We’re excited to announce the launch of our updated insider threat solution, Proofpoint 7.5. The exciting new features and functionality will help your security teams to identify, investigate, and eliminate insider threats. This latest release advances our modern approach to insider threat detection and prevention for the post-DLP world, bringing user activity and data activity together with analytics.
3 New Capabilities Introduced in Proofpoint 7.5
1. Gain Greater Visibility into Web Applications
A key aspect of any effective insider threat program is gaining visibility into the activity of contractors, third-party developers and employees to prevent the loss of sensitive intellectual property. This release provides security analysts with granular visibility into activity on sensitive IP stored in web-based systems of record, such as:
- SharePoint
- WorkDay
- SalesForce.com
- ...and much more.
Proofpoint's lightweight user-mode agent can track activity such as renaming, deleting, copying or moving data downloaded from web apps, without requiring any additional browser plugins and across all platforms. Legacy DLP players require both browser plugins and kernel-level agents for visibility into web applications -- an approach that’s heavy on the endpoint resulting in end user experience suffering, mounting user frustration, and a solution that is difficult to deploy and maintain.
With Proofpoint, security analysts can leverage a robust insider threat library of 300+ common insider threat indicators, built based on CERT research and input from our more than 1,700 customers. Alternatively, customers can configure their own indicators to trigger real-time alerts when the movement of sensitive IP is detected within the organization.
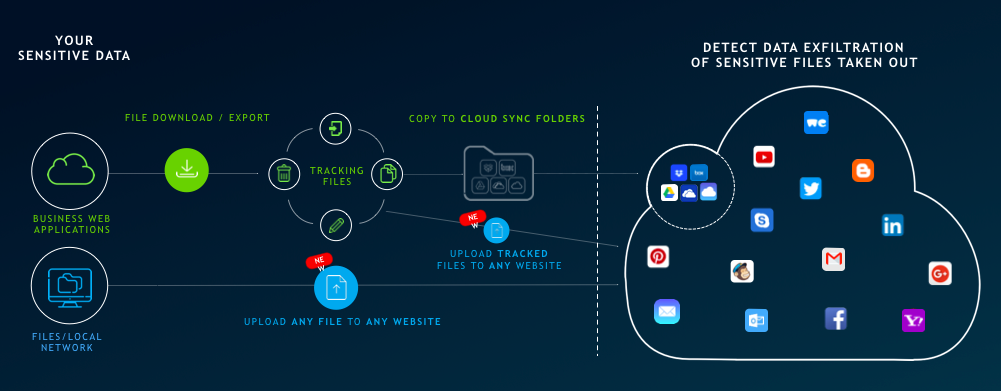
2. Prevent Exfiltration of Sensitive IP to the Web
We frequently hear prospects are most concerned with web-based exfiltration of sensitive IP. With version 7.5, we’re continuing to invest in a broad range of data exfiltration use cases. While traditional DLP and CASB vendors require browser plug-ins and API-based integrations limited to a handful of SaaS applications, Proofpoint's user-mode agent provides end-to-end file activity monitoring, along with real-time alerting for data exfiltration attempts to any web application, including:
- Email apps such as Gmail and Yahoo Mail
- Social media sites, including Facebook and Twitter
- Cloud storage solutions such as DropBox and WeTransfer
- and many more.
3. Access APIs + Integrations in Our Developer Portal
Proofpoint is deeply integrated within the security fabric of organizations, with native integrations into top software and systems. With this release, we’re launching a revamped developer portal that enables our customers and partners to easily build or extend integrations with top SIEM, security automation and orchestration, and ticketing solutions. Besides the out of the box native apps for Splunk, IBM QRadar, LogRhythm, and others, developers can use the RESTful APIs to access comprehensive metadata around users and their data activity with real-time alerts.
Let us know what you think!
As a company, we’re constantly striving for continuous improvement by providing the features and functionality you need most to protect your company from the inside out.
Not a Proofpoint customer yet? Try Proofpoint free.











