Enterprise password vault solutions help organizations secure and track the use of privileged login accounts by controlling access. They also serve the important function of generating an audit trail of which individuals utilized shared privileged login accounts (such as administrator, root and sa).
While these solutions offer important security benefits to the organization – especially given the fact that most security breaches today are the result of malicious insiders or hackers using privileged accounts – they can also serve to lull IT security staff and administrators into a false sense of security regarding their organization’s privileged accounts. Let’s take a look at what password vault solutions are missing and how these drawbacks can be mitigated.
User Activity Logging and Screen Recording
While password vaults record who logged in to which system using which account, most do not record or log user activity once users are inside the system. Recording actual user activity is critical during any security incident investigation: searchable recordings of all activities performed in all applications and system areas can quickly reveal who did what and when. They can also provide bullet-proof visual forensic evidence for law enforcement purposes.
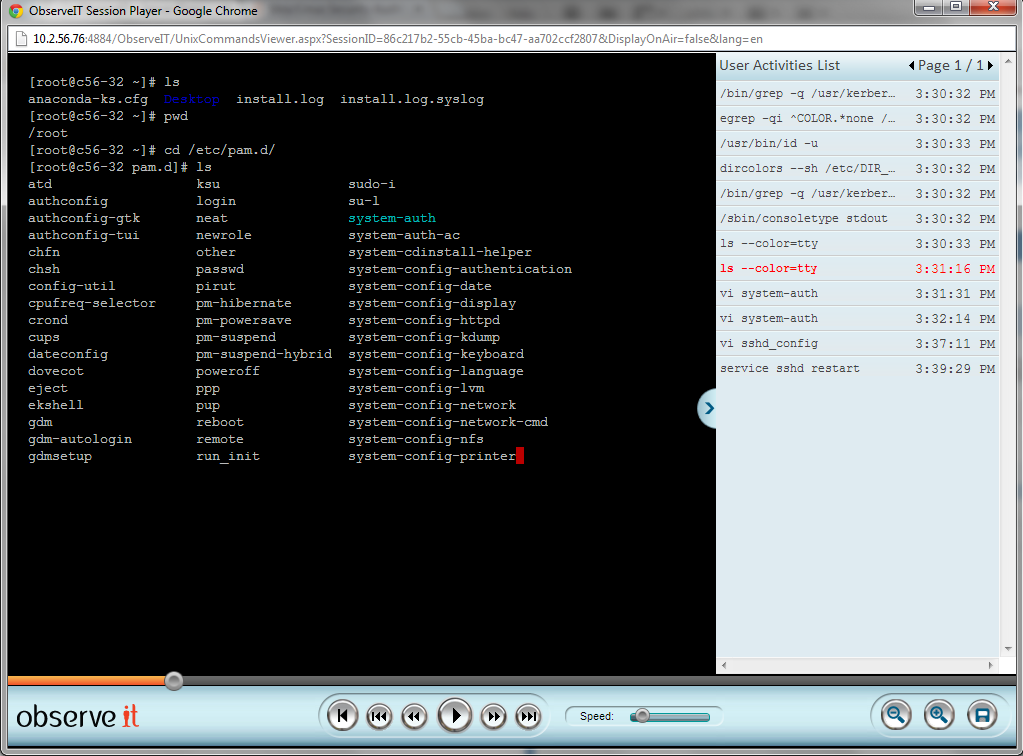
User activity video playback and searchable activity log (Unix).
Some password vault solutions do offer rudimentary activity recording of keystrokes and/or screen activity, but even then, it is usually only in particular applications, e.g., database management. Be aware that this is not nearly enough! Comprehensive, searchable user activity recordings are necessary because:
- Logging DBA activity alone is not enough. During any security incident investigation, it is important to have access to all activities performed in all applications and system areas (not just databases) and by all users (not just DBAs).
- Keyloggers which only record raw keystrokes neither “tell a story” of what the user did, nor indicate the context in which the keystrokes were typed (e.g., which application, window, text box or checkbox). This makes it very difficult for an administrator or investigator to understand what the user was actually doing, just by looking at the key logs.
- It is simply not practical to sit through hundreds of hours of screen video looking for one command or filename (especially since it might never even appear on screen!). Therefore, it’s critical to have text-searchable activity video logs which can find all text entered (regardless of whether it was typed, pasted, edited, auto-completed, or entered using the mouse), all windows opened, all files touched, all URLs accessed and all Unix/Linux commands executed (whether typed directly or run via a script or alias).
