All organizations have specific files and file types that are especially sensitive and worth protecting. These may include intellectual property or trade secrets. Security tools have long attempted to defend these files, but in many cases have only added to the noise and alert fatigue that plague security teams and slow them down when real breaches occur. In a nutshell, tracking data and files is a difficult problem to solve in today’s technological landscape.
File activity monitoring (FAM) is a relative newcomer to the security arsenal, specially designed to do the sort of granular, file-level tracking that we have just described. However, it has been challenging to implement effectively. Often, it adds to the noise that security teams must sort through, and in some cases it requires a level of fine-tuning and fiddling that isn’t sustainable over the long haul.
In this post, we’ll take a deeper look at how organizations have attempted to solve this common security problem, what has and has not worked, and how Proofpoint’s newest release (7.7) adds a helpful new approach to combat data exfiltration and the misuse of sensitive files.
Let’s dive in.
Potential Approaches to Monitoring File Activity
The Block and Log Approach
The approach that many organizations take is what we call “block and log.” This is often done using a data loss prevention platform (DLP) or security information and event management (SIEM) tool. These applications block certain actions on the endpoint and log all activities.
One problem with logs is that they are simply chronological, which means that it can be difficult to sift through and identify related activities. As a result, investigating potential security breaches can take a very long time, since there is no straightforward process for gathering context. Another problem with logs is that they do not treat individual files as units, but rather track everything happening on the endpoint. This leads to a lot of noisy and unhelpful alerts.
Ultimately, tools like this only see one-time events—for example, a file being downloaded from Salesforce. They do not have and cannot provide context on what happened before, during, and after a potential incident. Tracking files throughout their lifecycles with a tool like a DLP is extremely manual and may not even be possible in many cases.
Additionally, these tools often require an endless amount of fine-tuning to even produce alerts in the first place. The process of setting up a DLP can take months or longer, so many organizations have never even fully set them up. Even once they are set up, teams must clearly and continually define the various files they need to be worried about (which, as you can imagine or may know first-hand, is a tall order).
For all of these reasons, the “traditional” methods for tracking data and files have not worked well at all.
File Activity Monitoring
Beyond the block and log approach, there is, as we mentioned, file activity monitoring. With file activity monitoring, any file download from sensitive data locations (servers, cloud, network fileshares, desktop, removable media etc) or upload to various exfiltration channels can be tracked.
This is a good start, but the problem is that it also creates a lot of noise. For example, if an image is downloaded from Pinterest, that’s probably not of much interest to the security team, but they may still receive an alert. On the other hand, if a file is downloaded from Sharepoint, that could be much more relevant. So while file activity monitoring has been a step in the right direction, it still produces far too many alerts for most security teams to wade through. It is high time for a new approach.
FAM Filtering with Proofpoint 7.7
With Proofpoint 7.7, you can now filter the types of alerts you receive using file activity monitoring, and the types of activity you track. This enables you to only track and receive alerts on the most relevant file activity. For our users, this change will result in an average of a 10:1 reduction in alerts. In other words, teams should receive about 10% of the alerts they previously did with file activity monitoring, and the alerts they do receive should be much higher fidelity.
By reducing alert fatigue, FAM filters make file activity monitoring doable on a daily basis, and therefore more effective.
To get into the nitty-gritty, Proofpoint 7.7 allows teams to develop specific FAM filters for:
- Endpoints
- Downloads to or from sensitive internal web applications
- Uploads to web-based exfiltration channels (e.g., cloud storage, cloud email)
- Certain file extensions
These are common filters that can help teams zero in on the files and types of file activity that are most relevant to their security programs.
Tracking Sensitive Files with Proofpoint FAM Filtering: Use Cases
Let’s take a look at some examples of how our customers are putting FAM filters to work.
Use Case 1: Tracking Downloads from Internal, Sensitive Web Locations
With FAM filters, teams can make a list of sensitive locations and track anytime something is downloaded from one of these.
Some examples of potentially sensitive locations include internal web apps or websites where sensitive data lives, such as:
-
- Hubspot for marketing
- Salesforce for Sales/CRM
- ADP for HR
- Github for developers
- Sensitive databases
- Internal collaboration platforms (e.g., Sharepoint)
- Slack
- Google Drive
Which sites and apps are worth monitoring (and which should be filtered out) depends entirely on the organization. Some organizations might have reason to worry about files being downloaded from Dropbox, but won’t care about Gmail. For other organizations, it might be the reverse. It all depends on the organization, but Proofpoint makes it simple to deploy and tune these file download filters with a few clicks.
Use Case 2: Focusing on File Extensions
It’s important to be able to access a clear file history that delineates what happened to a file before, during, after an exfiltration event. Certain file extensions are often associated with high-value intellectual property or trade secrets, so this is a good place to focus file history.
Common file extensions that indicate sensitive intellectual property in the technology sector include .jar, .war, and .ear., since these are used for compiled source code. For other organizations, .xls or .ppt files may be of concern. Of course, organizations don’t want to track irrelevant files, since this will only add to the noise. Among our customers, .jpg and other picture formats are often not tracked based on their risk postures.
Being able to focus on file extensions allows businesses to protect their intellectual property, from design documents to manufacturing plans to drug recipes to source code. Many times, this IP is created in custom-built or industry-specific applications, so they have unique file extensions. By focusing on file extensions, teams have a shortcut to tracking important and sensitive data as the user moves it around the web and endpoint.
