
(Updated on 02/24/2021)
Unix and Linux servers are growing ever more popular in today’s enterprise environment. With their increased popularity, Unix/Linux systems have become more popular targets for security incidents. There have been cases of external threats where hackers have gained access to these Unix/Linux servers through the internet. However, the largest threat to your Unix/Linux system is not external, but internal.
Unix/Linux Insider Threats:
Insider threats can come from anywhere, but in Unix/Linux, there are some insider threats that stick out as both common and extremely harmful.
- A user creates and disguises a backdoor
- A privileged user duplicates his/her account
- A system administrator or developer implanting a piece of code that allows to use or damage the server
These are a few insider threats that are common, but let’s take a use case to fully illustrate the danger of insider threats without a proper monitoring solution in place.
John is a UNIX system admin who is responsible for several hundred servers in the company data center. Each time John has an alert or a problem with one of the servers, he is required to connect to a server via ssh to figure out the alert cause. The server configuration disallows the user to connect as a root user directly, so John logs in to the server as a regular user and runs all the commands that need root privileges using a sudo command.
John gets tired of typing his password each time he needs to connect to each server, so he creates bash script called testme.sh that creates a local user on the system with root privileges (uid=0). This bash script also adds a ssh public key to the user which enables the user to run commands on a remote server without the need of entering a password. The bash script deletes any trace of this action and leaves no trace in the logging system. By running testme.sh John overrides all traditional log and monitor systems.