- Especially in Windows, admins are much more likely to use their mouse than keystrokes to perform many critical actions, so being able to identify and quickly find those actions is vital. In these situations, keylogging is useless.
It is important to note that, when required, User Activity Monitoring solutions can also provide unique identification of shared-account users without the overhead of a separate password vault solution. This is accomplished with a “secondary identification” subsystem that requires individual login credentials before granting access used a shared account.
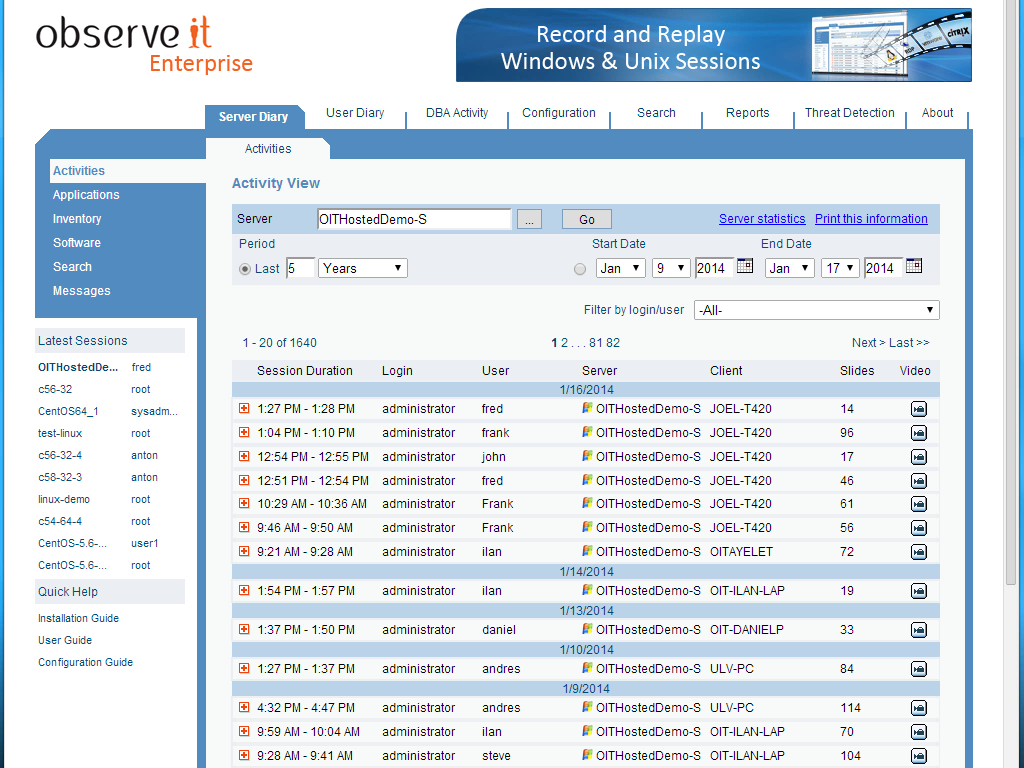
The “User” column shows the individual logging in with the shared Administrator account.
Real-time User Behavior Analytics and Alerting
Even more important than providing a powerful tool for ad hoc forensics investigations, User Activity Monitoring provides proactive breach detection and prevention, a critical security facility missing from password vaults. While password vaults help control access to privileged login accounts, once those accounts are abused or compromised, a malicious insider with authorized privileges or an outside hacker who has somehow gained access to the insider’s password vault credentials can easily steal valuable information or vandalize critical systems. In these types of situations, the password vault provides no protection or deterrence at all, and the organization is entirely at the mercy of the user.