Use Case 3: Tracking & Alerting on Exfiltration through Specific Websites/Apps
Mature security programs have at least a working knowledge of approved web applications for internal use. They’d want to know of potential exfiltration out of the company when employees or contractors use websites outside the approved internal sites.
Examples include personal Google Drives, Dropbox, burner email accounts, Pastebin, and many others. As with the previous two use cases, it is key to have access to the entire file history if potential exfiltration is occurring through one of these channels. With Proofpoint, the security team can correlate user and file activity, look at the file origination and who did what, and go look at the user to triage an alert or investigate an insider incident.
For this particular use case, it’s worth noting that using filters can help organizations respect and maintain users’ privacy. They can, for example, exclude social media platforms from tracking so as not to pry into users’ personal lives. In this way, Proofpoint can be used to meet privacy regulations and norms for unique organizations as they see fit.
Using OIT 7.7 for FAM Filters: Key Features
Entry Filters
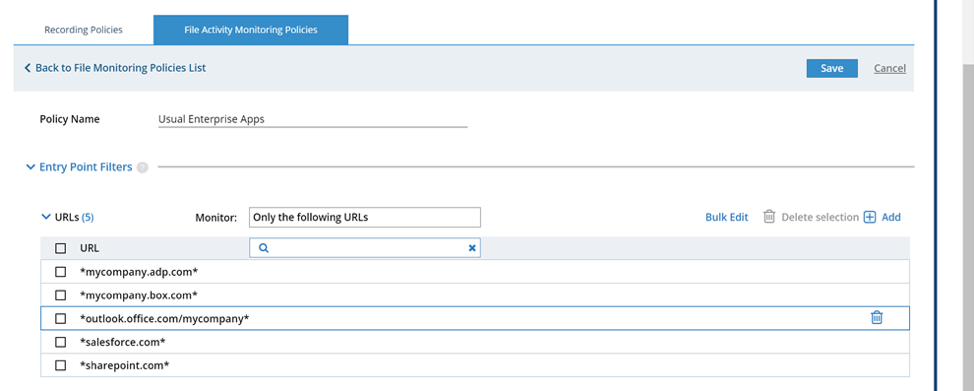
Entry filters show where files originate from, and are best used to help security teams monitor when files are being accessed via sensitive corporate applications such as Sharepoint, ADP, or Outlook.
Exit Filters
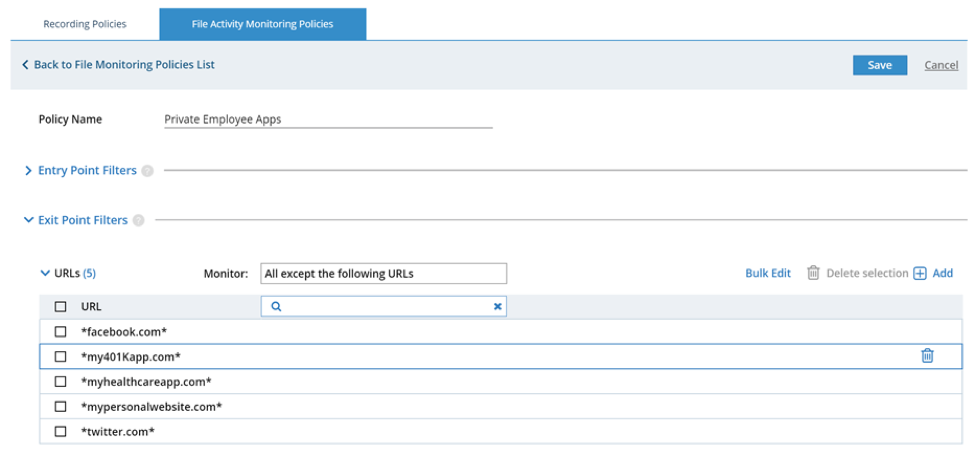
Exit filters show where data is leaving a corporate network, and can be used for two major purposes:
- Privacy: Many organizations prefer not to monitor private applications that employees use, such as social media. They only want to focus on corporate exfiltration, not on productivity or how employees spend their time otherwise, since this can be a slippery slope to privacy invasion. This enables customers to enhance their GDPR compliance while still building an insider threat program.
- Exfiltration: It’s key to focus on high-priority exfiltration channels specific to your unique firm and industry. For example, one HR recruitment and consulting firm found out that corporate communication channels used to communicate between recruiters and potential candidates was being misused. Accordingly, they focused their detection and response efforts around potential data exfiltration on those channels first. This drastically reduced the number of alerts a small, seven-person IT security team had to deal with. Previously, without visibility from Proofpoint, they didn’t even realise that such fraud between recruiters and potential candidates was occurring through these corporate communication apps.
Reducing Alert Fatigue to Increase Security Success
Alert fatigue is one of the biggest problems that security teams must face in 2019. Proofpoint's FAM filtering features, released with version 7.7, are specifically designed to help teams track and alert on only the file activity that is important to them. As we mentioned earlier, for many teams, this will reduce alerts by 90%, while improving the accuracy of the alerts they do receive.
If and when an investigation is called for, Proofpoint's FAM filtering enables teams to rapidly build context around what happened before, during, and after an incident. Teams no longer need to fine-tune rules or sort through mysterious logs. Instead, they can achieve a simple and streamlined vantage point into the file activity that matters most to the organization.
Ready to give Proofpoint 7.7 a shot?
Existing customers:
New to Proofpoint?











