Edward Amoroso, Founder and CEO, TAG Cyber
If you can imagine a group of security technologists sharing hand-scribbled drawings back and forth over webcams, then you have a pretty good idea how I just spent the past hour. The focus of all this scribbling involved how to enable visibility in support of enterprise cyber security. My partners in crime were Mike McKee and members of his fine executive team at Proofpoint, a cyber start-up that knows a thing or two about this topic.
Two key questions to consider about Cyber Visibility:
- What does it mean today for an enterprise cyber security team to have sufficient visibility into meaningful activity to properly manage risk?
- With the evolution of most businesses to more virtual workload-based cloud services, what will it mean in the coming years for an enterprise team to have sufficient visibility, perhaps remote, to manage cyber risk?
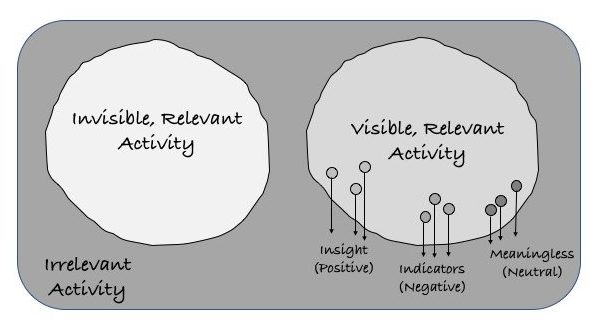
Both questions begged a taxonomy of visibility options – and we inevitably began drawing circles. My initial attempt was to draw a simple universe of visibility that broke things into two circles: visible and invisible activity. It makes me gulp that whereas today’s concept of invisible activity is called Shadow IT, tomorrow’s view of invisible activity will be normal employee use of public cloud. That is quite a change.
The Essential Benefits of Visible Actions
The second round of drawings involved deriving more insight into the categories of visible activity. After going back and forth a bit, we agreed that three benefits emerge when security teams dip their ladle into the visibility circle:
Visible actions can offer the following benefits:
- Business Results: Positive insight that can, in turn, enable business results.
- Negative Indicators: Detection of negative indicators, usually based on profiles, behaviors, or signatures.
The alternative is that some visible actions can be meaningless, and offer neither insight nor detection.
Distinct Categories of Relevant Cyber Visibility
I really liked the resulting security taxonomy because it provides four different categories of relevant visibility:
- There is invisible action, which should make you uncomfortable if you manage risk for a living.
- There is insightful visibility, which is obviously positive.
- There is visibility that detects unwanted activity, which is positive because it prevents negative
- There is visible, but useless information, which seems all too common.
Final Thoughts
Have we considered the correct categories? Are we missing something in the taxonomy? I am honestly tempted to incorporate these views into my writing and lecturing, but the result seems so simple – perhaps even obvious – that I wonder why I haven’t noticed this before. And, my belief is that with transition to hybrid cloud enterprise, the notion of visibility becomes one of the main primitives in our discipline.