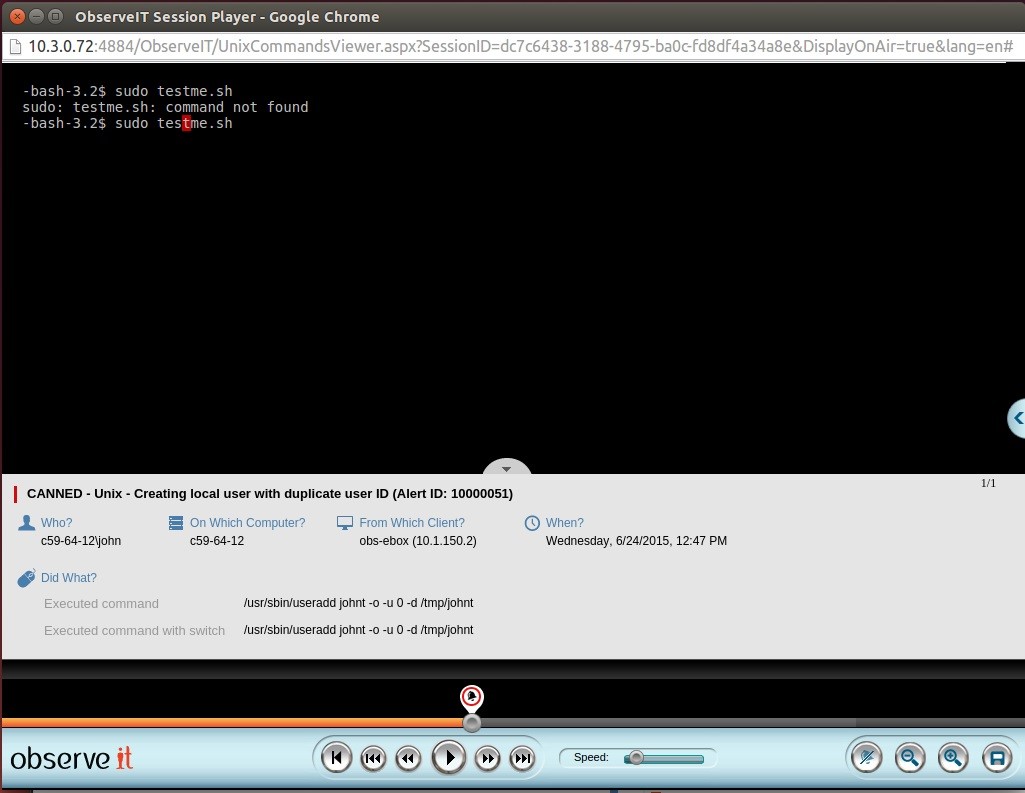
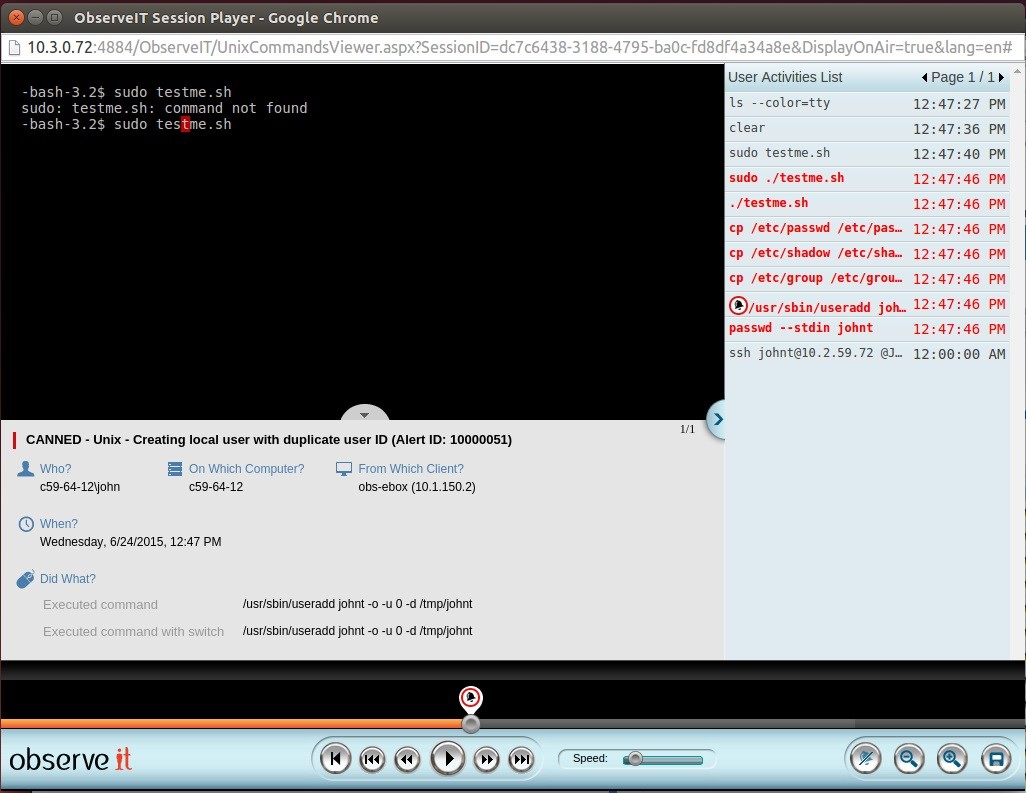
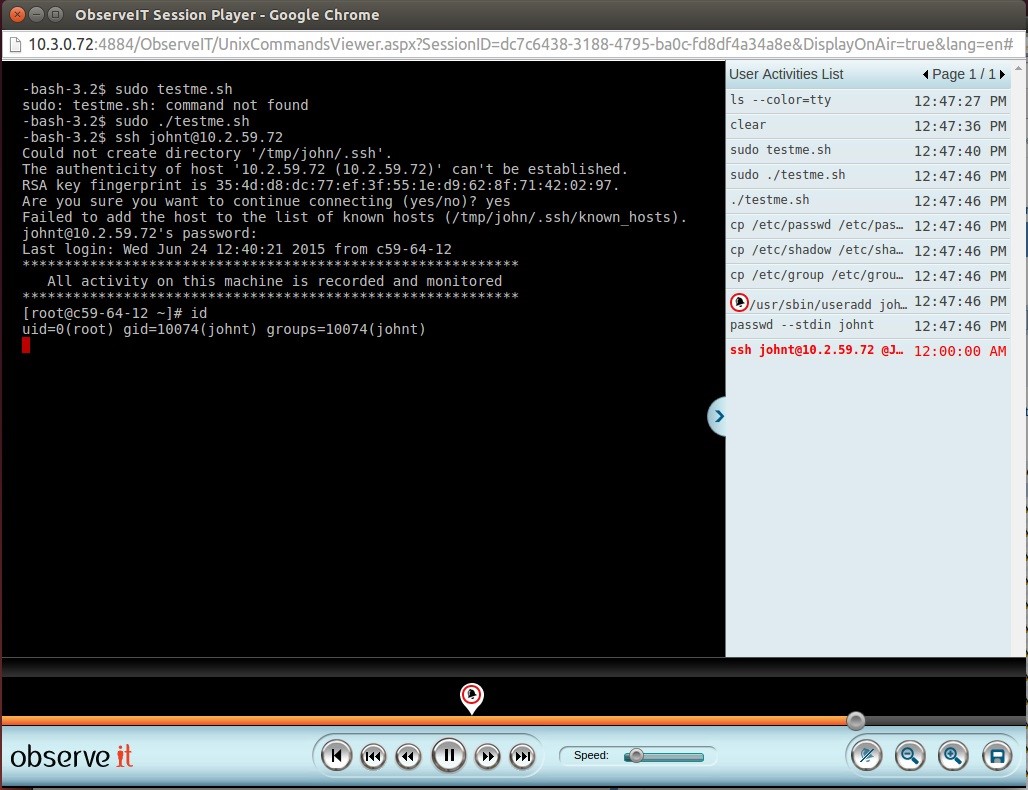
These insider threats can occur without anyone noticing. Organizations need to put a system in place in order to detect these activities.
Proofpoint ITM’s UNIX/Linux Monitoring Capabilities
Proofpoint ITM’s approach to monitoring UNIX/Linux is different from all other monitoring solutions. Proofpoint ITM’s agents can monitor process activities and behavior to detect anomalies. The agent can record any user session and gives a unique view of the flow of commands running inside the UNIX/Linux session. Proofpoint ITM agents send data to the central server in order to generate real-time alerts when a command or specific parameter triggers an alert based on predefined security rules. The Proofpoint ITM administrator can then follow the alerts back to the command video playback in order to view the entire user session. The data is also indexed and searchable, enabling Proofpoint ITM administrators to quickly search for alerts and find the corresponding video playbacks.
Proofpoint ITM UNIX/Linux Benefits
- Process Base Inspection: Proofpoint ITM’s solution is based on process monitoring, thus it has the ability to track the flow of process and sub processes and generate in real time a visual and indexed record using a web UI interface.
- Centralize Management: Proofpoint ITM’s centralized control dashboard enables organizations to monitor all their servers, get real time alerts and deploy and distribute rules in one click.
- Multi-platform Support: Proofpoint ITM supports all the main Linux distributions, all major UNIX platforms, AIX, HPUX and Solaris, and Microsoft platforms in a single dashboard.
- Segregation of Duties: Proofpoint ITM enables the CSO to deploy and enforce monitoring rules on the server directly without the need of the system administrator as a mediator.
