Healthcare organizations have spent years implementing systems designed to secure their EMR/EHR systems and PHI databases. These include firewalls, virtual private networks (VPN), intrusion detection system (IDS), identity and access management (IAM) and database activity monitoring (DAM). These solutions collect a vast quantity of system and infrastructure log data in order to monitor the systems and report on what is going on.
The big problem with this current state of affairs is that users – IT administrators, external contractors and regular employees alike – have direct access to the organization’s sensitive and regulated healthcare data via the applications they use.
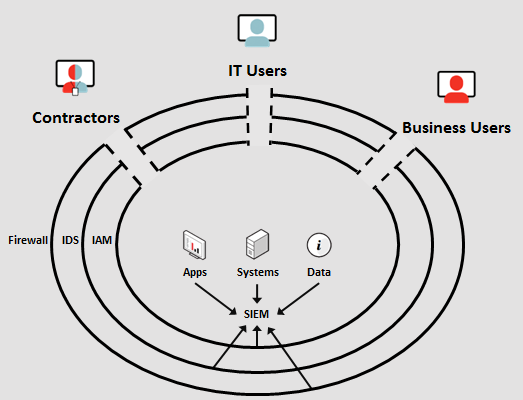
In other words: while IT security teams spend most or all of their IT security budgets on securing their servers and databases, they are ignoring the dangers inherent with what users are doing via the front ends of the patient record applications to which they have access. This is a massive gap in the security posture of most healthcare organizations.
The User Risk Landscape
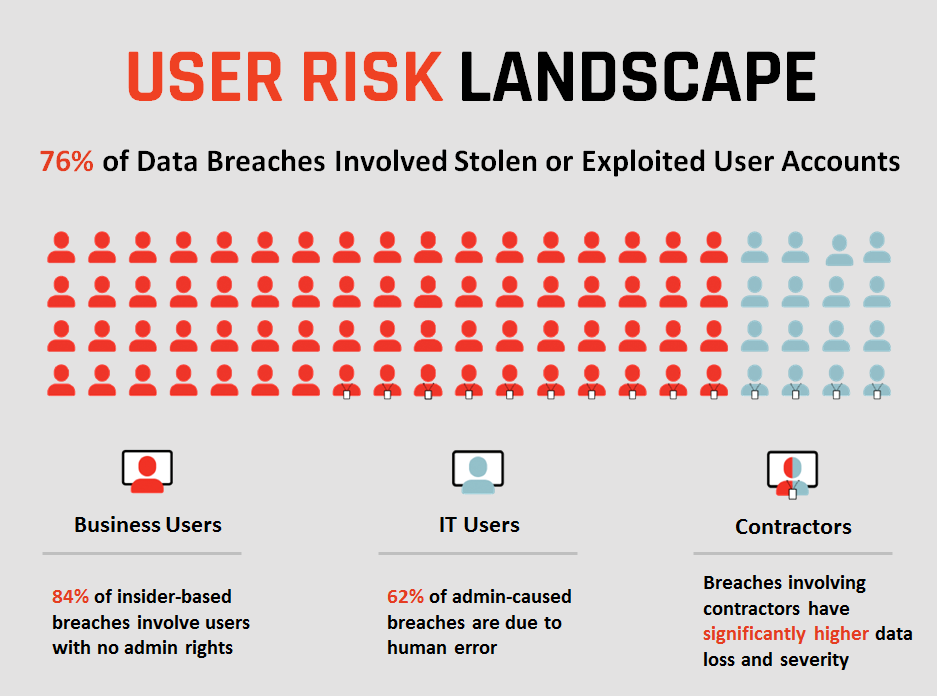
User-based risk is behind the majority of breaches and security incidents happening today. In fact, 76% of data breaches involve stolen or exploited user accounts (source: Verizon DBIR 2013). And this risk exists across the organization’s entire user population:
- Regular business users – those with no admin rights – account for 84% of data breaches (source: 2014 IBM/Ponemon Cost of Data Breach report).
- IT users – We tend to think of malicious users and hackers stealing credentials, but 62% of breaches stem from human error on the part of IT users (source: ibid).
- External contractors – Data breaches involving contractors have significantly higher business impact than those involving employees (source: Verizon DBIR 2014).
Clearly, the user risk landscape is one of the biggest and fastest growing security threats facing organizations today.
Risk from Users with Access to PHI
There are countless ways in which user accounts authorized to access PHI in Cerner, EPIC, Meditech, Allscripts, and other patient administration, electronic medical records (EMR), and electronic health records (EHR) applications can put the healthcare organization at risk. Application usage examples include:
- A healthcare worker views/copies the record of a patient not under their care
- A healthcare worker views/copies the record of a high-profile (VIP) patient
- A manager runs a report that exports a large quantity of PHI
Privileged IT users with access to PHI data storage infrastructure also pose great risk. Examples of risky activities include:
- Exporting chunks of a database containing PHI
- Installing “backdoors” to enable later penetration
- Changing the administrator or root password
- Using admin credentials on one machine to “leapfrog” to a more restricted machine
User Activity Monitoring Mitigates the Risks
User Activity Monitoring is a comprehensive, user-focused security solution that provides the required insight into exactly what every user is doing on the organization’s network. This type of solution enables security administrators to immediately detect dangerous, unauthorized and out-of-policy user activity – and to stop it in its tracks. These solutions also give administrators the ability to quickly and accurately determine, after the fact, exactly who did what, when and how with sensitive and regulated data.
The three pillars of an effective User Activity Monitoring solution:
- Visual Endpoint Recording collects user activity data by recording activity in every Windows and Unix/Linux application, webpage and system area, regardless of how users gain access (RDP, SSH, Telnet, ICA, Citrix, VMware direct console login, etc.).
- User Behavior Analytics automatically profiles user behavior and detects risky activity. User behavior analytics continually analyze user activity to detect actions that are out of role, suspicious, or in violation of security policies.
- Live Session Response allows security administrators to receive real-time alerts whenever unauthorized or suspicious activities take place.
Conclusion
User-based risk represents the greatest IT security risk to healthcare organizations today. User Activity Monitoring specifically mitigates these risks: by providing comprehensive monitoring, behavioral analytics, incident alerting, audit reporting and IT forensics capabilities for the activities of users in the front ends of applications, User Activity Monitoring closes the largest security gap found in healthcare organizations today.