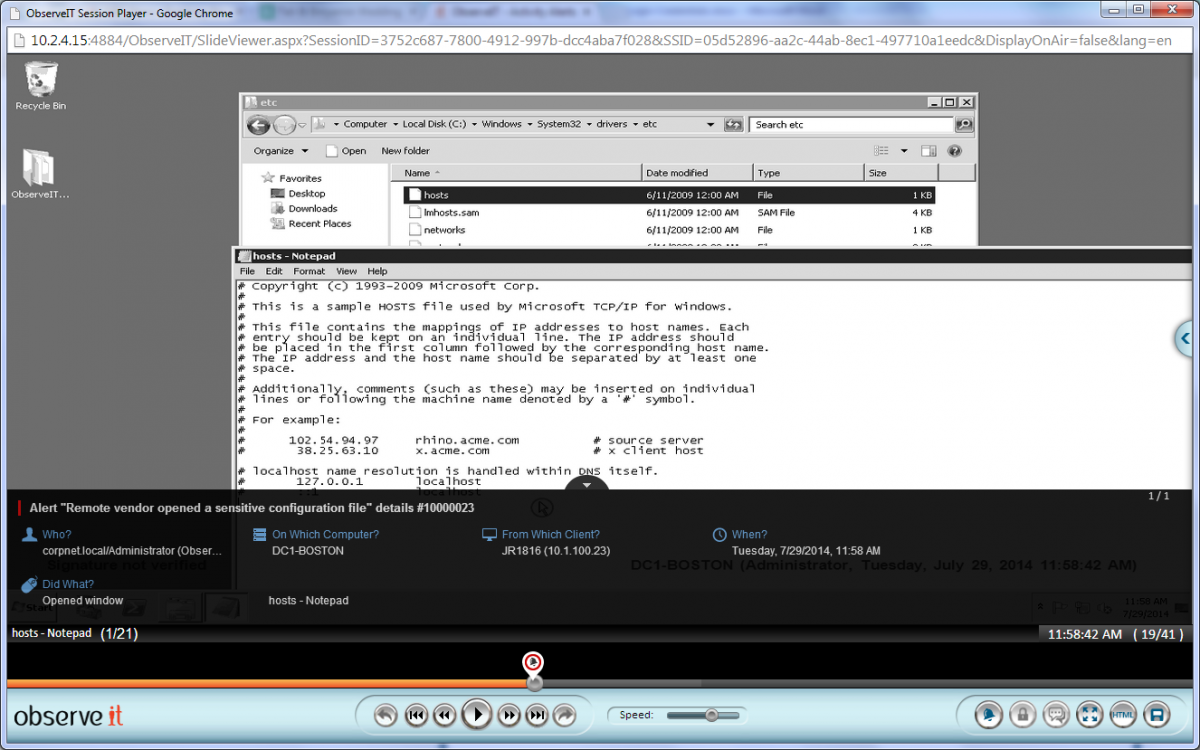
User activity video playback and real-time alert (Windows).
Given the extent of their access to sensitive systems and data, it is critical to monitor the activity of all privileged users once they have logged in via the password vault – in real-time. User Activity Monitoring solutions analyze everything that a user does and generates real-time alerts to administrators whenever a user engages in suspicious, dangerous or out-of-policy activities. Since time-to-detection of data breaches and system downtime causes are crucial, this capability is an essential complement to password vaults.
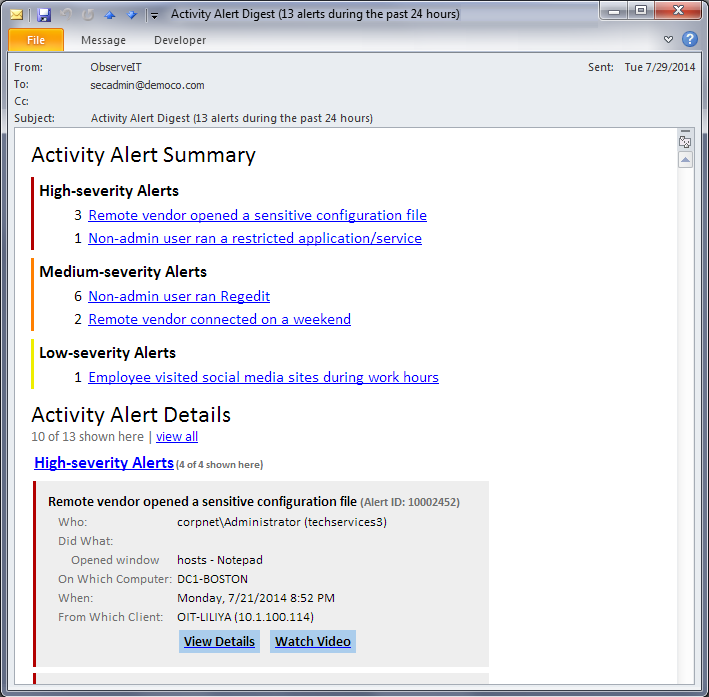
Alert digest email.
Session Recording without a Gateway
By virtue of their implementation architecture, password vault solutions are only relevant for users logging in via the vault’s gateway server. When users log in to company servers or desktops directly, whether sitting at the actual machine or via a remote access channel, the password vault does not come into play.