- Forensics Abilities: In case of a security rules violation, Proofpoint ITM recordings allow the security officer to trace back all the actions that were done including attempts of covering up the actions, even in case of a server being deleted.
- Real-Time Activity Alerts: Proofpoint ITM has real-time alerts that will alert when a security violation is taking place. For example package installations or the use of unexpected commands like wget, curl gzip and co.
- User Activity Inception. Proofpoint ITM monitors legitimate users doing illegitimate tasks such as a system administrator that overrides the ssh credentials, a developer adding a backdoor script to the server or someone connects directly from the server console.
- Intrusion Dictation. Proofpoint ITM inspects the abuse of legitimate processes to hack a server. For example, the hack of a server by using website vulnerabilities and opening a reverse shell from the server.
Proofpoint ITM’s capabilities with its UNIX/Linux Agent enables companies to record, replay, search and alert on user activity. Proofpoint is the only security software company that provides tailored analytics, alerting and visual forensics to identify when users are putting your business at risk. Over 1,200 companies like Cigna, Charles Schwab and Starbucks use Proofpoint ITM for incident response, forensics, and compliance. Proofpoint ITM provides screen-recording technology to capture all user activity regardless of the environment and converts the screenshots into User Activity Logs which makes searching, analyzing, and auditing user activity simple and easy. Proofpoint ITM is able to uniquely help companies prevent the loss of sensitive corporate and customer information by detecting suspicious behavior in real-time and providing forensic evidence on exactly what happened.











