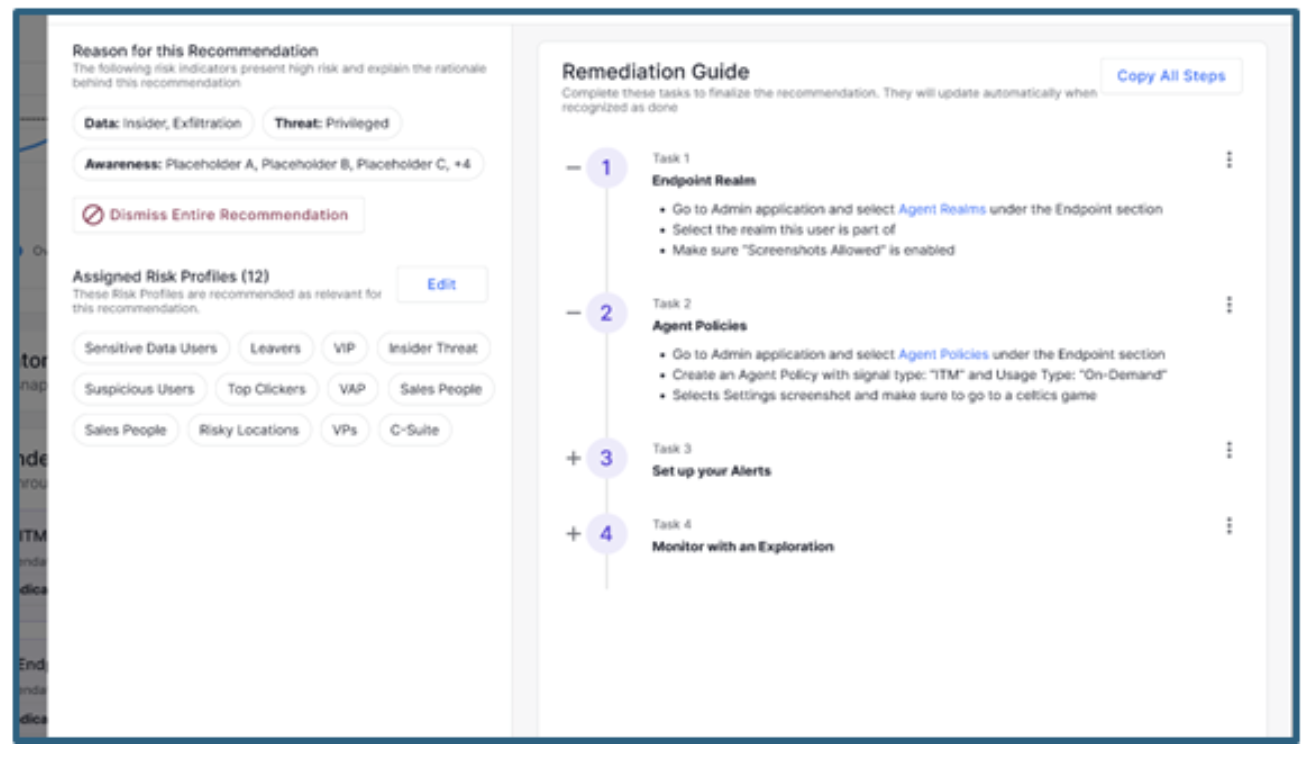
Figure 4: Example of a recommended mitigation control in Human Risk Explorer.
Human Risk Explorer provides automated recommendations based on the level and type of risk. These recommendations can include enrolling a user into targeted training, applying stricter data controls or escalating a risk for further investigation. The recommendations are mapped to the underlying risk drivers and aligned with best practices, making the next steps clear and actionable.
This is visibility with purpose. This is protection informed by context. This is how you stop wasting resources on guesswork and start making every decision count.
Optimizing investments. Minimizing risk.
Human Risk Explorer isn’t just a feature. It’s the next step in Proofpoint’s journey to protect people and help organizations like yours do more with what they already have.
It helps you:
- Get more value from your existing threat, data and awareness tools
- Focus security efforts where they matter most
- Evolve from reactive protection to proactive, risk-informed defense
- Report confidently on human risk to stakeholders and boards
Learn how it fits into Proofpoint Prime and our data security solutions
With Human Risk Explorer, we’re not just giving you more data, we’re giving you a clearer path to action. No more guesswork and wasted investigation time. Just smarter protection, built around your people.
Read the solution brief to learn how Human Risk Explorer helps elevate your entire security strategy.