This major drawback can also be addressed by deploying User Activity Monitoring. User Activity Monitoring solutions excel at recording and analyzing everything that every user does on company servers, desktops, VDI sessions, virtual machines and published applications – whether logged into the machine via a gateway/jump-server, via direct remote login not via a gateway (e.g., Telnet, RDP), using Citrix XenApp or other VDI, or with local/console access.
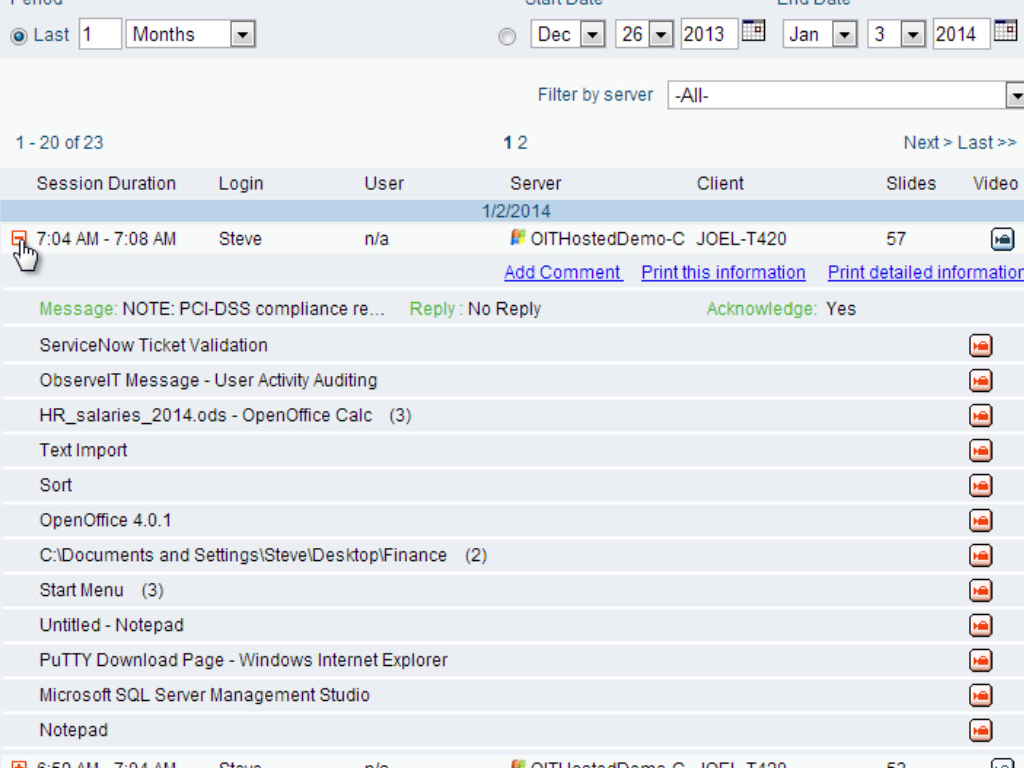
User activity log for a local session (not via a gateway), including direct playback links.
This is very important because security audits, incident investigations and real-time alerting require access to all user activity, regardless of whether the user logged in via a gateway or not. Also, it is critical that user activity logs include sensitive business applications (e.g., SAP, Salesforce), especially when the built-in logs of these applications are not sufficient to show exactly what users did.
Session Recording of Named (not just Shared) Accounts
Password vault solutions only capture sessions initiated via the vault, which is only used for shared privileged accounts. In other words, these solutions do not log or record any sessions initiated by people using individual named accounts, whether they are privileged users or business users.
This is an important
drawback because any security or compliance audit must be able to show every user’s access to sensitive resources, not just shared-account access. User Activity Monitoring solutions complement this deficiency by capturing every user session, for both shared-account and named-user login sessions.
Conclusion
While password vaults provide important benefits related to the security and management of shared privileged login accounts, they leave open many important gaps related to user activity. Most importantly, they provide little or no useful insight into what users are doing once logged into the system, and they are completely bypassed by many of the organization’s users. Thus, organizations interested in fully protecting their sensitive data and servers need to add comprehensive User Activity Monitoring to their existing security ecosystem.
A recent study by the Ponemon Institute reported that 56% of security executives are looking for solutions to provide increased visibility into user-based risks. This webinar will show you how CA’s Password Vault maps to your enterprise user-based risk and how you can greatly expand your risk coverage with user activity monitoring.











